Mamba Ransomware Background
In September of 2016, a strain of ransomware was found in the wild which performed full disk encryption. According to Kaspersky Lab researchers1, this ransomware strain named “Mamba” now appears to be re-circulating, primarily in Brazil and Saudi Arabia.
The ransomware includes a DiskCryptor tool capable of using strong encryption algorithms to make recovering the encrypted disk content next to impossible unless the victim is able to obtain a decryption key from the ransom authors.
The resurgence of this malware has prompted analysis efforts by LogRhythm Labs researchers to ensure users are prepared to protect their systems and help prevent infection of this malware variant in the future. In-depth analysis of this latest Mamba sample follows. Signatures in support of detection are included at the end of this report.
Mamba Ransomware Analysis
The Mamba dropper sample analyzed has the following respective MD5 and SHA256 hashes, and will be referred to as “b9b60.exe” for the remainder of this report:
MD5: 79ed93df3bec7cd95ce60e6ee35f46a1SHA256: b9b6045a45dd22fcaf2fc13d39eba46180d489cb4eb152c87568c2404aecac2fUpon executing the dropper, Mamba creates the folders “C:\xampp\http”. This would appear to mimic the open source XAMPP application distribution2, which is a cross-platform package containing the web server Apache, database MariaDB, and the PHP and Perl programming languages. The directory mimicked by the malware is specifically the Apache web server component directory configured by XAMPP.
Figure 1: Files Dropped in C:\xampp\http
| Filename | Description | MD5 | SHA-256 |
|---|---|---|---|
| dcapi.dll | Cryptor library | b4c9a8deb15e312aecaec27d5fbc898f | 7fc78f3e1a6963185dac4af949fb76fd79b429148f9f61d429054e94f7a8ba32 |
| dccon.exe | Console version of DiskCryptor | 1a1222101c499eb15f5c91774583d24d | 2dd5dd9aa62a9072753fdf82a2d4b386401c00f59755a755d68cb6bbb608203c |
| dcinst.exe | Cryptor installer support | 88f25e2f08c90b3bbe253d0d64ab1d3e | 9136ee4e2b73dd617d116fc28e6673931043f03e94a6ee4f0b57a29609f96749 |
| dcrypt.sys | Cryptor driver | edb72f4a46c39452d1a5414f7d26454a | 0b2f863f4119dc88a22cc97c0a136c88a0127cb026751303b045f7322a8972f6 |
| log.txt | Created by malware, logs codes indicating malware activity | 1395dbadb21547be726872e3206d0e23 | 04f0e45b35a21d060d8d2324541739bc1c550ee0e6526b2685ae0b6bdd379447 |
Table 1: Description of Dropped Files
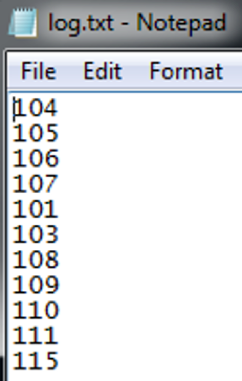
In the case of the log.txt file created by the malware, this appears to track the activity of the malware. While the code references are still being analyzed, the value “107” in the log indicates successful creation of the service used for persistence, called “DefragmentService.”
Figure 2: log.txt File Contents
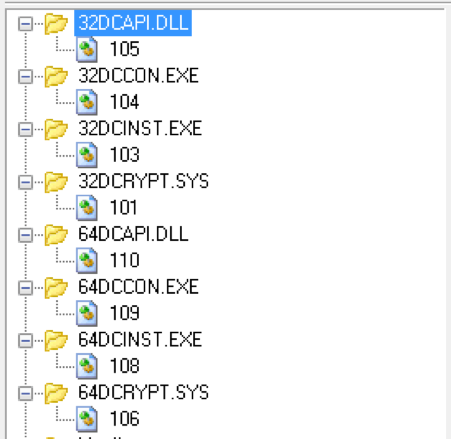
The malware contains the DiskCryptor cryptography tool3 embedded as resources in the main malware binary as shown below. According to the DiskCryptor documentation, the tool supports AES, TwoFish, and Serpent encryption algorithms. Analysis is still ongoing in order to determine the specific encryption algorithm used by Mamba.
