At LogRhythm, innovation is at our very core. While we enhance our product portfolio, we continue to invest in LogRhythm SIEM with our latest release of version 7.12.
LogRhythm 7.12, which is now available, streamlines the process for collecting and monitoring new security data sources and automates log source onboarding, giving analysts a simplified experience and shifting more of their focus from administration to detecting, investigating, and responding to threats. This marks our fourth consecutive quarterly release innovating our products and keeping promises to you.
Enhancing the Admin API
To build off LogRhythm’s initial work in LogRhythm SIEM version 7.11 introducing new endpoints to the LogRhythm Admin API, LogRhythm 7.12 includes additional endpoints needed to configure log source virtualization settings. With this addition, admins on your team can fully automate the creation of log source virtualization templates and virtual log source items.
With the latest version, LogRhythm is also introducing two new administrative functions in the API — Management of Log Source Types and Log Processing policies. This enables your admins to fully automate the management of Log Source Types and Log Processing Policies. The latest improvement enhances the level of automation that LogRhythm performs, helping you reduce mundane tasks and automate log source onboarding.
This feature updates the API to better support the configuration of more advanced and customized log source types. It also lays the foundation to bring additional log source administration functionality into the Web Console. Look for additional capabilities in the next release in June.
Introducing Log Sources to the Web Console
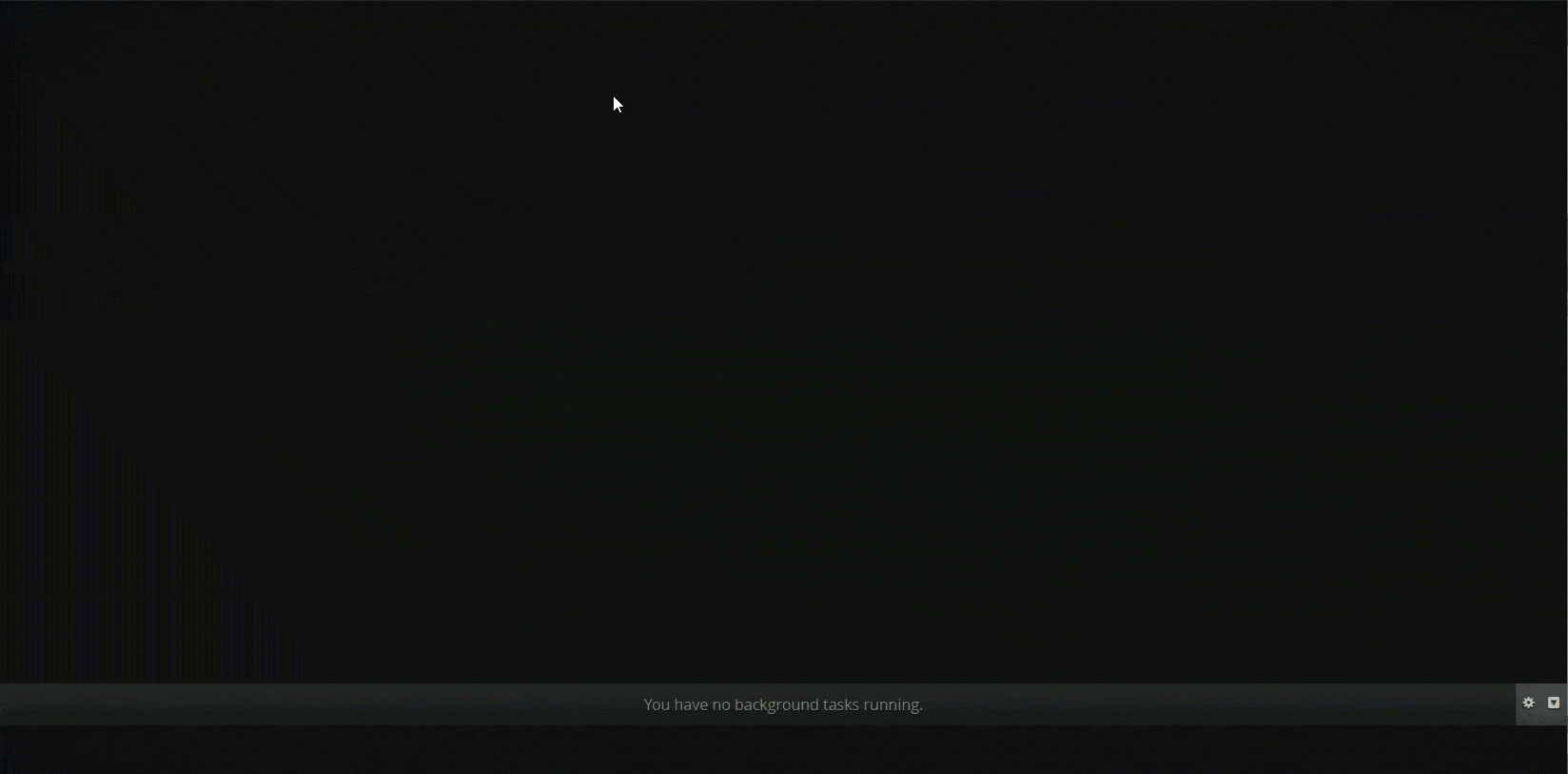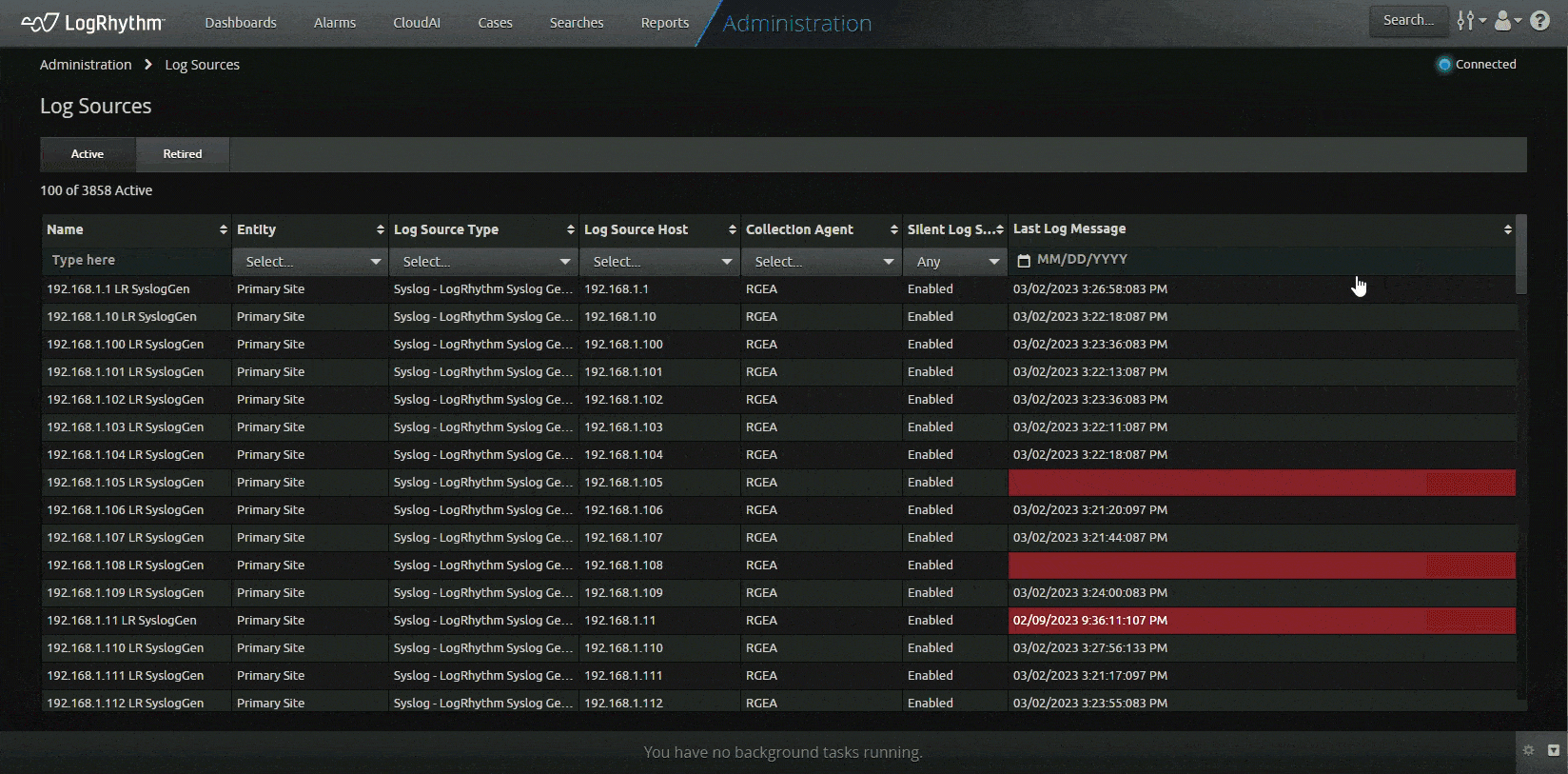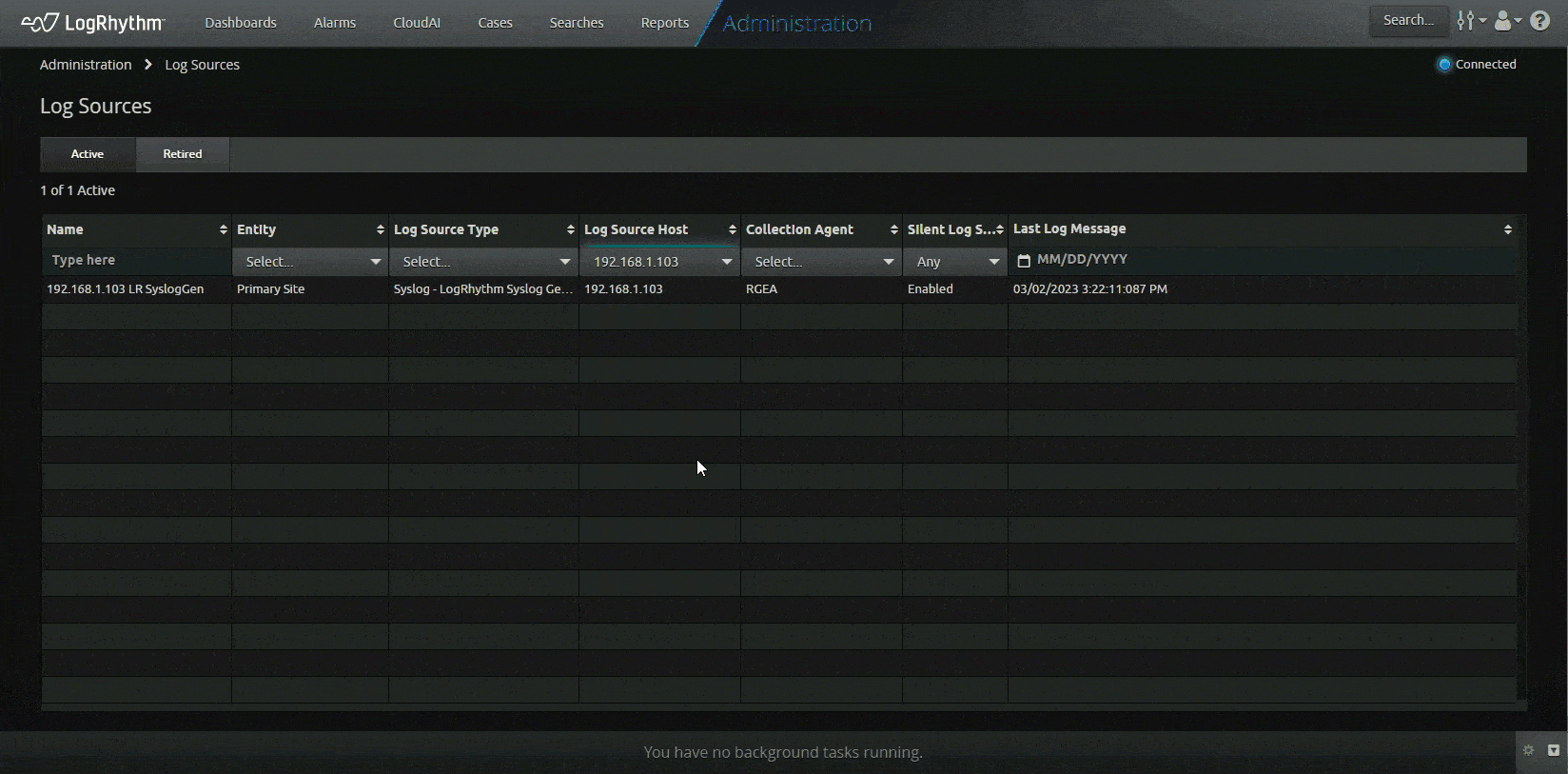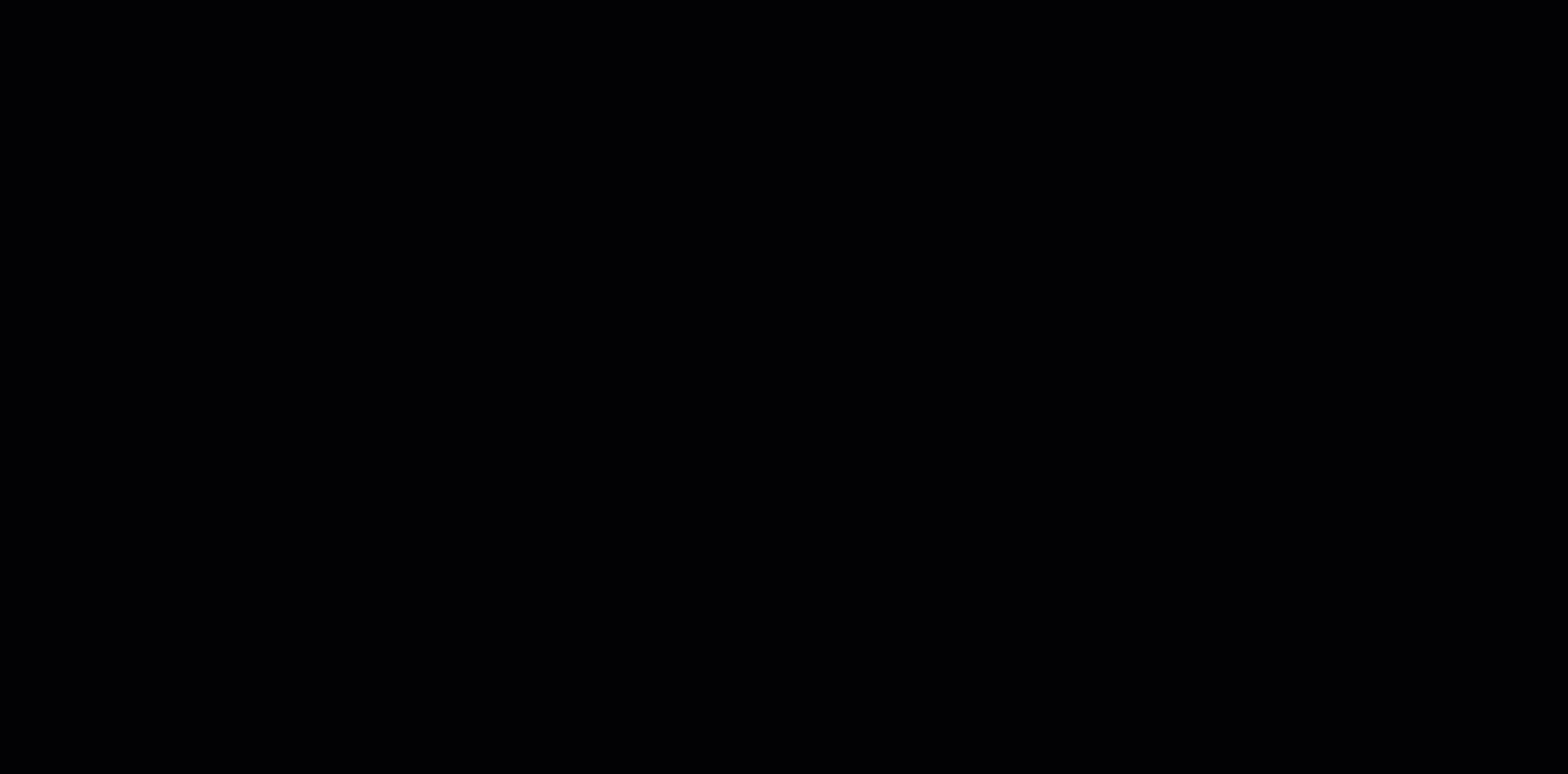
