With the volume of data that flows into a security operations platform, it’s critical to ensure you’re following the right steps and workflow to onboard log sources. For some, the process can be cumbersome and disjointed, but that’s no longer the case with LogRhythm SIEM.
As part of LogRhythm SIEM version 7.14, we’ve made it easier than ever to onboard Beat log sources. In the latest release, we’ve incorporated the workflow in the Web Console for a streamlined experience. The sixth consecutive quarterly product release also features Admin API enhancements to manage Beats and Open Collectors, a new in-platform Resource Center, and new and updated supported log sources.
Simplify Log Source Onboarding
To help save you time and boost the efficiency of your security operations center (SOC), LogRhythm simplified the process to onboard cloud-native log sources via the Web Console. With the latest release, we’ve introduced a new workflow to onboard data in the Web Console, making it easier than ever using a wizard-driven experience.
With this updated SIEM capability, you can cut your time to onboard log sources in half. The built-in wizard prompts questions to guide you on what you need from the API provider to connect to LogRhythm — all through a single screen. You don’t have to be an expert in LogRhythm, Open Collector, or Beats to understand how to onboard a log source. The new capability simplifies the workflow, making it simple to get data into the system and expedite the onboarding process.
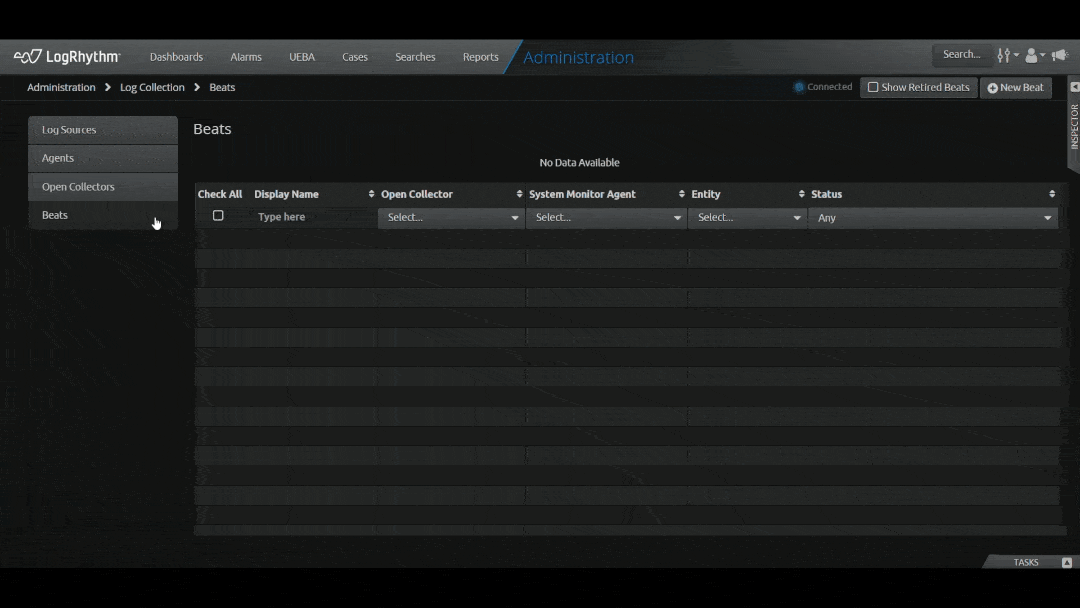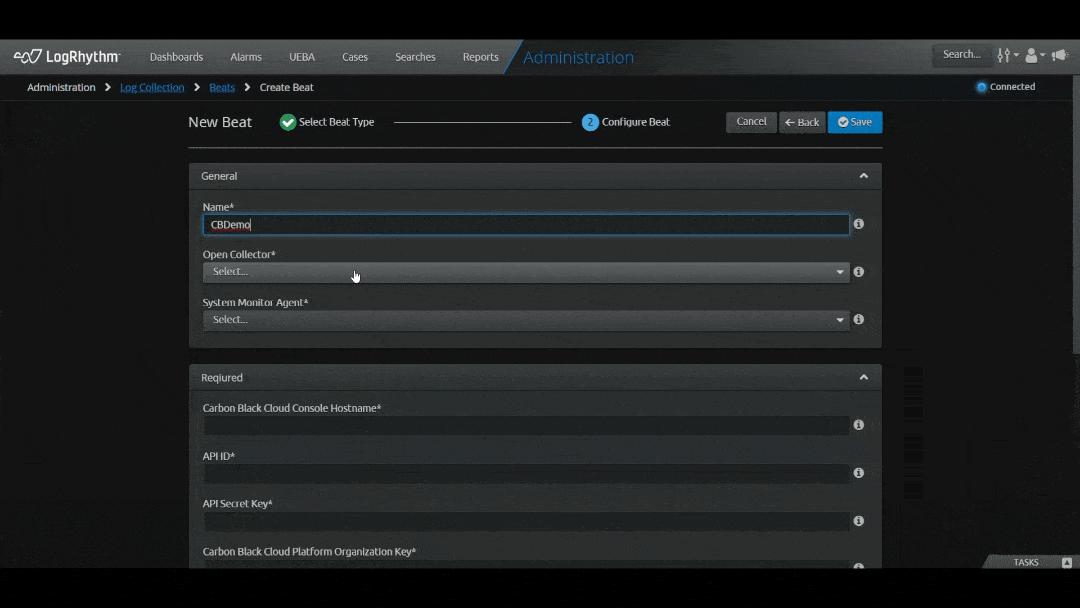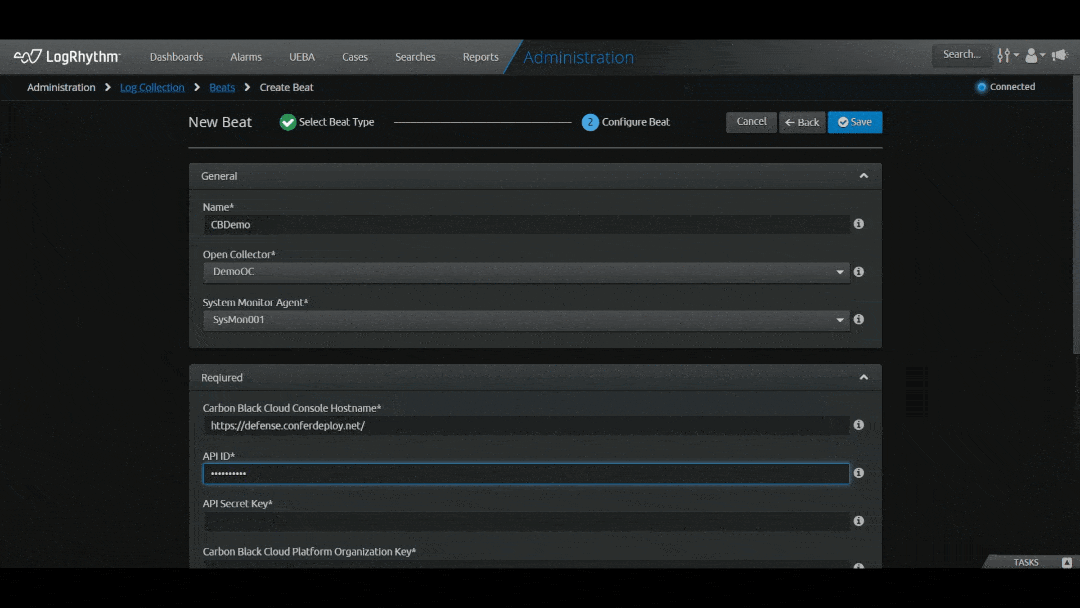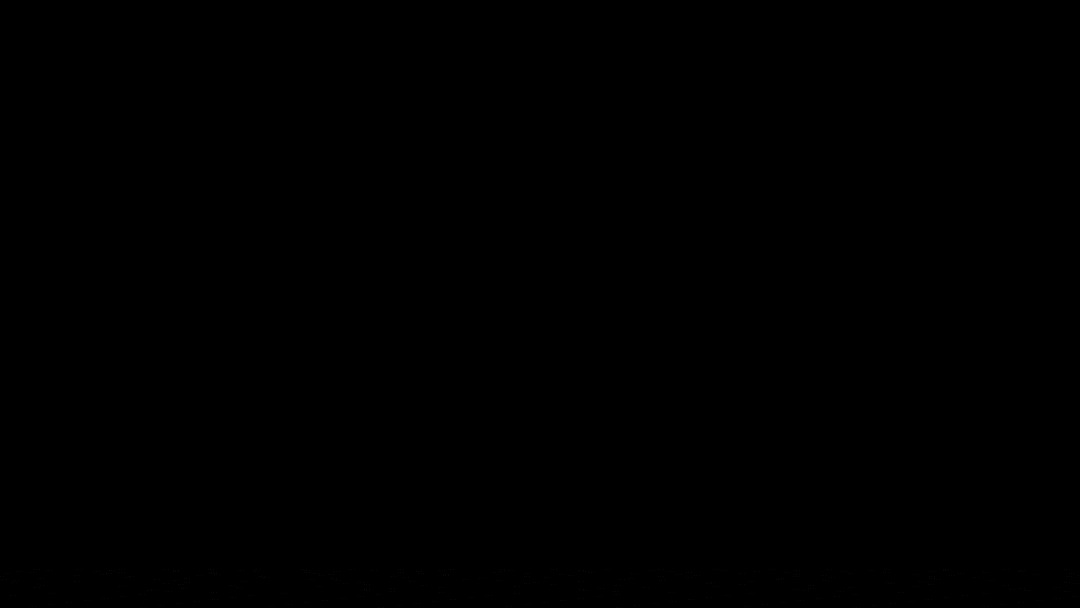
The latest release will support ten log sources, with others to follow in the coming months:
- AWS S3
- Azure Event Hub
- PubSub
- Microsoft Graph API
- Prisma Cloud
- Duo Authentication
- Carbon Black Cloud
- Cisco Secure Endpoint
- Proofpoint
- Symantec
Find out more about the new log source onboarding in the Web Console feature in my colleague’s blog post.
Admin API Improvements
LogRhythm SIEM is traditionally known as the heart of the SOC. Since many customers and partners have technologies that feed into the SIEM, it’s crucial to have rich application programing interfaces (APIs).
With LogRhythm 7.14, we’ve improved the Admin API to now include Beat Management and Open Collector Management. This enables administrators to integrate more advanced log sources and automate tasks via APIs, such as searching data, creating cases, and closing and opening alarms through APIs, reducing administrative overhead.
Improved Deployment Statistics
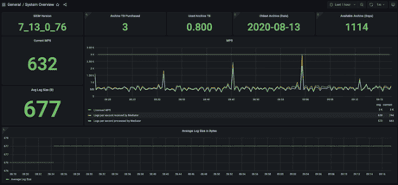
If you are a LogRhythm Cloud customer, gaining visibility into critical deployment information became easier. LogRhythm added an additional feature to make a Grafana dashboard available through for LogRhythm Cloud customers. This enables you to quickly access critical deployment information such as message per second (MPS) volumes, processing queues, and time to live (TTL).
