WannaCry: What We Know
It is worth noting that the first WannaCry infection was reported on February 10th then again on the 25th. We will refer to this as “version 1.” This did not have a widespread impact.
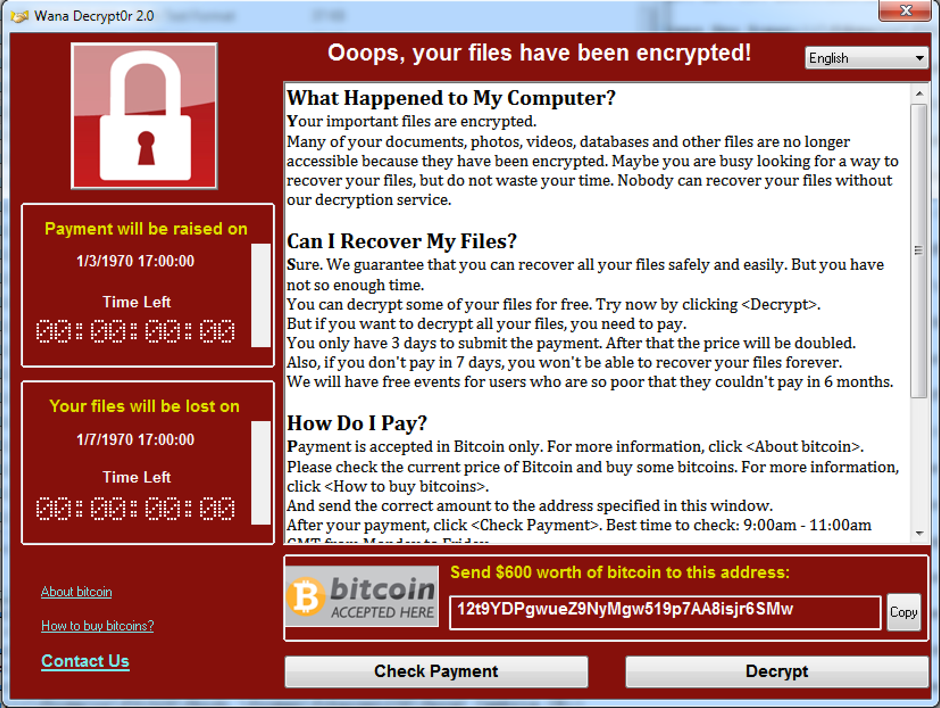
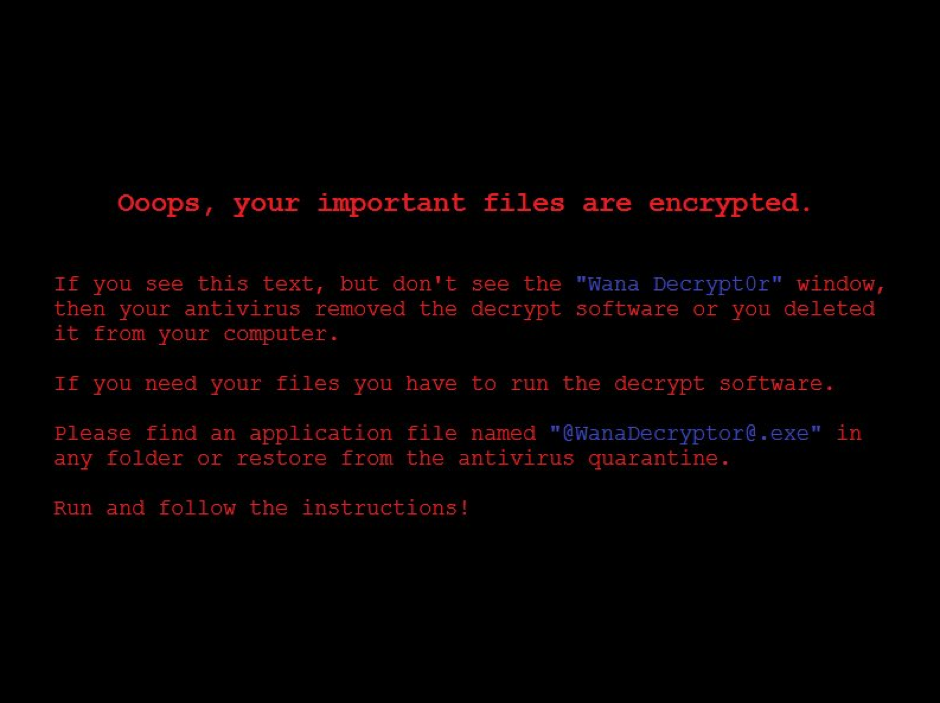
On the afternoon of Friday, May 12th 2017, what we will refer to as “version 2” of WannaCry started to infect systems around the world. WannaCry quickly spread to affect organizations such as the UK’s NHS. An example of the ransom demand can be seen below:
Click on images to expand
Figure 1: Example of WannaCry Ransomware Demand
By around 4:00 PM on Friday, there were reportedly around 36,000 detections, which were spreading globally. There had been some conjecture on social media that a PDF was the cause of the infection, but this was found to be benign. Currently, there is speculation that the initial vector of the attack was through a phishing email. While this is a likely cause, this has not yet been confirmed, and it may take some time before the root of the infection comes to light.
