In part 1 of our two-part series on securing water critical infrastructures (CI), we described how a water treatment plant’s operational technology (OT) security team quickly detected, located, and shut down contaminated water pipes during a potential chemical attack on the plant’s water.
In part 2, we describe how the security team can easily create correlated rules to alert to an attack at one of the plant’s remote locations.
Remote Terminal Units and Programmable Logical Controls
A water treatment plant has multiple field locations in addition to a central station. By using a supervisory control and data acquisition (SCADA) system, the plant’s security team monitors and controls processes at any of its remote locations from the master station.
Devices interfaced with equipment in the field to give the security team visibility and control over operational processes for any location are called a remote terminal unit (RTU) or programmable logical controller (PLC).
RTUs and PLCs can control some of the equipment’s physical processes, send data on the status of physical processes back to the treatment plant’s master server, and alarm the security team of any operational or security issues.
Below is an example of what a typical SCADA system looks like and how RTUs and PLCs fit in.
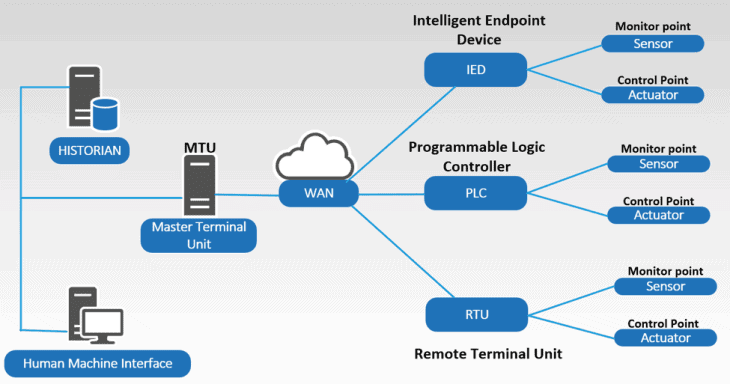
Figure 1: A typical SCADA system layout
Vulnerability of Remote Terminal Units and Programmable Logical Controllers
The connection of an RTU and PLC to a network make the water treatment plant’s remote locations vulnerable targets for a cyberattack. If an attacker gained access to an RTU or PLC, they could reprogram the unit and change the data going back to the master server or disguise any abnormal changes in the water or system. An attacker could also alter the process operations controlled by remote controllers without alerting the security team.
Any of these scenarios could have dangerous implications on the treatment plant’s water. In addition to creating alarms that help the team protect access and control of the SCADA systems, automated analysis and correlation of activity in the network can help detect threats at remote locations.
Using LogRhythm AI Engine to Trigger Alarms
Correlating a security event with a physical process change is critical to detecting an attack. A security event in the industrial control network could be reconnaissance, network behavior changes, changes in operator or engineering user behavior, detected or failed malwares, web-based attacks targeting human machine interfaces (HMI), or a man-in-the-middle attack, etc.
In this scenario, the team received an alert of an RTU intrusion followed by an abnormal increase in the plant’s chlorine levels. Together, the security event and change in chlorine levels are possible signs of an attack at one of the treatment plant’s remote locations.
To correlate these two events, the team uses LogRhythm’s AI Engine that’s integrated with the LogRhythm NextGen SIEM Platform. AI Engine delivers real-time visibility to risks and operational issues that can help the plant’s team correlate activities at all the plant’s locations.
Below the team uses the drag-and-drop rule wizard to create a correlation rule that will trigger an alarm if the above scenario were to occur.
