AlphaSights benefits from simplified approach to data gathering with user-friendly interface that gives organizations a unified overview of their security posture LogRhythm, the company helping security teams stop breaches by turning disconnected data and signals into trustworthy insights, has been selected by AlphaSights,…
Threat Detection

AlphaSights Chooses LogRhythm Axon to Protect Mission-Critical Data with Scalable Cloud-Native Threat Detection
Tags: Cybersecurity Visibility | LogRhythm Axon | partnership | SIEM | Threat Detection | Threat Hunting
Category: Customers | General
Type: Press Releases
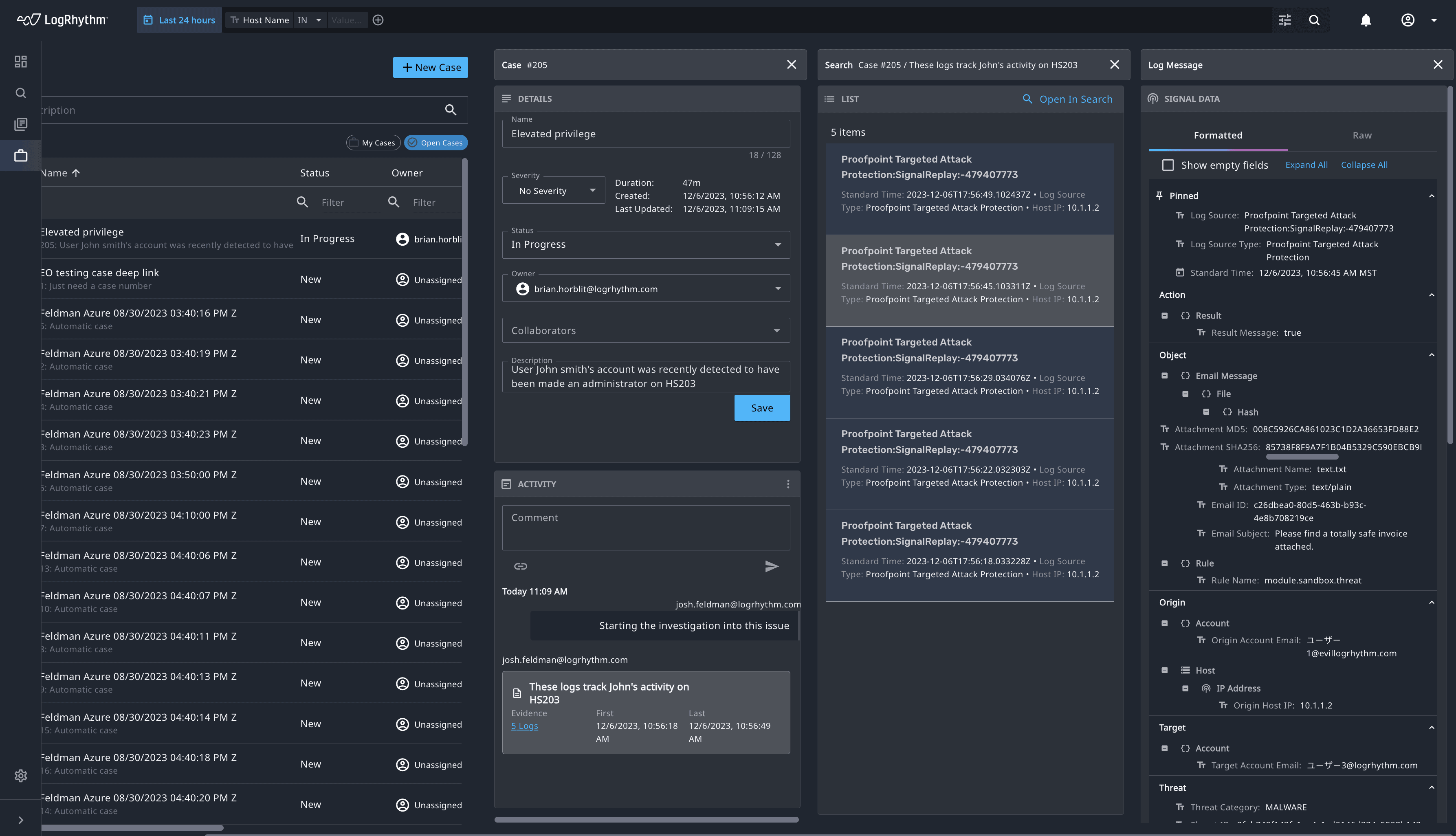
Attain Faster and More Accurate Threat Investigation with LogRhythm Axon’s Single Screen Investigation
Tags: LogRhythm Axon | SIEM | Threat Detection
Category: Product News
Type: Blog
When we built our cloud-native security information and event management (SIEM) platform, LogRhythm Axon, our goal was to make the product as efficient as possible to make the life of an analyst easier. With feature releases every two weeks, we’ve…
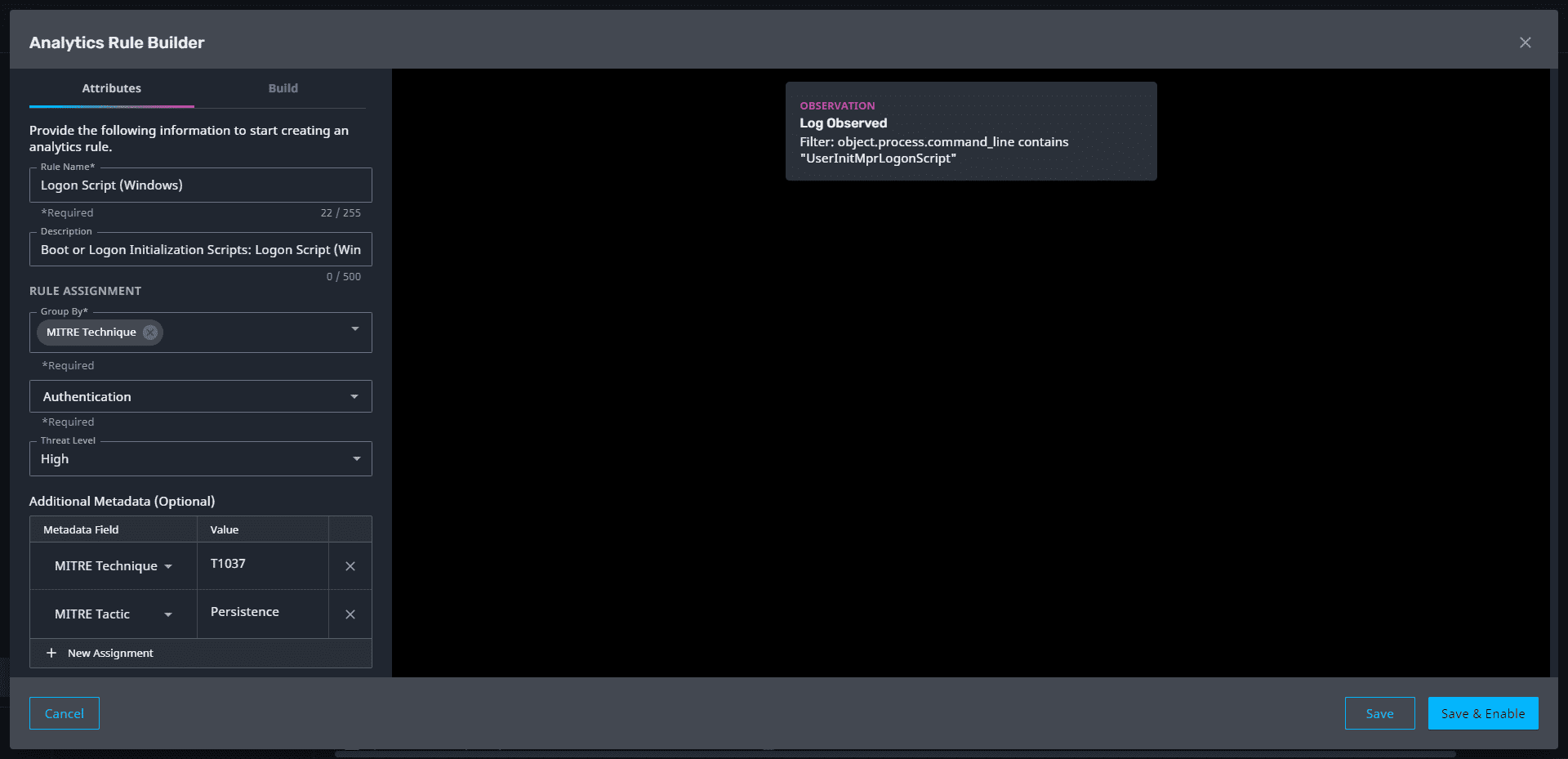
Automatically Catch Sight of Critical Threats with LogRhythm Axon
Tags: LogRhythm Axon | security analytics | Threat Detection
Category: General | Product News
Type: Blog
With the amount of data continuously feeding into a security operations platform, it is more important than ever to be able to identify the most critical threats and know immediately when those threats are triggered. With the latest LogRhythm Axon…

Improving Threat Detection Using LogRhythm SmartResponse with Lists to Monitor IOCs
Tags: SmartResponse | Threat Detection
Category: Customer Success | General
Type: Blog
As a security professional, you know all too well the need to continually improve your threat detection techniques and skill set. With today’s expanding attack surface and hackers becoming more sophisticated in their infiltration methods, building a stronger defense is…

Threat Hunting Framework: Three Steps to Translate Threat Reports into Actionable Steps
Tags: Discover Case Management Use Cases and Tips | Purple Team | Ransomware | Threat Detection | Threat Research
Category: LogRhythm Labs
Type: Blog
Thanks to Sally Vincent and Dan Kaiser from the LogRhythm Labs team for developing the process and guiding content described in this post. Threat research can be an invaluable asset to security teams when attempting to formulate a proactive stance…
