At LogRhythm, we know the foundation of security information event management (SIEM) is collection. That’s why we’ve focused our efforts supporting as many log sources as possible and making it easier for customers to get into the system with our latest SIEM release, LogRhythm SIEM version 7.11.
LogRhythm 7.11, which releases on Jan. 5, expands our library of supported sources, enhances Message Processing Engine (MPE) rule sharing, and adds functionality to the APIs for greater automation. Backed by nearly 20 years of experience in the security analytics space, we’re continuing to keep our quarterly promises to deliver new features and innovation for our customers. Let’s dive deeper into the features of LogRhythm’s latest SIEM release.
Simplifying Open Collector administration
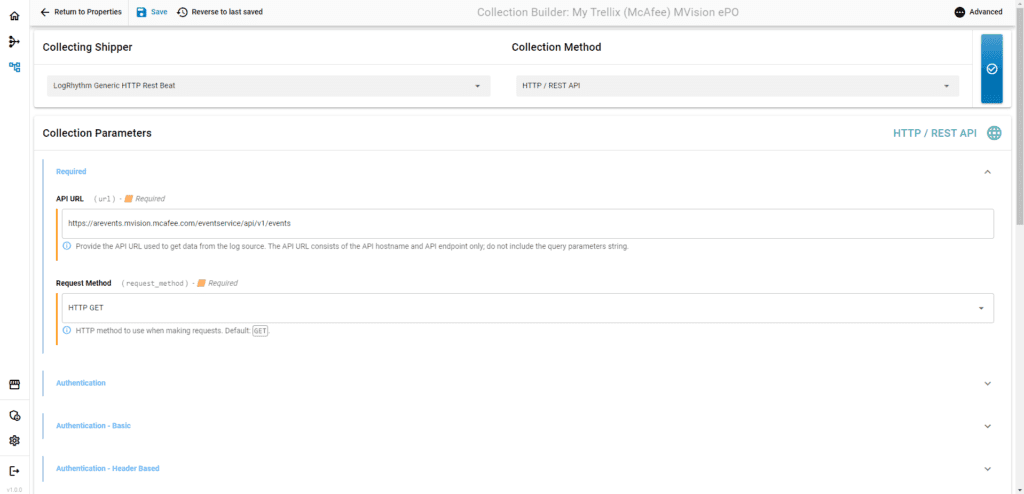
Collection is the heart of the SIEM. Without a simple user interface to configure, test, and manage modern log sources using LogRhythm’s Open Collector, the service that parses JavaScript Object Notation (JSON) data, collection can be difficult for some users. To ease the user experience, LogRhythm launched a new Web UI that runs on Open Collector called OC Admin.
The new web-based UI, available to all Open Collector users (with exception of LogRhythm Cloud and High Availability customers), eases the user experience and greatly reduces the time and effort it takes to configure, deploy, and manage log sources that require Open Collector. Prior to LogRhythm version 7.11, all interactions with Open Collector and its Beats took place from the command line. Rendering certain tasks, such as configuring collection from cloud sources using the Generic REST API Beat, is often difficult.
The latest feature offers an easy-to-use graphical interface to help users more easily manage log sources collected by Open Collector. By using OC Admin, it takes teams a tenth of the time required to configure a Beats configuration since it’s no longer necessary to manually re-enter all the parameters when prompted by Open Collector’s command line tool.
Enhanced auditing support
As a LogRhythm customer, admins on your team often make changes to LogRhythm configurations such as adding a LogRhythm user or editing an AI Engine rule. When making any change, it’s crucial to track what occurred. Without this insight, it’s difficult to monitor for malicious internal and external activity.
