With the amount of data continuously feeding into a security operations platform, it is more important than ever to be able to identify the most critical threats and know immediately when those threats are triggered. With the latest LogRhythm Axon release, analysts gain quicker access into contextual information with added metadata fields in the analytics rule builder that can be connected to email notifications and into widgets in the dashboard. Additionally, we have gained SOC2 certification, added new collection capabilities, and enhanced search functionality.
SOC2 Certification
Our customers and partners want validation that their environment is highly confidential. By aligning our processes with the SOC2 compliance standard, we provide them with a high level of trust in the security of our product.
Enhanced Detections
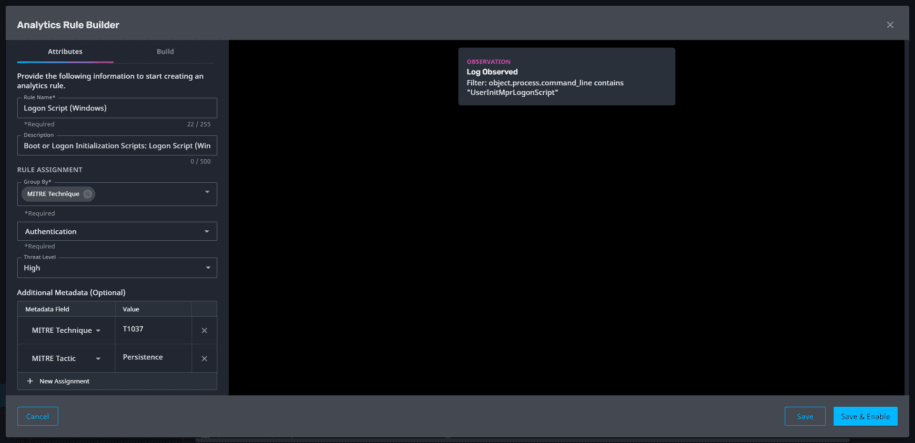
Prioritizing responses and the potential impact on any environment hinges on the ability to identify which threats are critical. By adding new metadata fields in the analytics rule builder such as threat severity, MITRE ATT&CK, etc., analysts can find critical observations quickly. Ultimately, these fields will appear in email notifications and can be used to build out widgets in the Axon dashboard, thus enabling analysts to gain quick access to contextual information related to the urgency of alarms that are received. We are continuously adding out-of-the-box MITRE ATT&CK detections as well as updating existing ones to help analysts