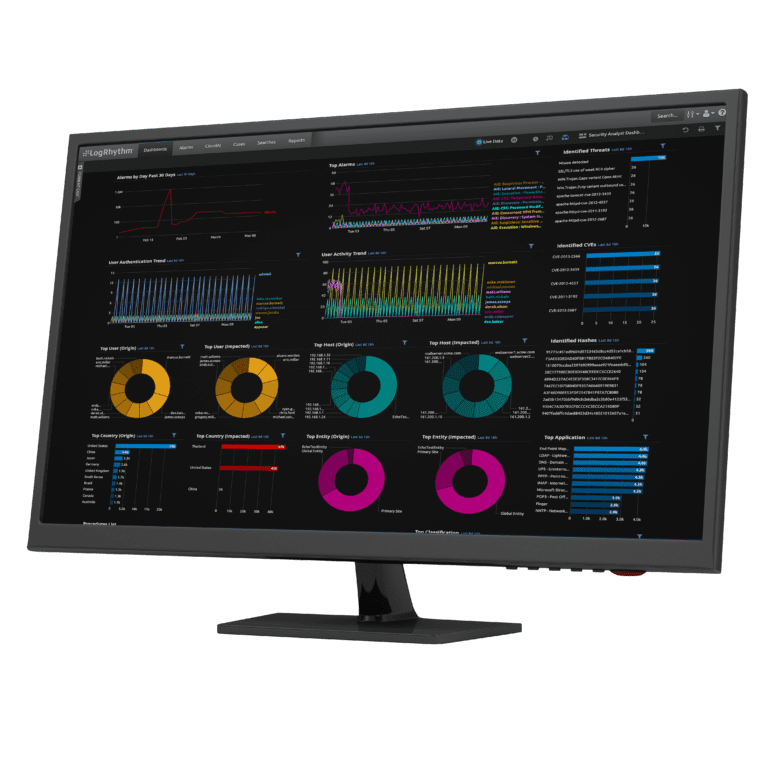
Worried that threats are slipping through the cracks? If your team is facing alarm fatigue — manually combing through false positives — it’s likely they are missing the real threats. They can’t work quickly enough to keep up with the data to be analyzed.
LogRhythm’s comprehensive approach to security analytics helps your team improve detection accuracy and efficiency so they can make smarter decisions, faster. Learn more about how real-time security analytics can help you detect user-based threats.
The security operations maturity model
Download the white paper to learn how your organization scores, ways to measure your team’s effectiveness, and how to improve your organization’s overall security posture.
The Security Operations Maturity Model
A Practical Guide to Assessing and Improving the Capabilities of Your Security Operations Center
Use cases for security analytics
There are many ways that your team can apply effective security analytics to improve your time to detect and respond to cyberthreats.

Detect user-based threats
With user and entity behavior analytics (UEBA), your security platform performs profiling against anomaly detection using analytics to detect account takeover, insider threats, and more.
Identify network threats
Network traffic behavior analytics expose attacks that are targeting your networked systems and devices. They also can identify covert channels of communication in your environment.

Expose endpoint threats
Deep, real-time visibility into endpoint and server activities can surface cyberthreats that are targeting your endpoints and servers — including custom malware and zero-day attacks.