LogRhythm is on a journey to enhance and modernize your experience. With LogRhythm version 7.12, LogRhythm made it possible for you to view and search through log sources through the web console, as well as see the last log message for each log source. Previously, log sources and the last log message timestamp could only be viewed from the client console, prompting you to use both the client console and the web console to accomplish tasks.
Under the Admin menu, you can navigate to the Log Source administration page to view and perform the following:
- View active and retired log source grids. Displayed columns include:
- Name
- Entity
- Log Source Type
- Log Source Host
- Collection Agent
- Silent Log Source
- Last Log Message
- Filter and sort in each column
- User visibility into log sources will adhere to user profiles and permissions
This is LogRhythm’s first step to bring log source management into the web console. This feature unifies administration consoles, saving you time by performing fewer clicks and keeping information in a central location. Look out for future updates next quarter when we plan to announce further improvements.
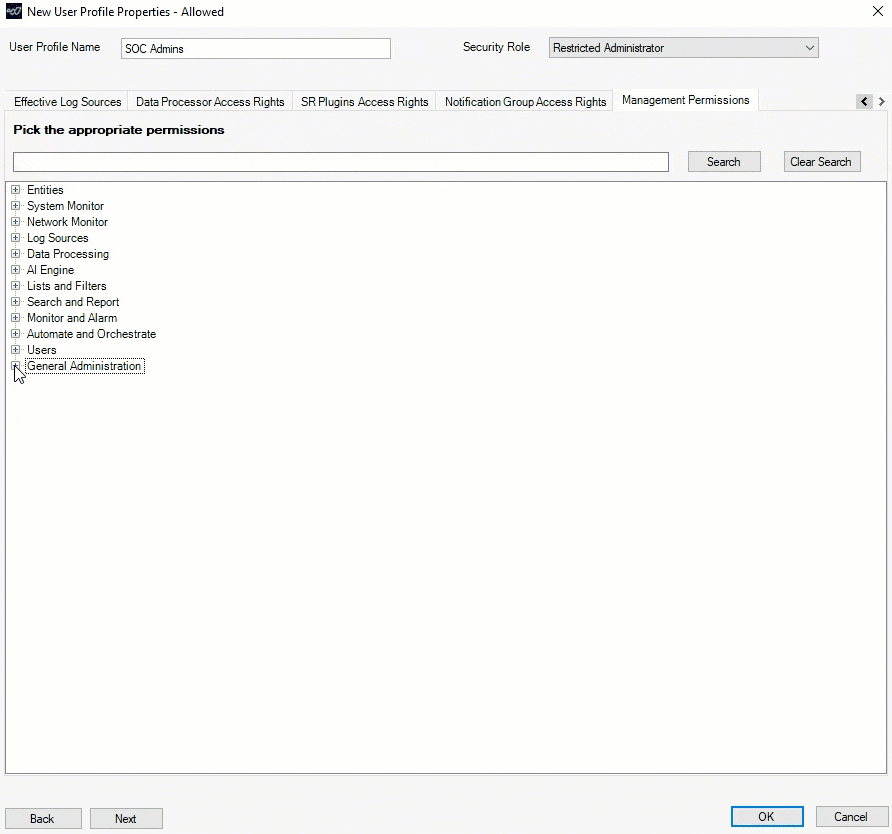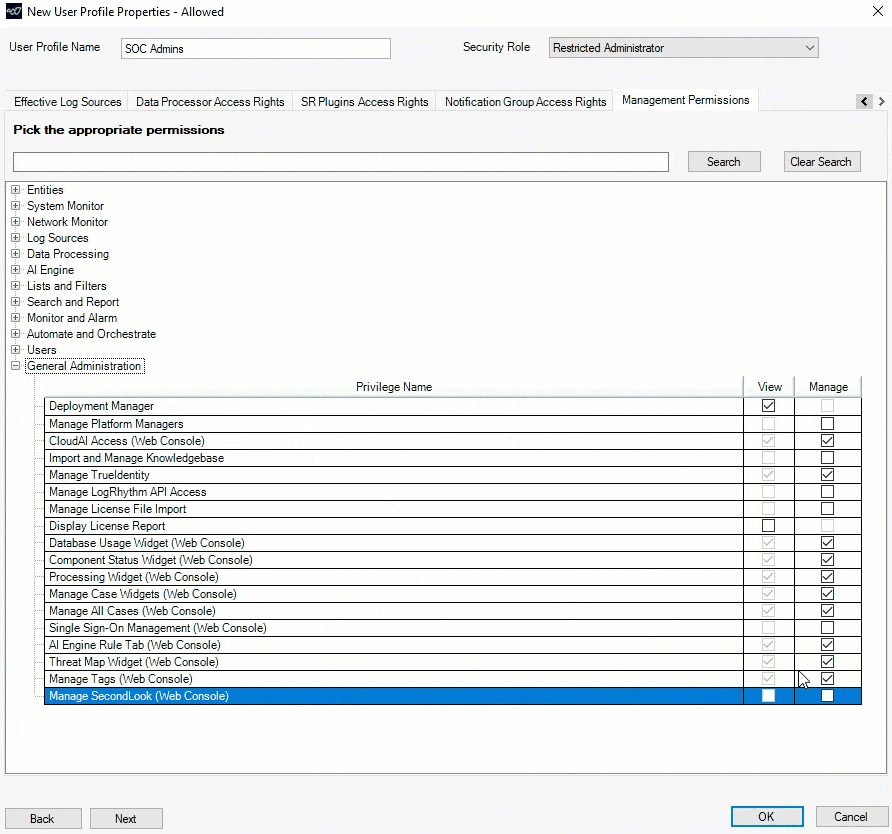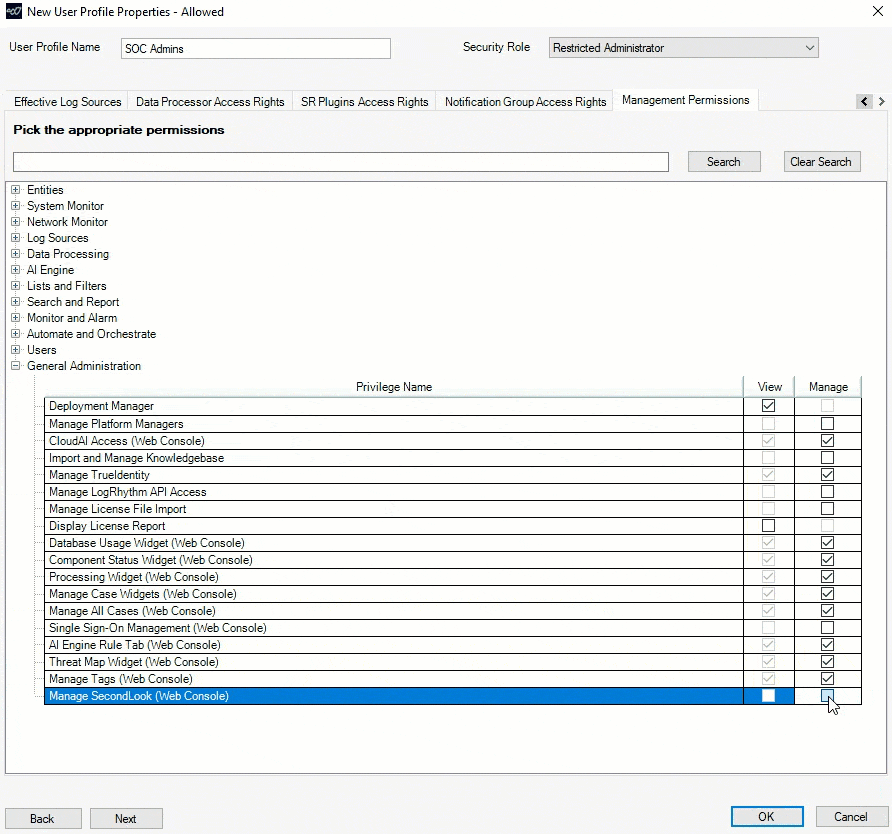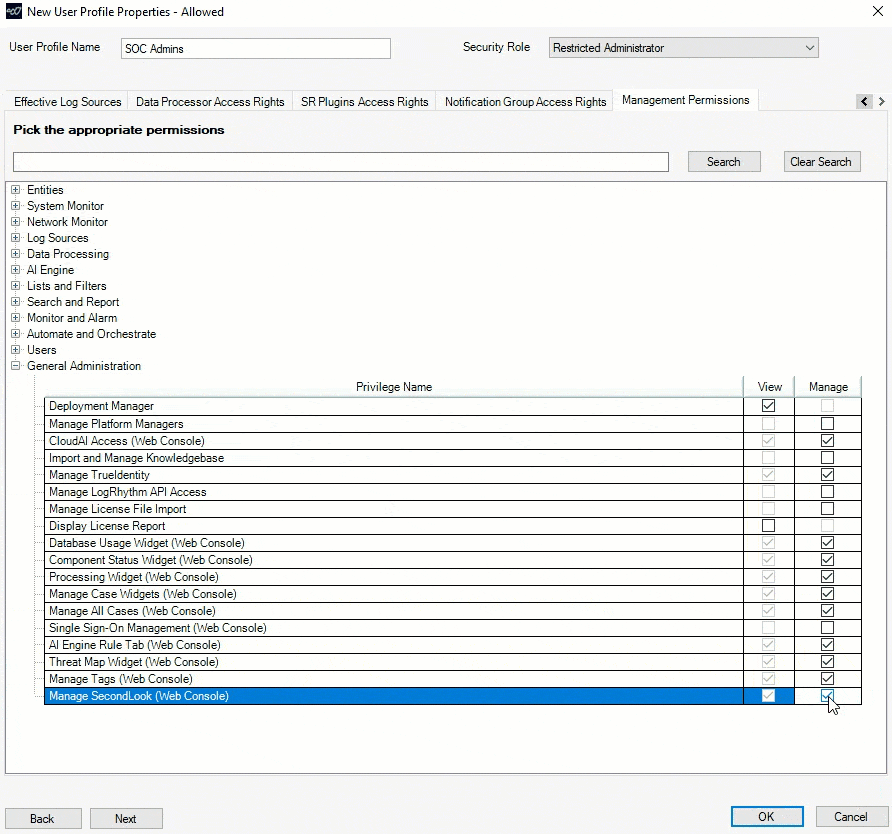
SecondLook features improved administration and workflow
Following the January launch of SecondLook, a tool that enables users to query data and search it in the archives, to LogRhythm Cloud customers, LogRhythm made further updates to improve the workflow.
In response to customer requests, SecondLook now features a quick search function for completed SecondLook restores. Users can quickly search for restored archives with a single click, preventing them from re-entering search filters. This saves LogRhythm Cloud customers time when searching for restored archives.