Figure 3: 32- and 64-Bit DiskCryptor Binary Resources
Note that further analysis and correlation of the dropped files and the publicly available versions is still underway. Although the hashes of the dropped files do not directly match those of the publicly available versions, static analysis suggests that the functionality is nearly identical. Although analysis of these files is ongoing, it is likely that the malware authors simply recompiled the available DiskCryptor source code for inclusion in Mamba.
After dropping the DiskCryptor files, Mamba additionally performs the following:
- Runs “C:\xampp\http\dcinst.exe -setup”
- dcinst.exe moves the cryptographic driver to %WinDir%\System32\drivers\dcrypt.system
- Two services are created named “dcrypt” and “DefragmentService” with the following registry values:
| Name | Data |
|---|---|
| DependOnService | FltMgr4 |
| DisplayName | DiskCryptor driver |
| Group | Filter |
| ImagePath | system32\drivers\dcrypt.sys |
| ErrorControl | 0x3 (Record the current startup as a failure)5 |
| Start | 0x0 (Boot) |
| Type | 0x1 (Kernel-mode driver) |
Table 2: KLM\System\CurrentControlSet\services\dcrypt
| Name | Data |
|---|---|
| DisplayName | Defragment service |
| ImagePath | <2nd parameter>6 |
| ErrorControl | 0x0 (Ignore) |
| Start | 0x2 (Automatic) |
| Type | 0x10 (16: A Win32 program that runs in a process by itself.) |
Table 3: HKLM\System\CurrentControlSet\services\DefragmentService
| Value7 | Data | Description |
|---|---|---|
| ResetPeriod | 0x78 | Reset failure count to zero after 120 (0x78) seconds if there have been no failures |
| RebootMsg | 0x1 | Unknown value |
| Command | 0x0 | Command line of the process is unchanged |
| Actions | 0x2 | Number of elements in SC Actions array below |
| SC Action ptr | 0x14 | Pointer to SC Action array |
| SC Action 1 | 0x1 0x3E8 | Restart the service after 1000 (0x3E8) ms |
| SC Action 2 | 0x1 0x3E8 | Restart the service after 1000 (0x3E8) ms |
Table 4: HKLM\System\CurrentControlSet\services\DefragmentService\FailureActions
- If the “DefragmentService” service is successfully created, the malware forces a reboot of the infected host, ensuring persistence for the malware.
- After the reboot, the malware runs the command-line encryption tool dccon.exe to encrypt the file system.
- This task runs under the original malware process name registered as a service in the above step.
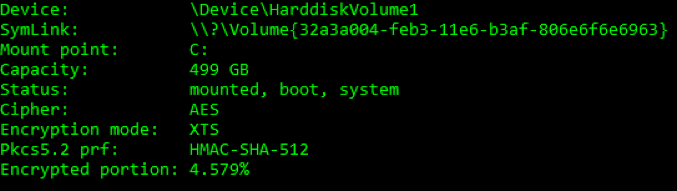
While the encryption process is running, entering the command “dccon.exe –info pt0” from a command-prompt will allow one to view the encryption progress, encryption type, and other details:
Figure 4: Sample Output of “dconn.exe -info pt0”
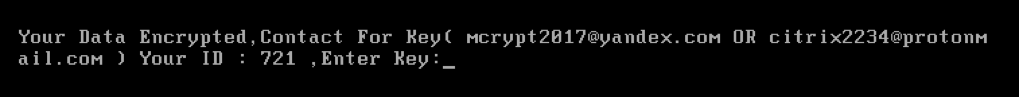
Once the encryption process completes, and after a further reboot, the victim is presented with the following ransom note, which requests that the user email one of two email addresses with an ID number, presumably to retrieve the decryption key. Note that there is no indication of what the actual ransom fee is.