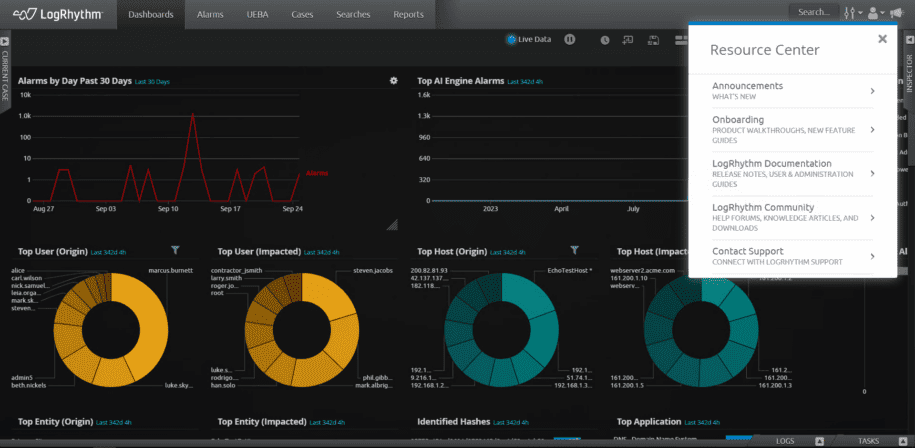
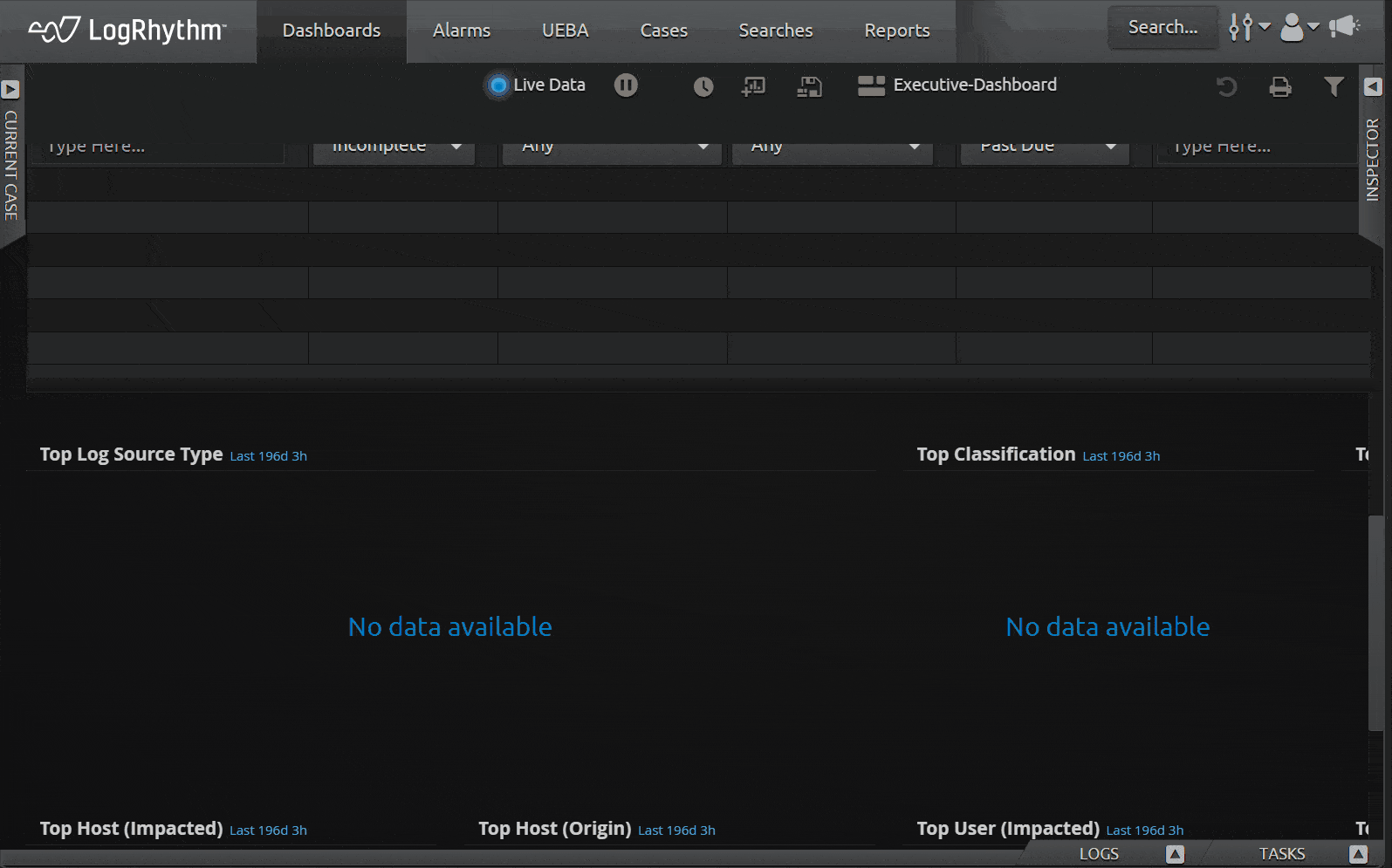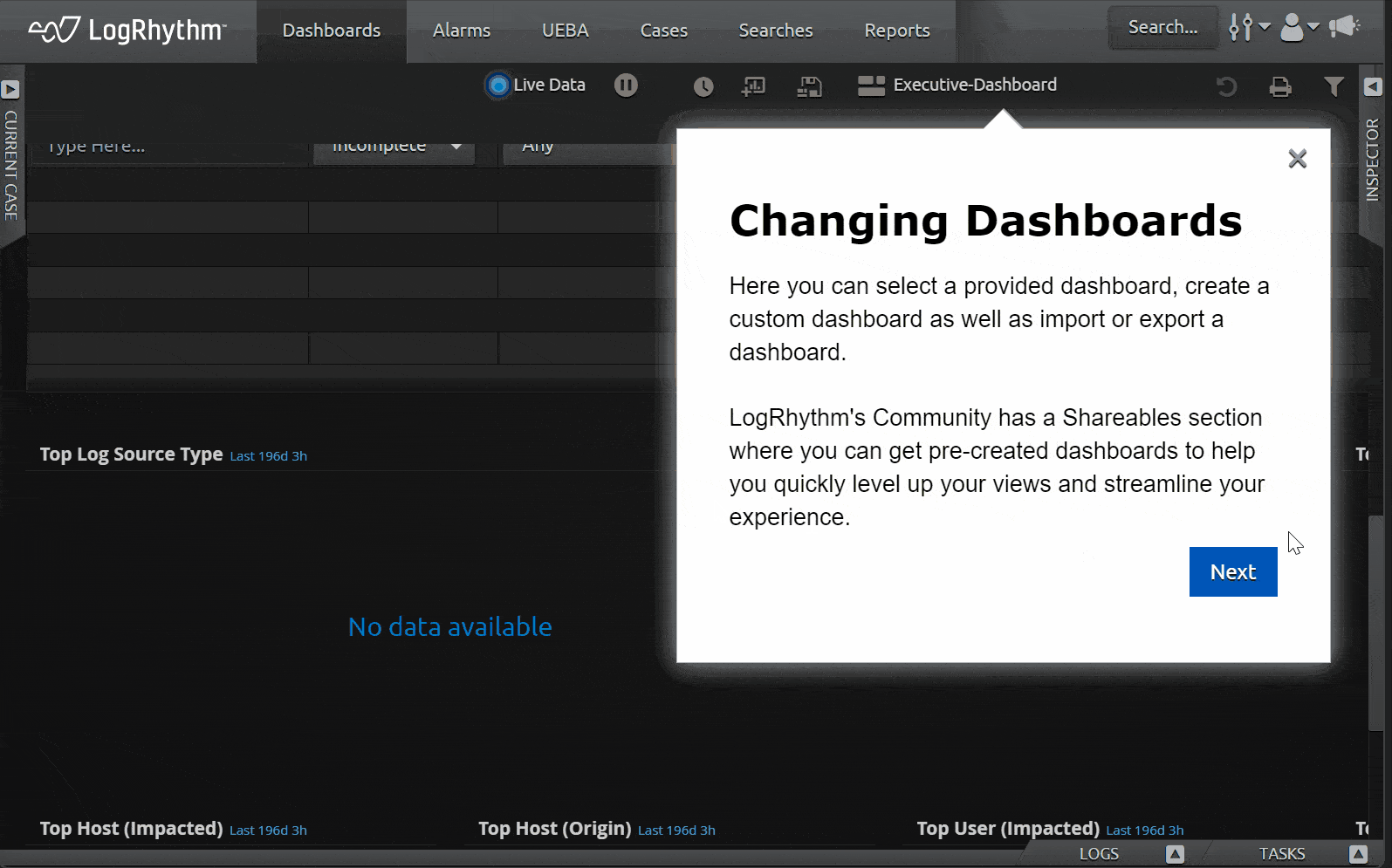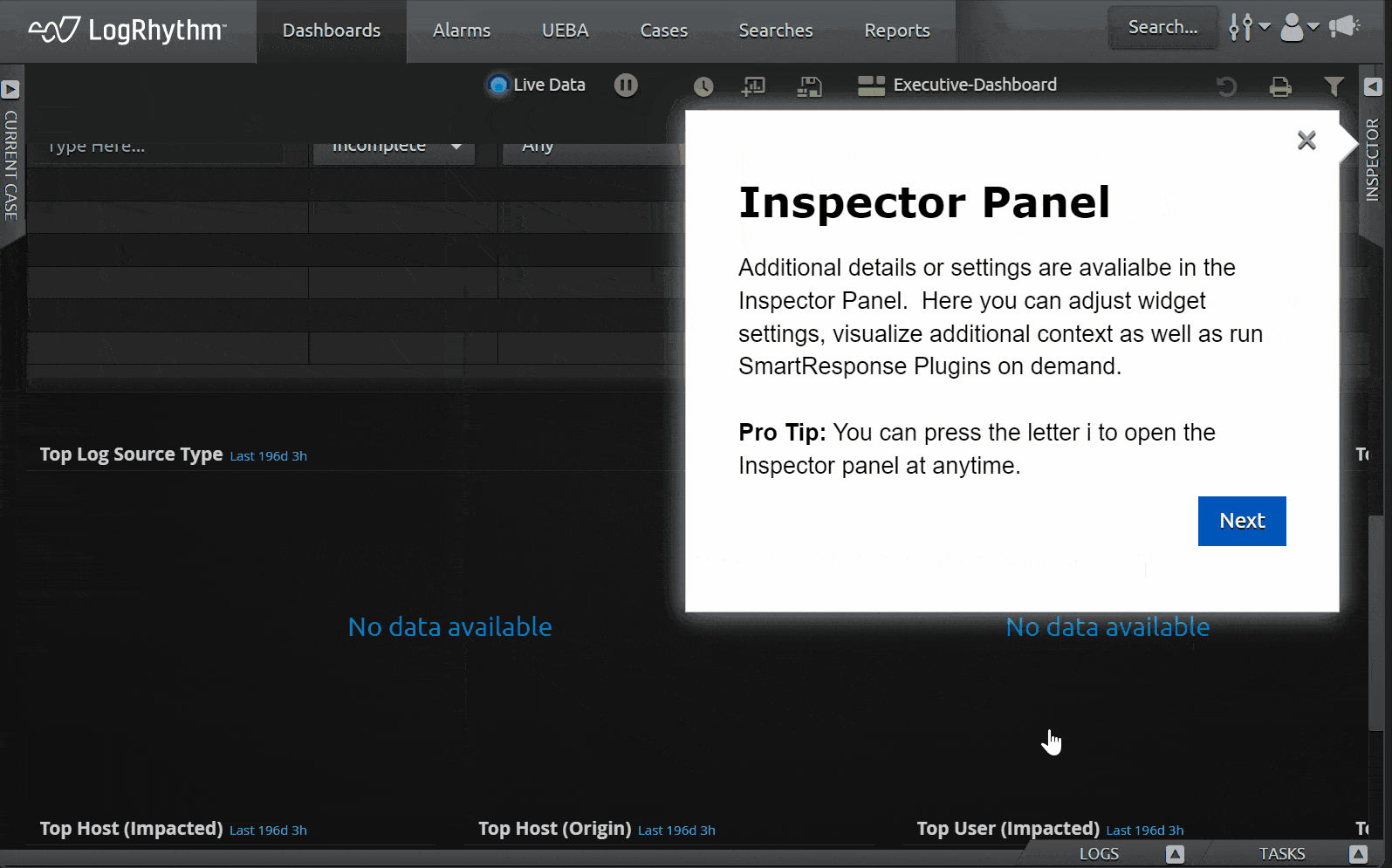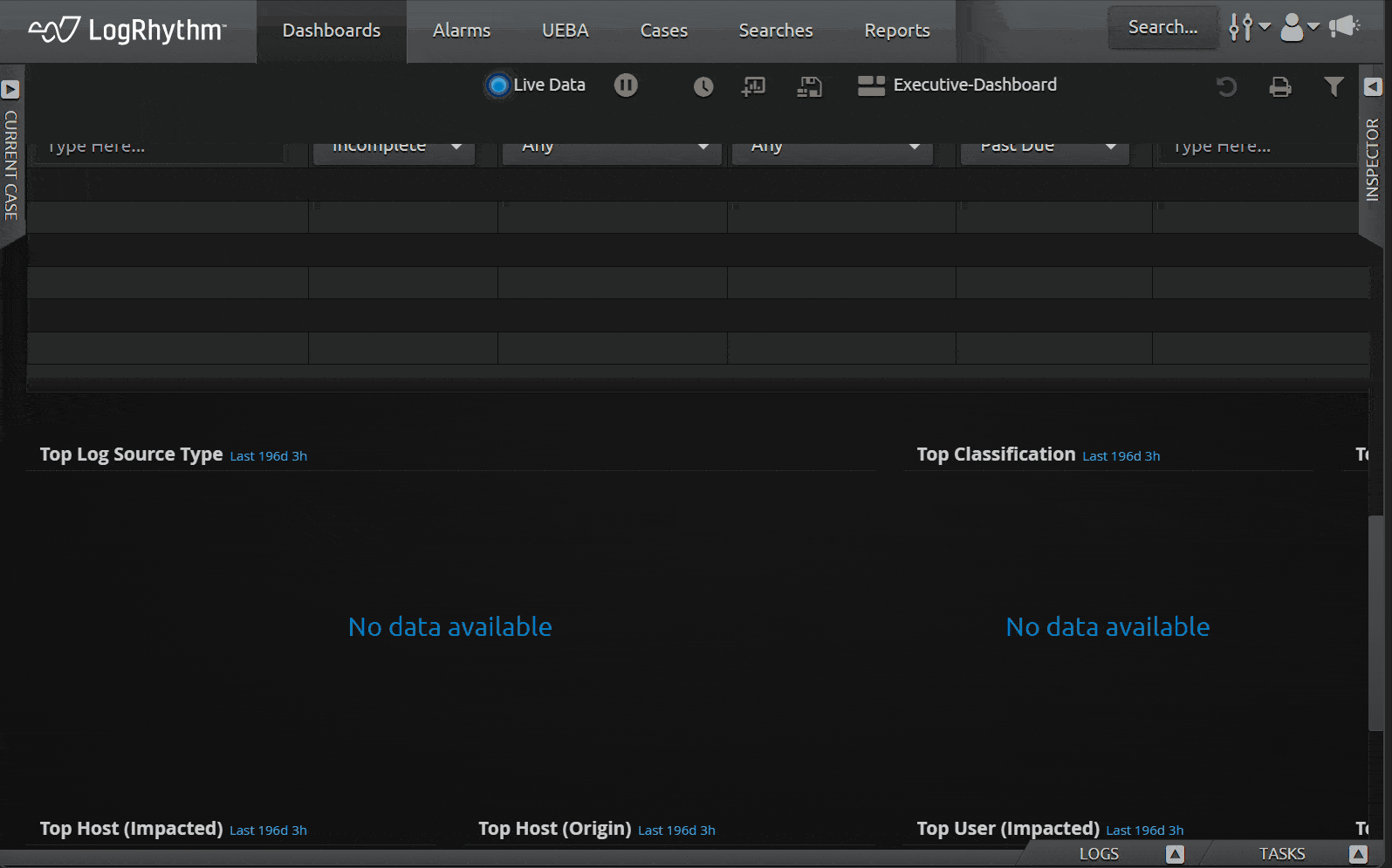
In-Platform Resource Center
Keeping customers informed about the latest innovations and documentation is a key tenet at LogRhythm. That’s why we added a new Resource Center in the Web Console. Here you’ll find pop-up notifications about new SIEM releases, as well as links to documentation, training, the LogRhythm Community, and support.
The Resource Center will not only keep you updated on the latest LogRhythm SIEM releases, but it will make it easier to get up and running quickly. Now, you no longer need to spend time browsing a website in search of specific documentation. With a few clicks of a button, you can get the information you need to become a more productive SOC analyst. This includes having quick access to release notes, documentation, Community, and in-app guides and quickly opening a case with Support.
