The mass migration to remote working in recent times has caused an increased focus on the security of remote collaboration tools. LogRhythm has found a variety of these tools in our customer base and has built collection methods and analytics to help security teams obtain more visibility into the use or abuse of these tools.
This blog post will guide you through how to use the LogRhythm NextGen SIEM to monitor Zoom meeting activity, so your team can quickly detect and take action on telecommunication tool exploits.
Zoom Security and Privacy Risks
Zoom is a popular teleconferencing app that is helping educators, organizations, and families connect from anywhere in the world. So, why do telecommunication tools like Zoom present security risks? With so much of the world staying at home and finding new ways to telecommute with others, collaboration tools are being used for everything from highly confidential government discussions to virtual children’s birthday parties. Both scenarios are targets for bad actors looking to exploit vulnerabilities. Zoombombing, where unauthorized users enter and disrupt a Zoom meeting, is one of the most widely seen security issues with the platform. At one end of the spectrum, a threat actor could gain access to state-level discussions to compromise high ranking government officials and their departments and at the other end, crash a children’s birthday party, whether accidental to outright criminal.
The best place to start protecting your organization from exploits is to collect log data from telecommunication tools. Log data can provide useful data in relation to the volume of usage, administrator activity, who is joining meetings, as well as the meetings being created, updated, and deleted. There may be other useful insights, but these provide a good starting point. Getting this data in real-time enables your team to quickly act should a bad actor seek to infiltrate a meeting. Real-time data can also help your team take action to prevent future abuse.
Because LogRhythm has seen an increase in the use of Zoom both by our customer base and elsewhere, we’ve put together this quick-start guide on how to get Zoom logs into the LogRhythm SIEM. We’ll follow up with guides for other popular collaboration tools over the coming days.
Automate Tasks With Zoom REST API
Zoom provides a REST-based API to provide access to resources in its platform. The API provides access to some of the most popular features like: create a meeting, add a new user, run a report, or edit settings. While the reporting is useful to provide an overview of the meetings created in the last 24 hours, or who participated in a meeting, LogRhythm wanted something more real-time for monitoring and alerting.
What the REST API does provide is a basis for a SmartResponse™ Automation. With an automated response workflow, you could create a meeting, remove a registrant from a meeting, or update a user in response to something detected in the LogRhythm SIEM via the REST API.
Using Zoom Webhooks to Monitor Activity
Webhooks are used by an application to provide other applications with information as it happens. A client application provides an endpoint URL for the server application to call when an event takes place, allowing that event to be reported to the client application. They are sometimes referred to as reverse APIs. Zoom provides webhooks to notify third-party applications about events that occur in a Zoom account. Instead of repeatedly polling the Zoom REST API, you can use webhooks to send notifications about events that happen in a Zoom account in near real-time.
This is exactly what the SIEM needs to help your team monitor Zoom activity. Webhooks send events as they happen, so you can consume those events in LogRhythm SIEM close to real time. You can use those events to create dashboards, analytics, and search like any other log source.
If you are not familiar with webhooks, you can find an example at the end of this article with the other resources for a quick refresher.
Send Zoom Webhook Notifications to the LogRhythm SIEM
So, how do you deliver a Webhook notification into the LogRhythm SIEM?
Configuring a Webhook on any software-as-a-service (SaaS) product, like Zoom, generally requires the provided endpoint URL to be at a publicly resolvable address and use HTTPS. However, creating new public-facing services is not a quick and easy task. Apart from the security aspects, resources must be sourced and configured, and you must consider the ongoing maintenance and support.
This is a situation where serverless computing can excel. We built a Webhook client application for Zoom using AWS Lambda, and the AWS API Gateway. If you are not familiar with AWS Lambda, review the tutorial material provided at the end of the article to get started.
