If your organization operates in an Amazon Web Services (AWS) environment, you may face a series of unique security challenges to protect sensitive data and abide by compliance mandates. To reduce risk, you need to continually mature your security operations and keep up with AWS security best practices.
In this blog, I’ll dive into common challenges security teams face, how to monitor CloudTrail and GuardDuty logs, and three AWS security use cases that you can implement for better visibility and protection across your cloud environment.
Overcoming AWS Security Challenges
With a shared responsibility model, where AWS is responsible for the security of the cloud infrastructure, the customer is responsible for securing their data and applications within the cloud. Security teams must understand their responsibilities and implement appropriate security controls.
Protecting AWS environments is challenging because it consists of multiple services, configurations, and dependencies. Especially in multi-account or multi-region deployments, security teams struggle to gain complete visibility and insights into their AWS assets and enforce security policies effectively. Addressing these challenges requires a combination of technology, processes, and expertise.
- Security teams need a way to consolidate data into one place to better understand what is happening across the environment and to easily audit log data for AWS security compliance.
- Manual processes won’t get the job done quickly and effectively and leave room for human error. To keep pace with the attack surface, security operations centers (SOCs) should leverage automation and orchestration tools to streamline security operations, such as automating security configuration management, incident response, and compliance checks.
Security teams need to adopt a proactive and holistic approach to security by leveraging best practices, streamlined processes, and trusted security partnerships to safeguard their AWS environments effectively.
Monitoring CloudTrail and AWS GuardDuty Logs
A security information and event management (SIEM) is a useful solution for security teams to centrally collect and enrich data across the environment, achieve auditing and compliance standards, and better detect, investigate, and respond to cyberthreats.
For AWS security best practices, I will dive into the importance of monitoring AWS CloudTrail and GuardDuty logs and provide examples of how to do so using LogRhythm Axon, a cloud-native SIEM platform.
Monitoring AWS CloudTrail Logs
AWS CloudTrail records API calls made on your AWS account, capturing details such as who made the request, when it was made, and the IP address from which it originated.
By logging all API calls, security teams can gain insight into who is accessing AWS resources, what actions they are performing, and where these actions originate from.
CloudTrail Auditing with LogRhythm Axon
CloudTrail provides an audit trail of all actions taken within your AWS environment. LogRhythm Axon can ingest these logs to monitor and analyze user activity, resource changes, and security events. This will help your team with:
- Forensics and Investigation: When incidents occur, CloudTrail logs help investigators trace back actions, identify the source of security breaches, and understand the context.
- Compliance and Governance: CloudTrail logs are essential for compliance audits, ensuring adherence to security policies and regulatory requirements.
By forwarding CloudTrail logs to LogRhythm Axon, you gain real-time visibility into AWS activities, enabling proactive threat detection and incident response.
Learn more about logging using CloudTrail here.
Monitoring AWS GuardDuty Logs
Amazon Guard Duty is a managed threat detection service that continuously monitors for malicious or unauthorized behavior in your AWS accounts and workloads.
There are several benefits to ingesting GuardDuty logs into a SIEM solution.
GuardDuty Auditing with LogRhythm Axon
- Threat Detection: GuardDuty analyzes network traffic, DNS data, and AWS CloudTrail logs to detect suspicious activities, compromised instances, and potential threats.
- Automated Alerts: GuardDuty generates findings based on threat intelligence and anomaly detection. These findings can be ingested by your SIEM for further analysis and alerting.
By forwarding GuardDuty logs to LogRhythm Axon, you gain real-time visibility into Suspicious AWS activities, enabling proactive threat detection and incident response.
Learn more about GuardDuty integrations here.
How LogRhythm Can Help Protect Your AWS Environment
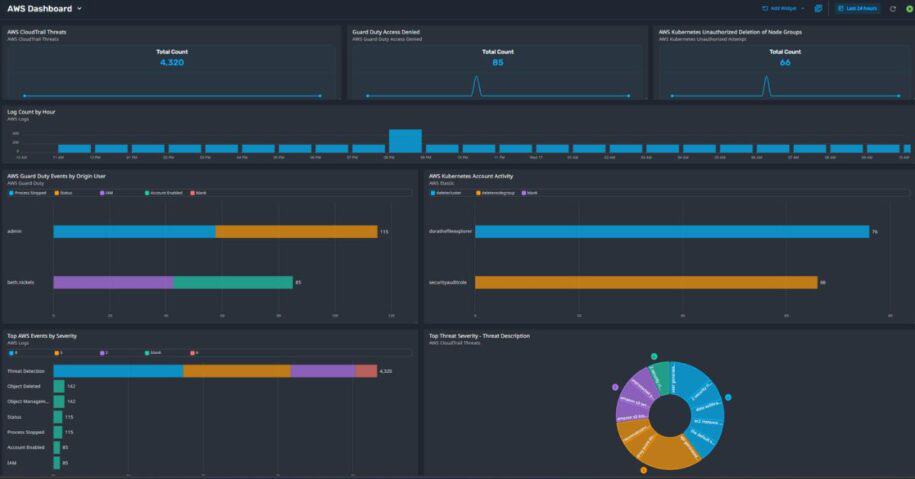
LogRhythm Axon provides seamless visualization of AWS data, including CloudTrail threats, GuardDuty events, Kubernetes activities, and more.