LogRhythm recognized the need and now enables audit logging around critical administrative tasks out of the box. And with the SIEM’s powerful searching, reporting, and alarming capabilities, it’s easy to keep track of important changes. LogRhythm 7.11 introduces the Enhanced Auditing feature which enables teams to monitor configuration changes in the following areas:
- AI Engine Rules
- AI Engine Rule Sets
- AI Engine Workloads
- Alarm Rules
- Entities
- Global Log Processing Rules (GLPR)
- Identities
- People/User Accounts
- Log Sources
LogRhythm’s Enhanced Auditing feature lets you easily search through configuration changes to see who made changes and when they occurred. Admins can set up alerts to closely monitor critical configurations and now have greater visibility into users that have access to important data. Monitoring the configuration of the SIEM helps your team ensure system fidelity.
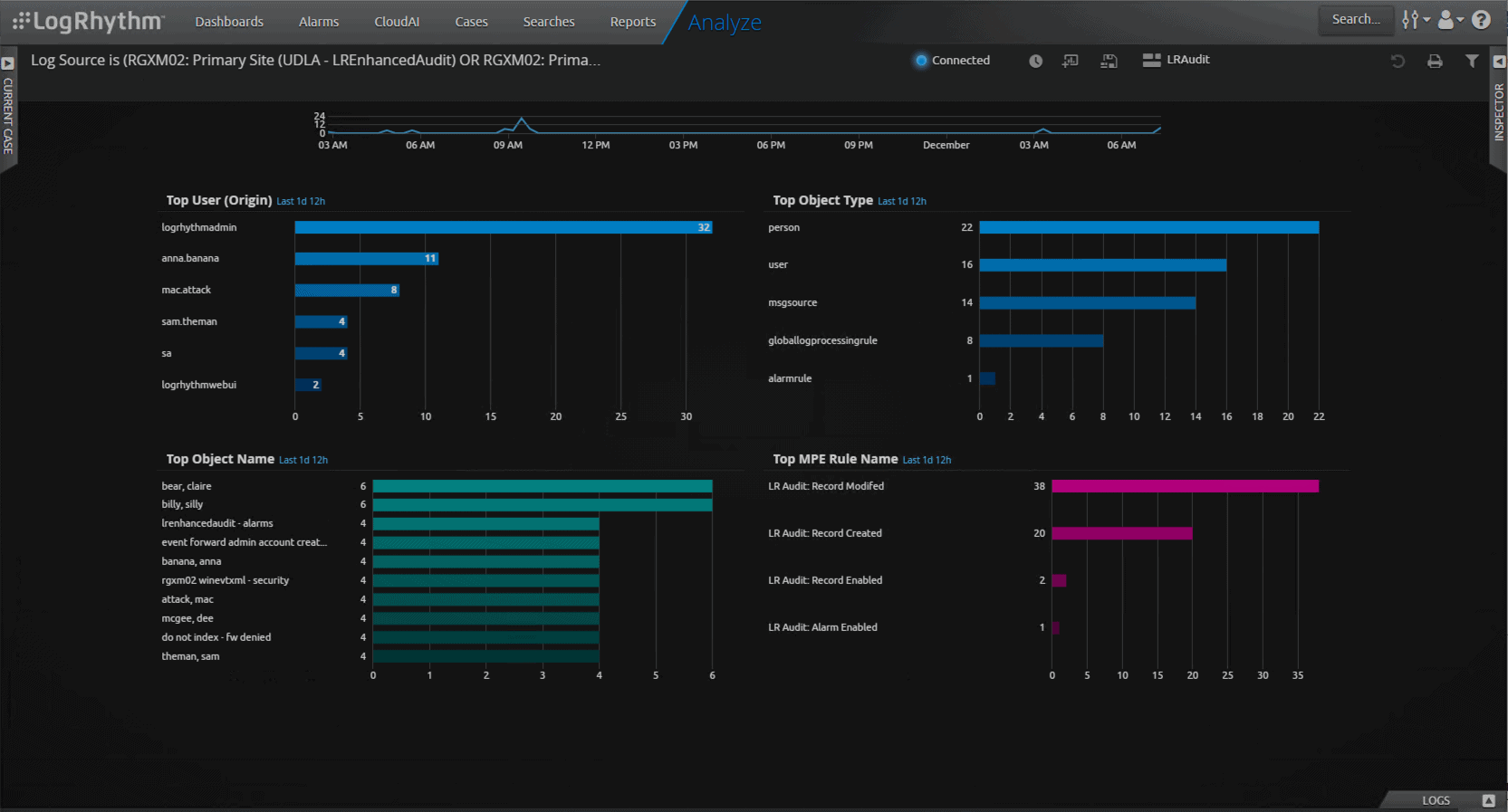
Improved MPE Rule sharing
When it comes to log sources, we know new, uncommon, and unique log sources that don’t have out-of-the-box parsers will always exist. Having a healthy Community that can share parsing rules often saves users time. To share work with peers, it’s crucial to have a reliable and easy way to export and import rules across LogRhythm environments. Today, exporting an MPE rule is simple, but importing one can be challenging.
