When your team detects a threat, rapid qualification and response can mean the difference between quick containment and a breach of critical data. Relying solely on manual processes puts your organization at risk.
To reduce response time, you should automate common investigation and response actions with LogRhythm SmartResponse™. By implementing automation via SmartResponse, you can save valuable time and be able to focus on more complex tasks at hand.
What is SmartResponse?
SmartResponse is a capability of the LogRhythm NextGen SIEM that enables automated actions. The capability is effectively a wrapper for windows command line and can automate any action you can run from the command prompt. SmartResponse actions can be fully automated, approval-based, or run by ad-hoc execution. You can also use SmartResponse to automate administrative tasks that your IT or security operations teams frequently undertake in order to save time on manual everyday tasks, such as unlocking user accounts.
You can find SmartResponse plugins in the Shareables section of the LogRhythm Community. LogRhythm provides prebuilt SmartResponse plugins and offers tools to build and develop your own SmartResponse actions. New SmartResponses are continually posted.
SmartResponse plugins can be written in either PowerShell or Python. Requiring little to no effort to run out-of-the-box, PowerShell is the most popular programming language used in SmartResponse, followed by Python for its vast developer base.
Customize SmartResponse Plugins to Fit Your Use Cases
Use SmartResponse plugins to automate a range of activities, from simple unlocks of user accounts in Active Directory to integrating with in-house systems by calling custom compiled binaries. You can incorporate mixed approval and automated settings on SmartResponse plugins on the same alarm. This means one alarm can trigger multiple SmartResponse actions, and these actions can be independently configured to fire automatically or upon approval. You can configure each individual SmartResponse action to your liking.
How can this help you? Let’s say malware is detected on a user account. You can configure two different SmartResponse actions to fire on this malware alarm — one that automatically gathers contextual information surrounding the event and another that disables the logged-in user account upon your analyst’s approval. Through mixed approval and automation settings, your team can begin investigating and quarantining an incident faster and ensure that a threat does not spread throughout your network — while retaining full control of remediation actions.
Find the Right SmartResponse Plugins for Your Use Case
Most LogRhythm SmartResponse actions fall into three high-level categories that are mapped to their specific role in Threat Lifecycle Management (TLM): notification and collaboration, gathering contextual information, and remediation.
Reduce Your Time to Qualify and Respond to Threats through Automatic Notification and Collaboration
When an alarm triggers, notification and collaboration SmartResponse actions fire to alert the team to the situation and get the right people involved. This category of SmartResponse directly reduces your time to qualify (TTQ) and time to respond (TTR) to a threat. Your analysts do not have to wait to check their email or spend time logging into a web console — they receive proactive notifications when an incident occurs and can immediately jump into action.
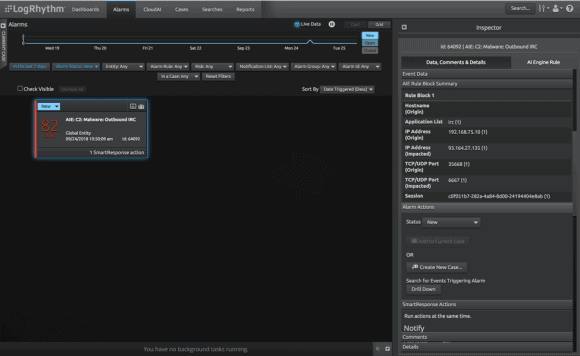 Figure 1: Outbound IRC alarm fires
Figure 1: Outbound IRC alarm fires
Let’s take a look at a real-world example: Suppose LogRhythm AI Engine detects the presence of outbound internet relay chat (IRC) on your network — a chat protocol regularly found in instances of malware. Upon detection, a SmartResponse fires and notifies your team about the alarm via your security team’s Slack channel. SmartResponse email notifications are specific to a user, but newer communication tools such as Slack allow for a collaborative experience and workflow.
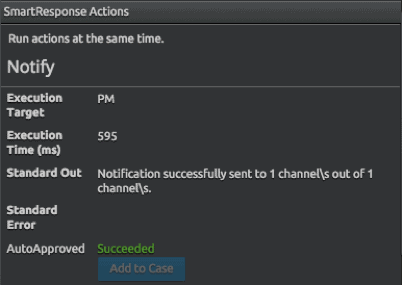 Figure 2: SmartResponse delivers automated analyst notification via Slack
Figure 2: SmartResponse delivers automated analyst notification via Slack
Easily Run Custom Searches for Information Found in Log Data with Contextualization
You are probably already familiar with contextualize actions that are used for looking up a user in active directory or pinging a host. However, LogRhythm offers additional contextualize actions that enable you to customize these searches to query other resources.
