LogRhythm Labs has gathered up the indicators of compromise (IOCs) from CISA, Volexity, and FireEye associated with the recent SolarWinds supply chain attack and made them available in a GitHub repository for your convenience. Feel free to download and import the IOC files into your LogRhythm deployment for investigations and real-time analytics.
Please note that new information on this advanced persistent threat (APT) activity will likely be released for weeks, if not months, given the scope of the attack. Although we will occasionally update our GitHub repository, we cannot guarantee the timeliness or accuracy of the information released by other parties. We advise you to review the sources discussed in this article on your own for the most updated information. In this blog post, we discuss how these IOCs were extracted and the threat hunting opportunities within the LogRhythm NextGen SIEM Platform.
TL;DR
Intel to Detect Indicators of Compromise
FireEye recently reported on a compromise involving a supply chain attack using SolarWinds. This report comes on the heels of FireEye recently disclosing that they too have been compromised by a threat actor. FireEye published IOCs that we shared along with details on how to use them in LogRhythm here.
Keep reading to learn how to apply the threat intelligence shared by FireEye, CISA, and Volexity to threat hunt for adversarial activity in your environment.
FireEye Sunburst Countermeasures GitHub Repository
FireEye’s “Sunburst Countermeasures” GitHub repository contains a list of IOCs. The following are ways you can use the IOCs in your LogRhythm deployment.
All-snort.rules
If you are running Snort in your environment and bringing in the logs to your SIEM, you can use the list here against the ThreatName field to search, event, or alert for occurrences of the malware in your environment.
Please see Appendix A for the regular expression used to extract the threat name from the Snort rules.
Indicator_Release Files
There are two indicator_release files in the GitHub repository containing hashes and network indicators. We will walk through extracting the IOCs from one of the files with Excel and the other using SED.
Indicator_Release_Hashes.csv
Save the file locally and use Excel to open the file to use in a LogRhythm list.
- Under the appropriate column (SHA256, SHA1, MD5), select the hashes to copy to the LogRhythm list.
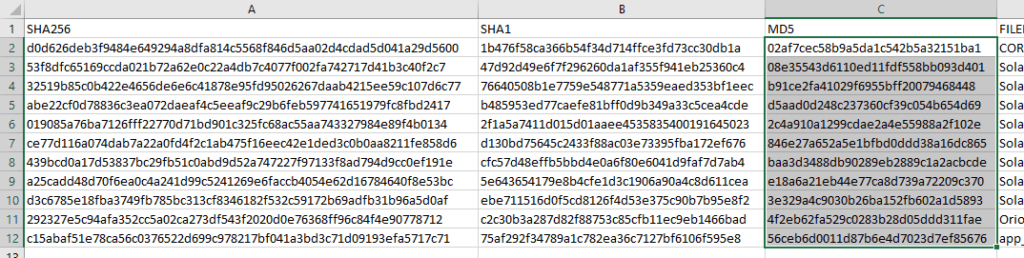
- Copy selected hashes and paste them into Notepad.
- Save the Notepad file as something like “FE_SW_Hashes.txt”
- In the LogRhythm Client Console, select “List Manager”
- Create a new general value list named something like “FE_SW_Hashes”
- In the “List Items” tab, select “Import Items”, and import the text file you saved earlier.
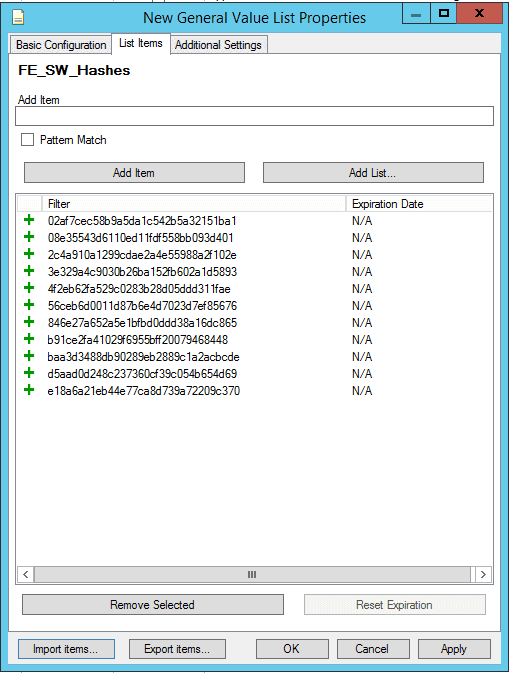
- Click the “Additional Settings” tab and place a checkmark in “Hash”.