LogRhythm recognized this challenge and created an easy way to import MPE rules. With LogRhythm 7.11’s MPE Rule Sharing feature, users are guided through an import process that makes it easy to view and customize MPE rule import options.
When importing a rule, users can now clearly see the Common Events and Message Source Types associated with the exported rule. Users can also view the Common Events and Message Source Types that already exist in their systems. By having the import and existing information clearly displayed, administrators select how to handle the import — by overwriting or associating the existing object or creating a new object. This feature helps users easily share their work with peers in the LogRhythm Community.
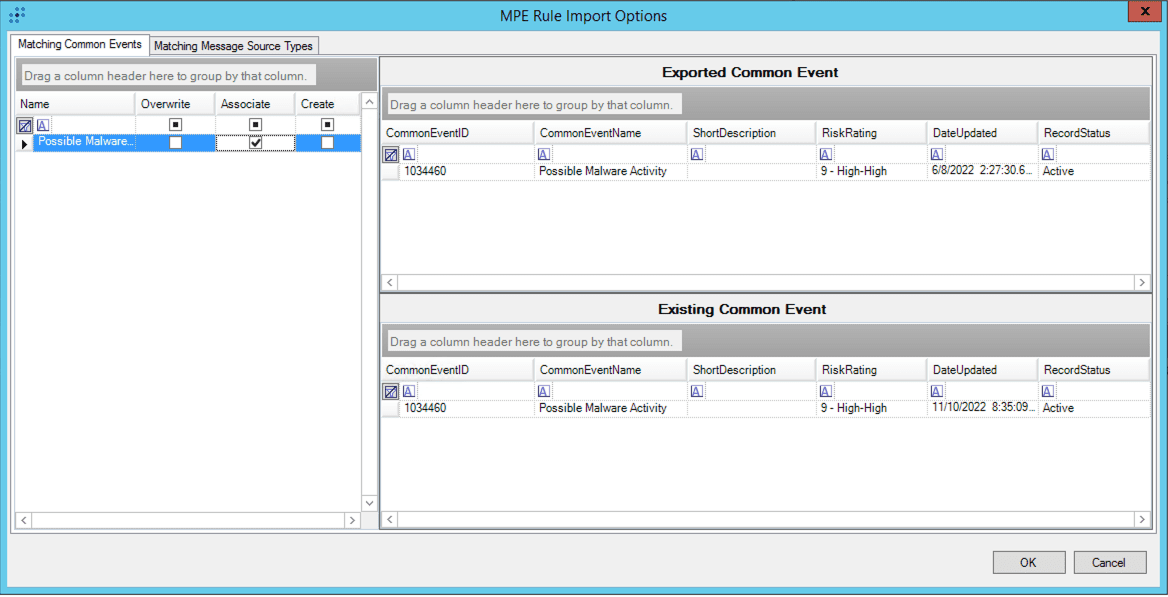
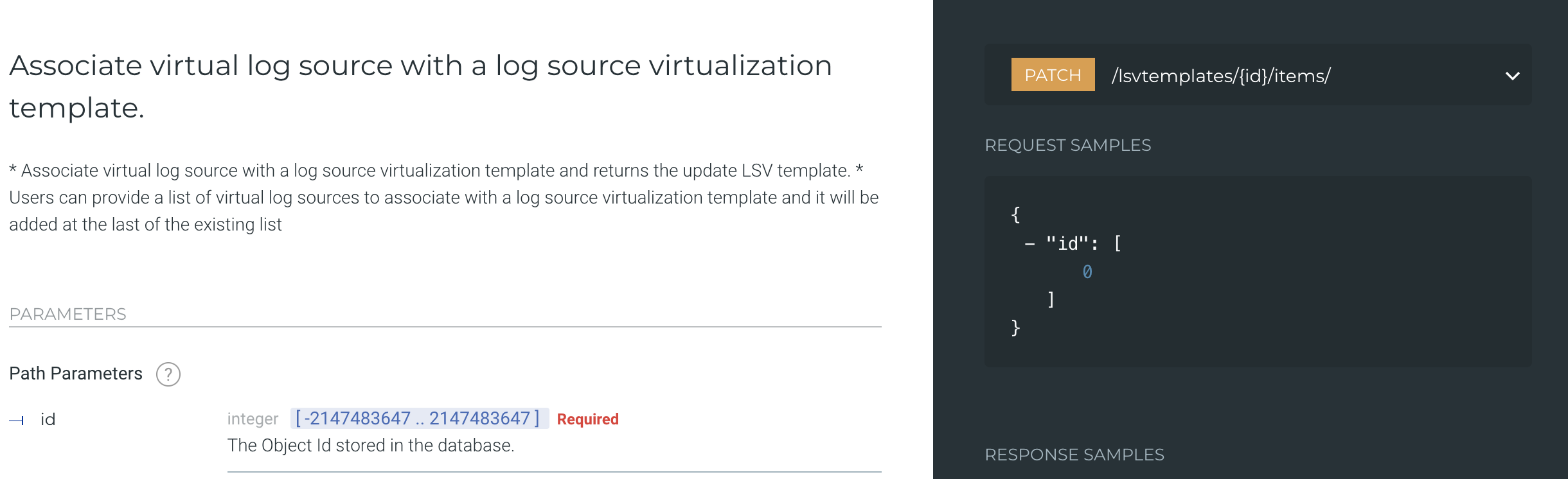
Admin API endpoints for log source virtualization
Automating log source onboarding and configuration through the Admin API helps administrators reduce day-to-day mundane tasks. The Admin API lets administrators take advantage of automation, but only to a certain extent. For example, configuring log source virtualization though the API is not available, making it impossible to automate advanced log source types and customizations.
To overcome this hurdle, LogRhythm 7.11 introduces new endpoints to the LogRhythm Admin API, which lets users configure certain log source virtualization settings and MPE rules via API. The API helps users automate the creation of new virtualization templates and administration of MPE rules, enabling more advanced work with log sources. LogRhythm plans to enhance the log source virtualization capability even further in the next release.
Continuous log source support and parsing improvements
As technology continues to evolve, it’s important to revisit our supported log sources and help you derive greater value. These updates enable better correlation and analysis of specific Beats to obtain a greater understanding of your data. Our latest Open Collector enhancements focus on Google Cloud Platform (GCP)’s Security Command Center (SCC) and Audit. The updates better equip customers to monitor Google Cloud’s centralized vulnerability and threat reporting services.
Additionally, we’ve updated LogRhythm’s MDI Fabric capabilities to enhance multiple MPE rules and signature IDs across Cisco Meraki, F5 Big-IP, VMWare, and Windows WMI. MDI Fabric is a feature unique to LogRhythm that converts complex terminology into human English. This helps analysts easily understand the data they are exploring.
As part of our ongoing commitment to excellence, we’re constantly enhancing our ability to help you collect and receive value from log sources in your environment. A big part of that is updating our tooling — our System Monitor (SysMon) Agent. With this release, we now have additional support to host our SysMon agent on Ubuntu 20 and 22, which gives you another operating system on which to run agents.
