Launched in October 2022, LogRhythm Axon is a groundbreaking cloud-native software as a service (SaaS) platform built from the ground-up for security teams that are stretched thin by overwhelming amounts of data and an ever-evolving threat landscape. Staying true to our commitment to our customers, we continue to release new functionality to make the life of a security analyst better by constantly enhancing Axon’s intuitive experience and supplying contextual analytics into cybersecurity threats to reduce noise and quickly secure the environment.
What’s New in LogRhythm Axon?
With the latest LogRhythm Axon release, we learned from over 18 years of experience and customer feedback to build powerful security analytics that surface the most pertinent threats to your organization and allow analysts to easily investigate threats by searching and drilling down into underlying logs.
Powerful security analytics
With limited resources available, analysts need every tool in their arsenal to help secure their environment. We’ve developed our analytics engine to automate the detection of threats with out-of-the box threat detections including those mapped to the MITRE ATT&CK framework, the ability to create custom threat detections through an authoring interface, and the capability to easily investigate log observations surfaced by our analytics engine. All combined, these provide powerful security analytics that make your life easier.
Analytics rule builder
Our analytics engine automates threat detections to make it easier and quicker to understand the threats that you face every day. You can build threat detections from quality out-of-the box content including detections mapped to the MITRE ATT&CK framework, common events, and metadata that are important to your organization. With end-to-end authoring of analytics rules, you can find and easily extract useful information such as how logs are connected, from enriched log messages to automatically surfaced threats for investigation in the Axon dashboard.
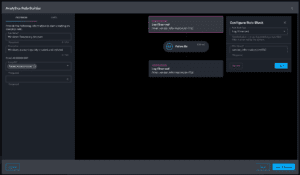
Observation workflow
Observations made by the analytics engine are built as another type of log source, enabling search across all collected data including third-party sources and observations made by analytics with no additional knowledge required. When an observation is raised by streaming analytics, you can quickly identify it by highlighting and flagging observations in table widgets and search results grid. In addition, you can easily drill down into the underlying data by finding more observations from the same rule, adding observation details to the metadata inspector, and easily retrieving rule details.
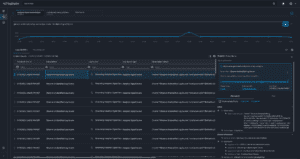
Enhanced analyst experience
There is an overwhelming amount of log data to search, investigate, and fully understand the meaning behind the data. We’ve built Axon to help analysts quickly find what they are looking for while simultaneously making the meaning behind the data more accessible through additional visualizations and data analysis tools.
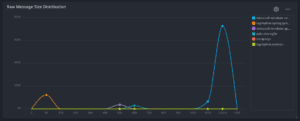
Histogram visualization
Plotting data points over a numeric distribution allows you to more quickly understand numeric data for use cases such as distribution of log message by log source type, traffic by user or host, and/or network activity by port number.
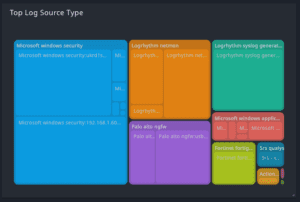
Treemap visualization (coming in January)
Display hierarchical and/or related data in a nested format so that analysts can quickly find outlier values to investigate further.
Notes widget
Ideally used for marking up reports and security operations center (SOC) dashboards, the notes widget transfers knowledge to another analyst by outlining what they should look for in a graph or the significance of results by easily adding contextual information such as user-configured text and images.
Expanded data collection and Agents
The foundation of any security operations platform begins with the data being ingested and the supported devices. That’s why we are never done expanding on Agents and log sources that can be ingested in the Axon platform.
We’ve expanded our cloud collectors to include Google GCP Cloud Collector and supplied additional out-of-the-box support for more log types, giving analysts increased visibility to prevent threats. In addition, analysts can now fine-tune Axon Agent performance (i.e. buffer, batch size, and compression), enable auto-update, and can troubleshoot via the Axon UI.
This is just the beginning of many remarkable releases to come and we’re nowhere close to being done! We’ll continue to innovate based on customer feedback so that organizations can better surface threats and respond to attacks quickly. As we look forward, we will be even better — we’re thrilled about the road ahead. To learn more about LogRhythm Axon, check out the product data sheet or request more information here.