Click images to expand
Figure 5: Mamba Ransom Message Following Successful Encryption
Base64 Encoded Strings for Mamba Ransomware
The analyzed Mamba sample utilizes Base64 encoding in order to obfuscate strings in the binary which reveal the malware’s functionality. Following are the decoded strings extracted from the binary. Note that some of the strings listed below are commands that were not observed to be used during execution.
| Encoded Base64 String | Decoded Base64 String |
|---|---|
| V293NjREaXNhYmxlV293NjRGc1JlZGlyZWN0aW9u | Wow64DisableWow64FsRedirection |
| S2VybmVsMzIuZGxs | Kernel32.dll |
| b3Blbg== | open |
| ICYgc2h1dGRvd24gL2YgL3IgL3QgMA== | & shutdown /f /r /t 0 |
| ICYgdGFza2tpbGwgL2ltIE1vdW50LmV4ZSAmIERlbCAiQzpcVXNl cnNcQUJDRFxNb3VudC5leGUiICYgRGVsICJDOlxVc2Vyc1xBQkNEXG5ldHBh c3MudHh0IiAgJiBEZWwgIkM6XFVzZXJzXEFCQ0RcbmV0dX NlLnR4dCIgICYgRGVsICJDOlxVc2Vyc1xBQkNEXG5ldHBhc3MuZXh lIiAmIG5ldCB1c2VyIC9kZWwgbXl0aGJ1c3RlcnM= | & taskkill /im Mount.exe & Del “C:\Users\ABCD\Mount.exe” & Del “C:\Users\ABCD\netpass.txt” & Del “C:\Users\ABCD\netuse.txt” & Del “C:\Users\ABCD\netpass.exe” & net user /del mythbusters |
| L0MgcGluZyAxLjEuMS4xIC1uIDEgLXcgMzAwMCA+IE51bCAmIHN jIGRlbGV0ZSBEZWZyYWdtZW50U2VydmljZSAmIERlbCAi | /C ping 1.1.1.1 -n 1 -w 3000 > Nul & sc delete DefragmentService & Del “-boot -setmbr hd0 |
| LWJvb3QgLXNldG1iciBoZDA= | -boot -setmbr hd0 |
| LWVuY3J5cHQgcHQ0IC1wIA== | -encrypt pt4 -p |
| LWVuY3J5cHQgcHQ1IC1wIA== | -encrypt pt5 -p |
| LWVuY3J5cHQgcHQ2IC1wIA== | -encrypt pt6 -p |
| LWVuY3J5cHQgcHQ3IC1wIA== | -encrypt pt7 -p |
| LWVuY3J5cHQgcHQ4IC1wIA== | -encrypt pt8 -p |
| LWVuY3J5cHQgcHQ5IC1wIA== | -encrypt pt9 -p |
| LWVuY3J5cHQgcHQwIC1wIA== | -encrypt pt0 -p |
| LWVuY3J5cHQgcHQyIC1wIA== | -encrypt pt1 -p |
| LWVuY3J5cHQgcHQyIC1wIA== | -encrypt pt2 -p |
| LWVuY3J5cHQgcHQzIC1wIA== | -encrypt pt3 -p |
| LXNldHVw | -setup32dcapi.dll |
| MzJkY2FwaS5kbGw= | 32dcapi.dll |
| MzJkY2luc3QuZXhl | 32dcinst.exe |
| MzJkY2Nvbi5leGU= | 32dccon.exe |
| MzJkY3J5cHQuc3lz | 32dcrypt.sys |
| NjRkY2FwaS5kbGw= | 64dcapi.dll |
| NjRkY2luc3QuZXhl | 64dcinst.exe |
| NjRkY2Nvbi5leGU= | 64dccon.exe |
| NjRkY3J5cHQuc3lz | 64dcrypt.sys |
| QzpcVXNlcnNcQUJDRFxuZXRwYXNzLnR4dA== | C:\Users\ABCD\netpass.txt |
| RGVmcmFnbWVudFNlcnZpY2U= | DefragmentService |
| XGRjaW5zdC5leGU= | \dcinst.exe |
| XGRjY29uLmV4ZQ== | \dccon.exe |
| Y21k | cmd |
| ZGNhcGkuZGxs | dcapi.dll |
| ZGNjb24uZXhl | dccon.exe |
| ZGNpbnN0LmV4ZQ== | dcinst.exe |
| ZGNyeXB0LnN5cw== | dcrypt.sys |
Table 5: Base64 Encoded Strings
Mamba Ransomware Network Artifacts
This variant of Mamba does not exhibit any notable network functionality. Unlike the recent ransomware outbreaks of WannaCry and NotPetya, this variant of Mamba does not contain any inherent exploitation or spreading functionality. The malware is executed solely on the infected host and will not self-replicate.
