Automated incident response (IR) refers to the process and management for systemic response to a security breach. This method allows a security operations center (SOC) to respond to critical incidents in real time and to triage alarms more efficiently.
Lack of Incident Response Resources Makes Organization Susceptible to Breaches
If your team lacks the resources for thorough response, a breach could be imminent. Operating in an inefficient response model leads to:
- False positives and alarm fatigue that result in periods of threat exposure
- Inefficient fragmented workflows overloaded with mundane tasks
- Inability to manage complexity at scale
To overcome these challenges, SOC teams need orchestration and automation for effective collaboration and response across the environment.
Top 5 Reasons to Invest in Automated Incident Response Tools
1. Better Cross-Functional Communication
Inefficient communication and lack of resources increase the risk of damaging threats slipping through the cracks. Automated incident response tools guarantee all prescribed steps are taken, and in the same order, ensuring nothing is missed — it’s like an insurance policy.
In order to optimize the efficiency of your SOC and reduce human error, you need built-in security incident response playbooks that provide a more attainable and standardized process, which will greatly improve communication across the board.
IR helps security teams automatically bring relevant parties together as soon as a potential breach occurs to mitigate risk and reputational damage. If data has been compromised, having real-time information will streamline interactions between internal and external stakeholders in the event of an attack. This can be crucial to maintaining healthy business relations and trust with all the parties involved.
2. More Bang for Your Buck
If your organization maintains an informal SOC and has limited resources, you may be facing delays in responding to incidents — or threats could be going unnoticed. Many organizations have strict budget limitations and some decide that automated IR is not the top priority; however, a compelling argument can be made to business stakeholders that incident response tools save time which can be directed to more pressing workflows and alerts can be handled by fewer people.
Collecting information security teams need is time-consuming — analysts must to go into each system to review its events to try to understand how the breach took place and what was compromised which greatly reduces response efficiency. Having an automated incident response solution with log management capabilities allows you to search for relevant alarms rather than combing through hundreds — if not thousands — of data points manually. Increasing time efficiency and streamlining mundane tasks helps SOC teams meet other KPIs such as reducing mean time to detect (MTTD) and mean time to respond (MTTR).
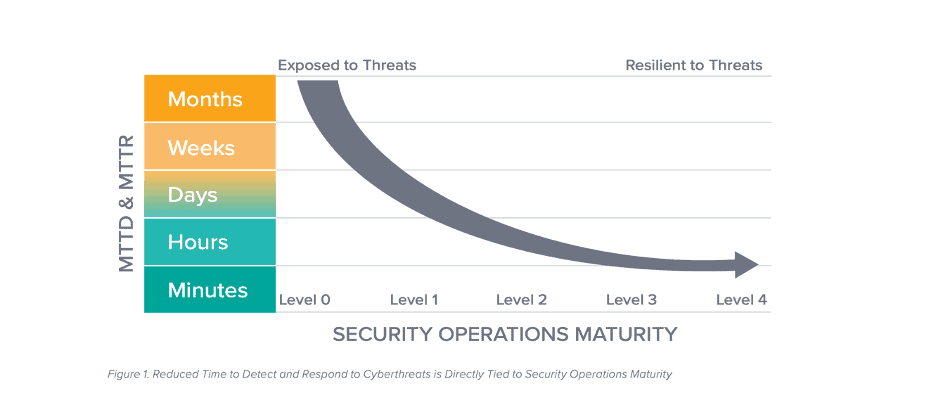
Overall, automated IR tools reduces time and resources providing a positive return on your investment. The consequences of a damaging threat breaching sensitive data before it’s too late will be much more costly to your company’s reputation and finances, than providing upfront costs for SOC tools. With higher security maturity, your team can also grow investor and client confidence across the board.
When growing and maturing your SOC, it’s critical that you evaluate your cybersecurity incident response program’s overall effectiveness. This can help create a valuable case for your board in order to gain future budgetary support. Download 7 Metrics to Measure the Effectiveness of Your Security Operations to understand how your SOC team is performing.
3. Less Stress for Security Teams
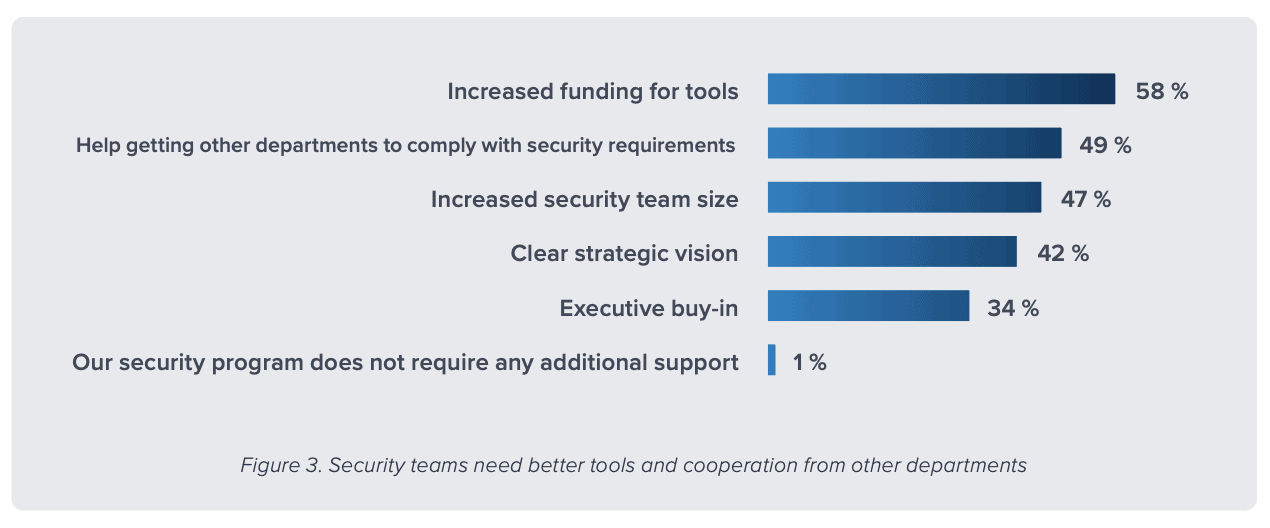
In LogRhythm’s latest research, The State of the Security Team, 75 percent of respondents admit they have more stress now than they did two years ago. With constant change in the industry and an increasing landscape of cyberthreats, security teams have a lot on their plate, yet still lack the necessary tools to effectively manage their workload — 58 percent of respondents believe that their security program requires increased funding for tools to keep up with the burden of securing the organization’s data.
