It’s easy to get lost in all the noise when trying to surface and make sense of potential threats to your organization’s network. Keeping your environment safe is a constant struggle with bad actors continuously looking for new ways to gain an edge. Fortunately, LogRhythm is making it even easier for customers to detect and respond to threats with our network detection and response (NDR) solution.
For our latest LogRhythm NDR release, we listened to customer feedback and focused on key areas of value, including enhancing the analyst workflow, improving detection, and platform improvements. This is part of our continued commitment to our customers — to deliver regularly releases new features and bringing quality products to market. Read on to learn more about our newest LogRhythm NDR features.
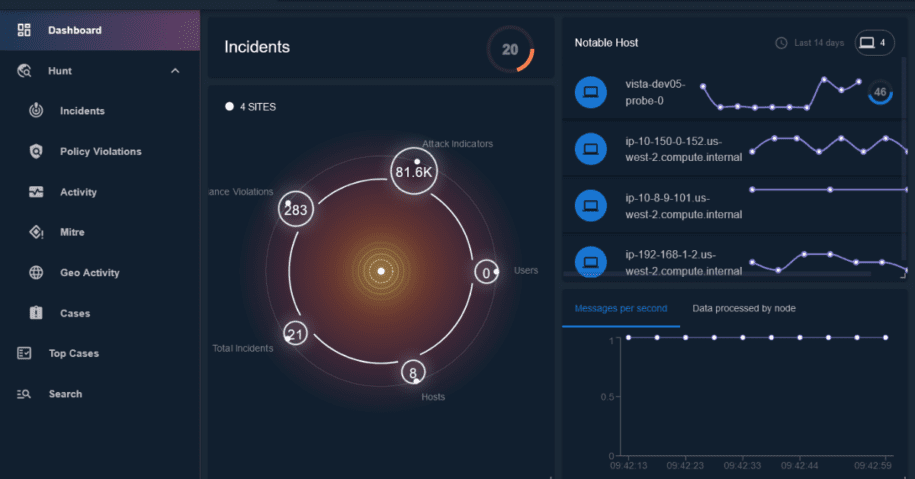
Gain greater insight with the updated LogRhythm NDR user interface