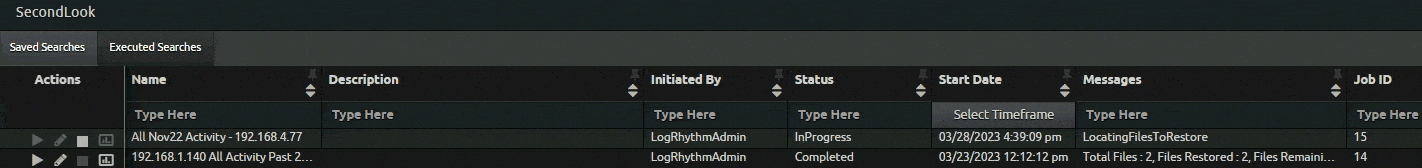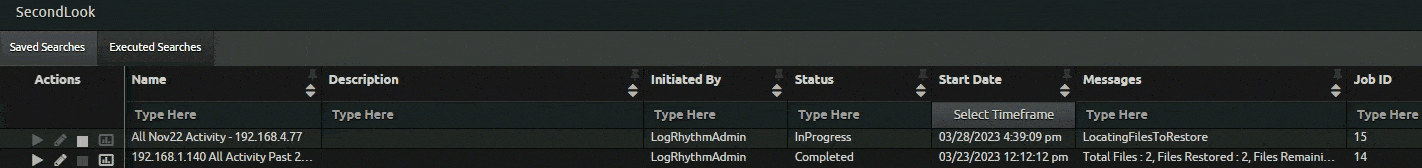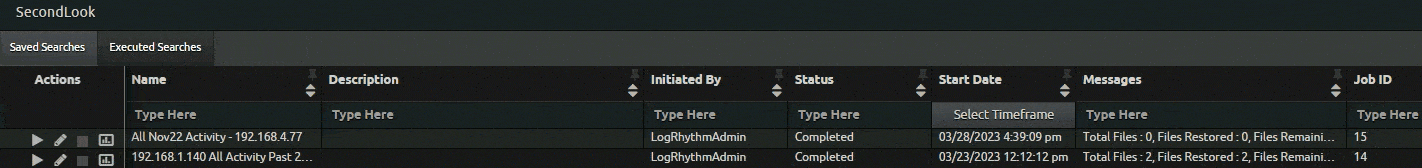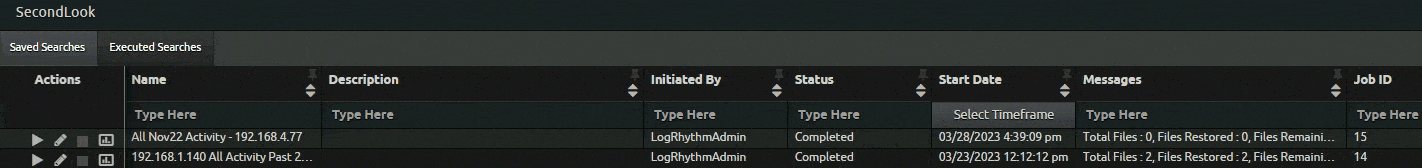
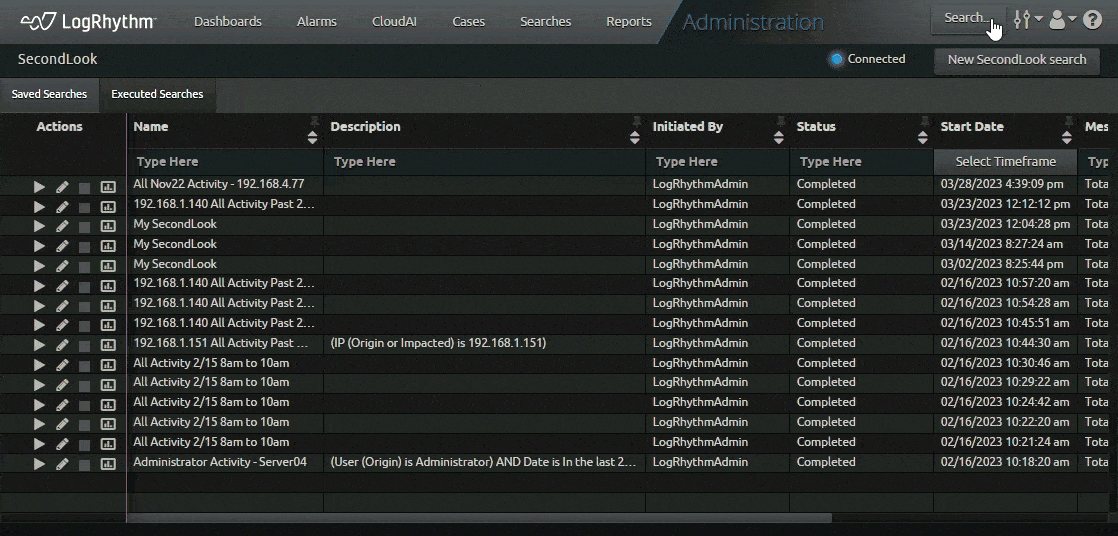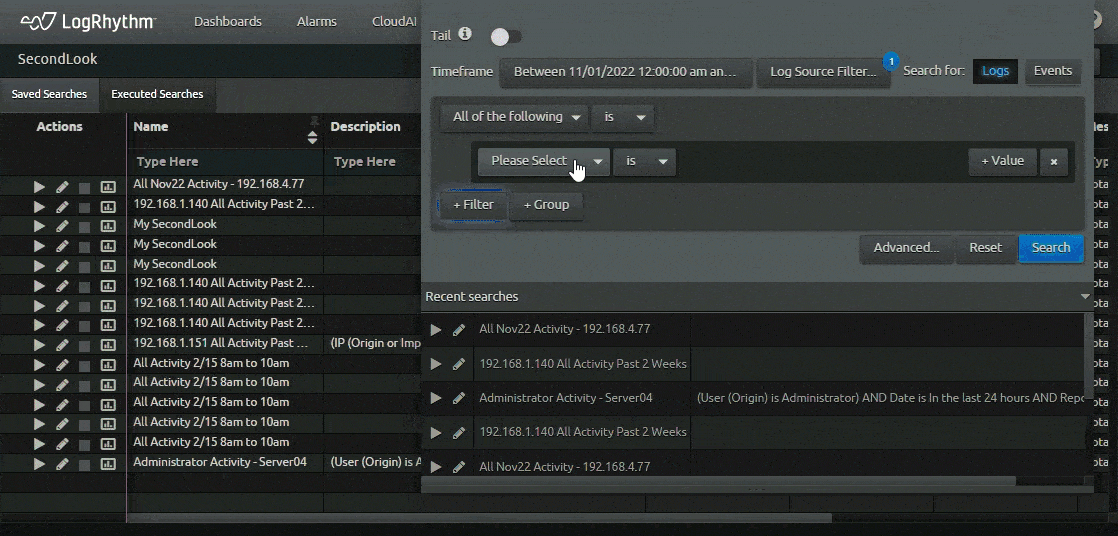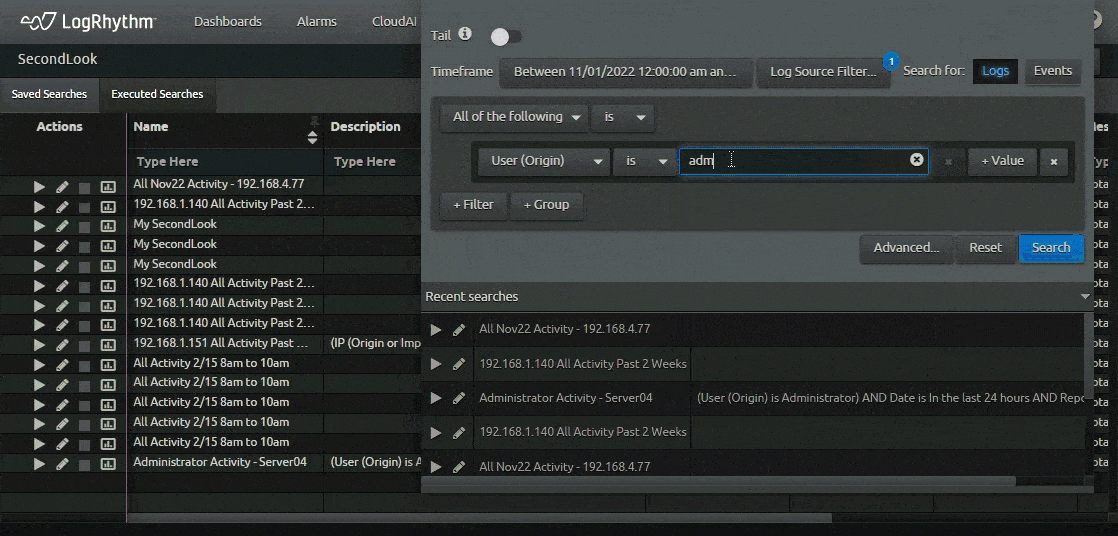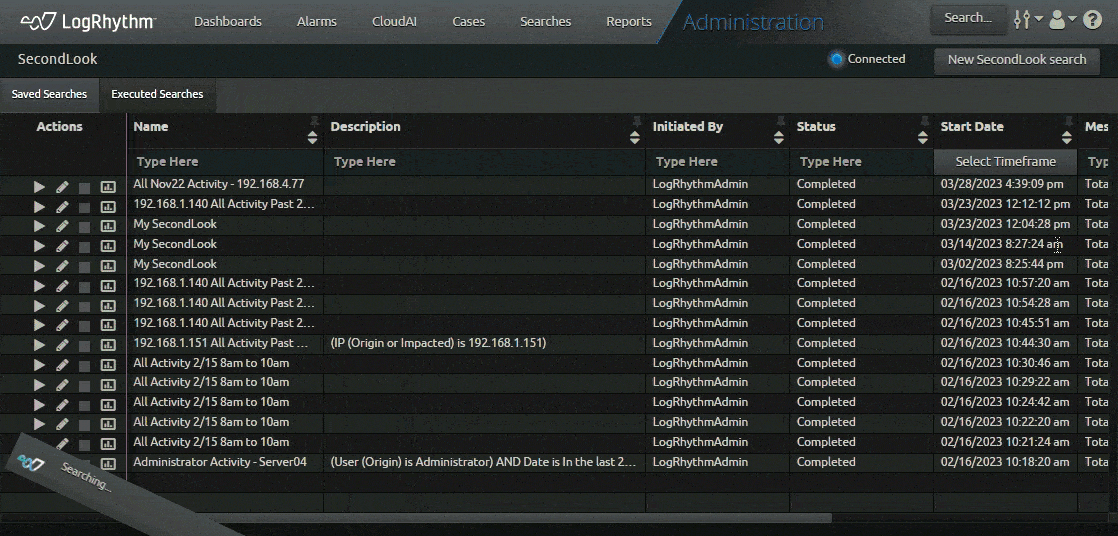
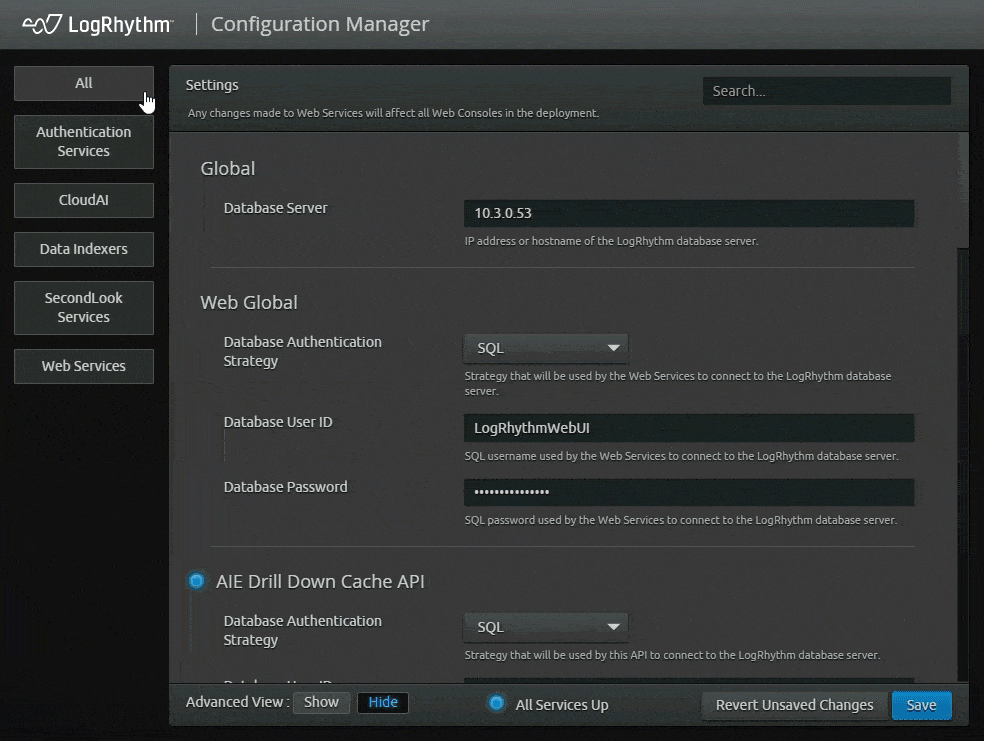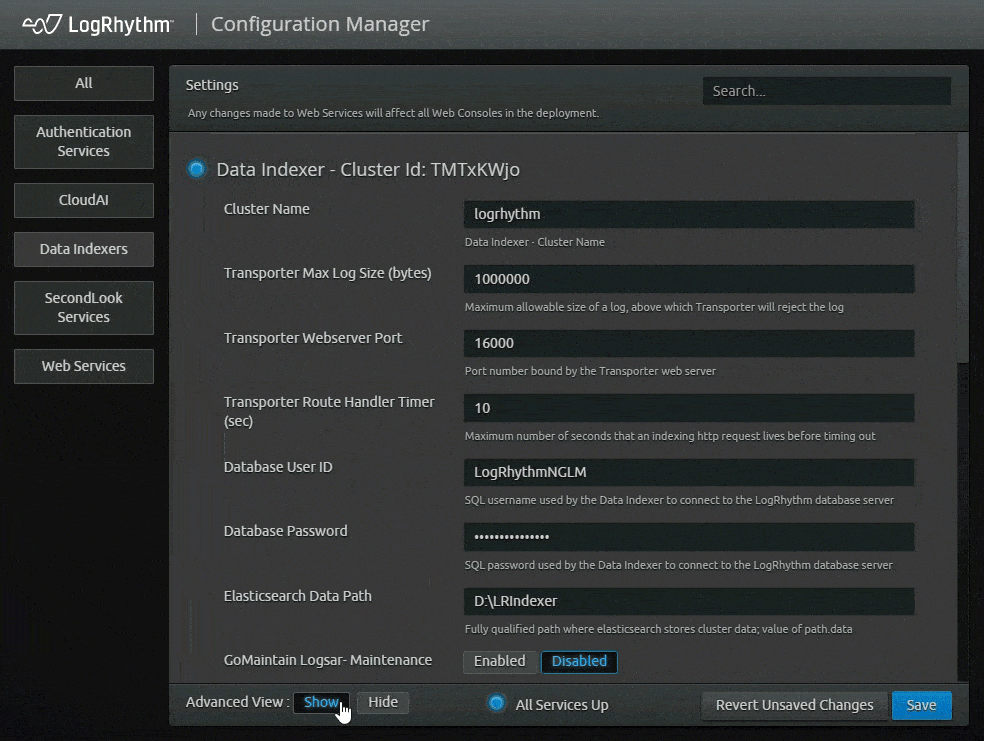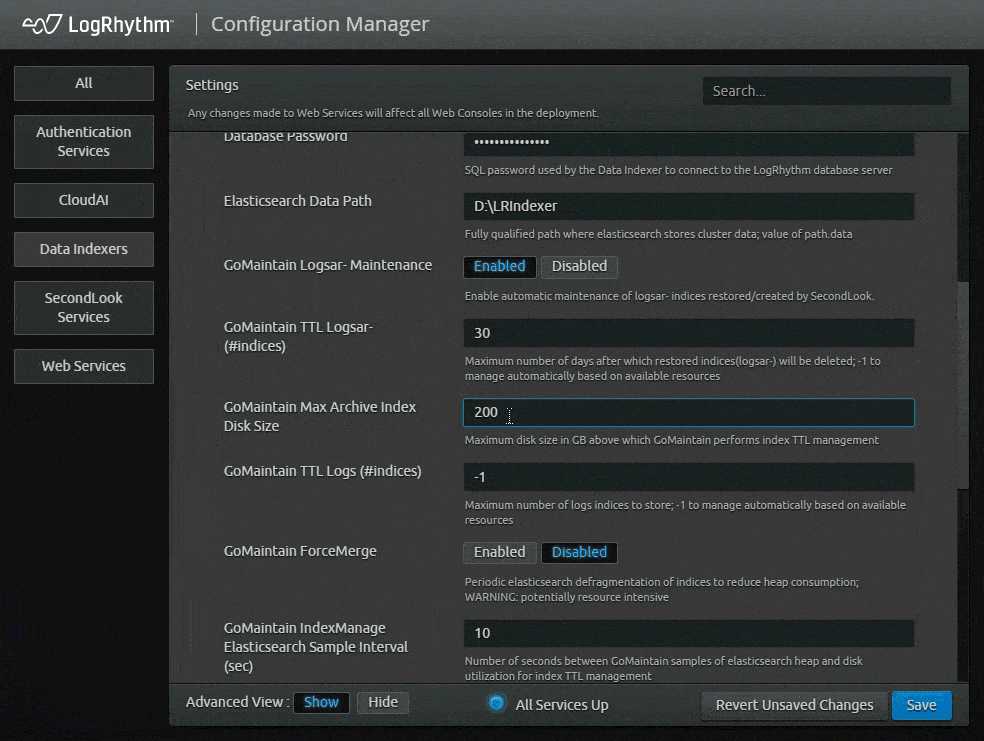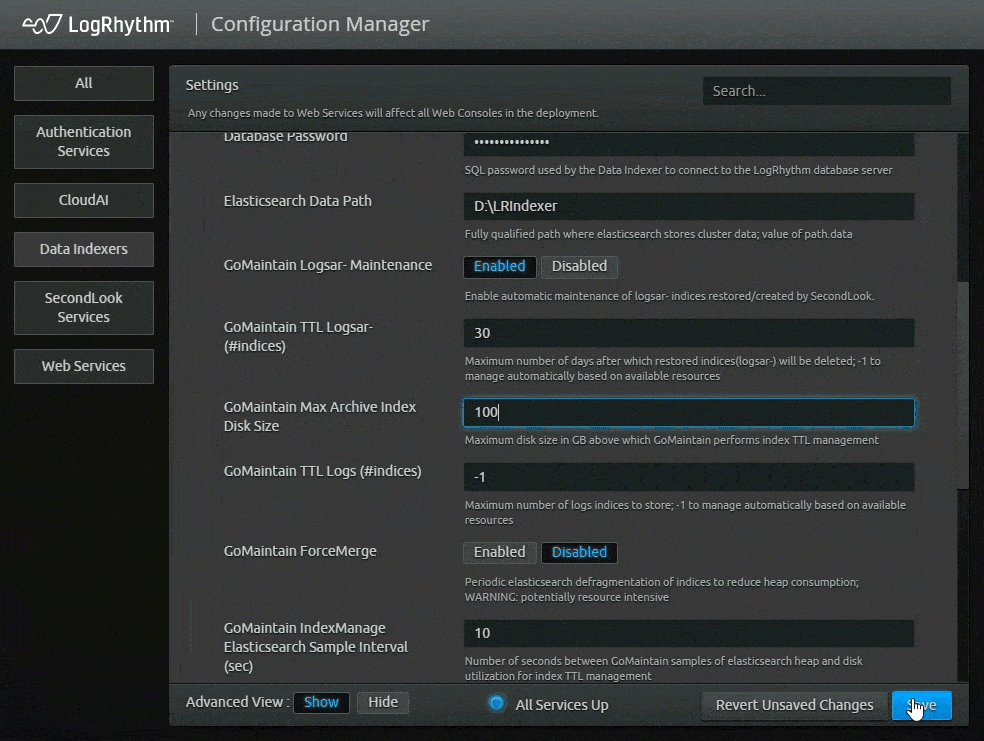
As part of the SecondLook improvements, LogRhythm version 7.12 offers self-hosted customers automatic maintenance of archive indices. With this function, logs that are in the data indexers are automatically deleted based on a time limit parameters customer set. Customers who enable the feature can modify specific settings to indicate how long they want to keep the logs.