gain quick time to value as well as quick understanding of the nature of the threats surfaced via observations.
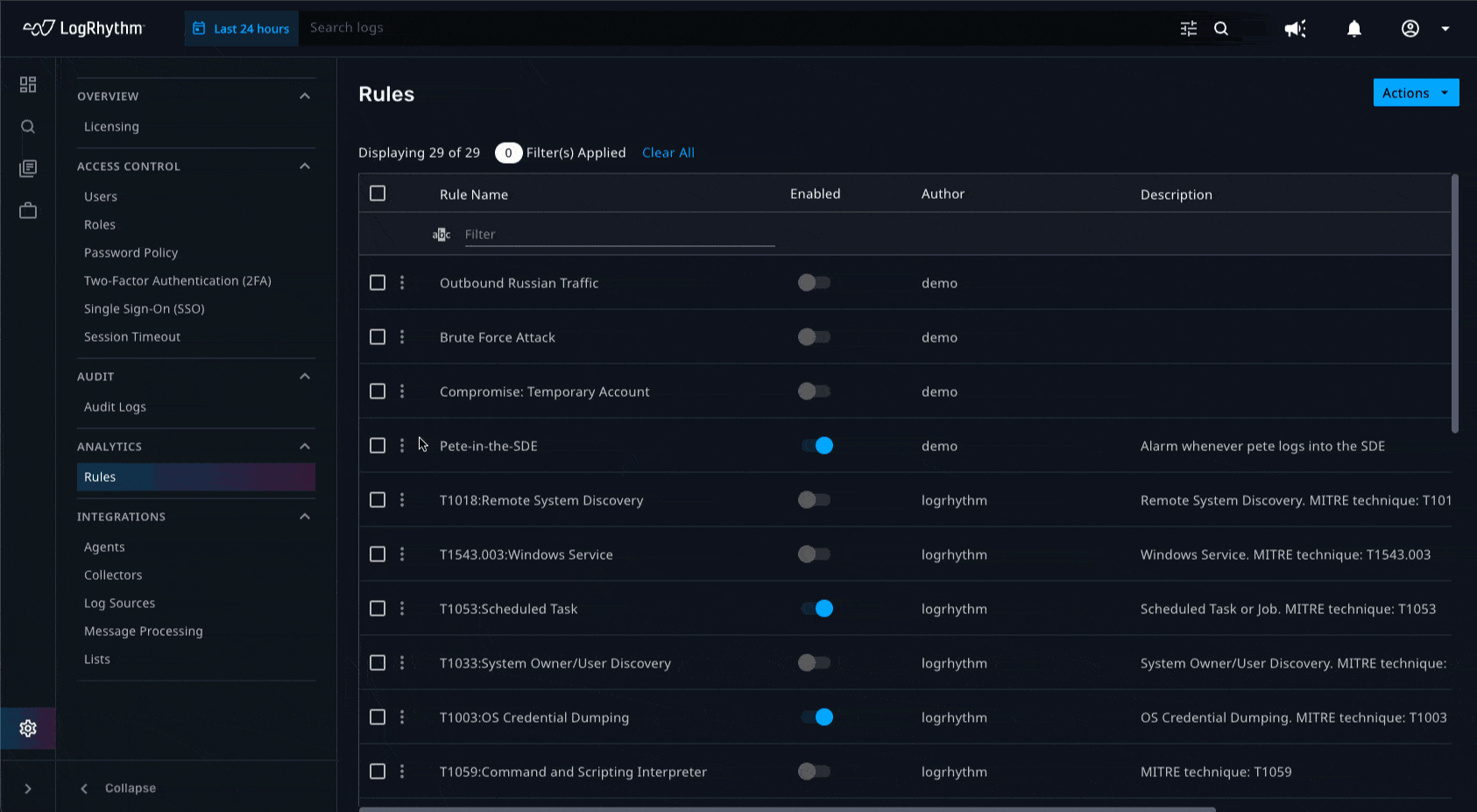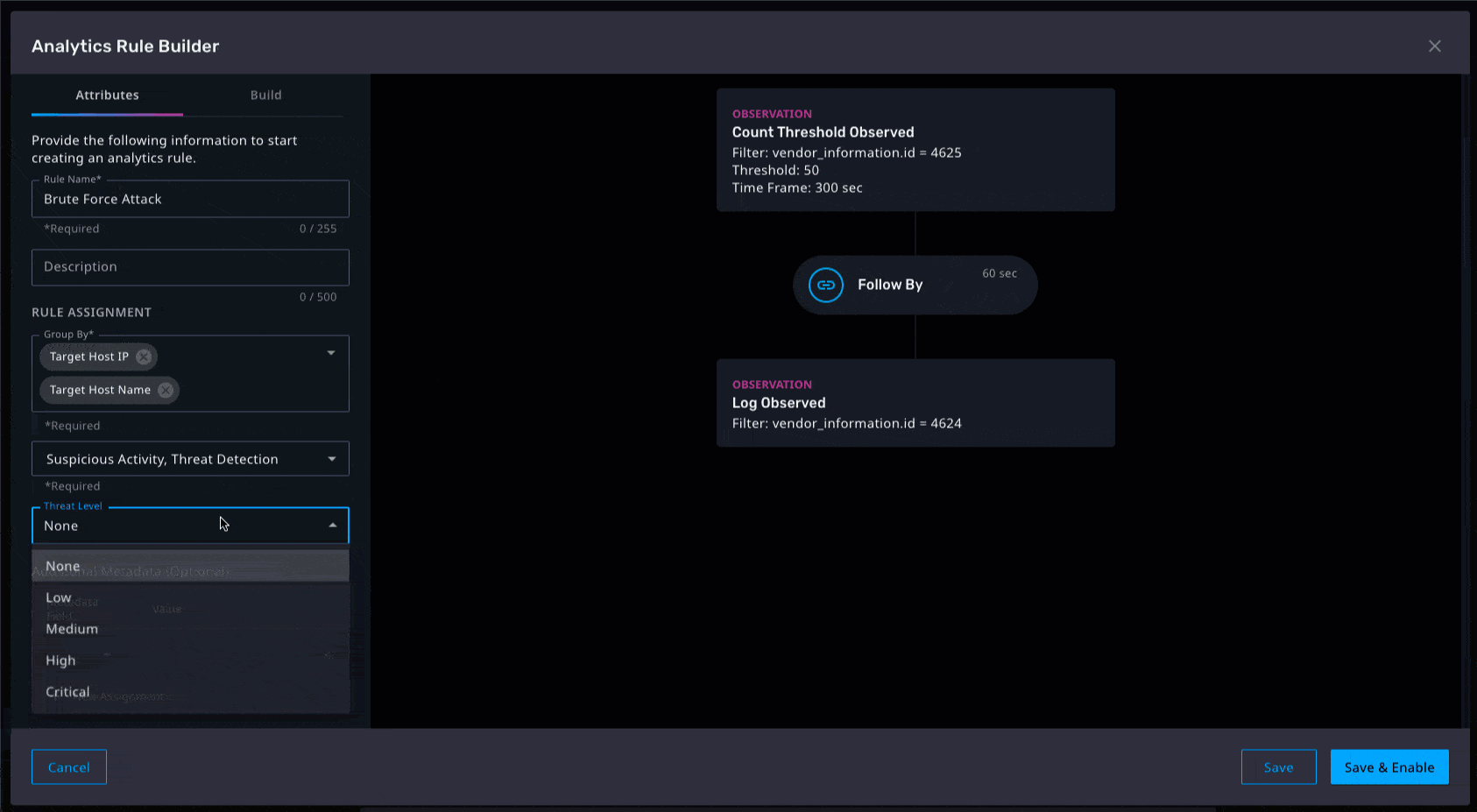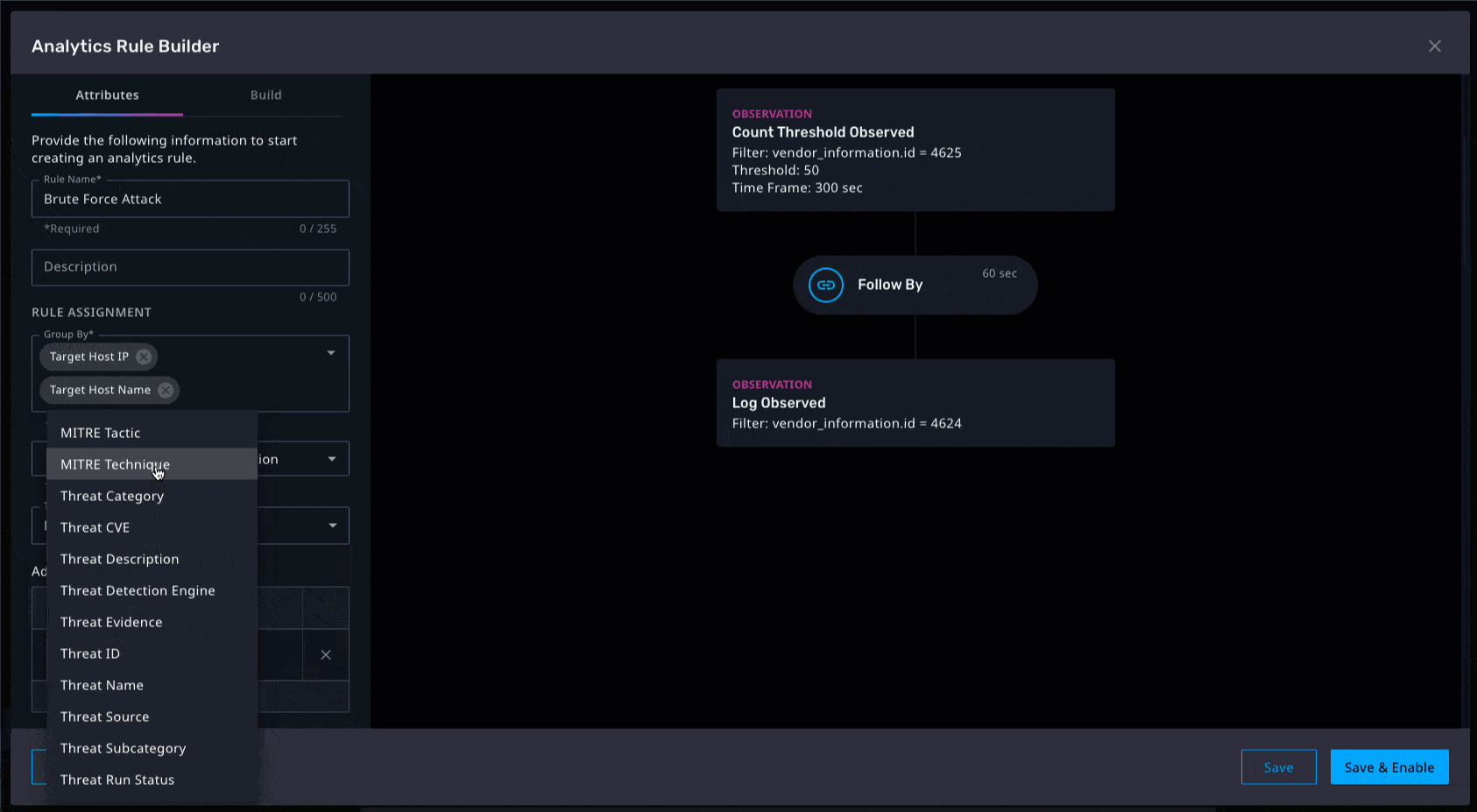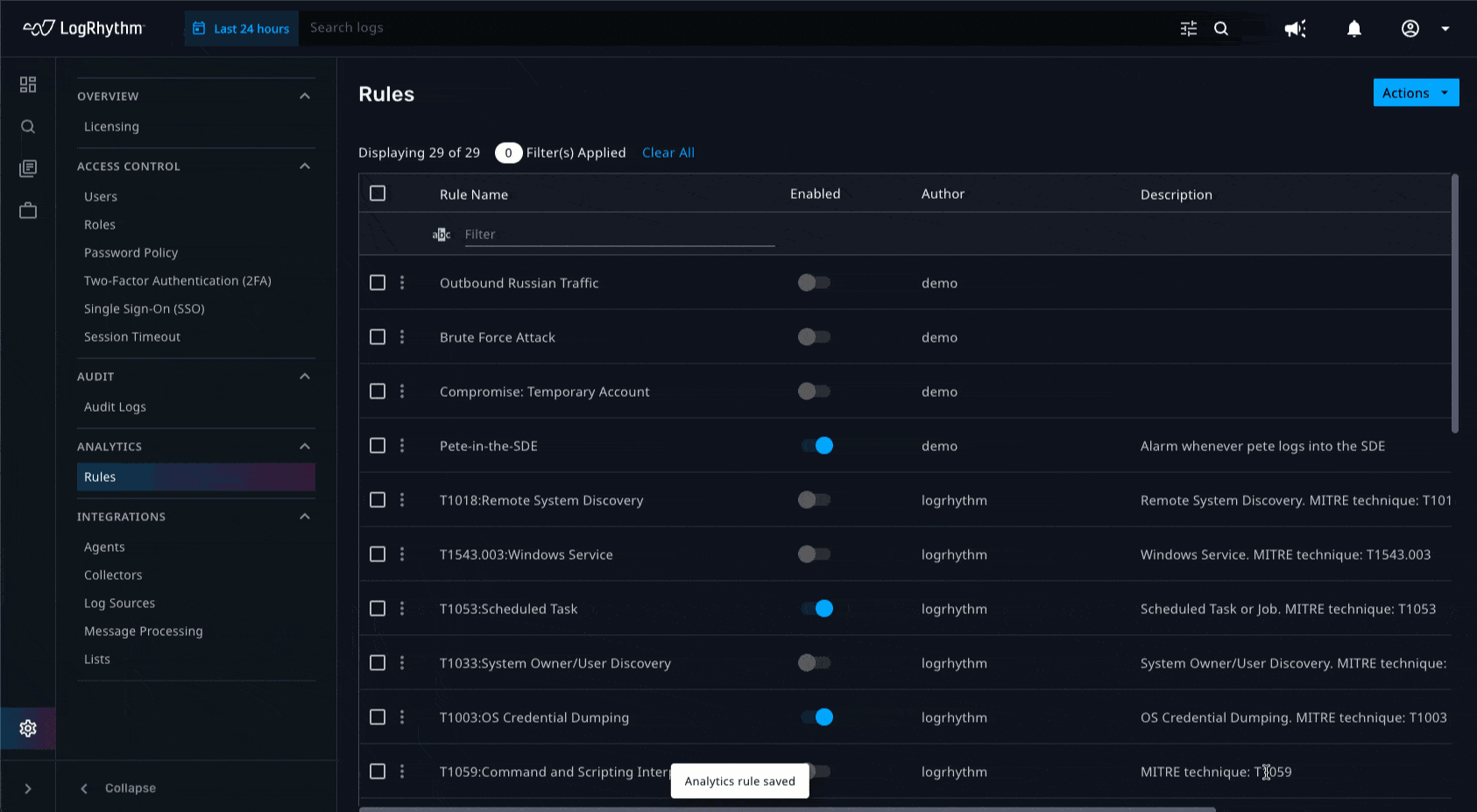
Email Notifications
Analysts cannot always be logged into the Axon dashboard to continually monitor threats that are coming in. With email notifications, analysts can automatically be notified of important events that are happening. By adding contextual information such as threat fields, threat severity, common events, and other useful metadata fields to these notifications, analysts no longer need to be logged into the system to quickly decipher what action needs to be taken.