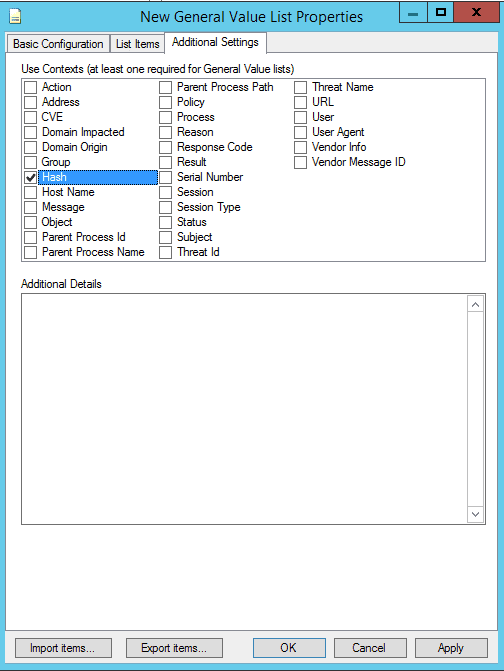
- Click “OK” when done.
Indicator_Release_NBIs.csv
- Save the file locally and use this “one liner” to extract the domain names to be used in a list.
- Import the list as a pattern match into the LogRhythm SIEM.
- Use the LogRhythm SIEM and list to search fields that contain domain name information.
Please see Appendix A for the sed command used to extract the domain names from Indicator_Release_NBIs.csv.
Cybersecurity and Infrastructure Security Agency (CISA) STIX Feed
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also released an alert regarding the APT activity related to the SolarWinds supply chain compromise. The alert includes a feed of IOCs in Structured Threat Information Expression (STIX™) format. The STIX feed is convenient for LogRhythm customers because they can leverage LogRhythm’s Threat Intelligence Service to ingest the IOCs, create LogRhythm lists for each type of IOC, and regularly check the feed for updates. Note: You must run the Threat Intelligence Service Manager as administrator. Otherwise, you will get the error message: Exception while saving provider details for Provider [feed name]: Key not found Parameter name: key.
It’s easy to pull the CISA IOCs by adding a custom STIX feed to the Threat Intelligence Service and pasting the feed’s URL into the STIX Indicator Endpoint field:
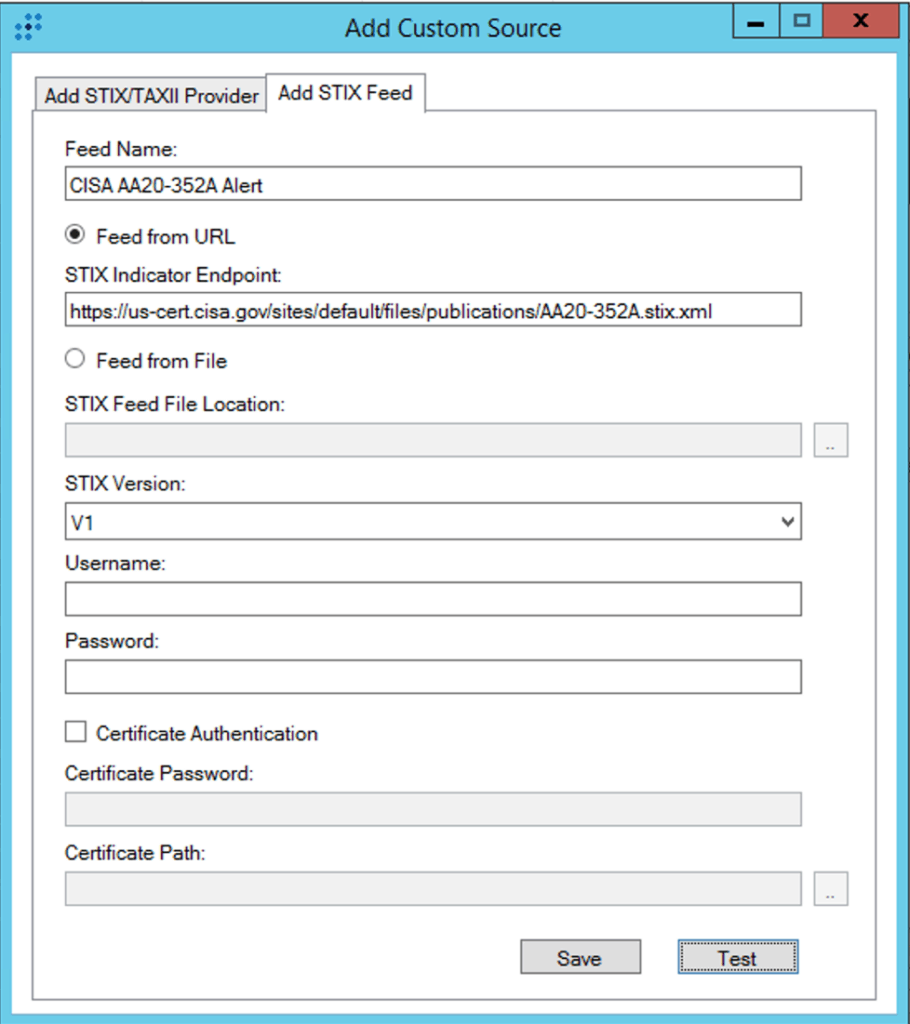
Once the feed is enabled, it will configure by default to update every 12 hours. You can click the Download Now button to immediately download the feed data.