After numerous malware analysts around the world started to dissect WannaCry, it quickly came to light that WannaCry makes use of “EternalBlue”, the exploit, and “DoublePulsar,” the backdoor/implant. The relevance of this finding is key, because back on the April 14th, a hacking group called “Shadow Brokers” leaked a series of files that they claimed were stolen from the NSA.
EternalBlue essentially is the exploit found in WannaCry that takes advantage of exploiting a core Windows networking protocol called Server Message Block (SMB). As SMB is so intertwined with numerous versions of Windows, this exploit can affect Windows XP up through Windows Server 2016.
For reference, this vulnerability was addressed in Common Vulnerabilities and Exposures (CVE) ids CVE-2017-143 through 148. Microsoft did, in fact, release a patch for this vulnerability on March 14th (in Security Bulletin MS17-010); however, companies that did not apply this patch have been vulnerable ever since. Despite Windows XP being already past end–of-life, Microsoft issued an emergency patch to address this vulnerability on Friday night. This was done as a good-will deed in order to help customers who are still running Windows XP to avoid the spread of WannaCry.
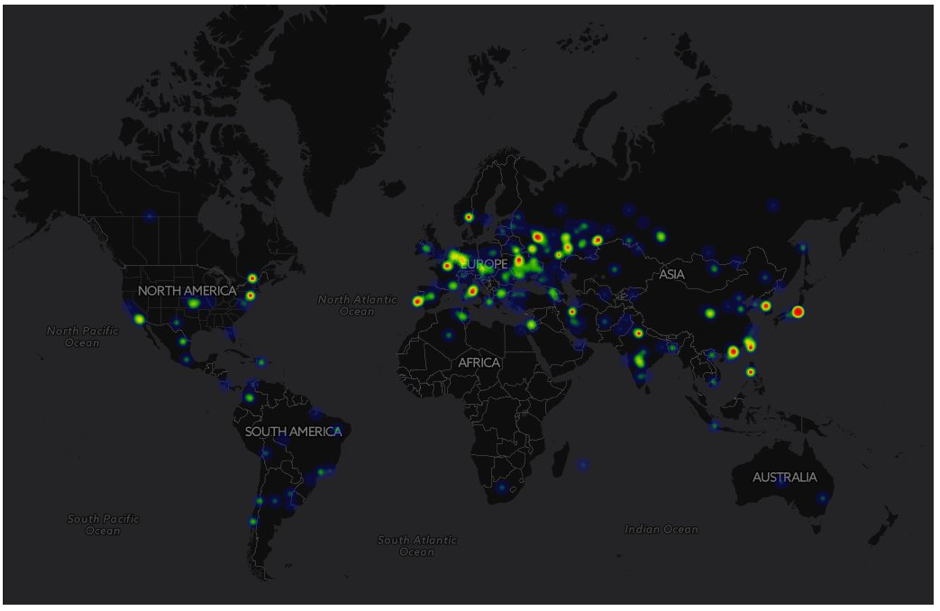
By Friday night, the National Crime Agency, Interpol, and numerous other organizations around the world had issued statements to notify and warn businesses in their corresponding countries of the wide-scale attack. Below is a map of infections that had occurred between Saturday (May 13th) and Sunday (May 14th). By that time, around 60,000 computers in 74 countries were infected. Companies in many industries were affected including: global shipping, auto manufacturers, health care, and educational institutions.
Figure 2: A Map of WannaCry Infections as of Sunday, May 14th (via @malrhunterteam)
By Saturday afternoon, Edward Snowden had commented on the drama underway. Snowden made a clear statement about NSA involvement in the attack: “Despite warnings, @NSAGov built dangerous attack tools that could target Western software. Today we see the cost.”
