Insider threats pose significant risks to your organization. Their actions are difficult to detect and many incidents take months or longer to discover. The key to defending against this class of threats is to understand the who, the why, and the when. Let’s look at those critical elements and what you can do to protect yourself.
The Who: Potential Threat Actors Within Your Organization
Insider threats can be anyone who has access to a business system, including internal permanent staff, contractors, temporary staff, partners, and former staff. This means that everyone, including managers and executives, should be equally scrutinized.
Complicating matters, these individuals can intentionally or unknowingly assist threat actors in conducting activities against your organization. The Australian Government highlights two categories of employees who pose a threat in its insider threat security handbook.
- The unintentional insider: a person “who inadvertently expose, or make vulnerable to loss or exploitation, privileged information, techniques, technology, assets or premises.”
- The malicious insider: someone “who deliberately and willfully breach their duty to maintain the security of privileged information, techniques, technology, assets or premises.”
The vast number of suspects, as well as the fact that attacks can be intentionally or unintentionally committed, are among the reasons why insider threats are so difficult to detect. The good news is that you can add layers of intelligence to help you narrow your area of focus.
The Why: Motivations for an Insider Threat Actor
Each attacker will have his or her own motivations for deviance. Ultimately, there are many driving forces behind attacks.
Financial Gain
Financial gain has proven to be a leading factor behind many insider breaches. The financial gain can be small (such as a janitor selling a laptop on eBay to make a quick buck) or large (such as a lower-level staff selling personally identifiable information (PII) on the dark web).
Business Gain
Typically, sensitive intellectual property (IP) is the target for those motivated by business gain. IP can be used to boost product offerings, eliminate a competitive advantage, or assist a bad actor in a business deal. Not only can an insider threat help a competitive organization, but it can also leave the targeted business with significant expenses, lost productivity, and a damaged reputation.
Revenge
A person can become disgruntled and seek revenge for many reasons. Such reasons include job dissatisfaction, perceived inequity, disagreements with co-workers, or a potential layoff.
Ideology
Political, religious, and social beliefs can also be strong motivations for insider threats.
The When: An Insider Attack Can Happen at Any Time
A malicious insider will understand the vulnerabilities of an organization, as well as how and when they can be exploited. An insider threat can easily blend in to a normal working environment, until just the right moment, especially if the malicious insider opts for the stealthy low-and-slow approach. Some cases of espionage have flown under the radar for months and even years.
How to Protect Yourself from Insider Threats
Fortunately, many of the activities performed by a malicious insider can be detected and stopped by using a layered security approach. This layered approach should include the usual security defenses, such as network forensics, security information and event management (SIEM), IDS, and endpoint detection. However, it should also include security awareness training, policy enforcement, and auditing. Often companies that are breached by an insider threat have overlooked these security programs.
When facing insider threats, there are some points to consider when you are looking to heighten your security operations.
- Data Management: Encrypt sensitive data stored on the internal network. Also, monitor exfiltration of sensitive data to an external USB drive.
- Privileged User Monitoring: Monitor and tightly control privileged user access. Only those that absolutely need to view sensitive information and systems should be granted access. Fully eradicate shared account usage in your organization.
- Physical Access Controls: Lock down physical areas containing sensitive and valuable equipment and should only be accessible by approved staff.
- Active Change Control Policy: While a change control policy won’t prevent insider attacks, it adds a level of accountability and ensures an audit trail is available should an investigation be warranted.
- System Logging: Logging systems such as door access control systems, sensitive financial systems, high-value databases, mail servers, and directory service systems is imperative.
- Employee Security Awareness: Enforcing regular security awareness training will help empower your staff to work with you to detecting and reporting unusual or suspicious behavior. Employees are the first line of defense for an organization and can work to significantly reduce security risks.
Beyond these tips, user and entity behavior analytics (UEBA) can go a long way to help you detect and respond to insider threats. Effective UEBA solutions perform profiling and advanced anomaly detection through diverse and complementary analytical methods, including scenario- and behavior-based techniques. By employing multiple methods, you can analytics in depth to protect your organization from malicious, compromised, and accidental user-based threats.
LogRhythm UEBA delivers both scenario- and behavior-based analytics as an integrated component of the LogRhythm SIEM platform or as a standalone product. In this example, I’ll explore how LogRhythm’s scenario-based threat detection capabilities work to detect insider threat activity, as well as track a threat progressing through the Cyber Attack Lifecycle.