Leverage a Custom AWS Dashboard
Using the cloud-native SIEM, you can take advantage of an AWS dashboard to quickly understand user actions — such as enabling accounts, deleting nodes, and managing users — enhancing your AWS security posture.
Three AWS Alarm Use Cases
Let’s explore three AWS alarm use cases that can help you improve AWS security monitoring and bolster your defenses.
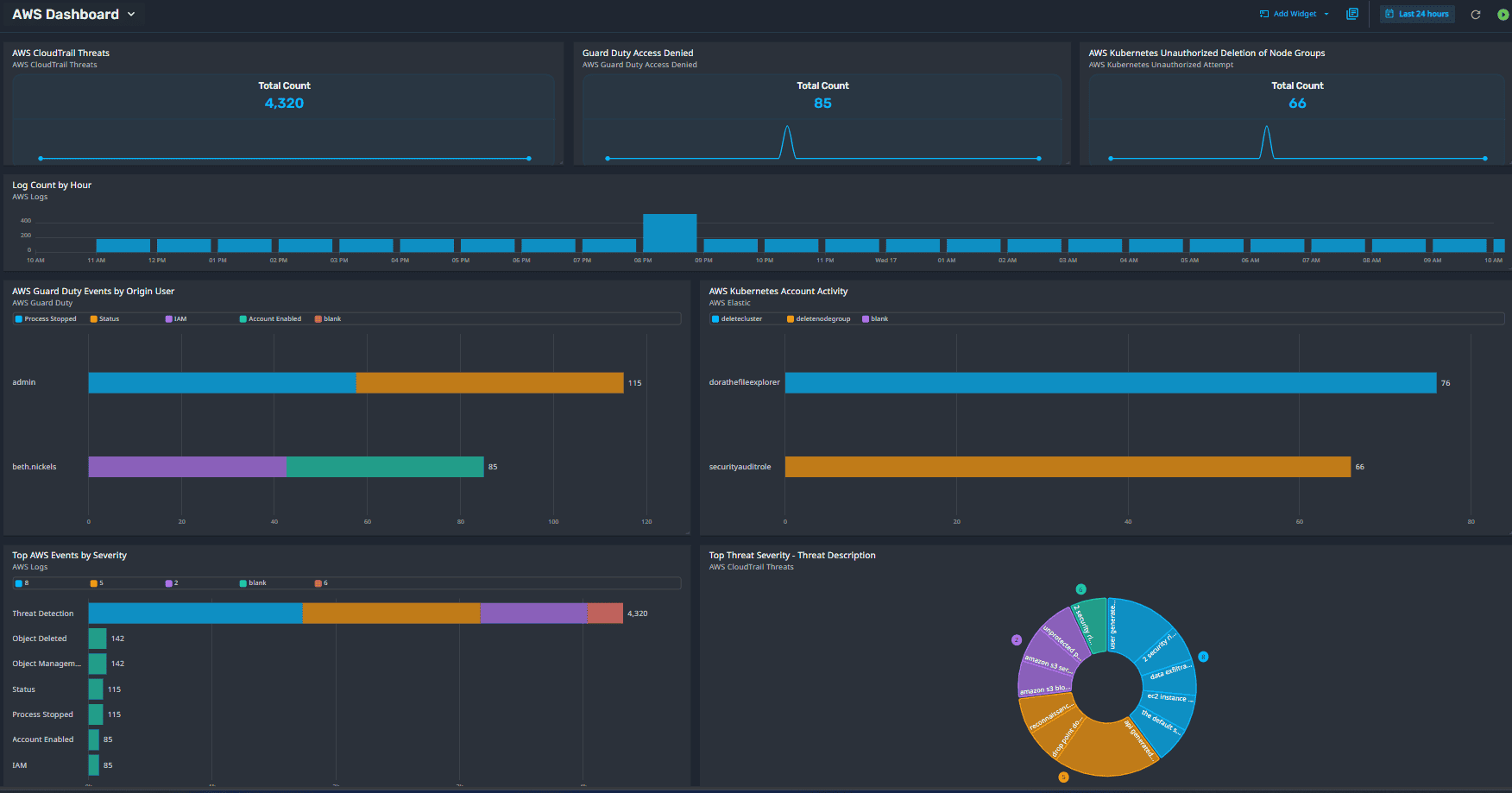
1. AWS GuardDuty Access Denied
When GuardDuty detects an unauthorized or suspicious activity, it generates an event log. In the following example, explore a scenario where Access is Denied and how you can detect this potential threat.