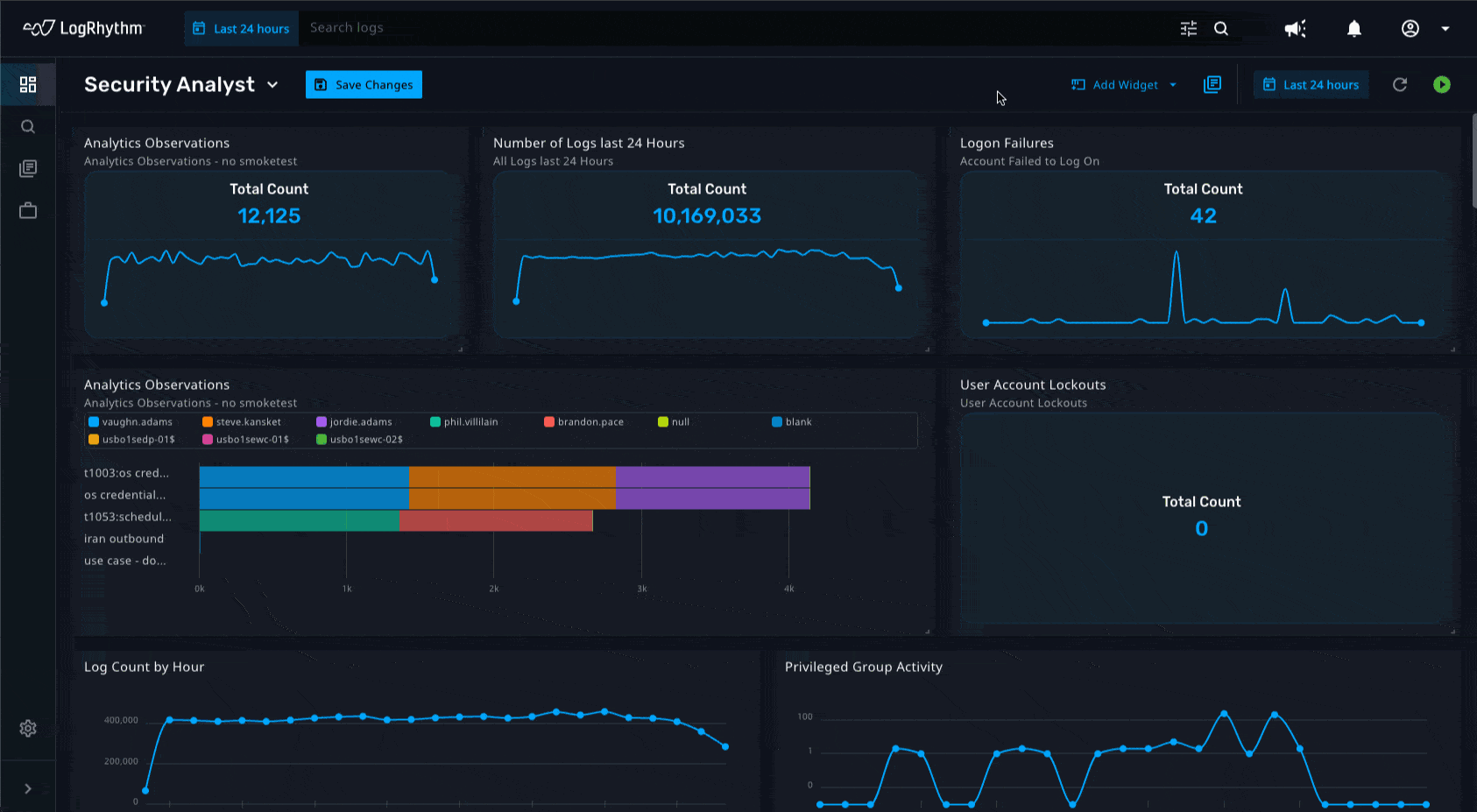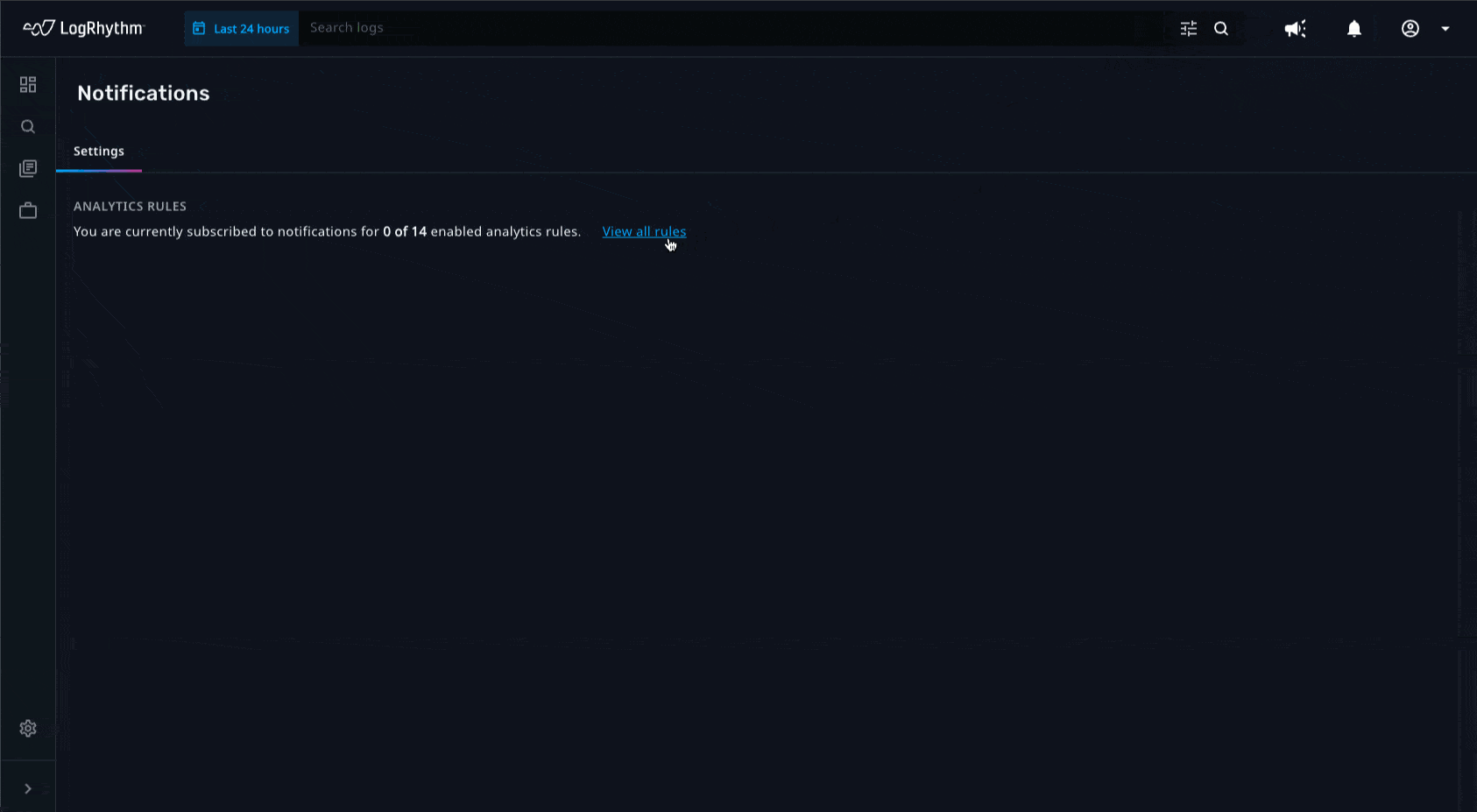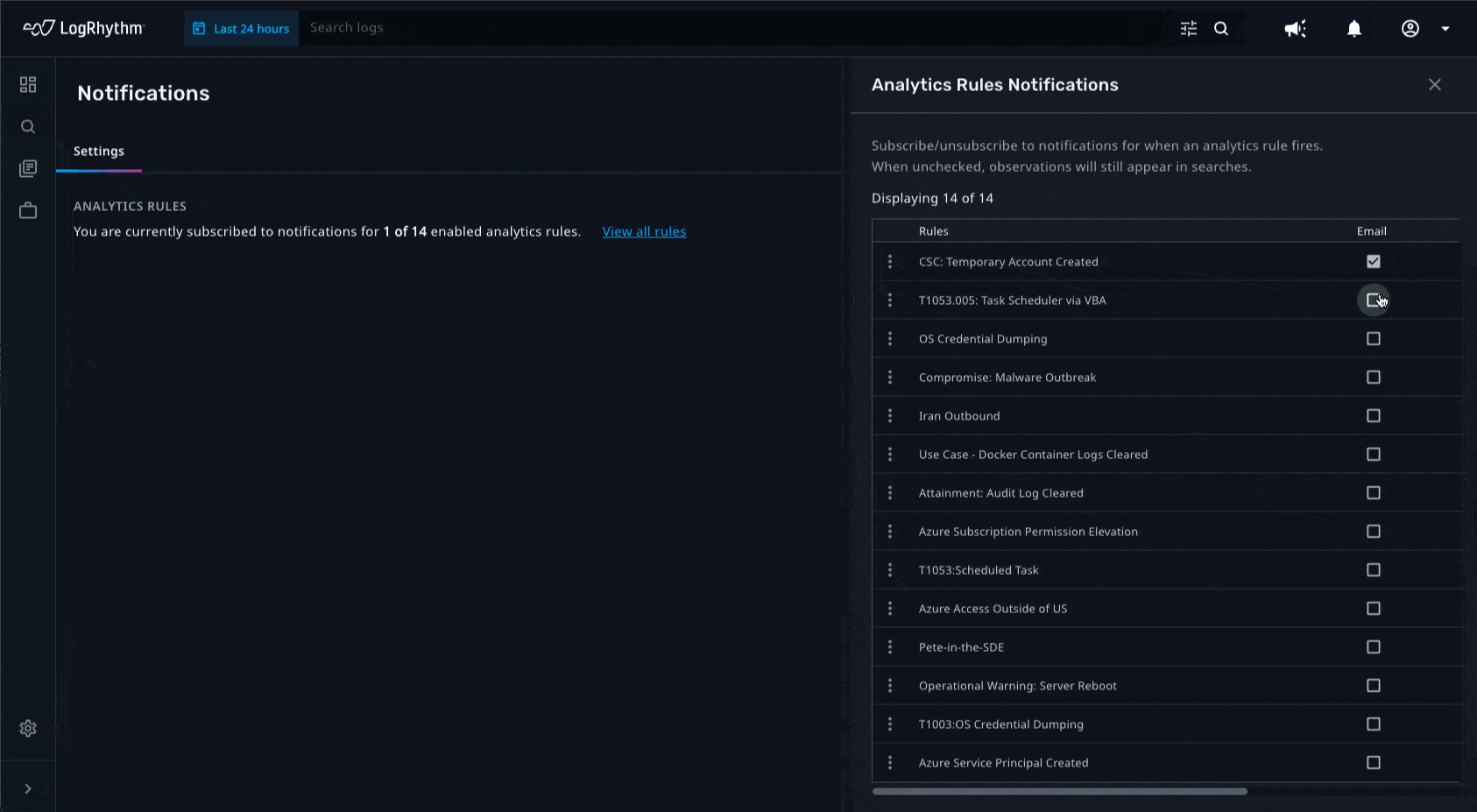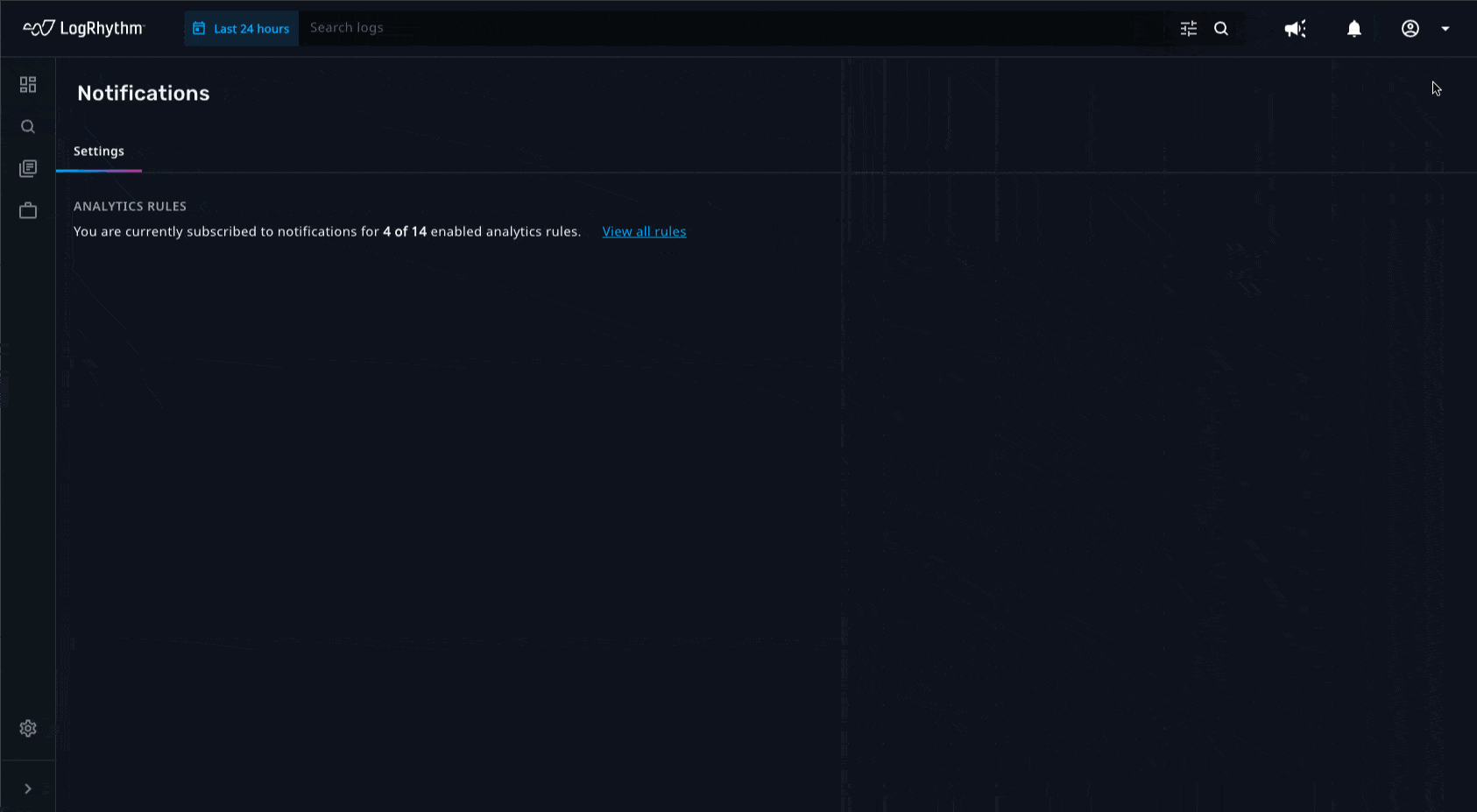
Amplified Search Capabilities
Logs come in all shapes and sizes. Our new search output shows a plain English description of the logs in the system make it easier to understand actions that have occurred. With our metadata extraction and enrichment, analysts do not need to understand the underlying log structure in order to use the data.