When your analyst notices an interesting occurrence in the log data, he can use additional contextualize actions to simplify and expedite the search for more information. Additional contextualize actions are easy to write and implement, and help gather the basic contextual information needed to make a decision and respond to the event at hand.
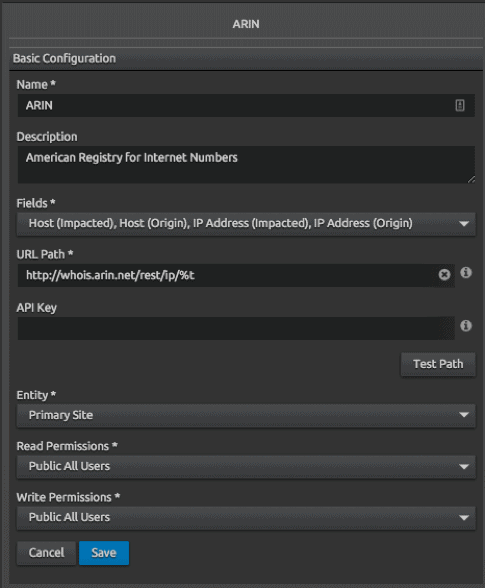 Figure 3: LogRhythm contextualize action configuration works to gather basic information
Figure 3: LogRhythm contextualize action configuration works to gather basic information
For example, if your analyst comes across Windows Event ID 4624, he won’t inherently know where the origin of that ID. Most analysts will turn to Google — or their preferred search engine — and query the unknown ID to learn more information. This means your analyst has had to open a new window, search for the information needed, and navigate to the appropriate third-party website to learn more.
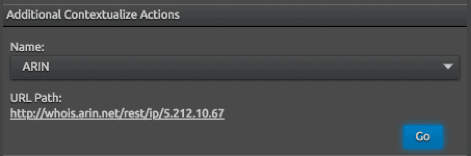 Figure 4: Additional contextualize action on an IP address
Figure 4: Additional contextualize action on an IP address
Additional contextual actions are a feature of your web console and operate similar to Chrome search shortcuts. With LogRhythm’s additional contextualize actions, you can simply click on Windows Event ID 4624 and a new browser is opened to query more information — allowing your SIEM do the searching for you. This reduces the number of clicks you take to get to your information and makes it easy to run custom searches for information found in log data.
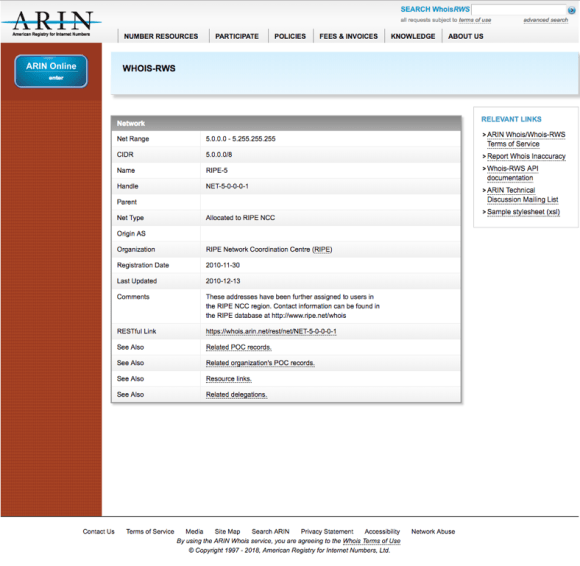 Figure 5: Host information from ARIN
Figure 5: Host information from ARIN
While additional contextualize actions expedite the process of querying for basic contextual information, LogRhythm offers contextual SmartResponse actions that can automate this process and perform more complex searches.
Discover the Important Information You Need Faster by Automatically Gathering Contextual Information
SmartResponse actions that perform contextualization actions allow you to save time by searching third-party platforms directly in your SIEM without needing to log into other applications and manually input security information and event management (SIEM) data.
SmartResponse actions that fall into the contextual information category automatically assemble information and return it to your analysts for analysis, investigation, and case management. They are, however, a bit more difficult to build and implement than your basic additional contextual actions and are perfect for analysts who want to employ their Python skills.
This class of SmartResponse allows you to automate and perform actions such as passing credentials or logging into a system. Contextual Information SmartResponse actions can directly integrate with case for further ease of use.
When an unknown or anomalous event occurs, you will need to gather more information to make an informed decision regarding next steps. Automating contextual information via SmartResponse drastically reduces your TTQ as it helps your analysts decide whether an alarm qualifies as a true threat and incident. It also helps you to determine the scope of impact. When using SmartResponse actions that gather contextual information, your team will be able to discover the important information it needs faster.