Log Sample:
“eventTime”: “2024-04-17T00:50:00.016097Z”,
“eventSource”: “guardduty.amazonaws.com”,
“eventName”: “EnableOrganizationAdminAccount”, – User Is Attempting to Enable an Admin Account
“awsRegion”: “us-xxxx-x”,
“sourceIPAddress”: “x.x.x.x”,
“userAgent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36”,
“errorCode”: “AccessDenied”,
“errorMessage”: “User is not authorized to perform this action.”, Access is Denied
“requestParameters”: {
“adminAccountId”: “xxxxxxxxxxxx”
You can detect this threat in LogRhythm Axon and have a Case Created to investigate it further. Below is an example of the rule block that will generate an Alarm for this activity.
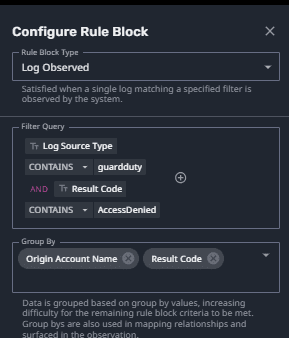
In Figure 3, you can observe details of what tracking this activity looks like using LogRhythm Axon’s Case Management and Single Screen Investigation workflow. This feature helps you drill down further and shows contextual insights across logs, Observations, security analytics, and raw metadata — all in one view.
2. AWS Kubernetes Unauthorized Deletion Attempt
Unauthorized attempts in Amazon Elastic Kubernetes Service (EKS) can occur when an entity or user tries to access resources without proper authorization. In the example below, explore a scenario that involves an unauthorized attempt and how you can detect it.
