In 2014, SANS published a Digital Forensics poster called “Know Abnormal…Find Evil.” This resource delves into the differences between normal and abnormal behavior—and what you might look for or ignore in a digital forensics investigation.
The Challenge
Using this reference guide—and other Windows knowledge—you can look for deviation from normal Windows behaviors in real time. This gives you quicker visibility into suspicious activities that try to hide within Windows.
The Solution
Several inquiries of the key Windows processes are of particular value:
- Where is the process being launched from?
- Is it a parent or creator process?
- Is the account being used to start the process?
- When was the process started?
We need a log source that provides us with both the process name that is being launched, where it is being launched from and the parent process name.
Versions of Windows prior to Windows 10 do not provide this information in the audit log, so you can use the Microsoft System Monitor Sysmon tool to provide you with this deeper level of visibility.
The out-of-the-box processing rule for Sysmon assigns the parent process to the “Object Name” metadata field, so we can directly us this to give us the visibility we need.
Unusual Parent
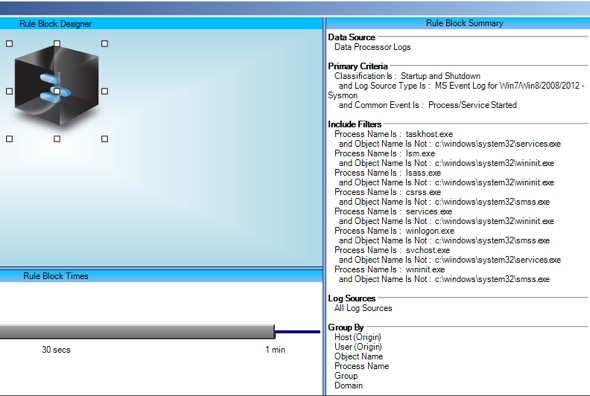
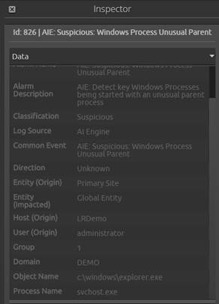
First, create an AI Engine rule that looks for occurrences of key Windows processes starting with an unusual parent process name.
The typical use case is malware launching a new process that is masquerading as a built-in Windows process in order to try to hide the new process.
Call this rule “Suspicious: Windows Process Unusual Parent.”
Click on images to expand
| [Figure 3. AI Engine Rule |
Unusual Folder
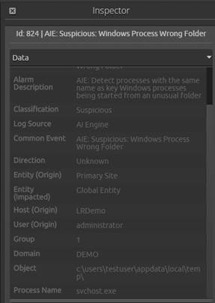
Next, create a rule looking for occurrences of those process names starting outside of their usual folder location.
The typical use case is malware trying to launch a process masquerading as a common Windows Process name but from a non-system folder.
Call this rule “Suspicious: Windows Process Wrong Folder.”
| Figure 6. AI Engine Rule | Suspicious: Windows Process Wrong Folder |
Unusual Account