Click on images to view larger
Figure 1: Cyber Attack Lifecycle
How LogRhythm Can Help Detect and Respond to Insider Threats
In this use case, I created a privileged user with the username eanderson and added it as a trusted system administrator.
Figure 2: Populated Privileged User List
I then logged onto a server with the new account, modified account passwords, and conducted some other nefarious activities. Let’s walk through the use case as a security analyst.
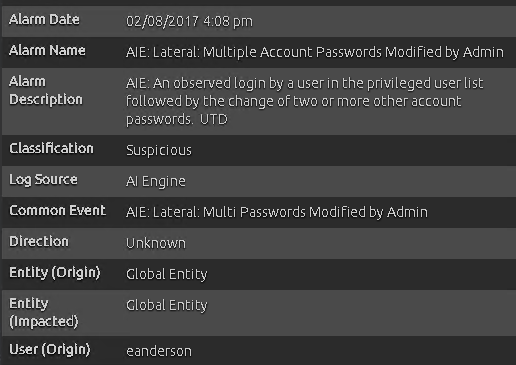
In the alarm viewer, you can see that AI Engine has detected the nefarious activity, initiating a high-priority progression alarm.
A quick look into the alarm details reveal the privileged user in question, eanderson.
Figure 3: AI Engine Progression Alarm Details
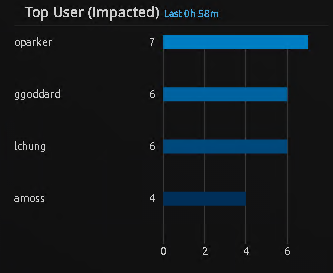
A further drill down into the alarm displays the affected impacted users whose passwords were modified.
Figure 4: Drill Down Revealing Impacted Users
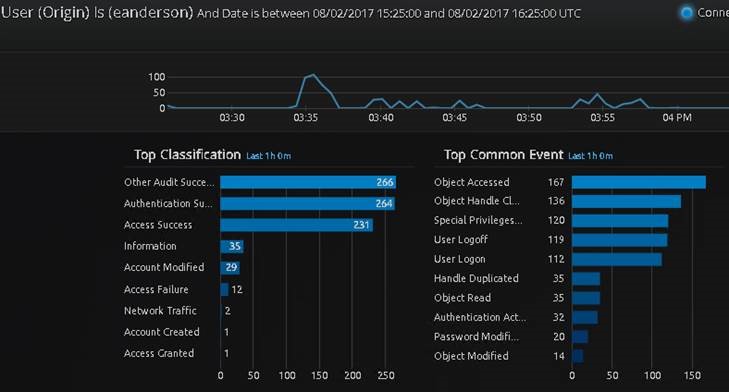
Now that you understand which users were impacted, you can use the pivot feature to go backwards in time and see what other activity this user was up to. The pivot revealed further classification and common events, as well as other metadata that can be further investigated.
Figure 5: Pivot to Reveal Relevant Alarm Metadata and Common Events
At this point, you should open a case then add all relevant artifacts and notes for investigation. Back at the alarms tab, you are prompted with two additional alerts.
Figure 6: SOC Analyst Dashboard
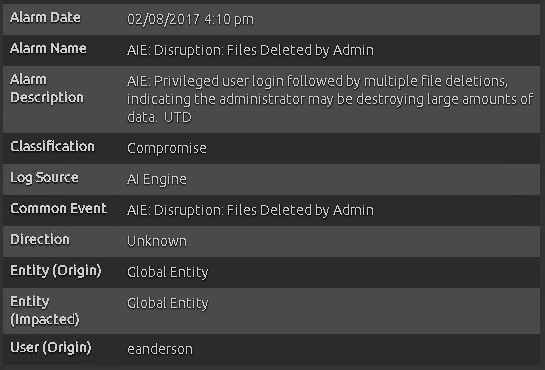
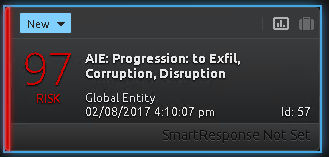
You continue the investigation by selecting the next alarm in the timeline with a 97-risk rating, which indicates that an admin deleted a number of files.
Figure 7: AI Engine Alarm
Alarm details revealed that the same user origin that modified the passwords also deleted sensitive files.
