Attacks on operational technology (OT) have been rising in the for the last decade.[1] The rise began with the Stuxnet worm that attacked Programmable Logic Controllers (PLCs) in SCADA systems and has increased sharply in the last few years. Much of this increase is largely due to the migration of ransomware from IT environments to OT environments. NotPetya malware, especially, has focused its attacks on critical infrastructure, threatening the loss of data and paralyzing corporations and government agencies.
Claroty and LogRhythm for Effective Operational Technology Visibility
To support protection and best practice guidelines, you might consider implementing OT security platforms such as Claroty in OT infrastructure. Claroty Continuous Threat Detection (CTD) provides visibility, threat monitoring, and insights into industrial control system (ICS) networks.
When integrated with the LogRhythm SIEM Platform’s full stack of capabilities, your team will receive consolidated, centralized security visibility of your OT environment. LogRhythm’s platform ingests security events from Claroty CTD and correlates these events with other data from solutions such as antivirus or endpoint detection and response (EDR) and provide risk-based analytics to detect attacks in your environment.
LogRhythm RespondX also offers security orchestration, automation and eesponse (SOAR) features for rapid response options to help reduce both mean time to detect (MTTD) and mean time to respond (MTTR).
Operation Technology Security Events and Use Cases
Although, protecting IT environments and OT environments have their differences, there are some similarities when it comes to detecting lateral movement from a malware attack.
We will explore how integrated Claroty CTD with the LogRhythm SIEM can help you detect EternalBlue, a common high-impact malware that utilizes lateral movement.
Investigate a Malware Infection
Using scenario-based analytics, LogRhythm can correlate events from Claroty that are related to EternalBlue to provide a holistic view of your OT environment.
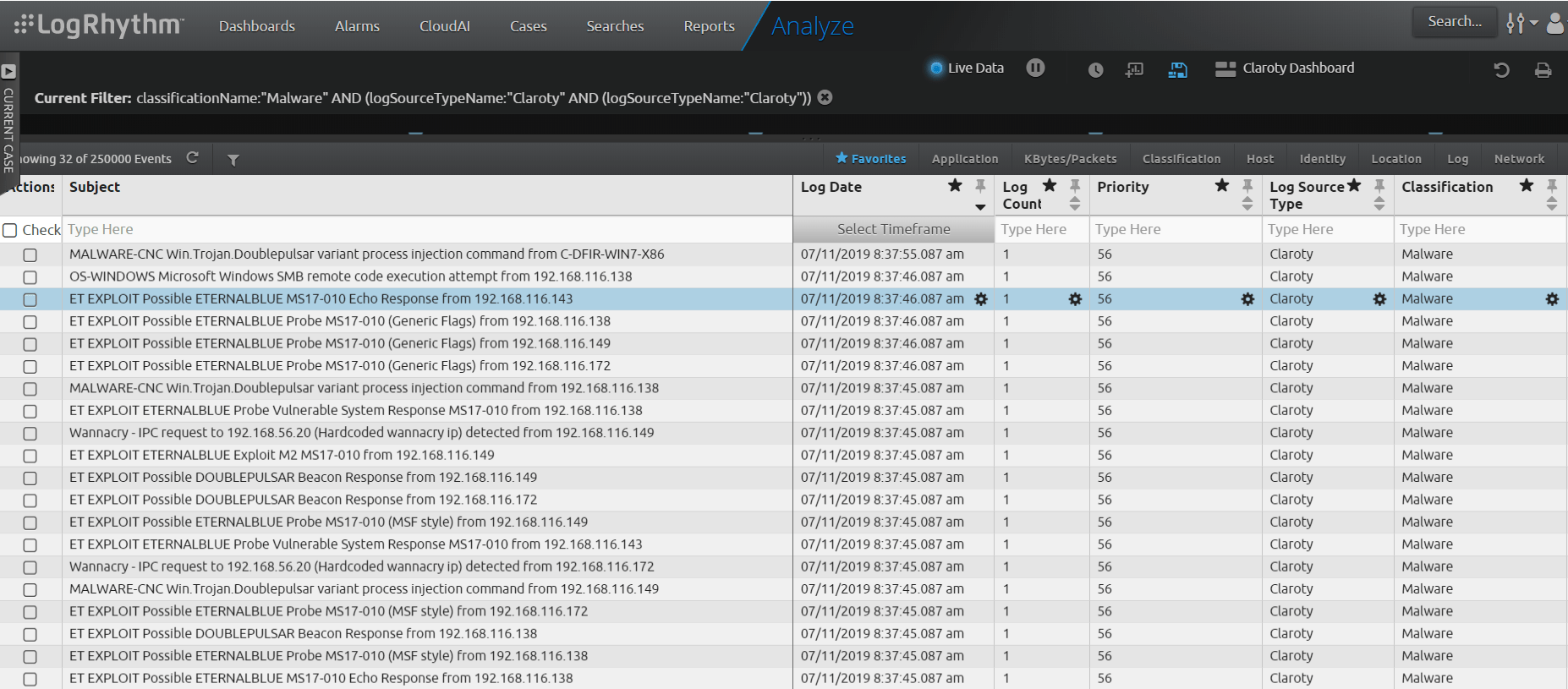
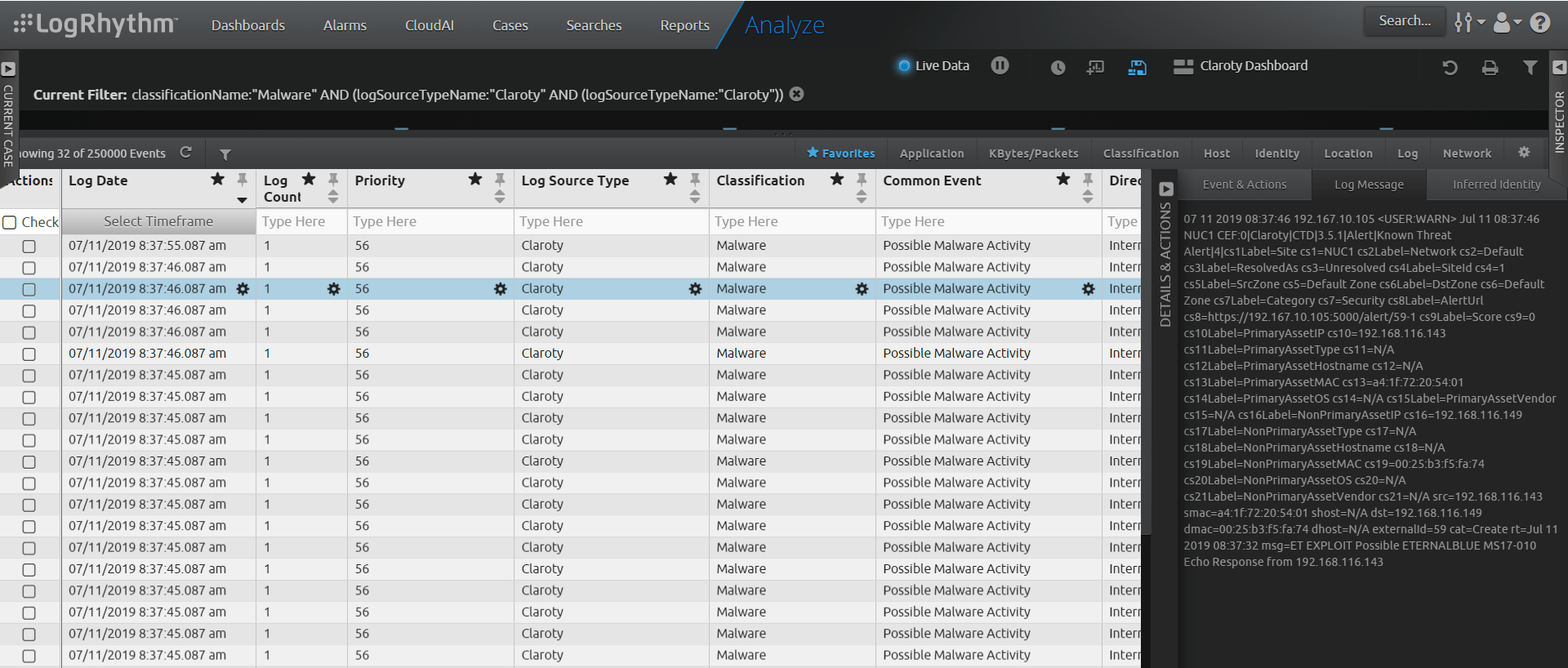
Gather Forensic Evidence
It’s important to gather forensic evidence to help your team identify, understand, and stop an attack quickly. Forensic evidence also serves as important intel when looking into other investigations.