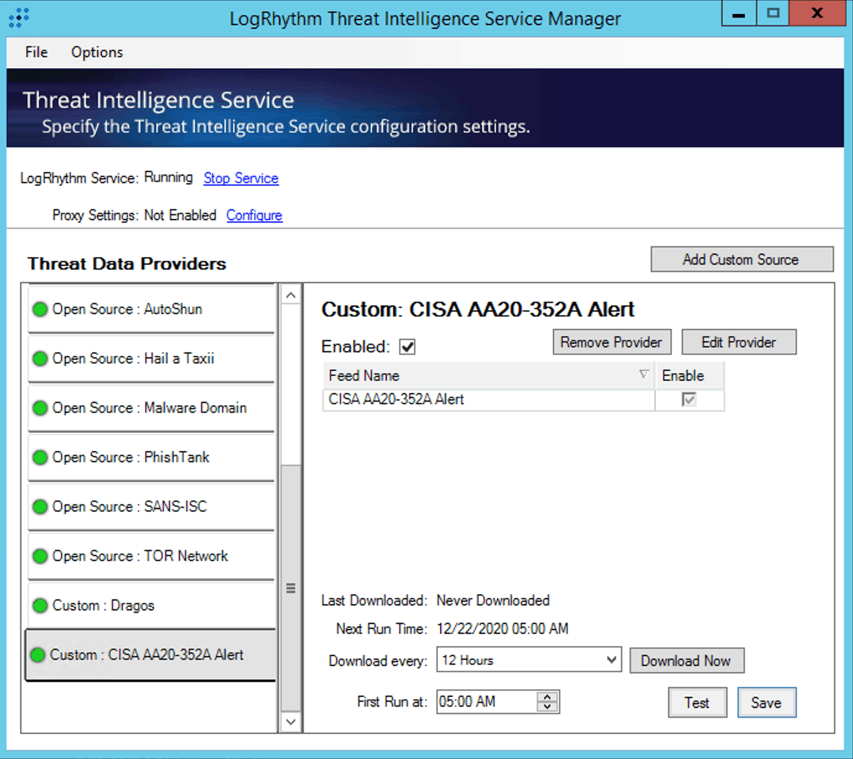
The Threat Intelligence Service automatically creates LogRhythm lists corresponding to each of the IOC types provided in the feed and configures the list to import any updates resulting from the feed’s periodic check.
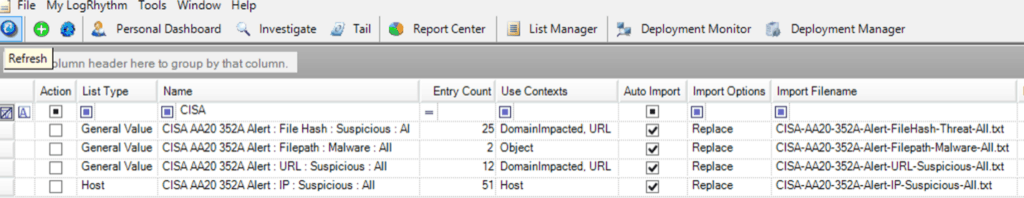
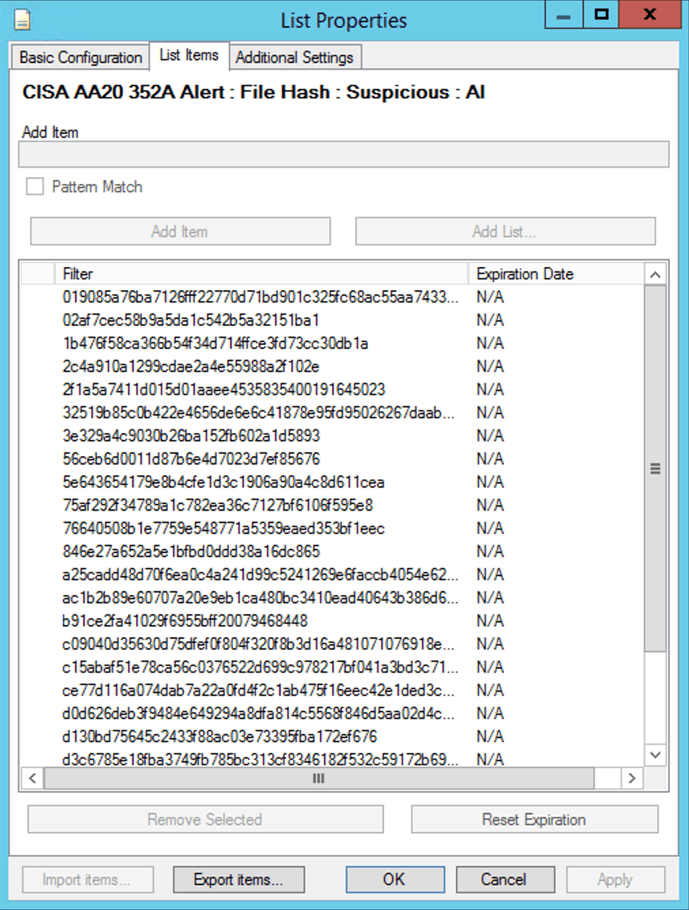
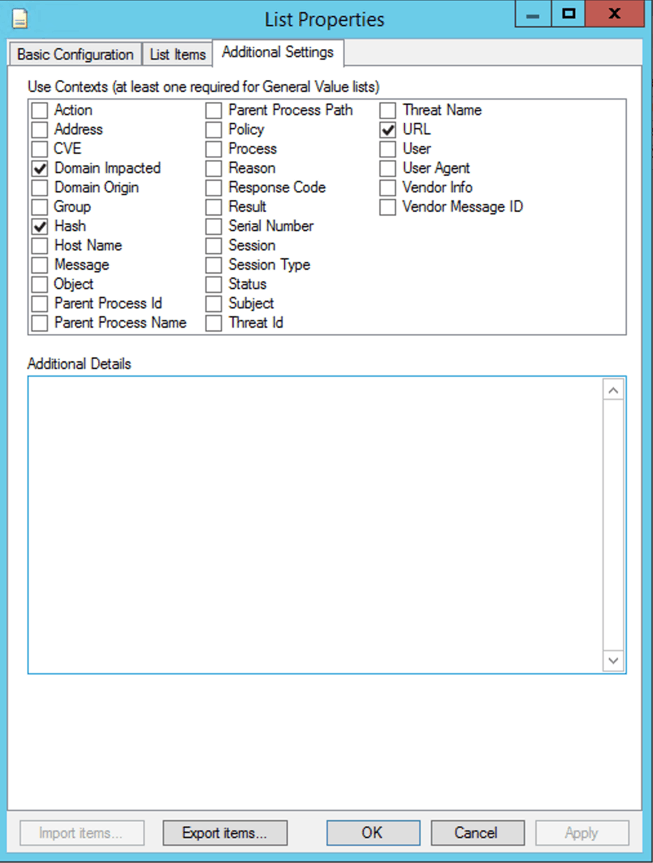
You can use the lists for retroactive threat hunts or as criteria for AI Engine rules. Note that you may need to confirm the Use Contexts of the list to ensure you can search for them against the metadata fields you require. In this case, we need to add the Use Context of Hash manually.
Locating CNAME Responses to DNS Queries