Axon search takes the best parts of a query driven workflow and graphical search wizard. We wanted to make it both easy and flexible by providing both options to customers to suit their preference. Our enhancements to the graphical and query driven searches as well as search guidance make it even easier.
Import/Export of Log Sources & Agent Side Log Filtering
Creating log policies from scratch is a fairly straightforward process. We wanted to make it easier for our customers and partners to build policies through the ability to share content. Analysts can export log source types and related policies into a file that we can quickly import into other tenants as needed, thus creating greater visibility through more parsing policies.
Additionally, we know analysts want to control the data collected and sometimes cannot tune all the logs that are being generated. Centrally managed through the Axon web interface, analysts can use Axon Linux or Windows Agents to specify which logs to include or which logs to exclude, gaining better control of what is being sent into the platform.
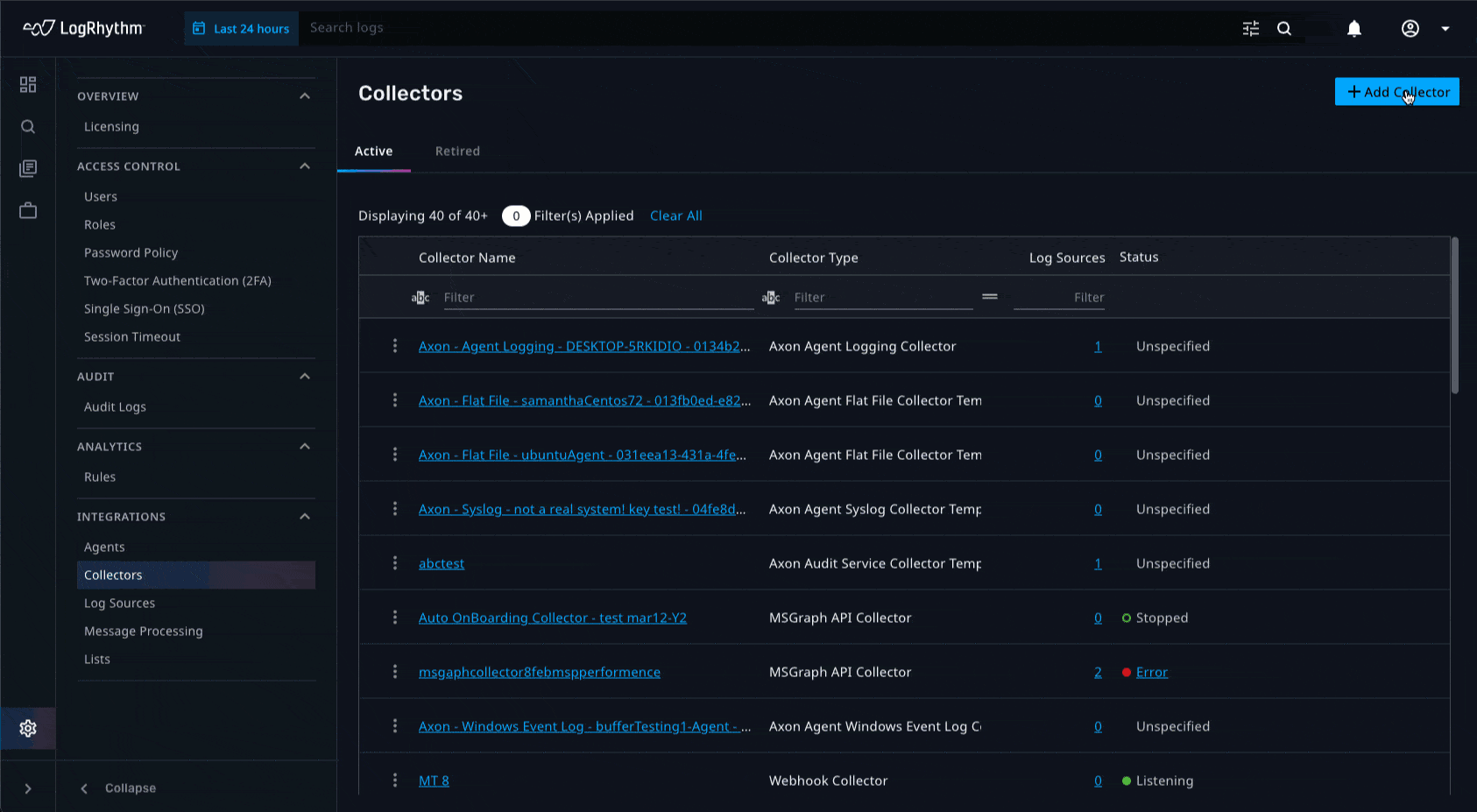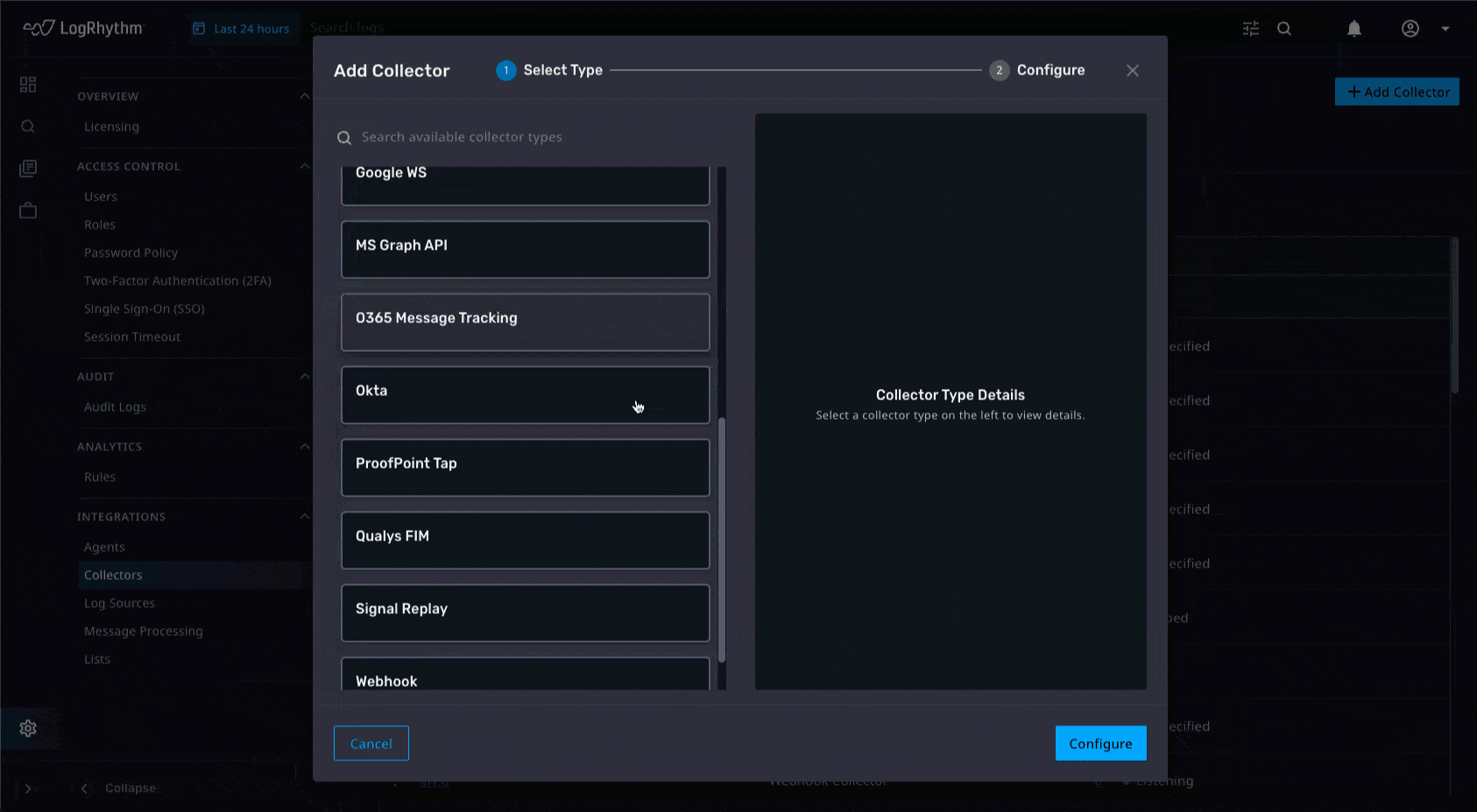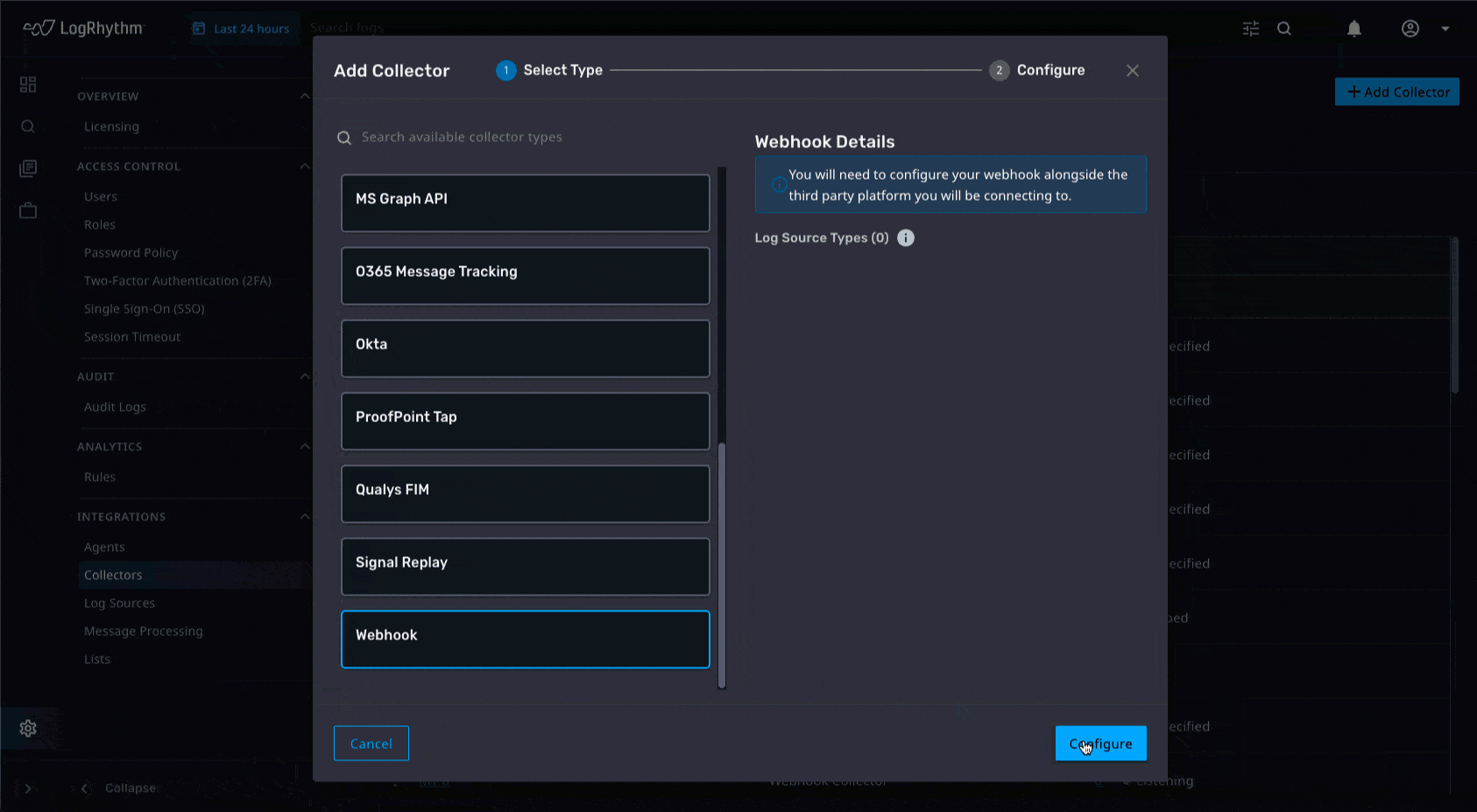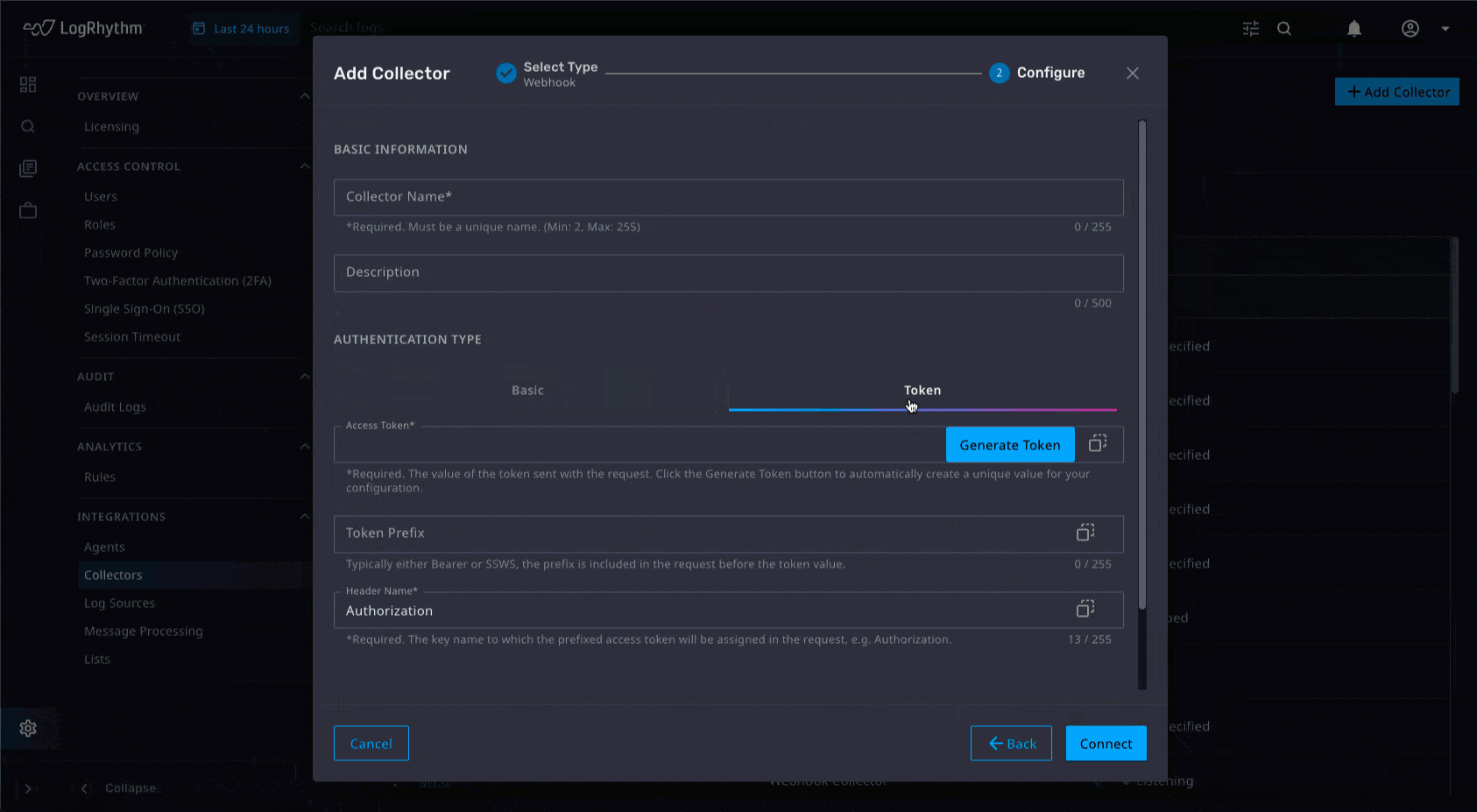
Webhook Collection and Expanded Log Collection
We’ll always be improving and enhancing collection to help our customers gain comprehensive visibility into their environment. Since an increased number of Software as a Service (SaaS) providers are utilizing Webhook, we have released a Webhook collector that supports both basic and token authentication so that data is easily sent into the platform for custom use cases, expanding visibility into SaaS environments. And just like every quarter, we’ve added new log source collection capabilities.
A Preview for Q3: Case Management
Always focused on an optimized analyst experience, we have started to build the foundation for case management. Currently, managing cases is a manual process that can be time-consuming, prone to errors, and difficult for tracking progress. To ensure greater efficiency in the security operations center (SOC), we built case management to be a centralized platform where cases can be tracked, managed, collaborated on, and monitored in real-time. With the first release of case management coming out in October 2023, analysts can create cases, view cases, and make updates and edits to those cases from the output of analytics rules. By having all the case evidence in one place across team members, you gain faster resolution times, greater efficiency, and better quality information.
We are excited to deliver our fourth consecutive quarterly release of innovations to the LogRhythm Axon platform, keeping our promise to you. Information and documentation on all these new enhancements can be found in our Release Notes, further enabling our customers to realize the full value of the Axon platform.
To learn more about LogRhythm Axon, read the product data sheet or request more information here.