Turnover is an inevitable part of a security team; however, providing incident response analysts with automated IR solutions can greatly reduce stress in their day-to-day responsibilities. Response effectiveness optimizes security workflows, empowers SOC teams, and increases productivity.
From an executive standpoint, IR tools allows CISOs to do their job and stay abreast of any issues by allowing them to tap into their team’s efficient workload potential resulting in minimized impacts of a breach.
4. Limit Exposure to False Positives
It takes longer to separate real threats from the false alarms and the amount of time spent on routine data gathering increases MTTD and MTTR. Using automation incident response to limit the exposure of false alarms enables analysts to pay more attention to the critical threats and increases the aggregation of data, putting the relevant details in front of the right people.
Manually combing through false positive alarms that may turn out to be meaningless can be a continuous and frustrating struggle for analysts.

Automation tools may require investing time up front to create rules that filter future cases, but SOC teams can see a quick return on saved hours after the initial setup. Reprioritizing time to focus away from mundane false positives means that security teams can more frequently tackle real, complex incidents that require skill and creativity.
5. Face Security Threats Confidently
Not having an efficient plan in place can easily cause panic when things go wrong. Automating IR not only allows for the decision-making process to be expedited in the event of an attack, but also ensures that the right decision-makers are clearly outlined which minimizes overlap. With more visibility and elimination of bling spots your team can operate with much more confidence when securing the organization’s data.
SOC teams can use IR tools to decide if they want fully automated playbook actions, semi-automated actions, or approval-based response actions that allow users to review before countermeasures are carried out.
When your team strives towards peak efficiency, it also develops the ability to address more complex use cases at scale. Your team can break down complex use cases into manageable pieces, using automation to decrease the number of steps to the ideal minimum for manual determination. Security automation use cases may include:
- Endpoint quarantine: Identify the network port where a suspicious device is located and disable the port or device
- Suspend users: If your team suspects an account has been compromised, they can halt a user’s account access no matter what device they use
- Collect machine data: Gather forensic data from a suspicious endpoint during a malware investigation
- Suspend network access: If data exfiltration is occurring, your team can kill the connection by updating the access control list used by your firewalls
- Kill processes: Discontinue any unknown or blacklisted process on a critical device with an automated action
LogRhythm’s Incident Response Orchestration Capabilities
Automated incident response tools handle sensitive customer data, preventing attackers from gaining access to potentially damaging information, and causing reputational detriment and distrust.
LogRhythm’s SOAR product, RespondX, enables SOC teams of all sizes to advance to a higher level of security maturity — without adding headcount. RespondX will give your team valuable time back through case management, case playbooks, contextualization, intelligent reporting, and more.
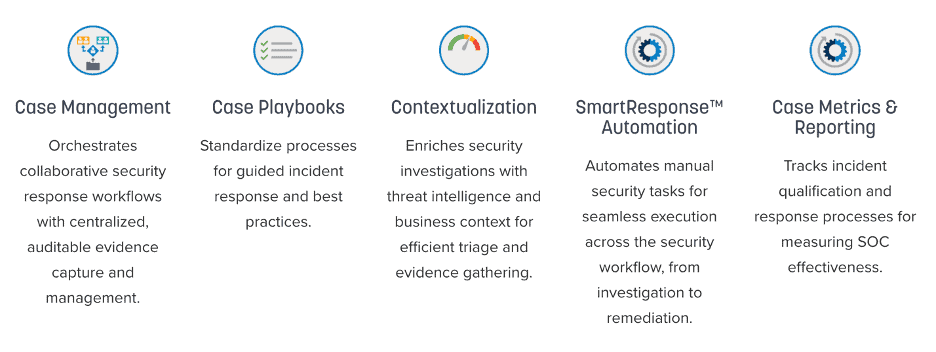
Many organizations think of automated IR as an added luxury, rather than a necessary system, but for a midmarket company with a team of one to three FTEs in their SOC, automation is essential — it enables smaller teams to get through a much larger, more meaningful case load.
“Out of the box, the platform delivers an extensive amount of capabilities and correlation rules that align with today’s threats. The automated responses and SOAR workflows can deliver an increased level of maturity to any sized organization. We’ve had a high degree of success with LogRhythm the past 3 years.” – Vice President, IS Global Security
Take your security maturity to the next level with automated incident response. Learn more about how LogRhythm RespondX can automate your team’s workflow to help detect and respond to incidents faster.