1. Create a rule block that looks at RTU intrusion detection:
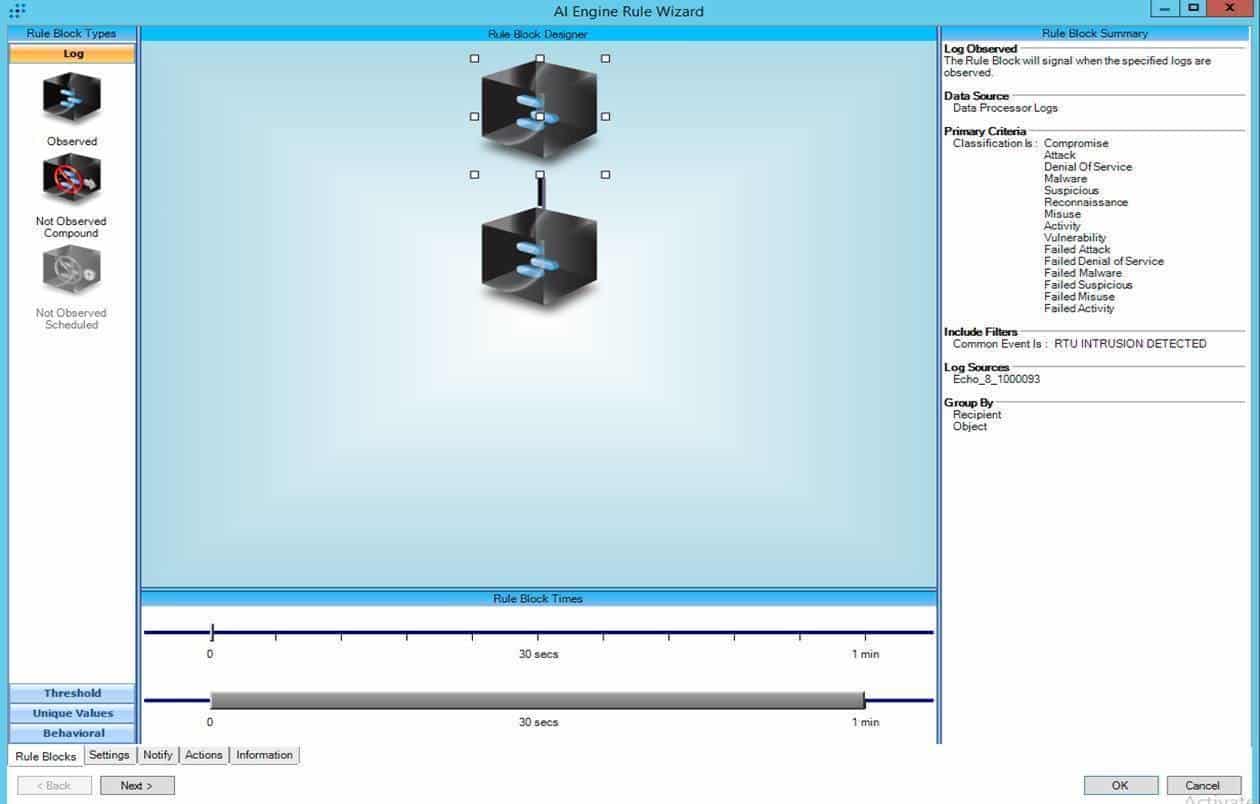
Figure 2: A rule block looks at RTU intrusions
2. Create a rule block that looks at chlorine indication level changes:
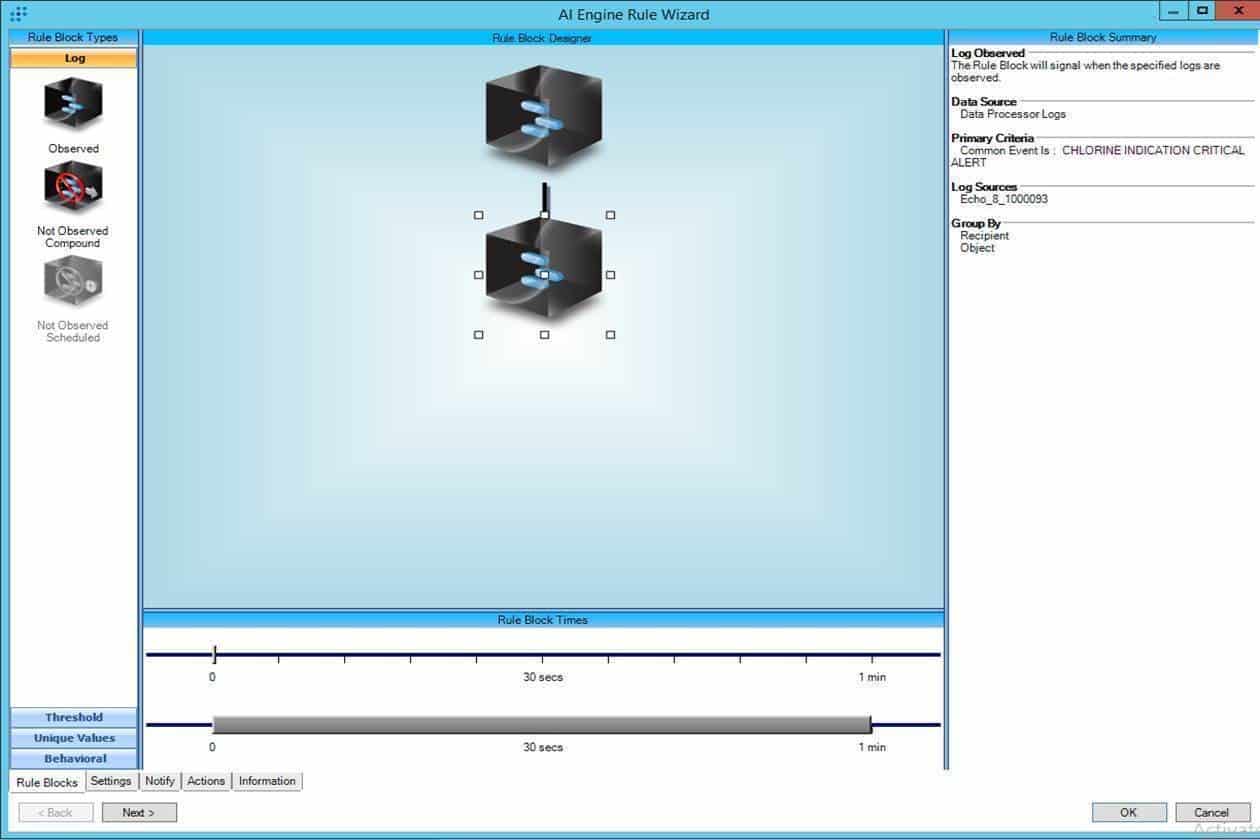 Figure 3: A rule block looks at chlorine indication level changes