Next, you will want to create a rule looking for occurrences of those process names being started by unusual user accounts.
The typical use case here is malware running under a user account trying to launch a process masquerading as a common Windows Process name.
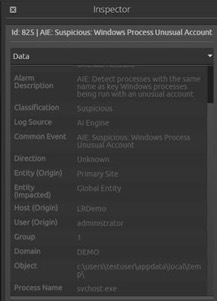
Call this rule “Suspicious: Windows Process Unusual Account.”
| Suspicious: Windows Process Unusual Account “Figure 9. AI Engine Rule |
Unusual Start Time
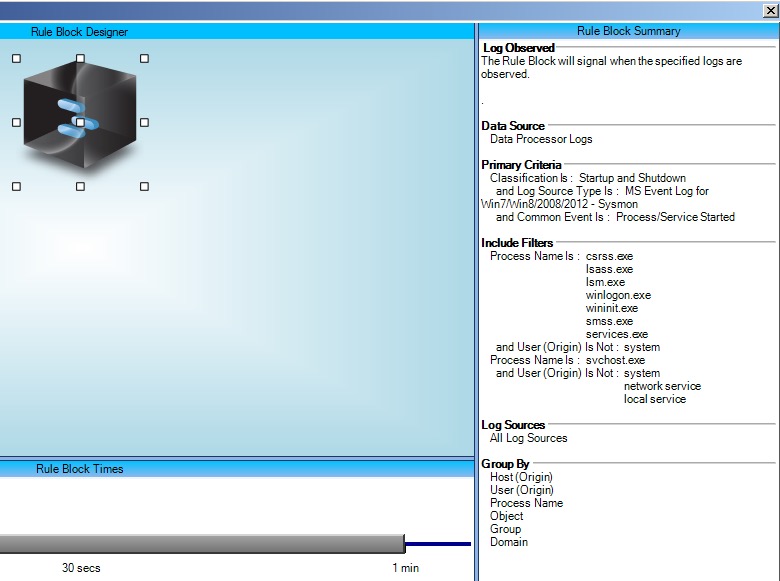
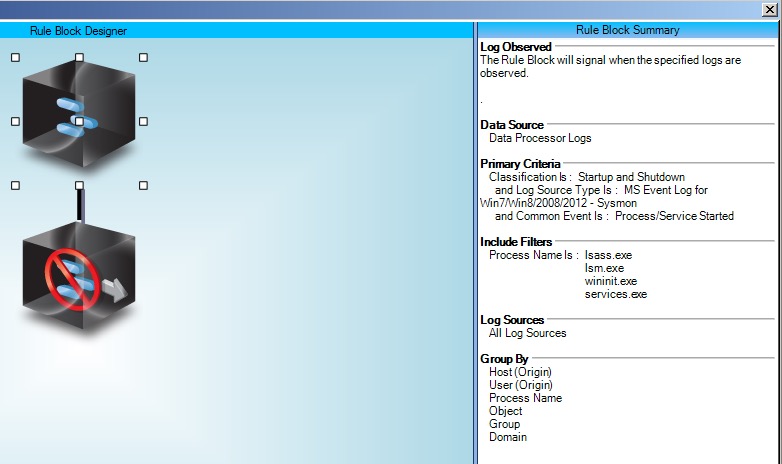
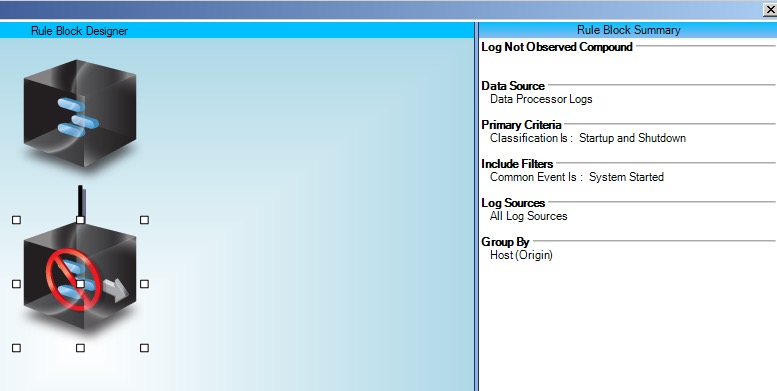
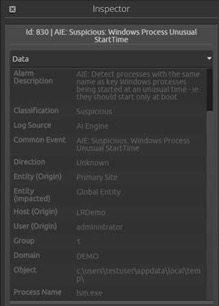
Now, create a rule looking for occurrences of those process names being started at any time other than immediately on startup of the system.
Because these processes only start at the system startup, malware trying to masquerade as one of these processes is the typical use case here.
Call this rule “Suspicious: Windows Process Unusual Start Time.”
| Suspicious: Windows Process Unusual Start Time“Figure 12. Rule Block Relationship |
| Suspicious: Windows Process Unusual Start Time“Figure 14. AI Engine Rule | Suspicious: Windows Process Unusual Start Time |
Manage Alarms
Because all of these rules are closely related, if one of them fires, two or more may also fire.
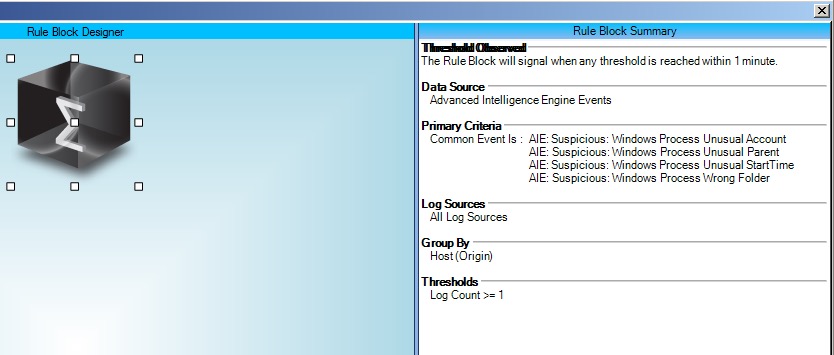
In order to reduce alarm fatigue, it may be preferable to configure the four previous AI Engine rules to just generate AI Engine events, and then create an overarching “Windows Find Evil” AI Engine Rule that will trigger when one or more of the above alarms fire.
Set the suppression to one minute, and call the rule “Suspicious: Windows Process Unusual Activity.”
For example, in this case, I launched “lsm.exe” from a temp folder. Three alarms fired (for what was, in fact, the same event), because it met the criteria for all three AI Engine rules. Turning these into events and only have the overarching alarm fire reduces alarm noise.
| Suspicious: Windows Process Unusual Activity “Figure 17. AI Engine Rule |
Quickly spotting the difference between normal and abnormal behavior is the key to defeating attackers. This AI Engine rule set will reveal the presence of abnormal processes trying to hide themselves within the plethora of common Windows processes.