By Sunday evening, the BBC had reported that there are now more than 200,000 computers infected in over 150 countries, according to Europol. Microsoft later blamed WannaCry on “NSA Vulnerability Hoarding Program.”
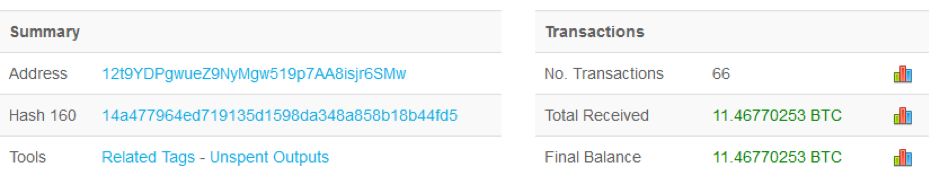
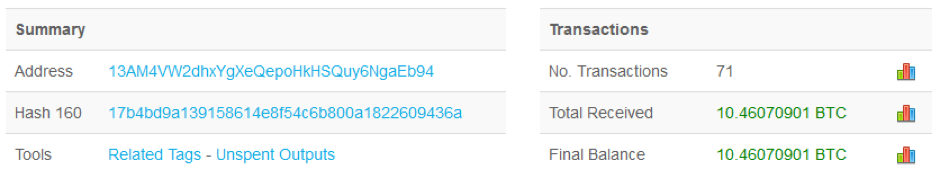
As of Monday morning, BlockChain reports the following statistics showing how many transactions and the resulting BitCoin balance for each of the three BitCoin addresses supplied within the malicious file. This translates to approximately $51,290 in revenue for attackers.
Figure 3. Bitcoin Payments for WannaCry Ransom (via https://blockchain.info)
High-Level Technical Overview
When the malicious file is run, a number of things happen. First, a call is made to a host. If the connection is successful, the program exits. (Refer to the “Kill Switch” section further down for more.) A Windows service called the “Windows Security Center Service” is created, and shadow copies (which are a snapshot/backup technology built into Windows) are then deleted.
The malicious file then extracts numerous other files, which include multi-lingual files containing the ransom note in 28 different languages, a background display image which gets set as the background/wallpaper for the infected system (shown below), and several other files which play a part in the encryption, communication and decryption stages.
Figure 4. Background Image Used for Infected Systems
There are notably three unique Bitcoin addresses, which are used to collect the ransom funds. The communication is first setup using Tor, which is a known program that helps achieve anonymity online.
Files are then modified and all users are given full access rights, and then encrypted. Each file name is appended with the extension WNCRY. For example, if you have a Word document saved as “finance.docx,” this would then be renamed and encrypted to become “finance.docx.wncry.”
As WannaCry uses Microsoft Enhanced RSA and AES cryptography, what this essentially means is that only after the ransom is paid (which is between $300 and $600), the files will then become decrypted and readable once more. Despite reclaiming files, the integrity of the system by this time would be severely impacted—the user or company would still be looking to restore from backup, until such time that a decryption tool is released.
The Kill Switch
A researcher known as “MalwareTech” on Twitter discovered that the domain name that WannaCry tries to first connect to was unregistered. After researching further, he decided to register the domain name. This had a fast-acting impact, because doing so essentially stopped WannaCry from running any subsequent steps. The only caveat of the kill switch is that infected systems that connect through a proxy server out to the Internet are, in fact, still vulnerable.
Advice for Defending Against WannaCry
Due to the widespread impact and scale of this attack, it is advised that anyone running Windows XP through to Server 2012, apply the MS17-010 emergency patch issued on Friday. Details can be found here.
For Windows environments that are still utilizing the SMB networking protocol, it is strongly advised that you consider whether it is viable to disable SMB version 1 at the earliest opportunity. Caution should be taken as there may be legacy applications in the environment that depend on SMBv1. Further instructions can be found here.
In addition, it is recommended that any hosts that are externally accessible over SMB have inbound traffic for ports 139 and 445 blocked, even at the host firewall level.
Internal network security monitoring should be done to monitor for outboud communications to TOR nodes.
