As part of the Subscription Services team, LogRhythm consultants work with customers to help bolster their defenses against cyberthreats and to improve the effectiveness of their security operations.
While working on certain use cases this quarter, we surfaced that Living Off the Land Binaries (LOLBins), such as Certutil and Windows Management Instrumentation Command-line (WMIC), can be used for a range of command execution attacks, including copying, downloading, and uploading. With careful monitoring of system behavior and abnormal process behavior (among other detection methods), you can find indicators LOLBin‘s usage.
In this blog, we will dive deeper into a recap from this quarter on several security use cases that may apply to your environment as well.
1. Detecting and Mitigating Living Off the Land Techniques
Living Off the Land Binaries are tools and applications native to the operating system that attackers can exploit to perform malicious activities. These utilities are legitimate components of the operating system (OS), designed to perform administrative, maintenance, or operational tasks. Because LOLBins are inherently trusted and often allowed by security software, attackers leverage them to bypass security measures, execute code, maintain persistence, and move laterally within a network without deploying external malicious software. This technique allows attackers to “live off the land,” minimizing their footprint and attempting to reduce the possibility of detection by the security team.
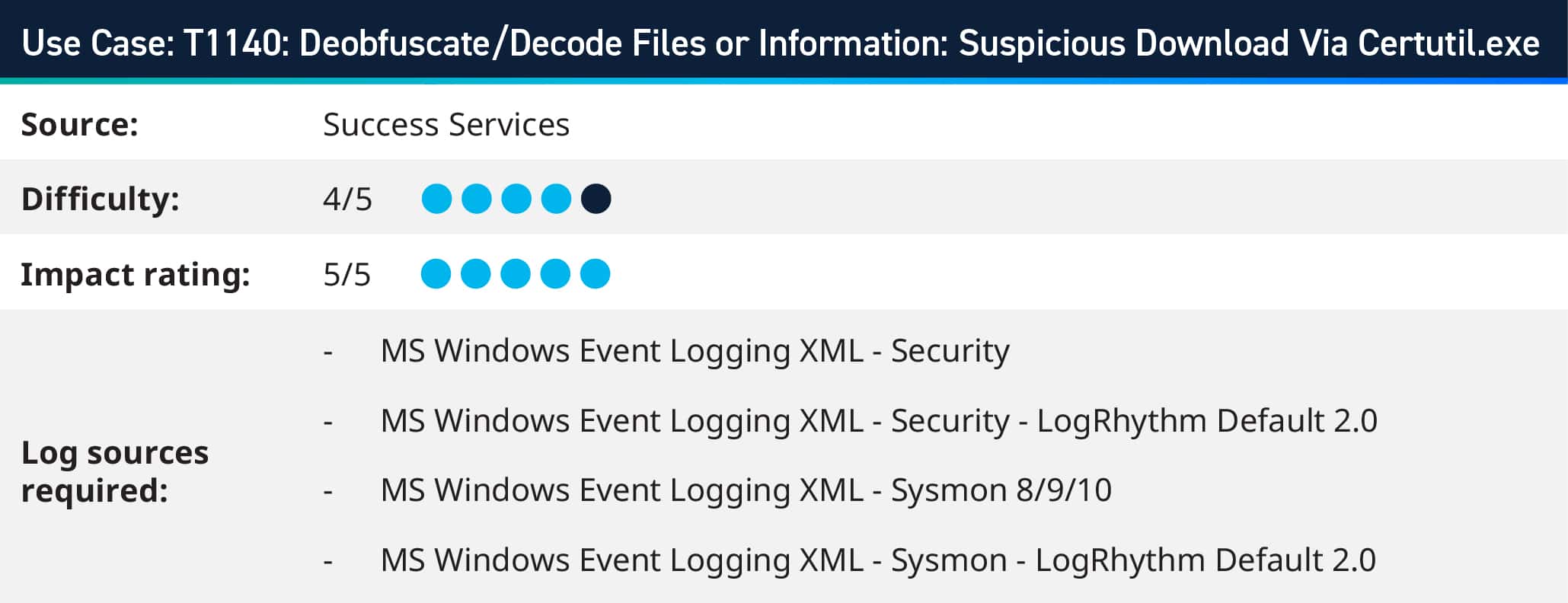
Certutil.exe is an excellent example of a LOLBin. It is a command-line utility that comes with Microsoft Windows and is intended for managing certificates on Windows systems. However, its functionalities, such as downloading, installing, and managing certificates, make it an attractive tool for attackers/red teams. They can misuse Certutil to download malware from a remote server, decode malicious files encoded to evade detection and execute malware while appearing as legitimate system activity.
