Cathy Huang, Associate Research Director of IDC Asia/Pacific’s (AP) Services and Security Practice, caught up with Joanne Wong and Leonardo Hutabarat, to discuss the role and differentiation of security operations platforms and how it drives the overall enterprise security efficacy and cyber-resilience.
Q: What role do effective security operation platforms play in driving the overall security posture as well as cyber-resilience capabilities of organizations in the AP region?
Joanne: Breaches can only be prevented if the organization takes basic security seriously. The challenges are multi-layered, both on the individual and organizational level, much of which can be attributed to the lack of manpower and quality information from the security operations team. Organizations also face the issue of alarms being triggered by too many false positives. These challenges prevent security operations from responding effectively and responsibly.
It is crucial for organizations to strengthen the performance of their security operations with an integrated security operations platform that provides knowledge based on common attack tactics, techniques and procedures. Analysts’ familiarity with the Utilization Playbook is also critical, especially to those who are still gaining experience.
Leonardo: Security orchestration, automation and response (SOAR) technologies in combination with security information and event management (SIEM) on one platform will provide integrated intelligence, from event correlation to user entity behavior analytics (UEBA) analysis, while providing integrated automation in terms of response. An effective security platform incorporating SOAR technology also needs to integrate with organizational business processes so quick workflow approval can be obtained if the platform needs to make security response and security changes in response to an attack. In summary, it is important to have a single integrated intelligent platform with SOAR capabilities and for organizations to enforce a proper security best practices process.
Q: It is not uncommon to hear that organizations have been hacked or breached despite the investments they have made to strengthen their security posture or to comply with local and industry regulations.
What is missing? What is the level of security that organizations should be looking to achieve?