This feature lets customers analyze and interrogate historical data more easily. It also reduces administration, saving users time from performing manual clean-up on their own.
SecondLook Role-based Access Controls (RBAC)
For LogRhythm Cloud customers, role-based access controls now offers more granular options for allowing access to SecondLook. Within a user profile, administrators can grant a user access to the SecondLook tool in the Client Console, in the Web Console, or in both consoles.
Enhancing Log Collection with LogRhythm OC Admin
Building off the introduction of OC Admin in LogRhythm SIEM version 7.11, LogRhythm made additional improvements in the latest release to enhance the workflow and make it even easier for customers to onboard log sources. With LogRhythm SIEM version 7.12, customers can now access a simple interface to parse data and centrally manage deployed Open Collectors, allowing for greater automation of the technology.
Additionally, LogRhythm 7.12 enables customers to ingest data from a variety of API sources using OC Admin. LogRhythm expanded its log collection to include the following:
- Prisma
- Symantec Web Secure Service (WSS)
- Microsoft Graph API
- Carbon Black Cloud
- Cisco AMP
- DUO
- Proofpoint
To improve technical support issues with Open Collector, version 7.12 also introduces light administration capabilities within OC Admin. Customers often are challenged with configuring Open Collector or they lack the know-how to fix an issue when something goes wrong. As part of the Open Collector Manage page, customers can perform a series of actions such as starting and stopping, importing, and exporting full configuration, viewing high level configuration, exporting logs as files, and viewing real-time logs in the UI.