Ensure your compliance initiatives
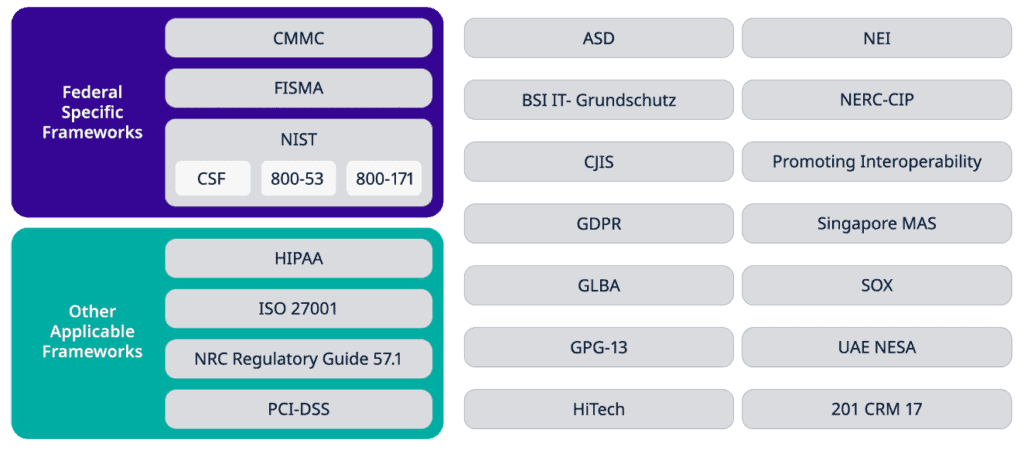
Meeting your organization’s complex compliance requirements can be challenging. LogRhythm provides prebuilt content specifically mapped to the individual controls of each regulation to simplify compliance.
Compliance automation modules help you detect compliance violations in real time to minimize any potential issues. Your team can automate and enforce compliance requirements for PCI DSS, HIPAA, SOX, FISMA, NERC-CIP, GDPR, and more.
91% of companies cannot identify an insider threat
Learn more about how real-time security analytics can help you detect user-based threats.
Detect Insider Threats with LogRhythm UserXDR
Watch now to see how LogRhythm UEBA can help your team detect an insider threat, collaborate to build a case, and quickly neutralize it.
Big data analytics for advanced security
Security analytics holds a lot of opportunity to improve your organization’s security posture. But for some, the cost and complexity of this opportunity can pose an obstacle.
At LogRhythm, we’re focused on simplifying the complex into one efficient, scalable platform so your team doesn’t bear the additional budget or complications of managing multiple tools.
Artificial intelligence and machine learning
Artificial intelligence (AI) and machine learning can significantly reduce the mundane work that your highly skilled team is performing. It makes faster, more efficient, effective, and accurate incident response a reality.
Scenario-based analytics
Your team can use scenario-based analytics to detect and prioritize established threat patterns with techniques such as advanced correlation, statistical analysis, rate analysis, and dynamic whitelisting and blacklisting.
Elasticsearch-powered analytics
With Elasticsearch, your team can search with precision using a combination of contextual and full-text criteria. Elasticsearch is fast, so you can make rapid decisions with precise access to big volumes of forensic data in real time.
Achieve accurate security analytics and threat detection in a single platform
The LogRhythm NextGen SIEM Platform delivers holistic visibility into threats across users, networks, and endpoints with risk-based prioritization powered by intelligent security analytics.
See threats across the entire attack surface
LogRhythm Labs provides threat detection modules with prepackaged content that enable your team to see threats across your entire environment and identify potential threats.
Discover both known threats and never-seen-before threats
The LogRhythm platform uses a variety of techniques to discover both known or unknown threats. By applying machine learning, the platform surfaces anomalies outside of known threat activity patterns.
Easily develop custom analytics
With LogRhythm, you don’t need a team of programmers to develop your own security analytics. Our GUI-based rule builders let your team quickly customize pre-packaged analytics modules or create their own.
Achieve richer visibility with deep packet analytics
LogRhythm NetMon’s Deep Packet Analytics (DPA) provide a richer source of visibility into network traffic, including immediate recognition of personally identifiable information, credit card information, and data indicative of inappropriate movement.
Access threat intelligence feeds
Your team can easily integrate threat intelligence feeds from leading commercial and open-source providers with out-of-the-box integrations, such as STIX/TAXII-compliant providers, to more precisely prioritize alarms.
Advance threat detection with MITRE content
LogRhythm’s MITRE ATT&CK module detects and alerts to suspicious behavior on a per-technique basis helping your team effectively test your security monitoring environment.
Investigate and qualify threats fast
Don’t get bogged down in meaningless alarms. LogRhythm DetectX offers prebuilt, customizable security analytics that surface critical threats to help your team accurately detect and efficiently investigate malicious threats. Watch the demo to see DetectX in action.