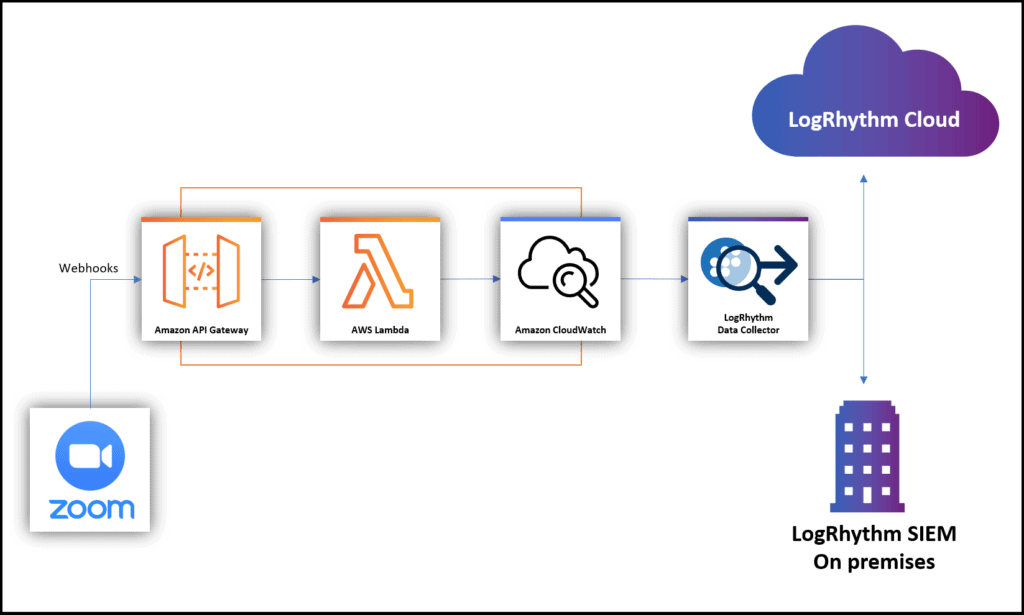
The solution uses event notifications from Zoom using a Webhook that delivers the events through AWS API Gateway to AWS Lambda. Lambda runs a function that carries out pre-processing and writes the log data to AWS Cloudwatch. The LogRhythm Data Collector pulls the logs from AWS Cloudwatch and delivers them to the LogRhythm platform — either LogRhythm Cloud or the LogRhythm NextGen SIEM (on prem).
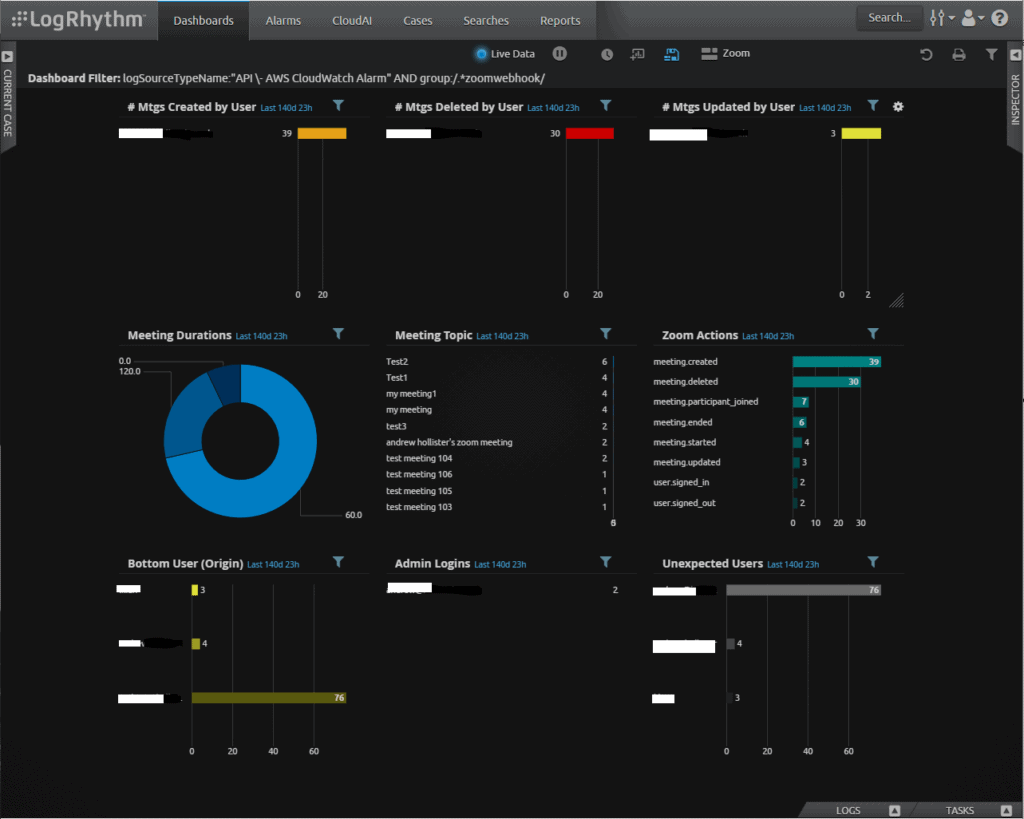
Here is an example LogRhythm dashboard showing an overview of all activities for the Zoom account:
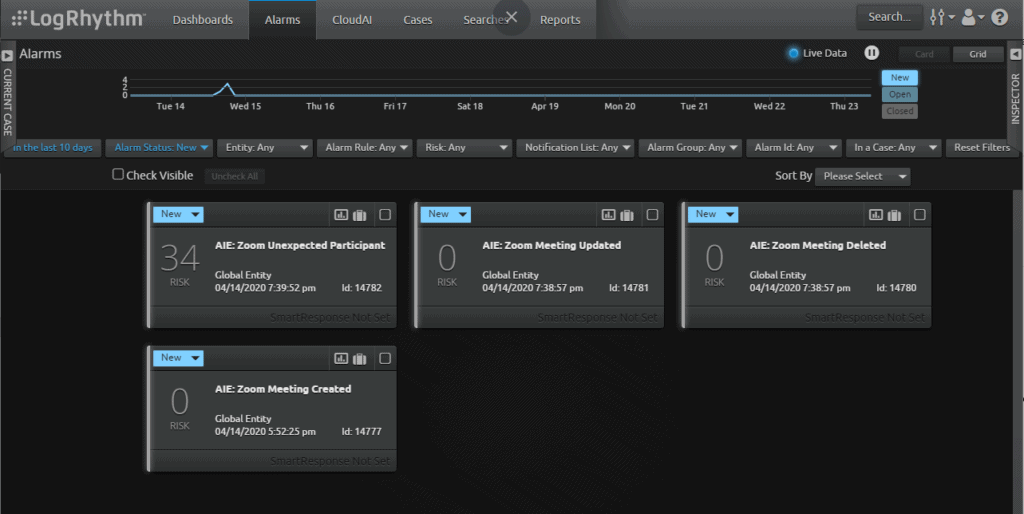
Here are some example alarms for meetings being created, updated, and deleted. Plus, an unexpected participant joining a meeting:
Missing Zoom Events
Some events that you might expect to see are missing from this list, specifically failed user logins. Unfortunately, Zoom does not provide audit information about failed login attempts or unauthorized access attempts to the administration user interface. It would also be helpful to include IP address information in the event stream to provide a geolocation on where users are joining meetings from. Hopefully, this functionality will be added in the future, but in the meantime, all the available events can be found in the Zoom references listed at the end of this article.
Protect Your Users from “Zoombombing”
Even when your team does everything it can to detect and quickly act on video-conferencing security issues, it is important to communicate to your organization’s users ways they can help stay safe. Make sure employees know to password protect their meetings, meeting host should disable screen sharing, remote control, file sharing, and make sure the meeting room feature is enabled so they can screen attendees before allowing them to join the meeting. And of course, advise users not to share their meetings links and passwords publicly.