Log Sample:
“eks.amazonaws.com”,
“eventName”: “DeleteNodegroup”,
“awsRegion”: “us-xxx-x”,
“sourceIPAddress”: “x.x.x.x”,
“userAgent”: “eks-security.audit.amazonaws.com”,
“errorCode”: “UnauthorizedAttempt”, Unauthorized Attempt error code
“errorMessage”: “User attempted unauthorized deletion of a node group“, – Error Message
Here is an example of the rule block that will generate an Alarm for this activity.
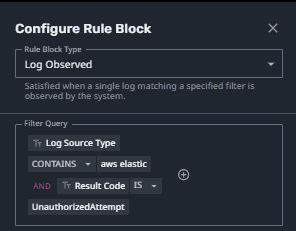
Security analysts can dive deeper into the Case to investigate this threat. Figure 5 shows key insights into who attempted the unauthorized deletion of the host where the request originated.
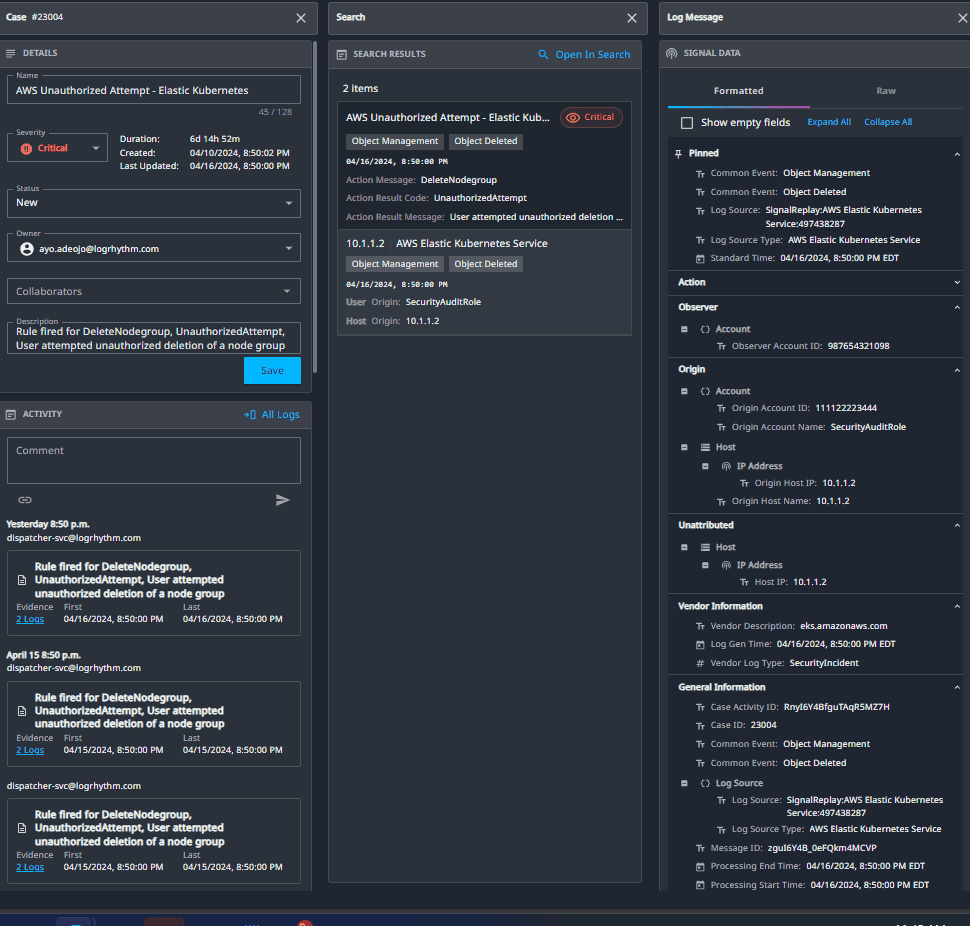
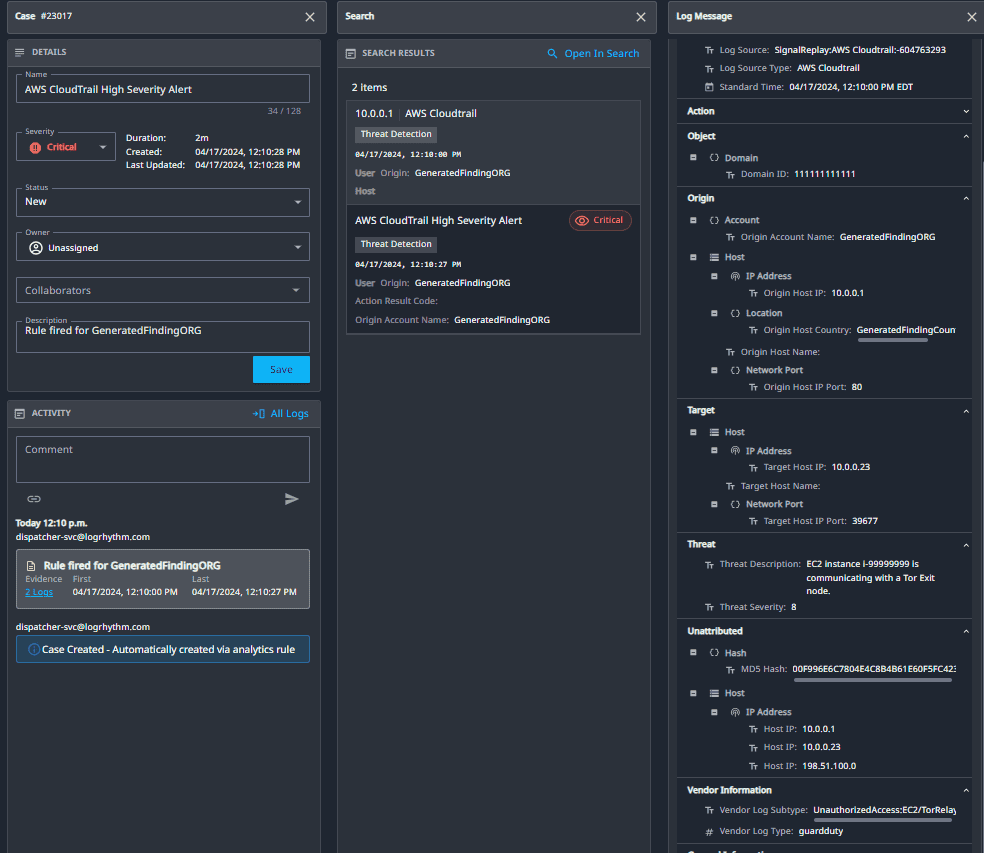
3. AWS CloudTrail High-Severity Alerts
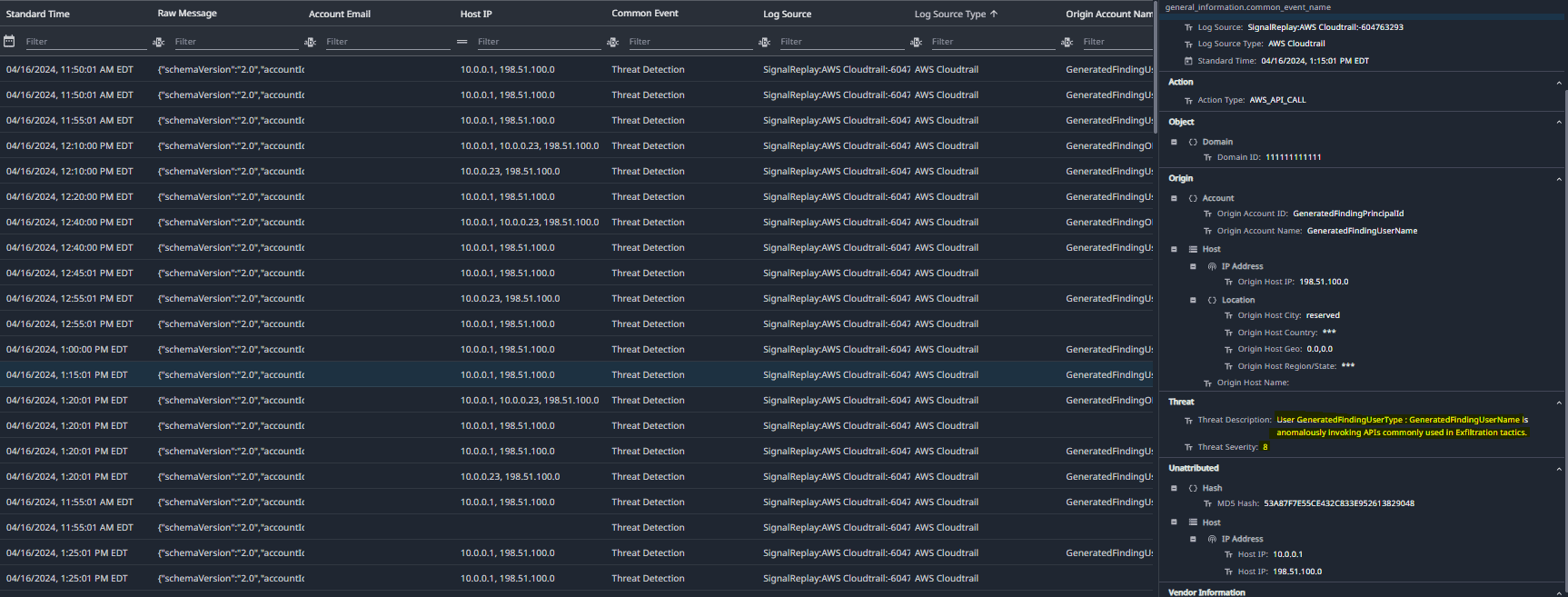
LogRhythm Axon employs seamless and innovative parsing techniques for all ingested events. Specifically, when it comes to AWS CloudTrail logs, we focus on identifying detected threats. These logs are meticulously labeled and assigned threat severities on a scale of 0 to 10. Leveraging this severity information, you can set up alarms to trigger for high-severity CloudTrail alerts.