With LogRhythm, you can effectively monitor command-line activity on endpoints, particularly commands related to Certutil.exe. Leveraging LogRhythm’s capabilities, such as Sysmon integration and Windows Event Log monitoring, provides comprehensive visibility into command-line executions.
2. Defending Against Brute Force Attacks
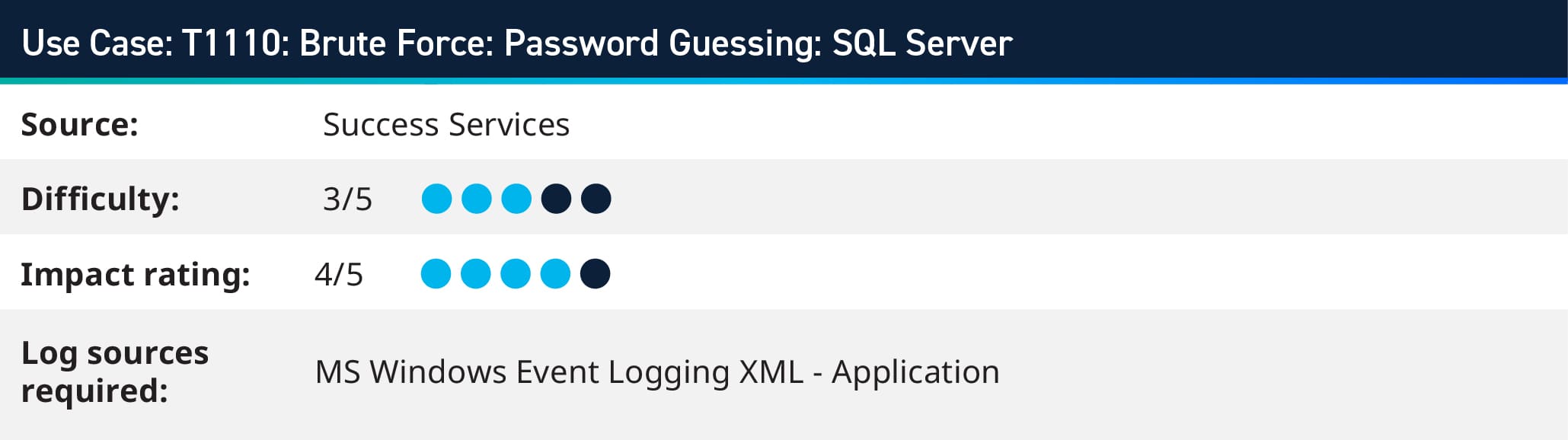
In December 2022, an intrusion was observed on a public-facing MSSQL Server, leading to a network-wide deployment of BlueSky ransomware. The initial access was achieved through brute force attacks targeting the MS SQL “sa” (System Administrator) account. Once inside, the attackers used the “xp_cmdshell” to execute commands, leading to a connection with a Cobalt Strike server and the execution of PowerShell scripts for further activities, including disabling antivirus solutions and deploying a miner payload. The BlueSky ransomware was deployed within approximately thirty minutes of initial access, illustrating a rapid progression from initial breach to widespread impact.
LogRhythm’s log monitoring capabilities enable comprehensive visibility into SQL Server activities, including login attempts and authentication failures. By aggregating and analyzing SQL Server logs, LogRhythm provides real-time insights into potential brute force attacks. Customers can learn more about this use case on the Community here.
