The zero-day “baseStriker” vulnerability is still widely in use, but do you know what to look out for if it finds its way into your organization?
While 18 months have passed since Microsoft developed a fix for the vulnerability that was designed to defeat security services in Office 365 (O365), the threat it is still used, and it can be difficult to detect or prevent.
What is “baseStriker?”
The baseStriker vulnerability, recognized as a zero-day, refers to the method hackers use to disguise a dangerous link from security scans and enable hackers to send a bad link to Office 365 customers.
Most email is HTML based to properly display weblinks (URLs), pictures, and support many other media formats. Hyperlinks, whether they are email addresses or weblinks, are then properly displayed with the recognizable blue lettering and underline, indicating a link. HTML tags are used to create or reference a weblink (or URL) using a tag (“a href”).
But not everything is as it appears. Let’s take a closer look at the baseStriker vulnerability.
Looks Can be Deceiving
What makes baseStriker unique is that it adds another level or additional method to split (for lack of a better term) the URL by using another tag called base (i.e., “base href”). Then the combined references (“base href” + “a href”) complete the full URL, both visibly and clickable.

Figure 1: baseStriker splits and disguises the URL to create a malicious link
This method of breaking up the URL into two separate entries bypasses Office365 security checks. In addition, manual analysis is deterred or made more difficult because copying the link to test through sandbox analysis, malware, and link investigation doesn’t work with only half of the URL. This is what you see when “hovering” your mouse over the link, or if the link is clicked (see below example).
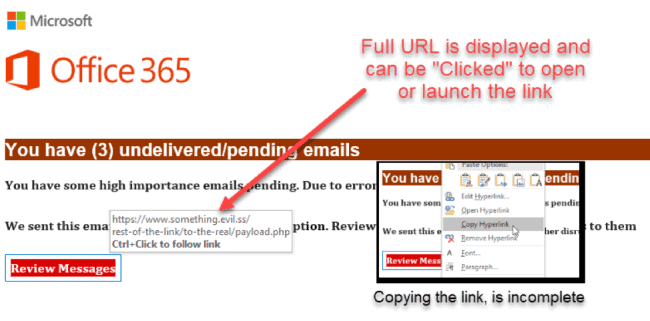
Figure 2: baseStriker creates an incomplete link to bypass Office365 security checks
With “baseStriker,” when you right-click the URL, select “Copy Hyperlink,” and paste the link into a text editor (like Notepad or other) you will only get the second half of the URL, minus the “base href” (see below example).
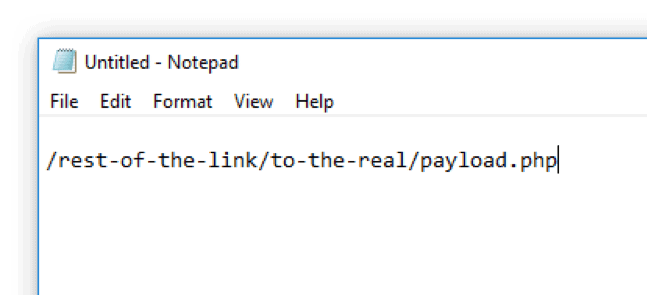
Figure 3: When the link is copied and pasted into a text editor, you will only see the second half of the URL
This is how you know the URL is a “baseStriker” and is designed to bypass or elude O365 security services. The copied hyperlink only copies the latter half or “href” details and not the whole URL. According to Microsoft, this has been patched, but that doesn’t stop hackers from using “baseStriker.”
How Can You Protect Yourself?
While Microsoft announced it has patched this vulnerability in Office 365 (O365) with its Advanced Threat Protection (ATP) under Threat Management, the patch hasn’t fixed all of the issues. This may catch or reduce the number of emails using “baseStriker” with (known) malicious content. But to this day, we still see phishing emails using the “baseStriker” method getting through to our users’ inbox.
As with any email containing hyperlinks (URLs) and attachments, use caution! We recommend going through the following mental checklist for any “red flags” on the email content:
- Were you expecting the email? This step alone can raise your suspicion on unsolicited or emails outside of your normal day-to-day email messaging. Unless of course, you receive emails from different unknown sources all the time.
- Is it from a recognized or known domain/sender (email address)? In other words, is it coming from a domain, business or other you recognize?
- Does the email contain weblinks (URL) or attachments? We receive and send emails all the time, and it is rare to include a weblink or an attachment.
- Was the email sent/received during normal business hours? This is just another “red flag” if the email was sent in strange or very late hours; like 3:00 a.m.
You can further protect yourself by using two-factor authentication for logging into your services. In the event the email is designed to steal credentials, two-factor authentication will reduce this attack vector’s effectiveness. You can also download our free posters to help educate employees in your organization on how to detect a phishing attack.