LogRhythm Signatures for Mamba Ransomware
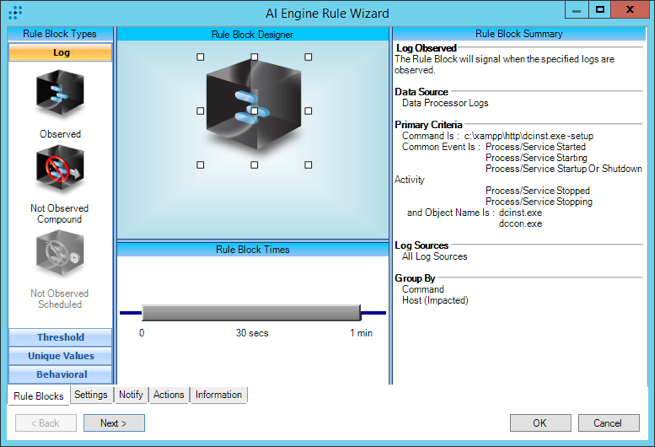
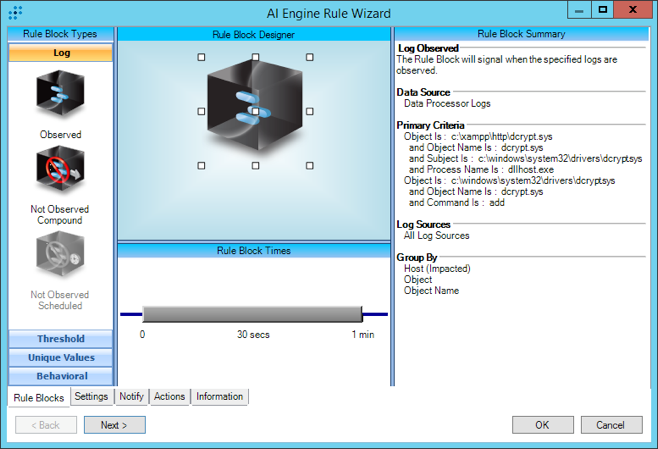
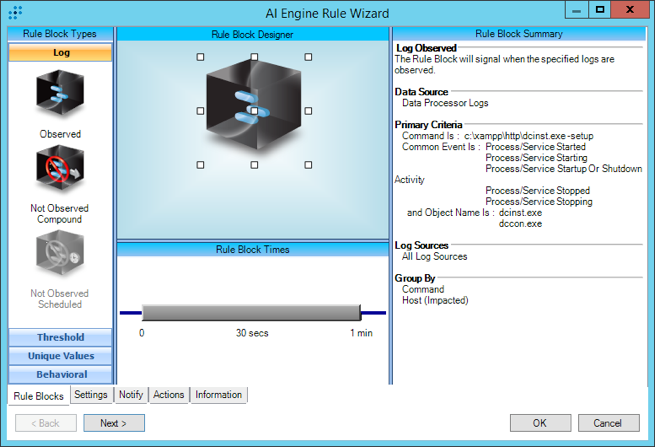
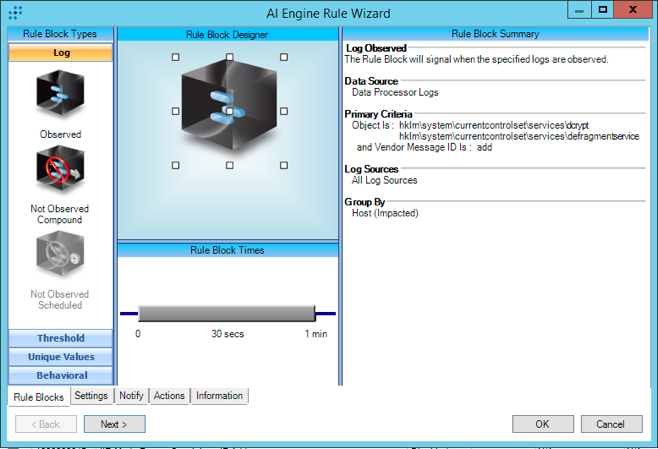
We created four LogRhythm AI Engine rules to detect some of the main indicators that we observed in our internal lab environment.