3. Detecting Inhibit System Recovery Techniques
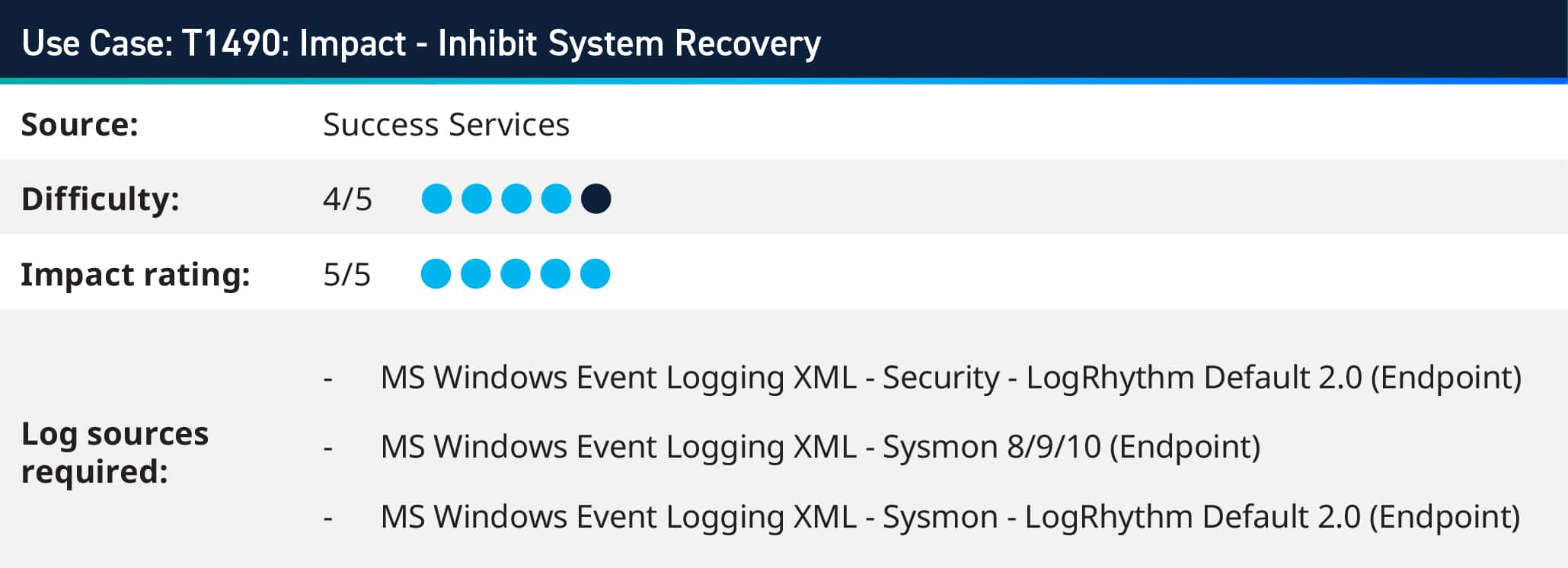
Ransomware threat actors use Inhibit System Recovery technique to force the victim into paying the ransom by deleting or removing built-in operating system recovery data and turning off recovery features used to fix a corrupted system. Consequently, malicious actors behind ransomware threats have adopted new strategies aimed at erasing recovery systems. This approach is intended to oblige organizations by eliminating their means of recovery.
Inhibit System Recovery involves eliminating built-in data and deactivating recovery functionalities that are intended to assist in the restoration of a compromised system, thereby hindering the recovery process. This action can result in the denial of access to existing backups and recovery alternatives.
Examples on Windows utilities are used by adversaries to disable or delete system recovery features:
- exe can be used to delete all volume shadow copies on a system
- WMI can be used to delete volume shadow copies
- exe can be used to delete the Windows Backup Catalog
- exe can be used to disable automatic Windows recovery features by modifying boot configuration data
LogRhythm’s File Integrity Monitoring (FIM) functionality enables continuous monitoring of critical system files and directories involved in the boot process, such as bootloader executables, boot configuration files (e.g., BCD), and recovery environment files. Any unauthorized modifications or deletions to these files trigger alerts, allowing for prompt detection and response to potential tampering.