The CISA and Volexity reports mention that organizations running the compromised builds of Orion will likely see DNS queries originating from their Orion server for avsvmcloud[.]com. Of particular interest is whether the queries produced CNAME responses. Per CISA: “If additional Canonical Name record (CNAME) resolutions associated with the avsvmcloud[.]com domain are observed, possible additional adversary action leveraging the back door has occurred.” [1]
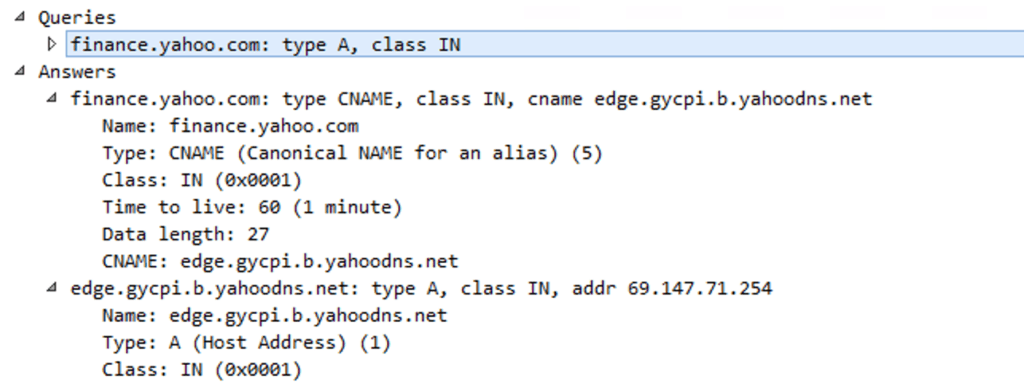
How do you find CNAME responses to DNS queries? The exact answer will depend on the log source type and how it’s parsed. Let’s look at an example using Microsoft Sysmon logging a query to finance.yahoo.com. Below is a screen shot from Wireshark showing that a DNS query for finance.yahoo.com returned a CNAME record (an alias to another DNS name) to edge.gycpi.b.yahoodns.net as well as its associated IP address 69.147.71.254.