Continuous Log Source Support
LogRhythm is constantly evolving the log sources we support and making updates to strengthen our correlation and analysis. Our new and enhanced methods of ingestion include:
- Salesforce eCommerce Cloud: New policies for parsing Audit and Security logs help prevent classification errors and provide more consistent parsing of data from Salesforce.
- Carbon Black App Control: Ensures that only trusted and approved software is allowed to execute on an organization’s critical systems and endpoints. Gain higher levels of control and visibility while eliminating unplanned downtime of critical systems.
- Zscaler: New policies help prevent classification errors and provide more consistent parsing of log source data for Zscaler while new MPE rules parse log metadata to the correct schema fields and classify highly complex log source data.
- FortiGate/FortiAnalyzer: New policies help prevent classification errors and provide more consistent parsing of log source data for FortiGate/FortiAnalyzer while new MPE rules parse log metadata to the correct schema fields and classify highly complex log source data.
- Microsoft Graph API: Helps customers collect data across Microsoft 365 services.
Enhance Threat Detection with New Models
In addition to SIEM, LogRhythm continually looks for ways to enhance our insider threat detection capabilities. LogRhythm recently expanded its threat detection capabilities to help analysts uncover potential attacks in LogRhythm UEBA, our cloud-native user entity and behavior analytics (UEBA) solution with two new models — Unusual Login Time Activity and Unusual Login Day Activity.
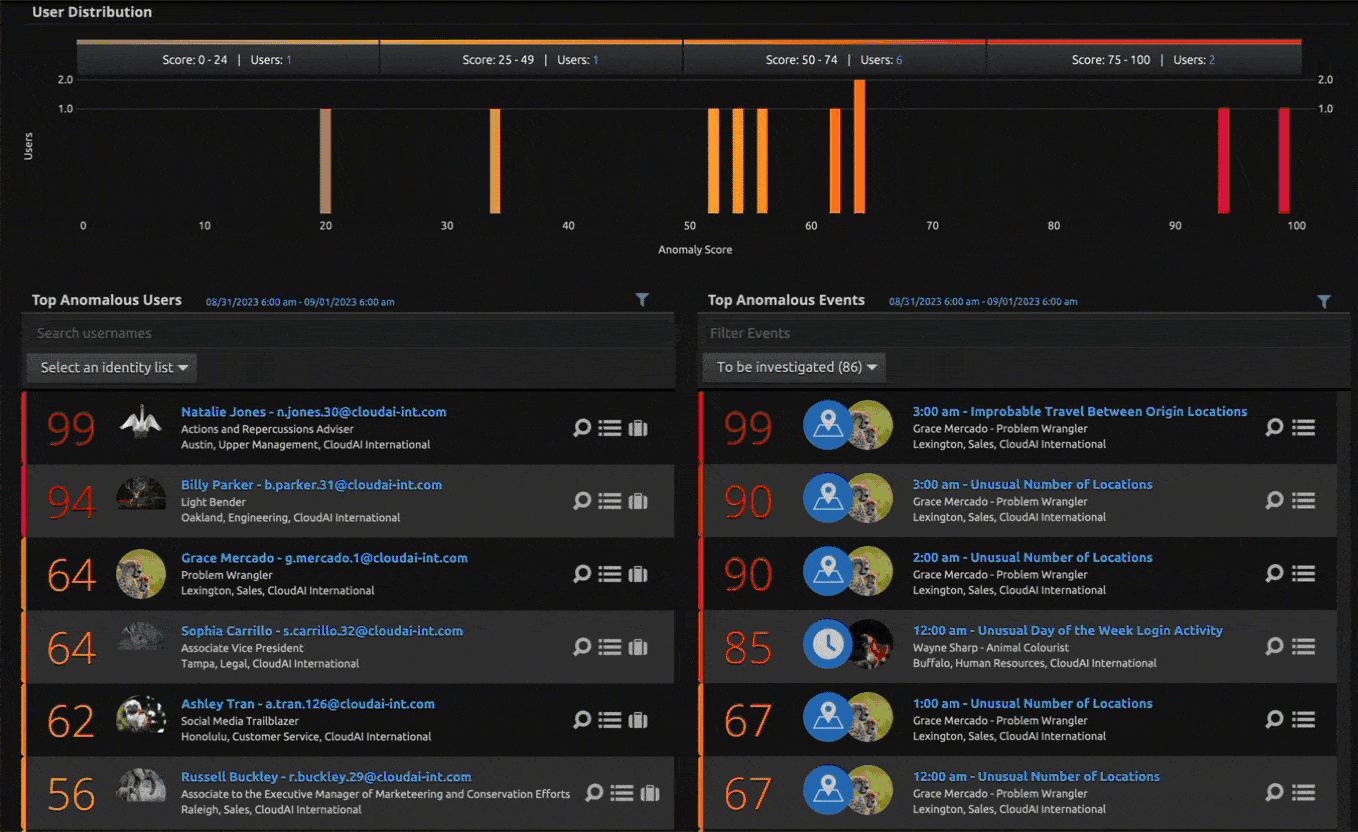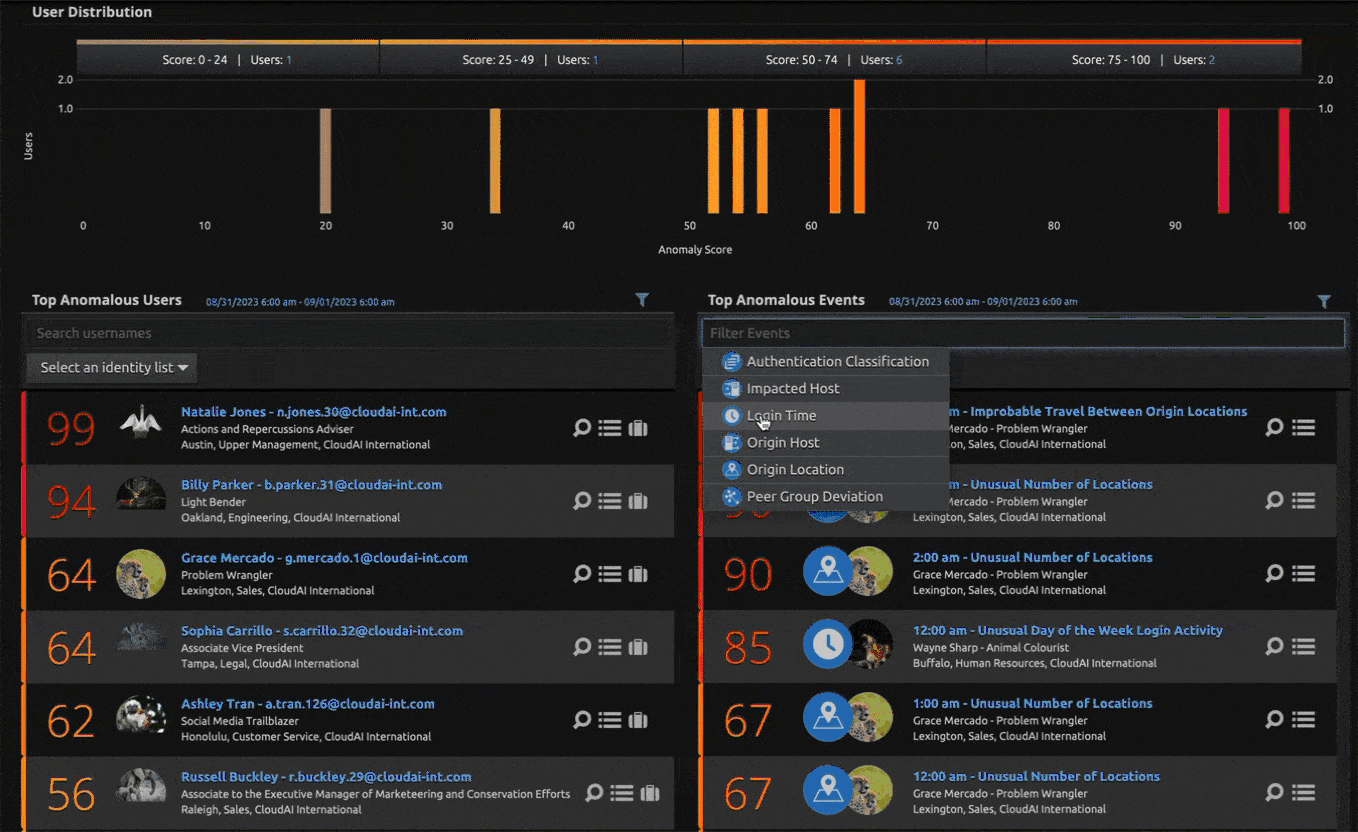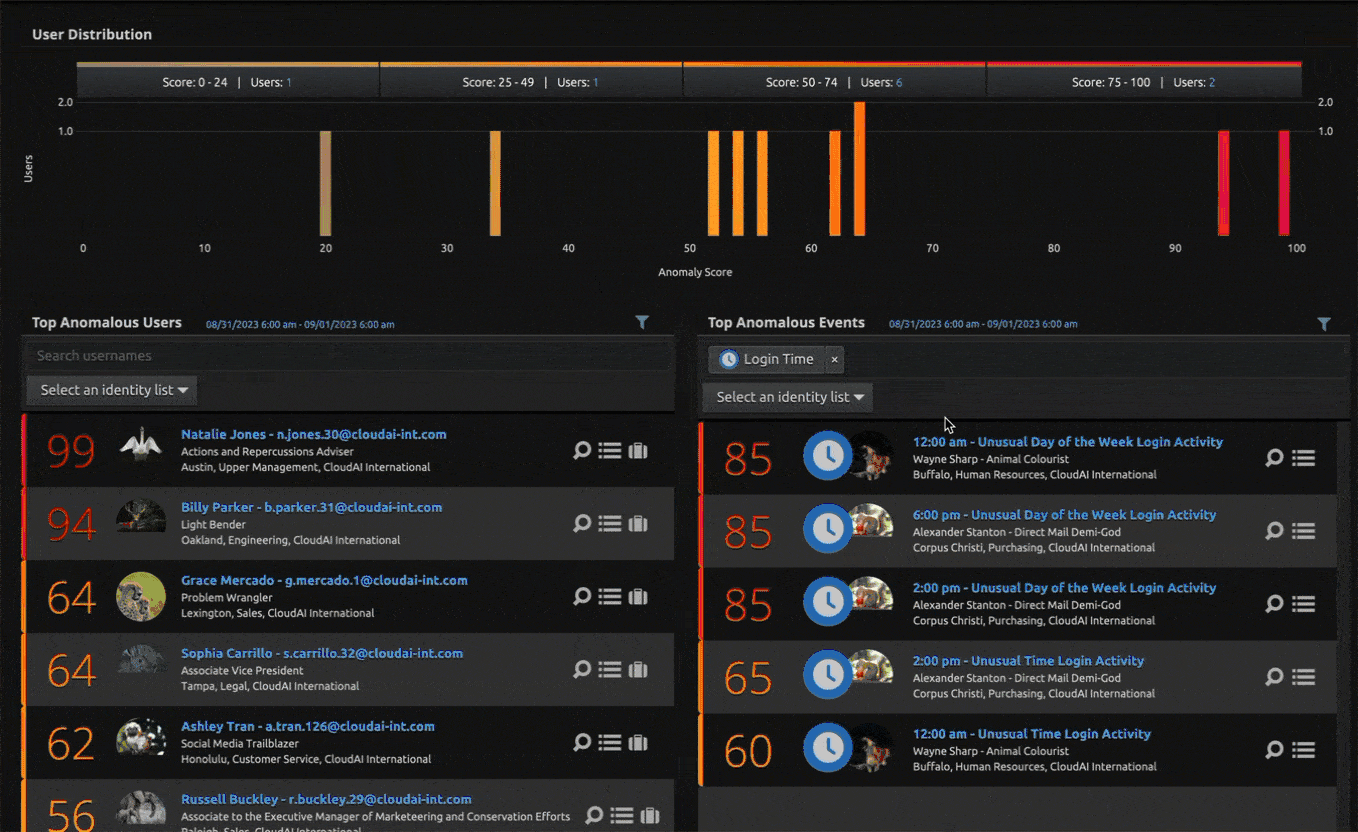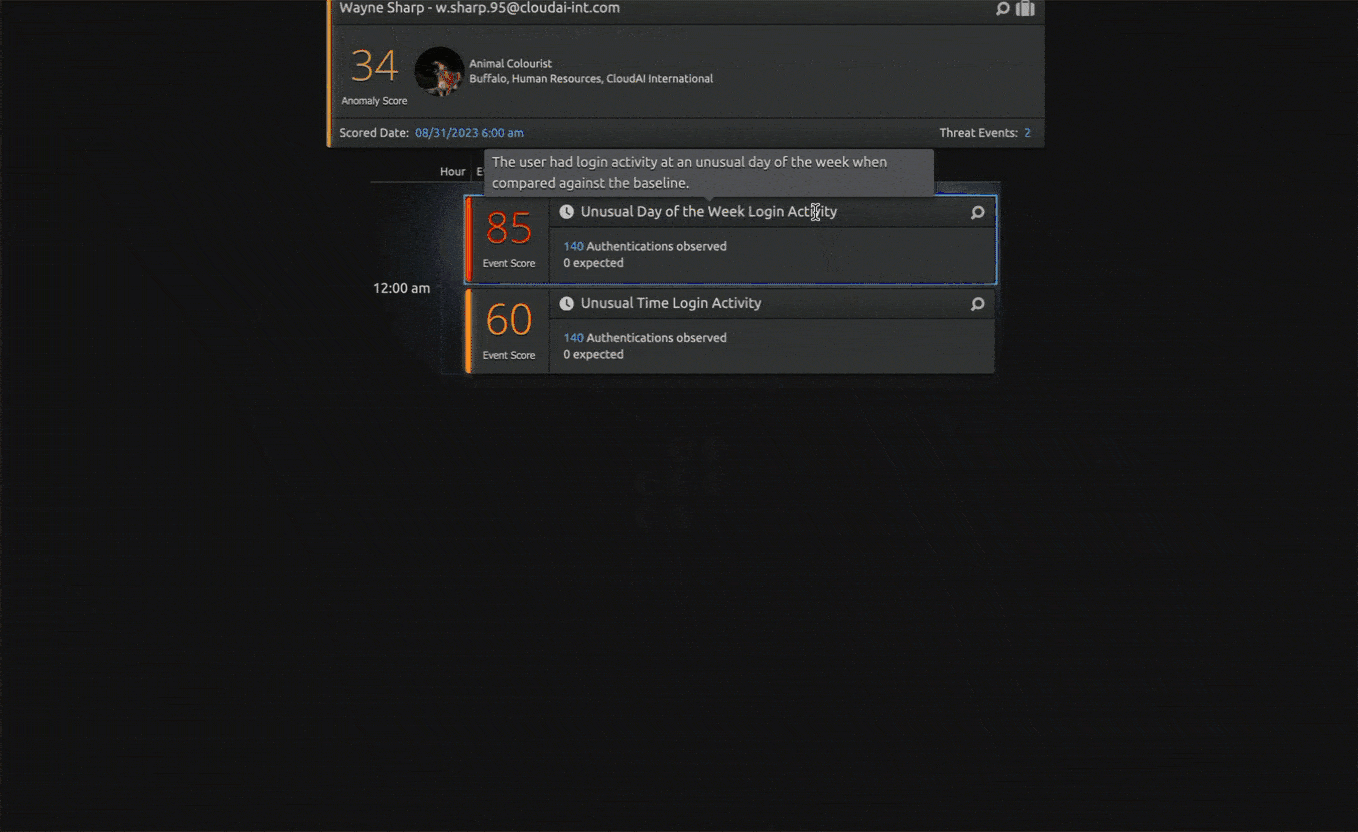
The new models detect when a user had logon activity at an unusual time of the day or when a user had logon activity on an unusual day of the week when compared against the baseline. For example, if an attacker steals a user password from a user who works Monday through Friday 8 a.m. to 5 p.m. and logs on in the middle of the night and over a weekend, the models will trigger. The models will warn of the unusual login time and of the unusual login day activity if the user typically works weekdays between 8 a.m. and 5 p.m.
LogRhythm customers can stay up to date for the latest on LogRhythm UEBA here.
Make the Move to LogRhythm 7.14
Don’t miss the latest features from LogRhythm SIEM! Existing customers can request a license here and download LogRhythm 7.14 from Community. LogRhythm’s Professional Service team can help you stay current with our SIEM releases every quarter with our Unlimited Upgrades Service. Information and documentation on all the latest enhancements are available in the Release Notes.
If you aren’t a customer or you want more details about LogRhythm’s product releases, register for the October 2023 Quarterly Launch webinar or visit our What’s New webpage.