4. Stopping Lateral Movement via CrackMapExec
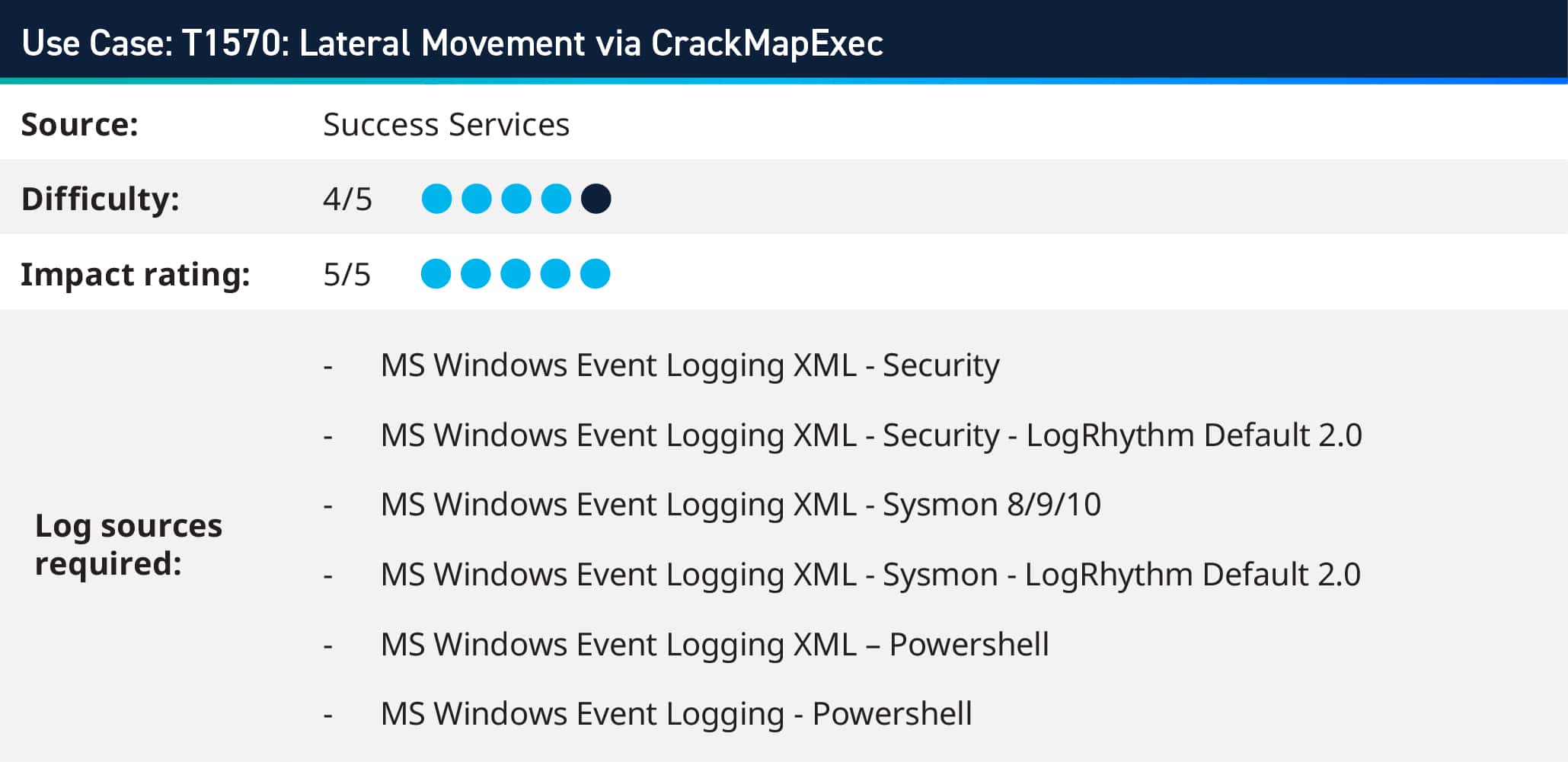
CrackMapExec is a tool used after exploiting a system, streamlining the evaluation of extensive Active Directory networks. Its functionalities encompass executing commands, enumerating shares, and employing lateral movement methods like pass-the-hash and pass-the-ticket.
Using LogRhythm, a user can review logs from Windows event logs, including Security, System, and PowerShell logs, for indicators of CrackMapExec activity. Look for events related to SMB connections, authentication failures, or unusual PowerShell script execution. LogRhythm’s log analysis capabilities enable the correlation of disparate log sources to identify sequences of events indicative of CrackMapExec usage, such as reconnaissance activities followed by lateral movement attempts.
Where to Find Out More?
These use cases and others are available to customers to download immediately within our Subscription Services Group Hub on the LogRhythm Community portal. To glimpse over other use cases LogRhythm consultants have worked on, visit the following blogs below:
To learn more about our Success Services and how we can improve your threat detection and response, learn more here. If you are a customer and you have questions, reach out to your customer success manager or account team to get more information about how we can help with your use cases and analytics!