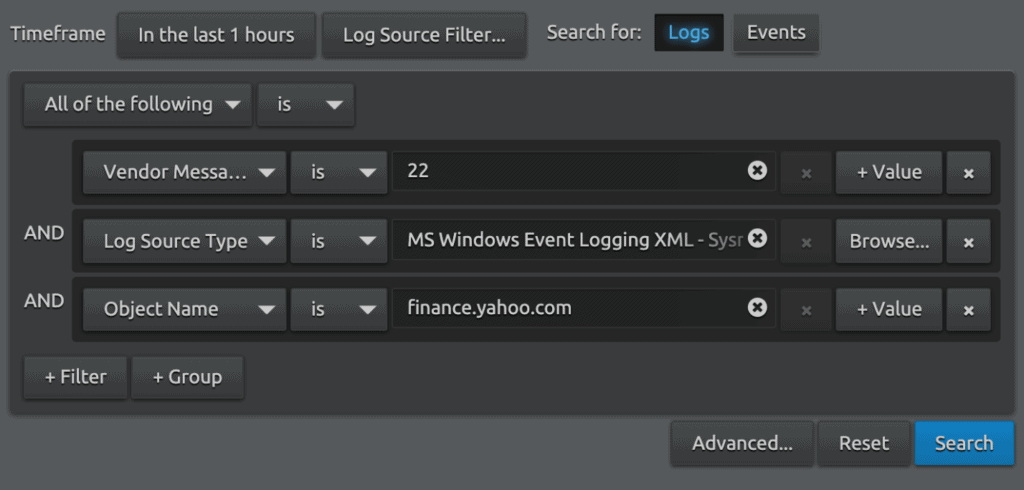
DNS queries are logged by Microsoft Sysmon as Event ID 22. We can search for the query in LogRhythm with the following criteria:
The search returns the following log:
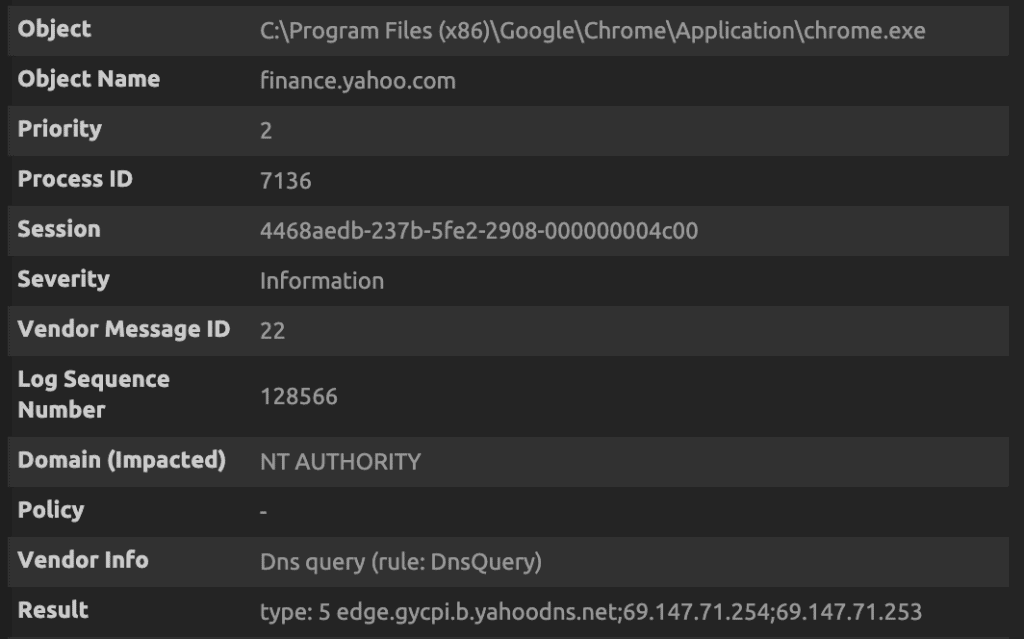
Note that the Sysmon log includes the process that initiated the DNS query (chrome.exe), the query that was performed (finance.yahoo.com), and the response (type: 5 edge.gycpi.b.yahoodns.net;69.147.71.254;69.147.71.253). The response type of 5 indicates that this is a CNAME response.