New and enhanced LogRhythm SmartResponses™
That’s not all. We’re continuing to add to our growing library of LogRhythm SmartResponses™, our prebuilt automated actions for third-party integrations. These actions enable you to execute preventative actions, accelerate your response, and shorten your workflow. With the LogRhythm 7.11 release, we’ve included the following new and enhanced SmartResponses™:
- urlscan.io
- Microsoft 365 Defender for Endpoint V1
- TrendMicro Vision One
- Microsoft OneDrive/SharePoint
- Microsoft Office 365 V3
SecondLook is now available to LogRhythm Cloud customers
LogRhythm knows how important it is to retain data, but some customers may need longer retention periods than others. With this latest release, we’ve made SecondLook, a tool that enables users to query data and search it in the archives, available to LogRhythm Cloud customers.
With SecondLook, LogRhythm Cloud customers who purchased archive storage can search through their archives using the Web Console instead of the client console. This helps customers save time and be more efficient. SecondLook lets LogRhythm Cloud customers access archive files and search through older log data.

New models in LogRhythm UEBA
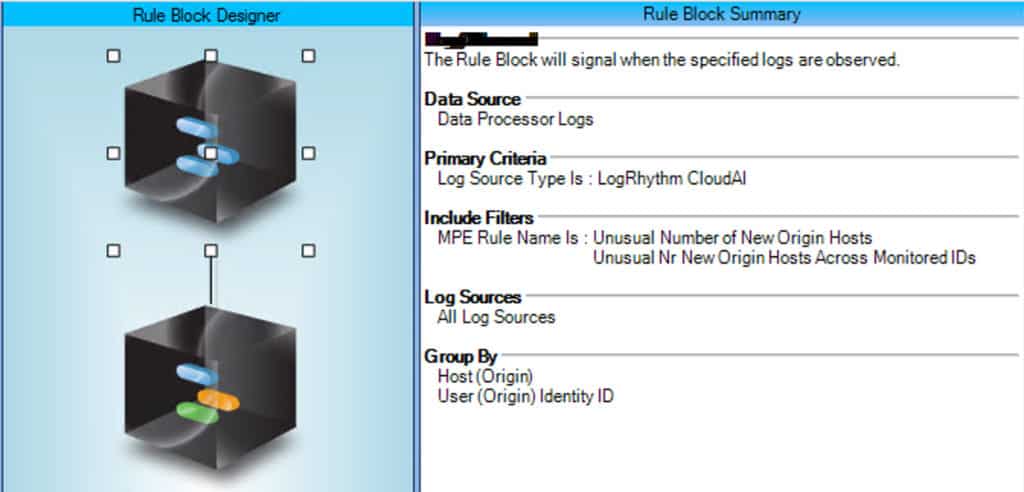
LogRhythm continues to build on its advanced analytics capabilities with updates from LogRhythm UEBA, an add-on to LogRhythm SIEM. Last quarter, we released a model in LogRhythm UEBA that tracks when a user authenticates with a new log source type — either new only for the user in question or new across all monitored users. We’re continuing our moment by launching new models that help address the growing volume and complexity of attacks against Windows systems.
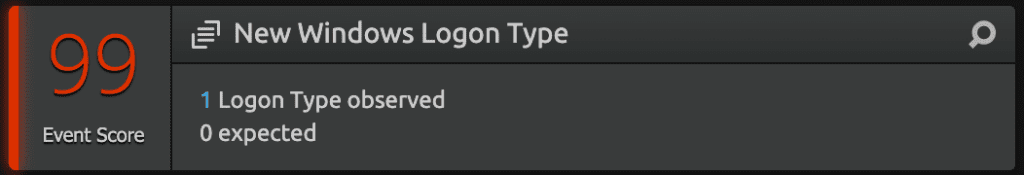
We recently released new models that track Windows logon types. These models trigger when a user authenticates using a never seen before Windows logon type or has not been seen across all baselines of all monitored identities. With these new models, users can now see a ‘type’ of logon.