There are also several processes and commands that execute, listed below, which should be treated as indicators of WannaCry:
**attrib +h .
icacls . /grant Everyone:F /T /C /Q
cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog –quiet**
There are various file hashes recorded that can be used to input into endpoint-monitoring software. The SHA256 hashes are listed below:
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
0a73291ab5607aef7db23863cf8e72f55bcb3c273bb47f00edf011515aeb5894
428f22a9afd2797ede7c0583d34a052c32693cbb55f567a60298587b6e675c6f
5c1f4f69c45cff9725d9969f9ffcf79d07bd0f624e06cfa5bcbacd2211046ed6
62d828ee000e44f670ba322644c2351fe31af5b88a98f2b2ce27e423dcf1d1b1
72af12d8139a80f317e851a60027fdf208871ed334c12637f49d819ab4b033dd
85ce324b8f78021ecfc9b811c748f19b82e61bb093ff64f2eab457f9ef19b186
a1d9cd6f189beff28a0a49b10f8fe4510128471f004b3e4283ddc7f78594906b
a93ee7ea13238bd038bcbec635f39619db566145498fe6e0ea60e6e76d614bd3
b43b234012b8233b3df6adb7c0a3b2b13cc2354dd6de27e092873bf58af2693c
eb47cd6a937221411bb8daf35900a9897fb234160087089a064066a65f42bcd4
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
2c2d8bc91564050cf073745f1b117f4ffdd6470e87166abdfcd10ecdff040a2e
7a828afd2abf153d840938090d498072b7e507c7021e4cdd8c6baf727cafc545
a897345b68191fd36f8cefb52e6a77acb2367432abb648b9ae0a9d708406de5b
fb0b6044347e972e21b6c376e37e1115dab494a2c6b9fb28b92b1e45b45d0ebc
9588f2ef06b7e1c8509f32d8eddfa18041a9cc15b1c90d6da484a39f8dcdf967
4186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d982
149601e15002f78866ab73033eb8577f11bd489a4cea87b10c52a70fdf78d9ff
190d9c3e071a38cb26211bfffeb6c4bb88bd74c6bf99db9bb1f084c6a7e1df4e
2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41dd
593bbcc8f34047da9960b8456094c0eaf69caaf16f1626b813484207df8bd8af
5ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec
7c465ea7bcccf4f94147add808f24629644be11c0ba4823f16e8c19e0090f0ff
9b60c622546dc45cca64df935b71c26dcf4886d6fa811944dbc4e23db9335640
9fb39f162c1e1eb55fbf38e670d5e329d84542d3dfcdc341a99f5d07c4b50977
b47e281bfbeeb0758f8c625bed5c5a0d27ee8e0065ceeadd76b0010d226206f0
b66db13d17ae8bcaf586180e3dcd1e2e0a084b6bc987ac829bbff18c3be7f8b4
d8a9879a99ac7b12e63e6bcae7f965fbf1b63d892a8649ab1d6b08ce711f7127
f8812f1deb8001f3b7672b6fc85640ecb123bc2304b563728e6235ccbe782d85
11d0f63c06263f50b972287b4bbd1abe0089bc993f73d75768b6b41e3d6f6d49
16493ecc4c4bc5746acbe96bd8af001f733114070d694db76ea7b5a0de7ad0ab
6bf1839a7e72a92a2bb18fbedf1873e4892b00ea4b122e48ae80fac5048db1a7
b3c39aeb14425f137b5bd0fd7654f1d6a45c0e8518ef7e209ad63d8dc6d0bac7
e14f1a655d54254d06d51cd23a2fa57b6ffdf371cf6b828ee483b1b1d6d21079
e8450dd6f908b23c9cbd6011fe3d940b24c0420a208d6924e2d920f92c894a96
0e5ece918132a2b1a190906e74becb8e4ced36eec9f9d1c70f5da72ac4c6b92a
9b3262b9faecb28da4637444f54c060c8d884c3e8cf676815e8ae5a72af48ed4
d5e0e8694ddc0548d8e6b87c83d50f4ab85c1debadb106d6a6a794c3e746f4fa
1465987e3c28369e337f00e59105dea06a3d34a94c2a290caed887e2fed785ac
402751fa49e0cb68fe052cb3db87b05e71c1d950984d339940cf6b29409f2a7c
e18fdd912dfe5b45776e68d578c3af3547886cf1353d7086c8bee037436dff4b
97ebce49b14c46bebc9ec2448d00e1e397123b256e2be9eba5140688e7bc0ae6
4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d
b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25
4870714e654ad4ca7b480b81195f29c56353c6f42d66754ad414c1bc1d25fbb9
bdc8f135484daf898c6d76a244e630a797652b0af1722712515ce844c66bf4af
71b25aeae6470f9ab93db1e80a500bf61282ae8dc505a8e3c781309e46037613
963caaac4a537ad1250fe77510906236261bc7b8ac3c72269d6c059cb5f8f71d