We know how critical the analyst experience is. That’s why our team dedicated resources to help ease the analyst workflow with a new and refreshed user interface. The LogRhythm NDR UI now features a sleek and elegant design along with a color pallet that ties into our newly released LogRhythm Axon, a cloud-native Software-as-a-Service (SaaS) security operations platform. With the latest LogRhythm NDR release, we are starting to roll out updates to our high touch pages in order to help you respond quicker and do your job more efficiently.
For example, the LogRhythm NDR dashboard more prominently features the MITRE ATT&CK® framework widget so you can prioritize response activities and surface more accurate threats. The UI also offers an enhanced search bar and navigation bar and relocated the notable users and notable hosts modules to a more prominent position. This helps you determine what hosts or users in your environment are most important or deserve immediate attention.
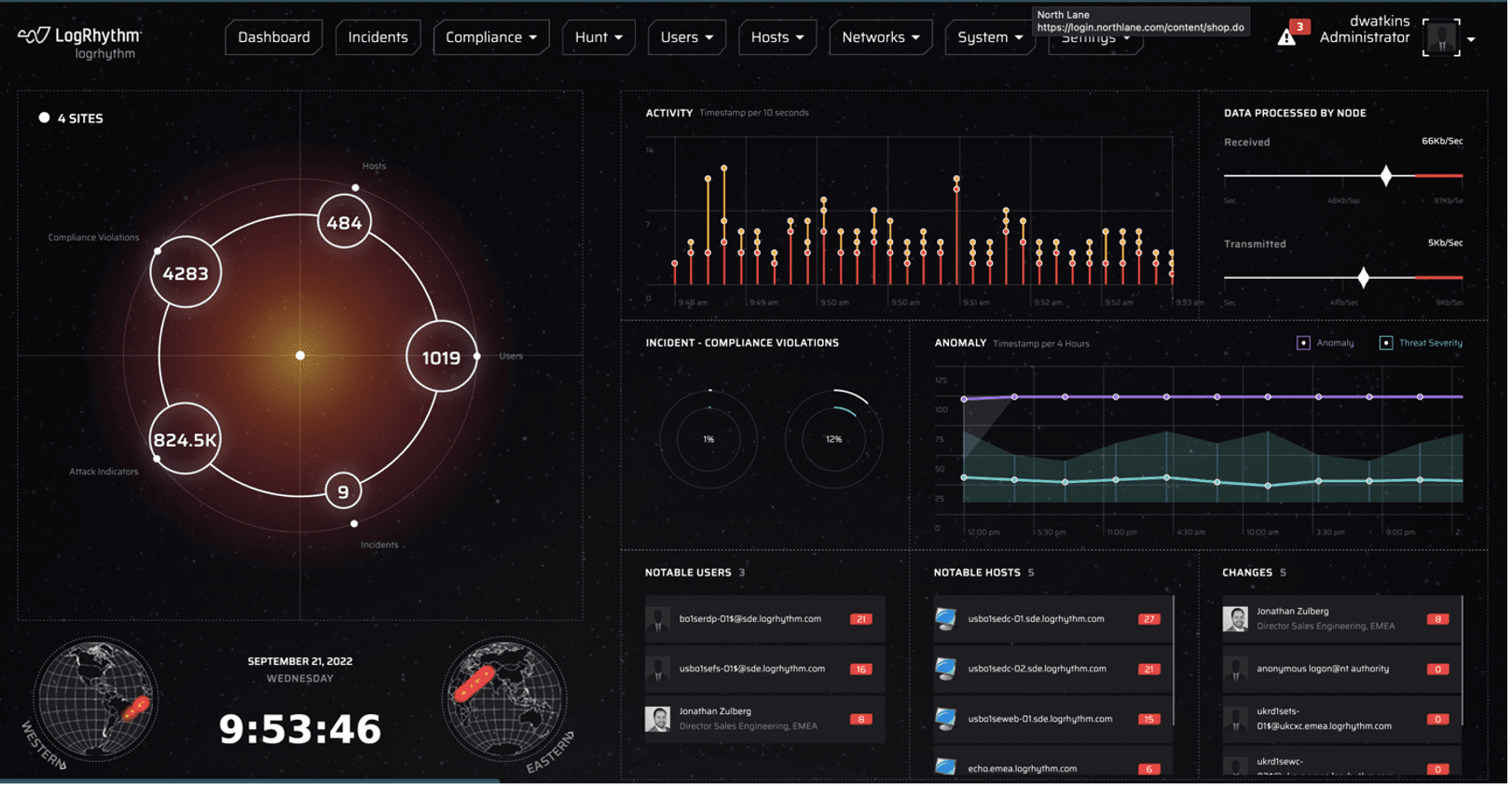
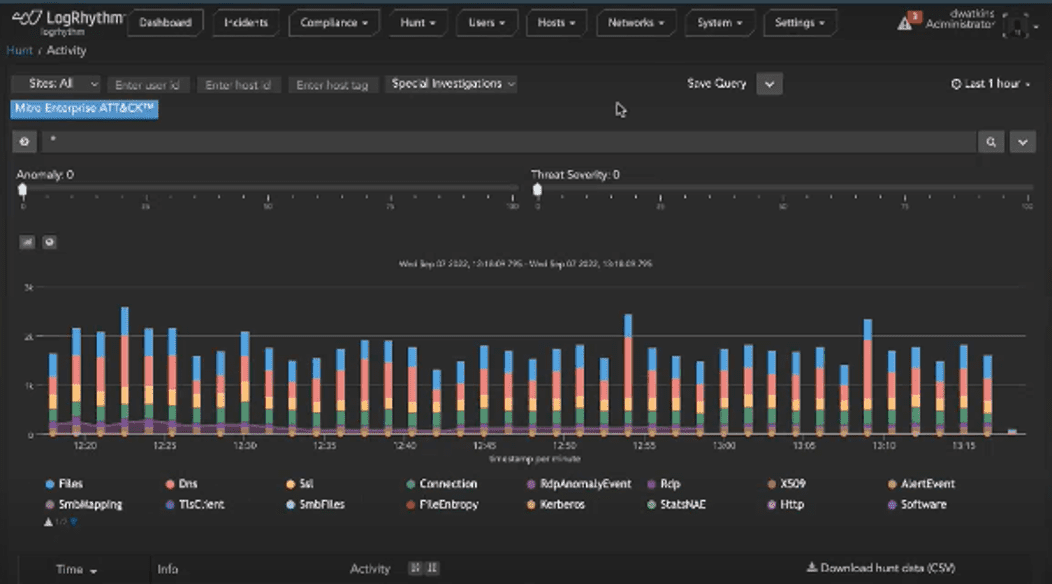
The LogRhythm NDR Hunt Activity page also features similar functionality, but with a more modern UI.
