How CISOs Can Use a SIEM Solution to Show Value of Their Program
Posted by: Kelsey Gast
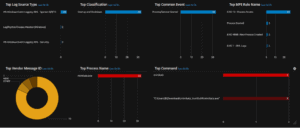
A security information and event management (SIEM) solution provides real-time visibility across an organization’s network and IT environment, making it more efficient to detect and respond to cyberthreats. In order to meet security needs for growing business demands, expanding team…
Read More
November 17, 2020
How to Build and Retain a Strong Security Operations Team
A security operations center (SOC) is like a machine. But like a machine, when one component is not working, performance can come to a standstill. Among the various elements — people, process, and technology — required to run an effective security operation, people…
Read More
November 16, 2020
Accelerate Malware Detection and Remediation with LogRhythm and Cisco Secure Endpoint
When it comes to threat detection, protecting your organization is no easy feat. Despite your best efforts to block threats with detection solutions, the reality is malware can still get into your network. By the end 2021, experts predict there…
Read More
November 10, 2020
How to Build Security Use Cases for Your SIEM
If you’re anything like me, you create an itinerary when traveling to a new place for an extended period. You want to prepare for the conditions you will be in, plan for things you will need, and have a plan…
Read More
November 9, 2020
What is ZeroLogon? How to Detect and Patch
Posted by: Brian Coulson
TL/DR What is ZeroLogon? In Layman’s Terms ZeroLogon is the name for a Microsoft cryptography vulnerability found in CVE-2020-1472 that makes it easy for cybercriminals to hack into your system by impersonating any computer. The Cybersecurity and Infrastructure Agency has…
Read More
November 5, 2020
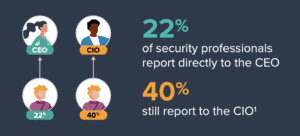
Cybersecurity Infographic: Succeeding as a CISO in 2020
Posted by: Kelsey Gast
CISOs are under tremendous pressure to deliver — our cybersecurity infographic will help security leaders stay informed on the latest industry trends and statistics in order to find success in 2020 and beyond. Don’t miss these key insights! Cybersecurity Infographic…
Read More
November 4, 2020