For example, if you, a person, performs a batch for the first time, that is unusual behavior. Perhaps that individual’s credentials were stolen. This activity will trigger LogRhythm UEBA to alert users to uncover potential attacks. In another example, if a user authenticates using an Interactive logon for the first time, this will trigger the following model.
LogRhythm also launched new models that trigger when a user authenticates using a never before Windows Event ID or has not been seen across all baselines of all monitored identities. The Event ID tells the analyst which type of interaction occurred. For example, a user leverages remote desktop protocol via a Windows server that leverages a New Technology LAN Manager (NTLM) authentication package while other machines use Kerberos authentication package. This will trigger a new vendor Event ID 4776. For a list of all LogRhythm UEBA models, click here.
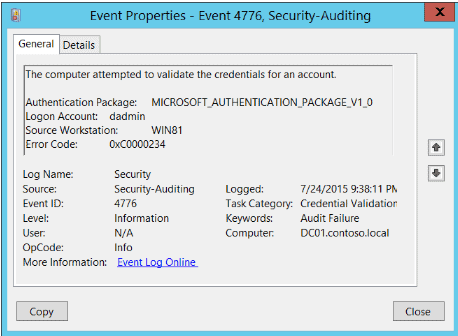
Figure 10: An example of a Windows Event ID showing Event 4776, Microsoft Windows Security Auditing.
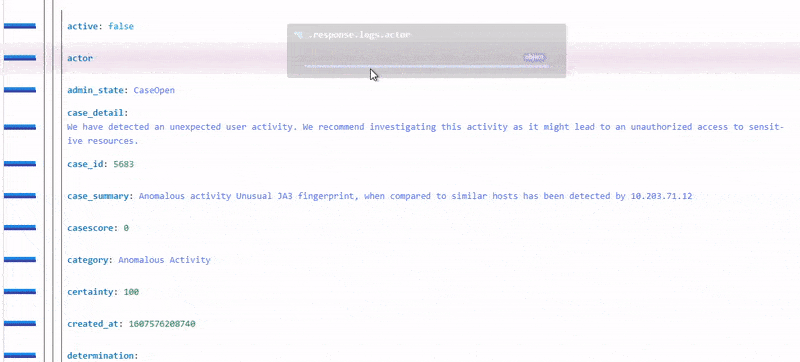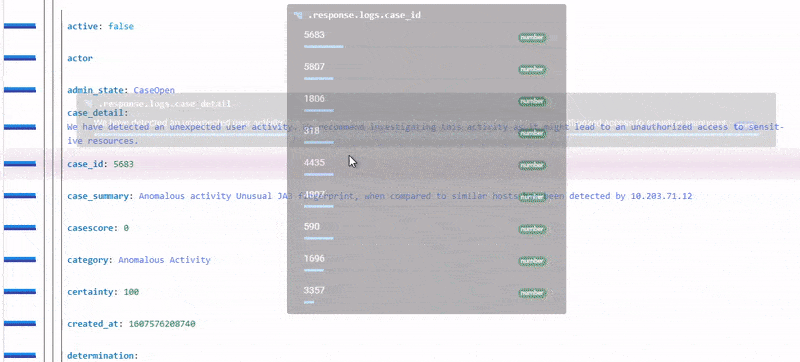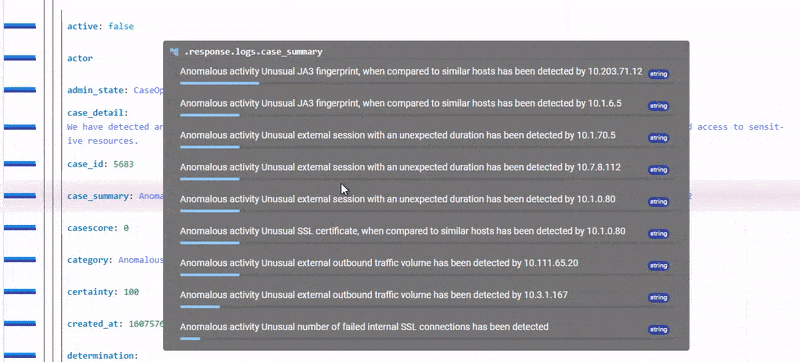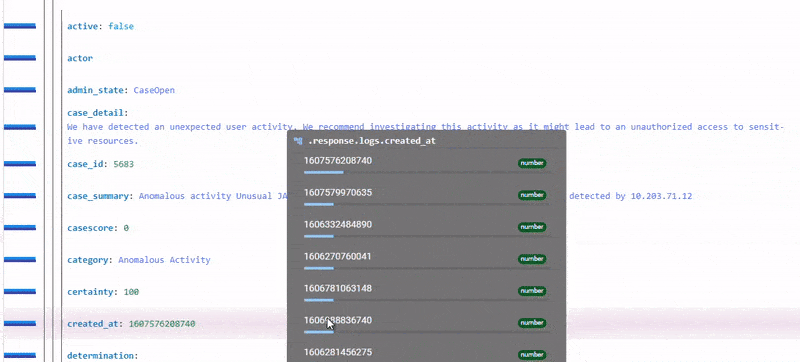
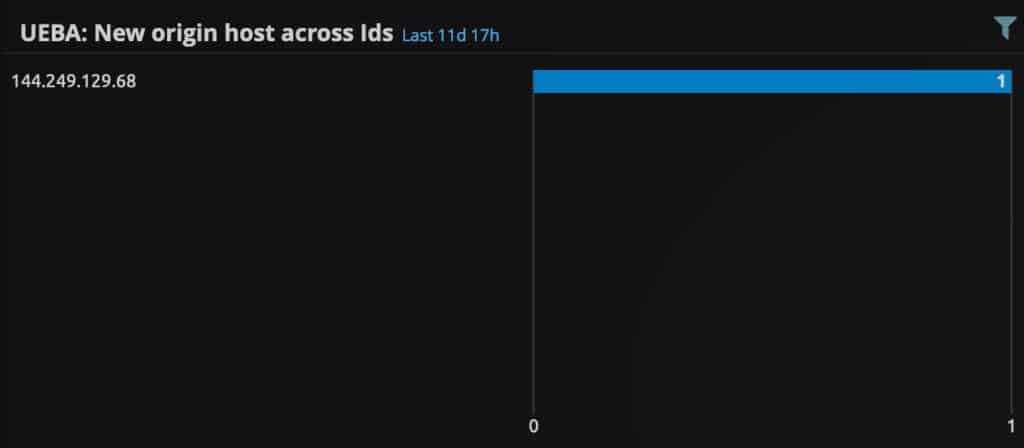