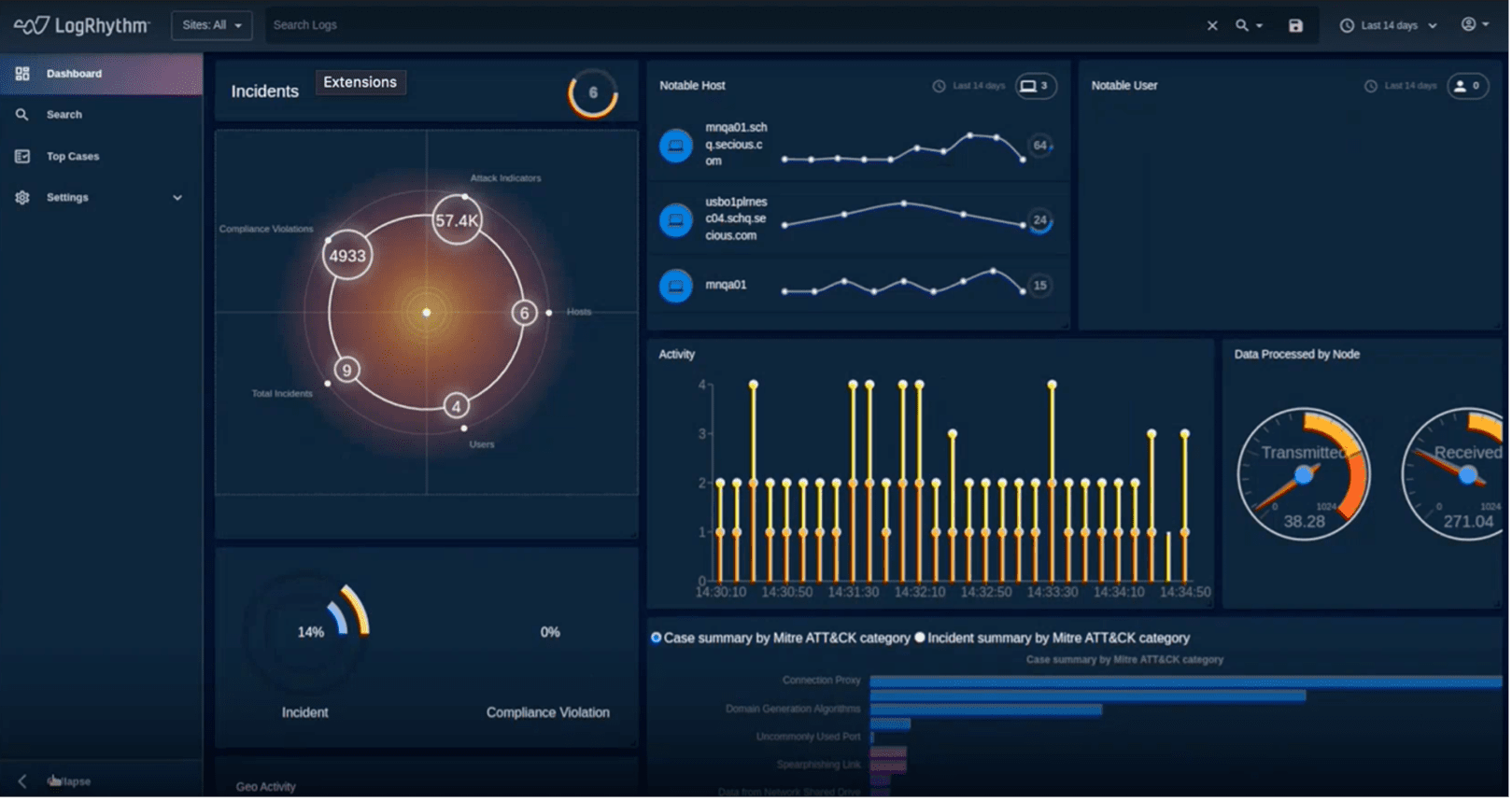
The team also updated the Incident Summary page by consolidating the summary view. The Summary page reveals the total number of incidents and severity level of severity of the incidents. Now you can drill down, expand, and collapse your data and sort items by criticality to support your investigations. This update reduces noise and helps you focus on the incidents that are most important.
That’s not all. The new UI lets you filter things that are of interest. For example, you can group incidents by source IP address. The UI also keeps you within the same context, so you aren’t moving from page to page. This modern workflow is especially useful when managing issues at the incident level.
Manage your workflow with an Allow list
Another enhancement to the analyst workflow is that LogRhythm NDR now enables you to create an “Allow” list from the policy management page. This feature comes as a response to a significant demand through customer requests.
If an incident surfaces, your team may already know about it. With the Allow list feature, you can whitelist the activity of a host or user that you don’t want to see. This helps save time from closing out each incident and improves your efficiency.
Ingest NetFlow data
Beyond analyst workflow, the LogRhythm NDR release also features detection improvements. LogRhythm NDR allows you to ingest data from NetFlow, a network protocol system by Cisco. We created an integration where LogRhythm NDR can now ingest NetFlow traffic and take it into account the models and identify malicious behavior from that traffic. This feature gives you greater awareness about the potential threats in your network, as well as the ability to detect and respond to those threats.
Qualify intrusion detection system alerts
While detecting network issues is important, understanding exactly what you are dealing with is even more crucial. As part of another detection capability, LogRhythm NDR now lets you use Vulnerability Scanner Data to help qualify intrusion detection system (IDS) alerts. Vulnerability scans search your network and provides a logged summary of alerts for you to act on. The data from the scans now help you eliminate false positives and elevate true positives as highly qualified incidents.
Improve network visibility with Case Definition
There’s no question that having greater network visibility will alert your team to incidents faster. But often you want to know more about an incident and its origin. That’s why LogRhythm NDR added the new Case Definition feature based on the IDS rule of indicators of compromise (IOC) to map to ransomware. This gives your analysts better visibility to understand where threats are being generated from.
Our latest LogRhythm NDR release is just the tip of the iceberg for more exciting things to come. For more information about LogRhythm NDR, read our data sheet or schedule a demo.