Figure 6 shows an example of formatting AWS CloudTrail logs as well as assigning a Threat Severity.
You can alarm on this in LogRhythm Axon and have a Case Created. See the rule block in Figure 7.
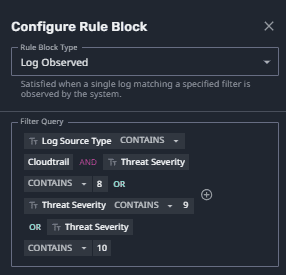
Here are Case details below, you can analyze relevant meta data such as the user or host involved.
Streamline Your AWS Security Monitoring
In the dynamic landscape of cloud computing, robust AWS security best practices are non-negotiable. By following these best practices, organizations can strengthen the security of their AWS environments and better protect their data, applications, and infrastructure from security threats and vulnerabilities.
Cybersecurity is a challenging job, and there is a shortage of cybersecurity professionals with expertise in cloud security and AWS. You may face challenges in hiring and retaining skilled personnel to effectively protect AWS environments.
Integrating LogRhythm Axon into your AWS environment helps you gain the ability to detect threats and visualize all your data in one location for an easier security and compliance experience.
To learn more about how LogRhythm can improve your AWS security monitoring challenges, request more information.
Related Resources
Enjoy these additional reads for protecting against AWS-related cyberthreats.