Beyond new models, LogRhythm UEBA is helping analysts detect threats faster by parsing hosts as metadata in the output logs. As attacks are growing more complex, it’s crucial to have a holistic view of what is occurring in an environment quickly. When LogRhythm UEBA detects an anomaly, the first thing an analyst needs is quick access to the contextualization about what triggered the anomaly. The faster this information is exposed, the quicker an analyst can act.
With the latest LogRhythm UEBA release, analysts no longer must go to the raw log to see which host was involved in an anomaly. The host involved in an anomaly is now extracted as metadata in the log. By extracting additional metadata to use in use cases, analysts can combine entities in their environment to decide on the next best course of action. Customers can now create widgets, dashboards, and AI Engine Rules using the host metadata. What’s more, LogRhythm SIEM will also further enrich the log with information about the location, direction, and mapping to known hosts. This leads to a greater mean time to respond and enhances the use of LogRhythm SIEM with anomaly outputs. Click here to stay up to date on what’s new with LogRhythm UEBA.
Getting started with LogRhythm 7.11
This is only the beginning. We’re laying the foundation for bigger things to come for LogRhythm SIEM. If you are an existing customer, you can request a license here. Download LogRhythm 7.11 from Community today! To learn more about more about LogRhythm 7.11 and our quarterly launch, register for the Jan. 12 webinar.