Visibility from the LogRhythm NextGen SIEM Platform
With large parts of the workforce now being frequent users of SaaS based collaboration services, visibility into those platforms is increasingly important to security teams. The solution is this article helps surface a variety of activities that could engender risk to your organization, from sensitive information being exposed in meeting subject lines, to external attendees joining a meeting that was meant to be internal or confidential. In addition, LogRhythm provides for monitoring adherence to organizational policy for use of a collaboration platform.
While this article outlines LogRhythm’s support for collection and analysis of log data from Zoom, we support many other SaaS services, and we are continually adding support for new platforms and services. See our website for more detail, or contact us here to discuss how we can help you monitor your remote workforce.
Additional Resources:
Zoom REST API: https://marketplace.zoom.us/docs/api-reference/introduction
Zoom Webhooks: https://marketplace.zoom.us/docs/api-reference/webhook-reference
Webhook refresher: https://codeburst.io/what-are-webhooks-b04ec2bf9ca2
Lambda Proxy Tutorial: https://docs.aws.amazon.com/apigateway/latest/developerguide/api-gateway-create-api-as-simple-proxy-for-lambda.html
Zoom Marketplace: https://marketplace.zoom.us/
AWS pricing: https://aws.amazon.com/lambda/pricing/
Detailed LogRhythm configuration guide: https://community.logrhythm.com/t5/SIEM-Best-Practice-Articles/Monitor-Zoom-Security-and-Privacy-Risks-Using-the-LogRhythm/ta-p/397943