If your Orion server had Microsoft Sysmon installed and was logging DNS queries, you could perform the same search for the Object Name of avsvmcloud[.]com and review the logs for type 5 responses.
Leverage Volexity’s Observations in Your SIEM
Volexity recently published a blog that references “Dark Halo” as the threat actor related to the SolarWinds compromise. Their blog focuses on the attacker’s goal, and methods used to achieve those goals, which ultimately was exfiltration of email. Dark Halo was observed using mostly PowerShell commands. The following are methods you can use to search or alert in your SIEM based on Volexity’s observations.
PowerShell and Command Line Logging
In order to use the references of PowerShell and Command Line logging to search in the LogRhythm SIEM, you will need to configure your endpoint logging first. It’s never too late to configure your endpoint logging, so if you haven’t yet, we highly recommend that you do so. You can learn more about our PowerShell guidance and how to detect PowerShell usage here in our MITRE ATT&CK Module. If you haven’t deployed the module yet, we recommend reviewing our RhythmWorld presentation, “Deploying the MITRE ATT&CK Module” for guidance on how to do so.
Detecting Suspicious PowerShell Usage: Parent Process is CMD.EXE
Detecting suspicious use of PowerShell from the example in Volexity’s blog is to note that CMD.EXE is invoking PowerShell.EXE with a command. The fastest way to detect suspicious PowerShell usage is searching Events for our AIE rules in the MITRE ATT&CK Module named “Execution : PowerShell” or “T1059.001:PowerShell”. Another method of searching is to look for Parent Process Name is CMD.EXE and Process Name is PowerShell.exe. In some environments it may be normal for powershell.exe to be invoked by CMD.EXE. We have provided guidance in two different Community posts on how to determine if PowerShell usage is normal in your environment. You can view them here and here.
Detecting Volexity’s Command Line IOCs
Volexity has published an appendix of their IOCs at the bottom of their blog. Appendix B contains their list of observed PowerShell commands used. The following are steps you can take to leverage these commands in your threat hunt using the LogRhythm Web Console.
- On the Dashboard, click on “Search…”
- Select “Command” is sql:% and the name from the IOC list%
- Example: sql:%Get-AcceptedDomain%
- Click on “Value” and repeat the previous step until all IOCs have been added.
- Your search criteria will look something like this:
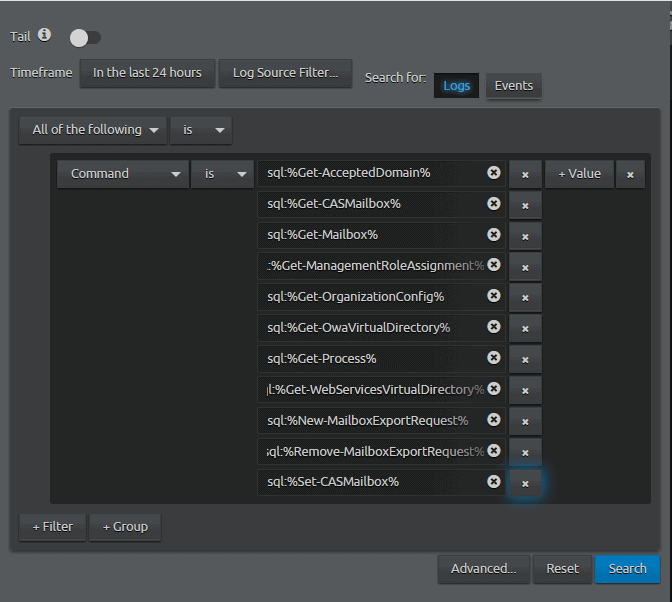
- Click on “Advanced…”
- Name the search something like “Volexity:DarkHalo:Commands”
- Change the Read Permission to “Public All Users”
- Change Write Permission to “Public Global Administrator”
- You may want to modify “Maximum Results” based on your environment.