Figure 6: Labs Mod – Mamba – Command – DiskCryptor Installation
Figure 7: Labs Mod – Mamba – DiskCryptor Driver Creation
Figure 8: Labs Mod – Mamba – DiskCryptor File Creation
Figure 9: Labs Mod – Mamba – Registry Key Creation
Instructions for Importing AI Engine Rules
LogRhythm Labs has created Mamba AI Engine Rules to help you detect Mamba. Please find the download above.
Now onto the instructions:
Open the LogRhythm Console.
Navigate to the AI Engine Tab via Deployment Manager > AI Engine Tab.
Figure 10: AI Engine Tab
Select the pull-down menu “Actions,” and then select “Import.”
Figure 11: Pull-Down Menu > Actions > Import
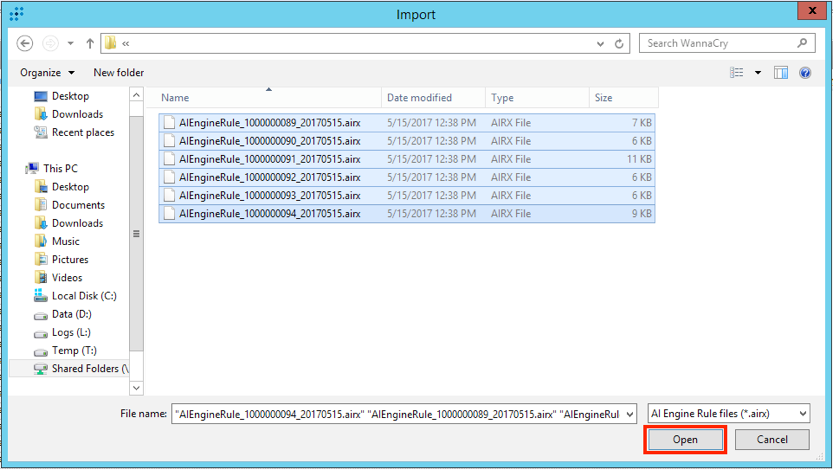
Select the .airx (AI Rules File Format) files you wish to import, and select “Open.”
Figure 12: Import .airx Files
Upon a successful import, you will be presented with the following pop-up window:
Figure 13: Confirmation
It is possible that an error will appear stating that the KB version is out of date with the AI Engine Rules selected for import. If this occurs, upgrade your KB to the latest version, and perform this procedure again.
Reference List
1 Kaspersky Labs, “The return of Mamba ransomware,” https://securelist.com/the-return-of-mamba-ransomware/79403/
2 XAMPP Apache Distribution, https://www.apachefriends.org/index.html
3 DiskCryptor Open Source Partition Encryption Solution, https://diskcryptor.net/wiki/Downloads
4 Note that the DependOnService makes use of the Filter Manager by installing a mini filter driver which can be viewed when running the command “fltmc instances.”
5 An ErrorControl value 0x3 as seen in dynamic analysis is unusual and requires further analysis to determine whether this is intentional behavior of the malware or a side effect of execution.
6 The first parameter is a password for the encryption and can be any value; the original value is unknown. The second parameter is required, and (reportedly) expected to be “/accepteula” (due to the typical execution via the Sysinternals tool psexec), but the malware will execute as long as any 2 arguments are passed in.
7 This value is binary data in the format of a SERVICE_FAILURE_ACTIONS structure as documented in https://msdn.microsoft.com/en-ca/library/windows/desktop/ms685939(v=vs.85).aspx.