Joanne: Each organization has its own understanding and perception of how local or industry regulations should be implemented in order to be fully secured. Complying with local or industry regulations does not equate to true information security, which has a wider and deeper scope. Compliance just means that the organization has met the minimum requirement to conduct business in that country or vertical.
The checklist to achieving true security is long. It means an organization needs to be continuously aware of: What assets they have, the changes happening in its environment and the latest vulnerabilities. It also needs to be up to date on recent breaches/attacks while providing, on the individual level, a security awareness program for internal and continuous improvement on its information security posture. And, the organization should have in place a security operation maturity model/program, so that it can continuously and effectively improve its security level/posture. As we all know, security is not an end state, but a journey.
It is imperative that an organization chooses technology that provides scalability and extensibility within the same platform, especially security-related technology such as SIEM, UEBA, file integrity monitoring (FIM), network detection and response (NDR), and SOAR. A single integrated platform will reduce operations, maintenance and integration costs, optimizing security spending.
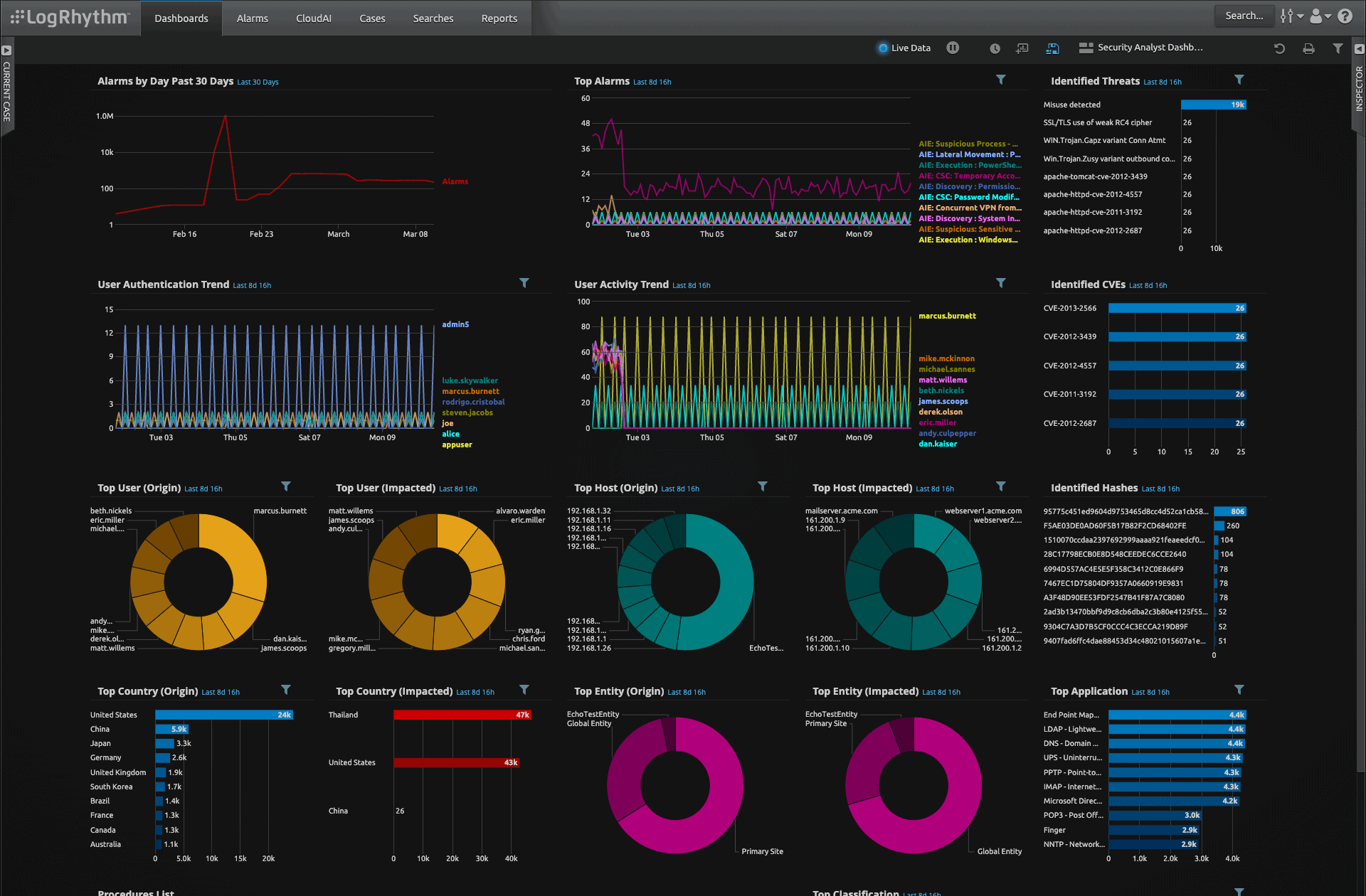
Q: Since achieving 100% security is not possible, what should AP organizations focus on and what are the key metrics they should use to achieve a stronger security posture and better cyber-resilience?
Leonardo: The key metrics used to measure an organization’s incident response capabilities would gauge the average time an attack is detected and average response time to an attack. Specifically, the organization would have to measure the Mean Time to Detect (MTTD) and Mean Time to Response (MTTR). The faster the platform detects an attack or breach and responds, the more effective its organization’s security operations will become.
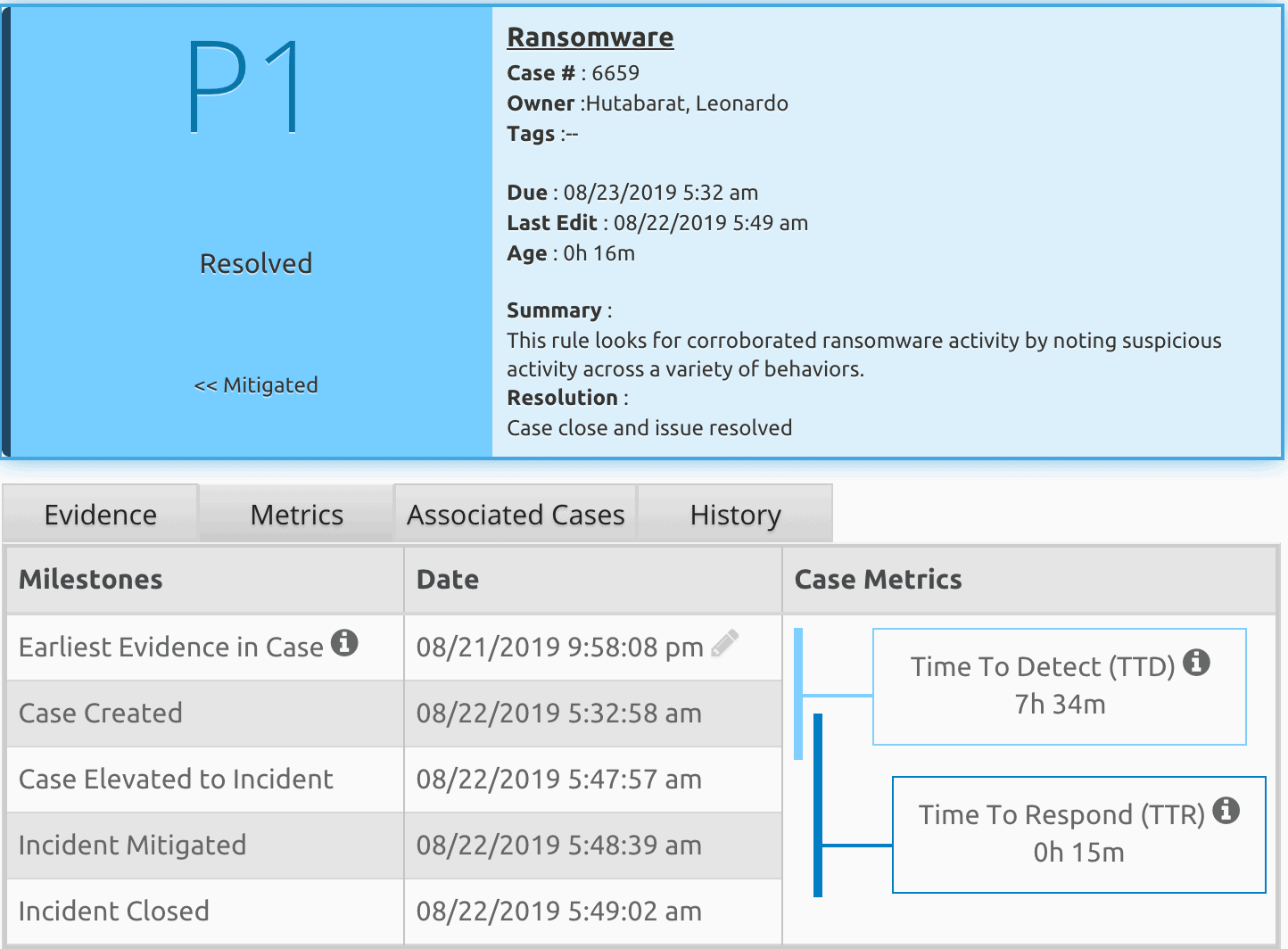
Q: Looking ahead, with the new emerging security architectures that emphasize identity-awareness (e.g., Zero Trust) and the rise of connected devices, how will this trend impact an organization’s security operations strategy?