- Your saved search should look something like this:
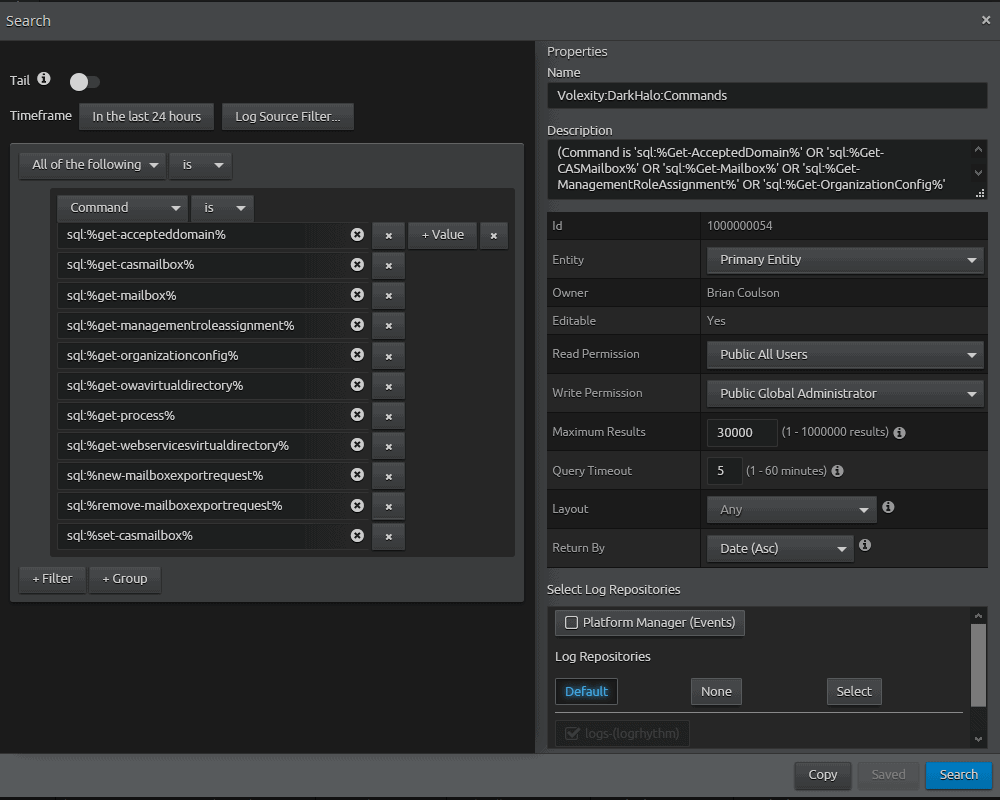
- Save your search.
- Before searching, we will modify the time frame. We know that the SolarWinds modified binaries occurred around March. Set the time frame starting March 2020 to present.
- Note: You may want to search in smaller time slices depending on the number of results.
- Your search should look something like this:
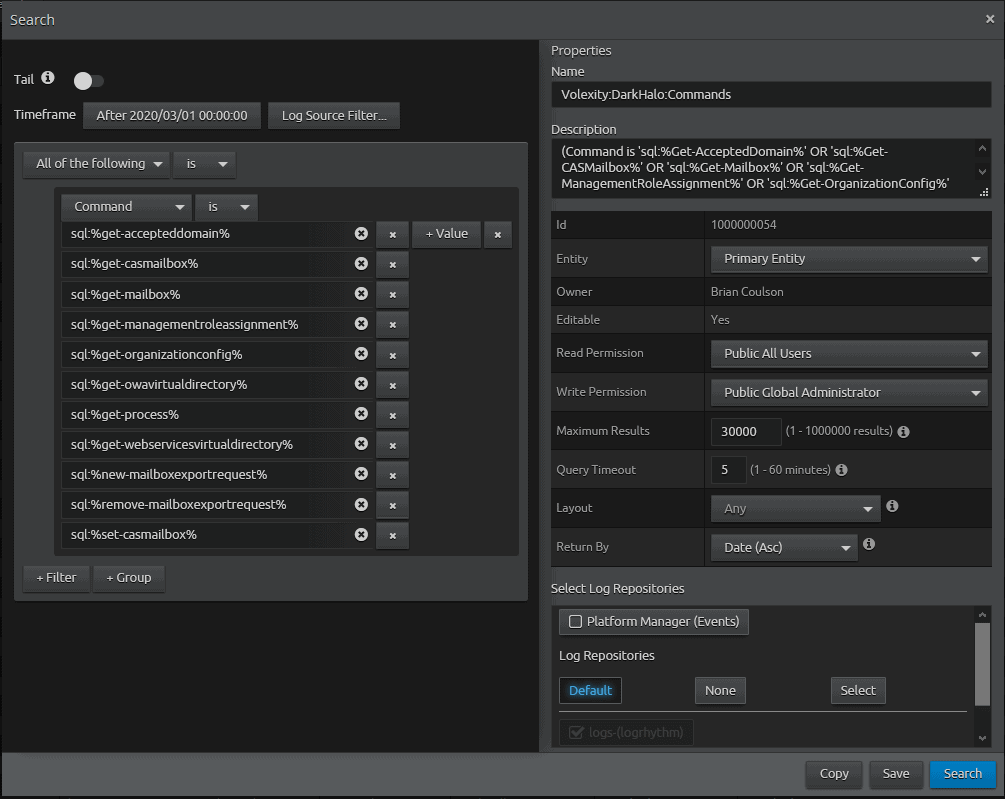
- Click on “Search” to execute the search.