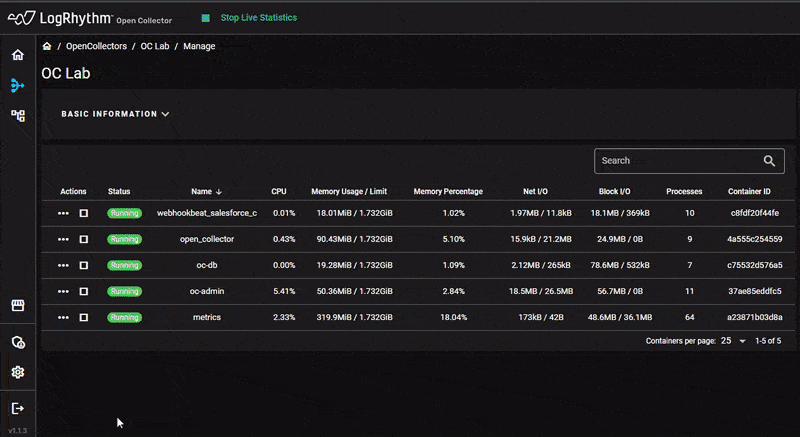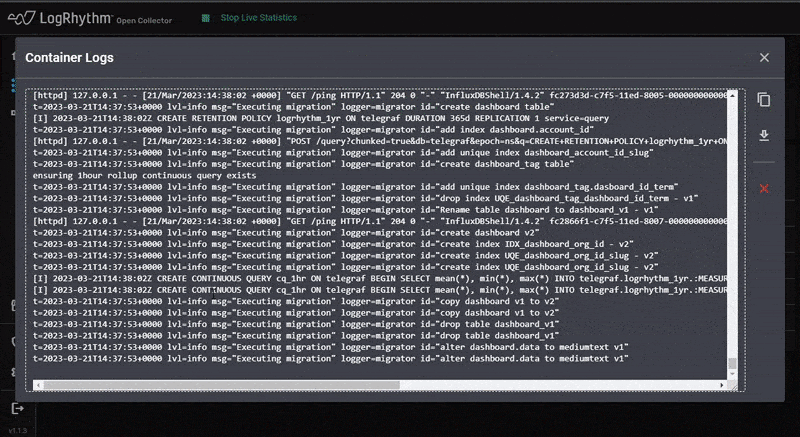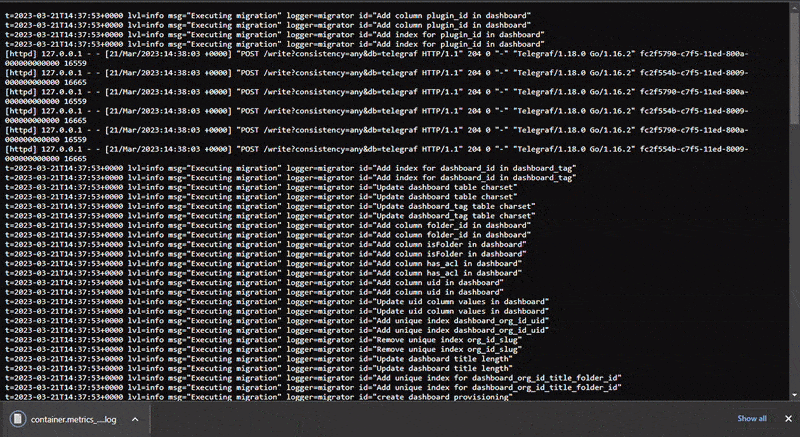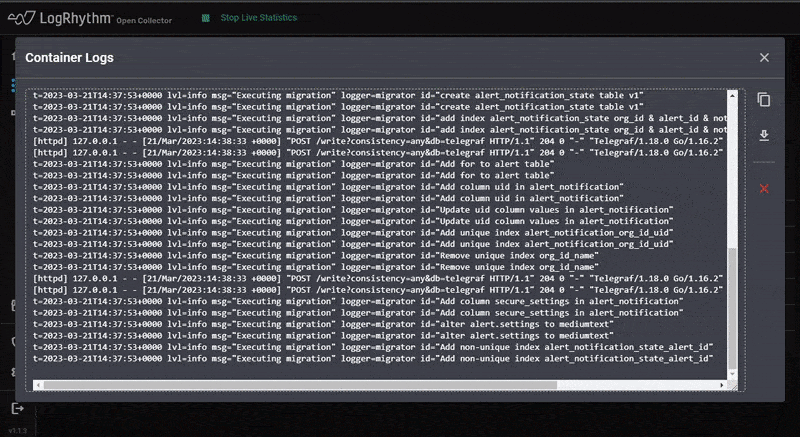
For more on OC Admin improvements, visit the blog post here.
Ongoing log source support
LogRhythm is committed to providing customers with greater value. As part of that mission, the team revisits supported log sources and updates them to enable better correlation and analysis. Our new and enhanced methods of ingestion include:
- Prisma Cloud API: Allows users to monitor everything that is occurring in the Prisma Cloud suite.
- SalesForce eCommerce Auditing: Allows users to see what client(s) created a Promocode or altered the price of an item, with what server and user
- Open Collector behind Squid Proxy: acts as an additional data security boundary to protect users from malicious activity on the internet.
- Open Collector: Oracle Version Update offers support between Oracle operating systems and Open Collector
- System Monitor (SysMon) Agent: Support for the latest version of RHEL
- System Monitor Agent: Support between Oracle operating systems and SysMon
We’ve also updated LogRhythm’s Machine Data Intelligence (MDI) Fabric capabilities to enhance multiple MPE rules and signature IDs across Cisco Secure Email, Cisco Umbrella, FireEye, Imperva, Tanium, ForcePoint, MS Windows Event Logging, MS Exchange Management, Symantec DLP, and among others.
New LogRhythm SmartResponse™
We’re continuing to add to our growing library of LogRhythm SmartResponses™, our prebuilt automated actions for third-party integrations. These actions enable you to execute preventative actions, accelerate your response, and shorten your workflow. With the LogRhythm 7.12 release, our Netskope 2.0 SmartResponse is now available. Through Netskope’s REST API, customers can add URLs, files, or SHA-256 hashes to the application blacklist in Netskope.
What’s new in LogRhythm UEBA
LogRhythm continues to enhance its advanced analytics capabilities with updates to LogRhythm UEBA, an add-on to LogRhythm SIEM. Recently, LogRhythm Labs, our dedicated team of threat intelligence experts, developed additional out-of-the-box use cases for LogRhythm UEBA to enable you to use anomaly outputs with other findings in your environment. The new uses cases include the following:
User anomaly + password modified
A user’s password is modified, and the user has a high anomaly score. This is a highly suspicious activity that is worth investigating. While a password change by itself is not suspicious enough, this is the direct added value of LogRhythm UEBA. This use case uses the following:
User anomaly + file downloaded
A user downloads numerous files and the user has a high anomaly score. This is a suspicious activity that you should investigate. Simply downloading files by itself is not suspicious enough, but LogRhythm UEBA deems it necessary for further review with the combination of the file downloads and the high anomaly score. This use case features the following:
User anomaly + file deleted first stage recycle bin
A user deletes numerous files, and the same user has a high anomaly score. This activity should immediately raise a red flag as it shows signs of highly questionable behavior. LogRhythm UEBA alerts you to this anomalous activity. This use case is as follows:
User anomaly + file deleted second stage recycle bin
An admin user deletes many files from the second stage recycle bin, and the user has a high anomaly score. As mentioned above, this activity is highly suspect and is worth investigating. When a file is deleted, it first goes into the first stage recycle bin. If a file is deleted from the first stage recycle bin, it moves into the second stage recycle bin, to which only admins have access. Merely deleting files is not necessarily cause for alarm, but LogRhythm UEBA shows you the direct value in associating these two user activities. With this information, you can minimize further damage. This use case includes the following:

Stay in the know with the latest updates on LogRhythm UEBA in Community.
Upgrading to LogRhythm 7.12 and influencing the future
LogRhythm remains committed to our customers. Our latest product enhancements come, in part, from customer feedback. To stay updated on the latest LogRhythm product news and help influence what’s coming next, visit LogRhythm’s Innovation Portal.
Take advantage of the latest features of LogRhythm SIEM version 7.12 by letting our team of experts perform the upgrade for you with our Unlimited Upgrades Service. Our Professional Services team is available to enable you to upgrade to every quarterly SIEM release with ease. Existing customers can request a license here and download LogRhythm 7.12 from Community.
For further details about our other product releases, register for our April 2023 Quarterly Launch webinar.