Figure 3: A rule block looks at chlorine indication level changes
3. When both conditions are met, an alarm triggers:
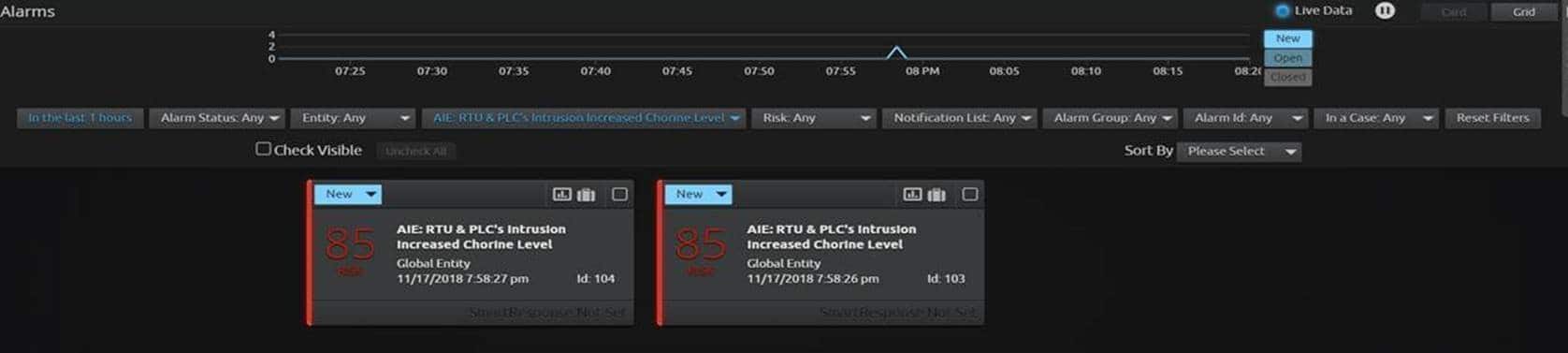
Figure 4: An alarm triggers to notify the team of a potential attack
4. Alarm drill-down
The team drills down to investigate the alarm further and can quickly find the exact location of the affected RTU and the root cause of the issue.