Analyzing Your Search Results with the Default Analyze (7.6) Dashboard
Viewing your results in the Default Analyze Dashboard should look something like this:
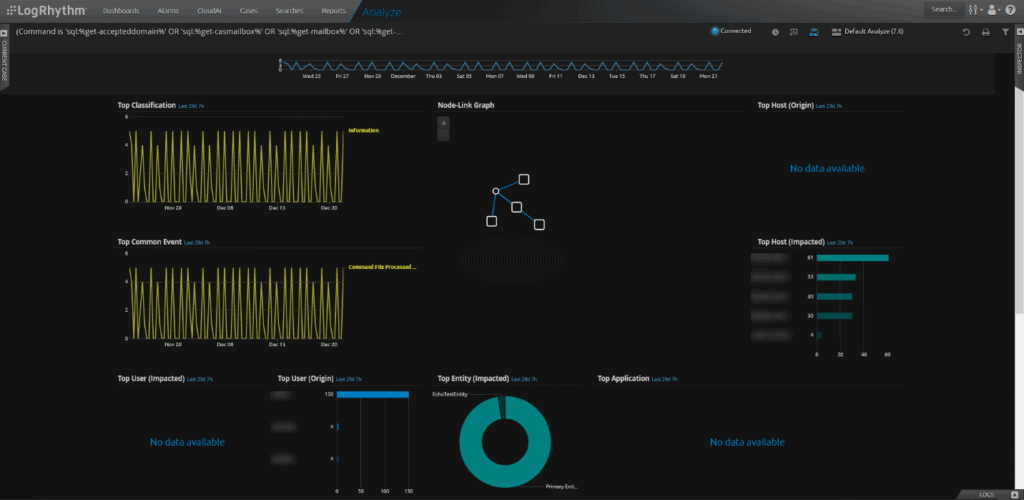
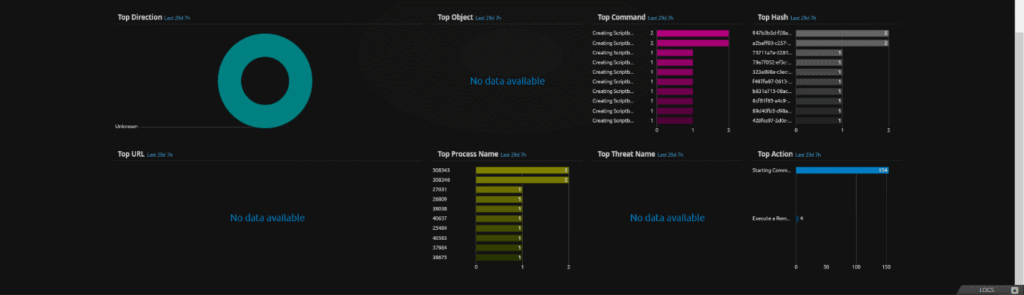
Most notable off the bat are User (Origin) and Top Host (Impacted). You can start your filtering by excluding known users and known systems that should be executing the commands. A quick way to exclude is by Alt + Double Click something you want to exclude.
You can also hunt by using the process of elimination by filtering on a user, and reviewing the commands issued to determine if they appear “normal” or are more in line with what the Volexity blog listed.
LogRhythm Labs wants to make sure LogRhythm customers have usable intel to help detect IOCs and defend their organization against attacks. Make sure to subscribe to the LogRhythm blog for updates when we publish new posts.
Appendix A
Regular expressions used to extract IOCs from the FireEye repository
| File | Indicator | Regular Expression |
| All-snort.rules | ThreatName | grep -o -P ‘(?<=msg:”)(([^”])*)(?=”;)’ all-snort.rules | sort | uniq > FE_SW_Snort.txt |
| Indicator_Release_NBIs.csv
| Domain Names | sed ‘s/[][]//g’ Indicator_Release_NBIs.csv | cut -d “,” -f 3 > FE_SW_nbi.txt |
[1] https://us-cert.cisa.gov/ncas/alerts/aa20-352a