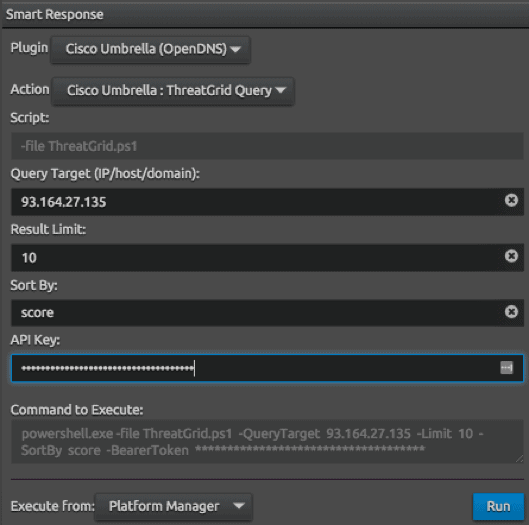 Figure 6: Contextual SmartResponse action is configured to perform a search in Cisco Umbrella
Figure 6: Contextual SmartResponse action is configured to perform a search in Cisco Umbrella
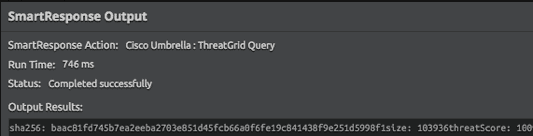 Figure 7: Contextual SmartResponse action query is completed
Figure 7: Contextual SmartResponse action query is completed
For example, when your analysts are alerted to the internal host communicating with an external entity on the internet using the IRC mentioned above, they immediately start working to learn more about the external contact. A contextual SmartResponse action helps you determine the nature of an IP address or hostname. This enables you to tell the difference between an Amazon CDN IP address or an IP address owned by an ISP in Eastern Europe, for example, or a location from which your employees do not typically communicate.
Contextual SmartResponse hits internal or external resources to bring data back into the web console and integrate with alarms and case. For instance, you can configure a SmartResponse to automatically look up the external IP address to find more information about the unknown host. Through such a SmartResponse, you’ll be able to rapidly search for the autonomous system number (ASN) used in this scenario. This means you can determine the IP address used and its accompanying network range to establish whether the host is malicious or not.
Automatically Contain and Remediate Threats
Once you qualify a threat and determine that it is of malicious incident, you must prevent it from spreading further and ensure minimal damage. For example, suppose you determine IRC is coming from a malicious IP address located in an abnormal geographic region. You can configure a SmartResponse to fire upon your analysts’ approval and block traffic from the entire network range associated with the malicious IP by interacting with a list of hosts or ranges configured on your firewall.
 Figure 8: Ad-hoc SmartResponse
Figure 8: Ad-hoc SmartResponse
Additionally, your analysts can use SmartResponse and LogRhythm integrations to rapidly contain and remediate a threat by taking a positive action to prevent a security incident from incurring damage. You can configure SmartResponse actions to add a firewall rule to block traffic through Palo Alto or disable a user account via an integration such as Okta.
While you can manually perform all of these actions, you will typically have to take the time to log in to other resources or systems such as an AD or a firewall provider. With LogRhythm SmartResponse, you can perform all remediation actions from within the SIEM and reduce this login time to a simple click of a button to expedite threat response.
You can queue up SmartResponse actions to execute only upon approval from an analyst or tiers of SOC analysts. This gives your team the speed provided by effective automation while also ensuring that actions do not execute until an analyst has reviewed it.
The LogRhythm SmartResponse Team
LogRhythm has assembled a SmartResponse team dedicated to developing useful SmartResponse plugins. The LogRhythm SmartResponse team will release certified SmartResponse plugins supported by LogRhythm and develop reusable examples that can be utilized by SmartResponse authors. Our SmartResponse plugins are based on and inspired by the work that LogRhythm customers, employees in the field, and partners are doing.
As a LogRhythm customer, you can develop your own SmartResponse plugins and post them to our Community and use or modify those posted by other LogRhythm users to fit your own security needs.
Check Out New SmartResponse Plugins and Integrations Now Available on the Community
You can configure SmartResponse actions to integrate with and help your analysts work within the following third-party contextualization providers:
- Active Directory Account Management: Actions used to disable, enable, unlock, and get info about an AD Account
- Cylance: Obtain info about a host or quarantine a file
- Palo Alto Networks: Manage lists of hosts to block or whitelist
- Fortinet FortiGate: Manage lists of hosts to block or whitelist
- LogRhythm Case Management: Actions can create a new case or add to an existing case
- Windows Log Off User: Forces a log off of a user on a Windows host
- Okta: Disable users, force password resets, and obtain additional user info
- Slack: Notify or communicate with users or an entire channel of users
Remember, this is not a comprehensive list, but a sampling of the most recent content available at the time of this post.
Check out all of the available SmartResponse plugins today to fully automate your SOC and maximize your security resources.