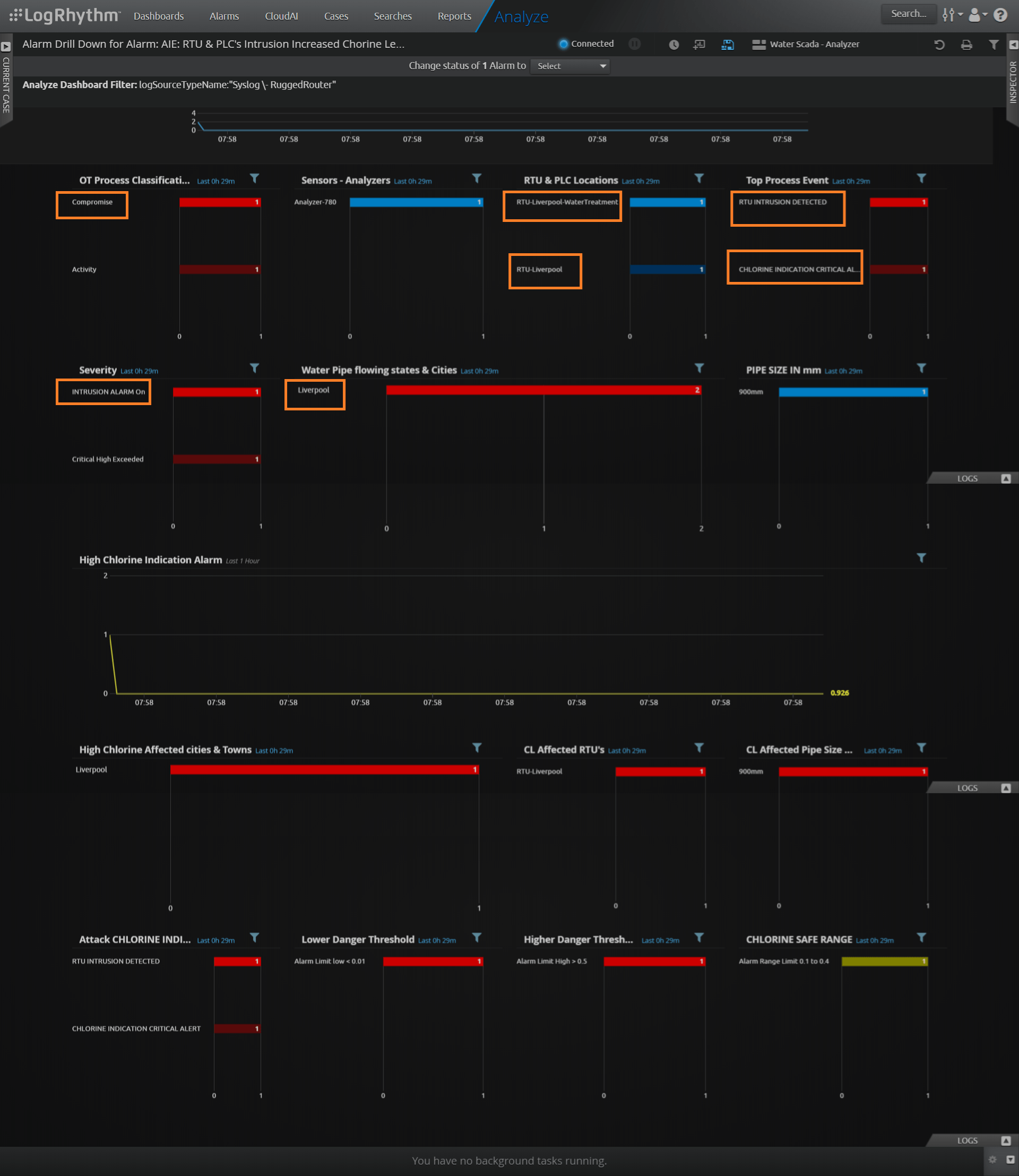
Figure 5: Alarm drill-down identifies the location and cause of the RTU intrusion
With the AI Engine rule, OT security operation center (SOC) teams can develop an advanced correlation without any programming or scripting language, detect cyberthreats at any location, and protect water CI.
Learn more about how LogRhythm can help you secure critical infrastructure here.