Figure 8: AI Engine Alarm Details Indicating User in Question
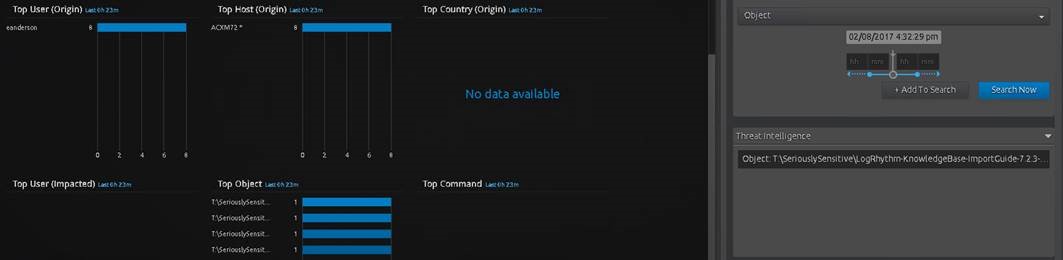
Fortunately, real-time File Integrity Monitoring provide you with extra visibility into common file system activities, so you can quickly establish which specific file system objects were deleted.
Figure 9: Drill Down Revealing Affected Files
To confirm your results and add further information to the case, you can jump into the third and final AI Engine alarm. This progression alarm indicates a progression through the Cyber Attack Lifecycle from target attainment to exfiltration/corruption/disruption.
Figure 10: AI Engine Progression Alarm
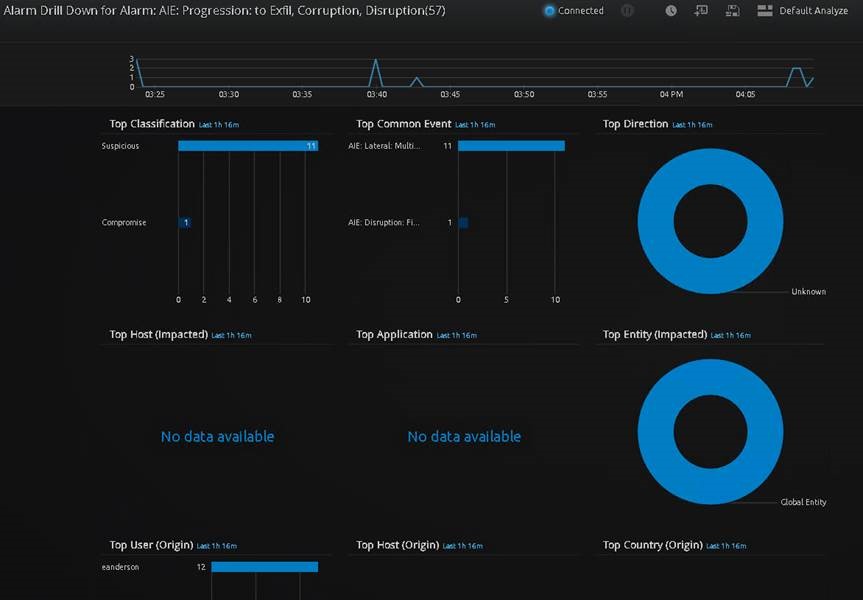
The final drill down into the progression rule immediately shows the two rules that were responsible for the progression rule to fire, along with the ability to confirm the origin user that was the culprit of this malicious insider activity — eanderson, aka Elliot Anderson, aka Mr. Robot.
Figure 11: Progression to Exfiltration/Corruption/Disruption Alarm Drill Down
Once you confirm the identity of the malicious user, you can automatically neutralize the insider threat and close the case.
Detecting Insider Threats Is Simplified with LogRhythm
In this use case, you stopped Mr. Robot from wreaking havoc on your environment. This insider threat was quickly detected and neutralized through advanced features, including File Integrity Monitoring, privileged user and group lists, UEBA, and an intuitive centralized UI/UX.
To take your UEBA capabilities to the next level, you can layer behavior-based analytics on top of scenario-based analytics to detect threats across the full spectrum of known (e.g., DDoS and drive-by attacks) and unknown threats (e.g., insider threats and zero-day malware).
If you’re interested in learning more about how LogRhythm can help you stop insider threats and detect stolen accounts using full spectrum analytics, read the in-depth review by SANS Analyst, Dave Shackleford below.