Leonardo: Organizations with new security architecture changes in identity awareness and connected devices will need to enrich their security operations with security analytics that understands user behavior, especially users with the same identity but who have different login accounts. They will also need to consider monitoring not only their physical infrastructure but also their cloud infrastructure. Monitoring cloud access security brokers and microsegmentations is also necessary for complete monitoring of software as a service (SAAS) applications.
To further enhance your organization’s total security monitoring strategy, apply monitoring visibility to Operation Technology (OT), which will be beneficial in situations where an attack moves between the IT and OT environments.
Q: What do you think differentiates LogRhythm from other SIEM vendors?
Joanne: LogRhythm’s main differentiator lies in its SIEM technology, an integrated single intelligent platform for security operations centers (SOCs) that aggregates technologies such as SIEM, UEBA, FIM, NDR and SOAR. The SANS Institute has tested the platform’s stability and scalability; its architecture is scalable to 300,000 messages per second. LogRhythm’s platform can be deployed physically, virtualized and in the cloud through a pay-per-use model such as infrastructure as a service (IaaS) or SaaS model. LogRhythm’s short implementation time also sets it apart from the pack, especially with out-of-the-box-supported log sources and artificial intelligence support.
LogRhythm empowers customers to run smaller SOCs due to the product’s effectiveness. In fact, 65% of respondents to a customer survey noted they only need between 1 and 3 people to run their SOC on our platform.
As part of LogRhythm’s network XDR offerings, the MistNet NDR, a cloud-based analytics platform, delivers vast network visibility and accurate threat detection, providing even greater visibility into network traffic and potential threats.
Financially, LogRhythm’s True Unlimited Data Plan provides flexibility for organizations to extend security monitoring to all organizational assets, providing complete visibility throughout the organization.

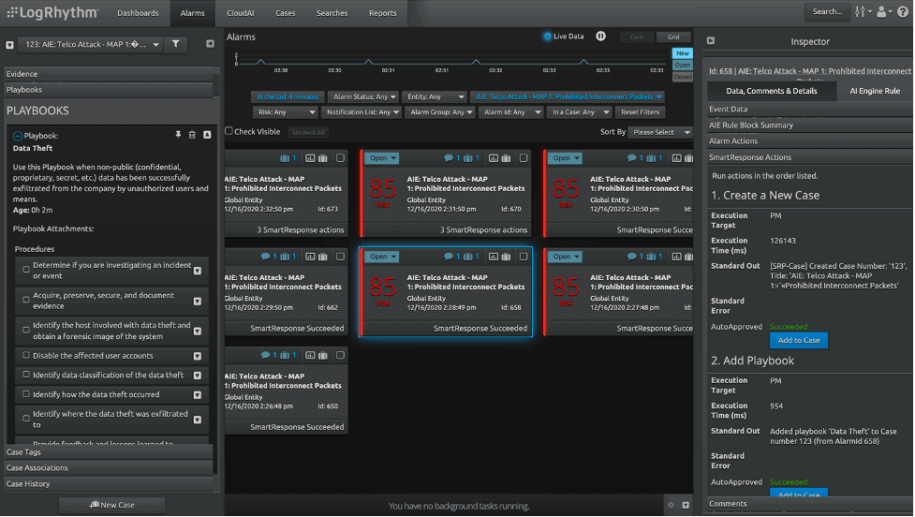
Get Started with LogRhythm SOAR
With LogRhythm’s SmartResponse™, you have the power to decide the best solution to automate work so your team can focus on complex incident response that requires skill and creativity. Choose from fully automated playbook actions or semi-automated, approval-based response actions that allow users to review before executing countermeasures.
Schedule a demo to see LogRhythm SOAR in action today.