The Claroty and LogRhythm integration allows you to see the original logs from the Claroty system in the LogRhythm dashboard. This dashboard will show your team where an attack started and help it decide the next best steps to take.
Detect Asset Changes in Your OT Environment
While there are similarities when detecting malware in IT and OT environments, there is a significant difference in monitoring “new asset” events in OT environments.
In typical IT environments, “new asset” events don’t raise eyebrows because the use of dynamic host configuration protocol (DHCP) and bring your own device (BYOD) practices cause frequent asset changes. However, in OT environments, “new asset” events are less common and require monitoring. If a new asset registers, it could simply be an approved system, or it could be an attacker trying to penetrate your OT environment.
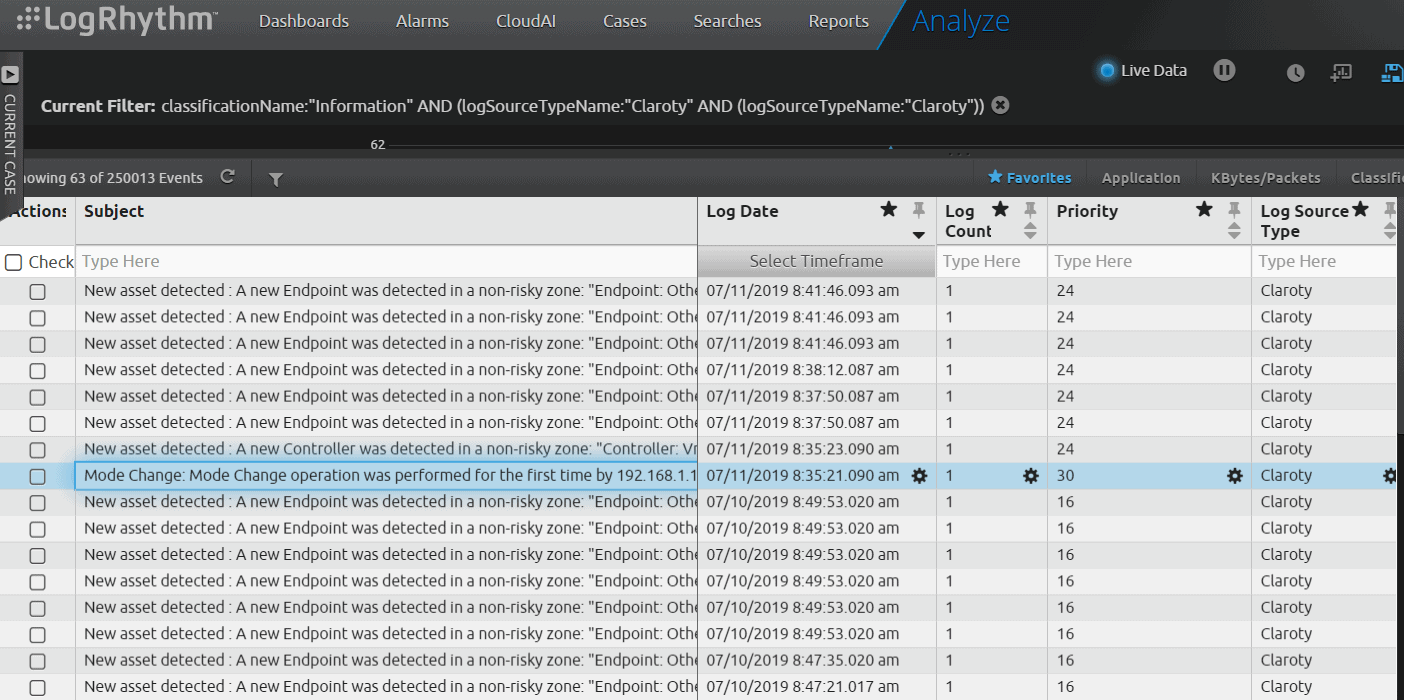
Detect Mode Changes in Your OT Environment
Claroty CTD detects anomalies in customer environments such as configuration changes, baseline deviation, and OT system mode changes. These are important changes to monitor in OT environments because they do not happen frequently.
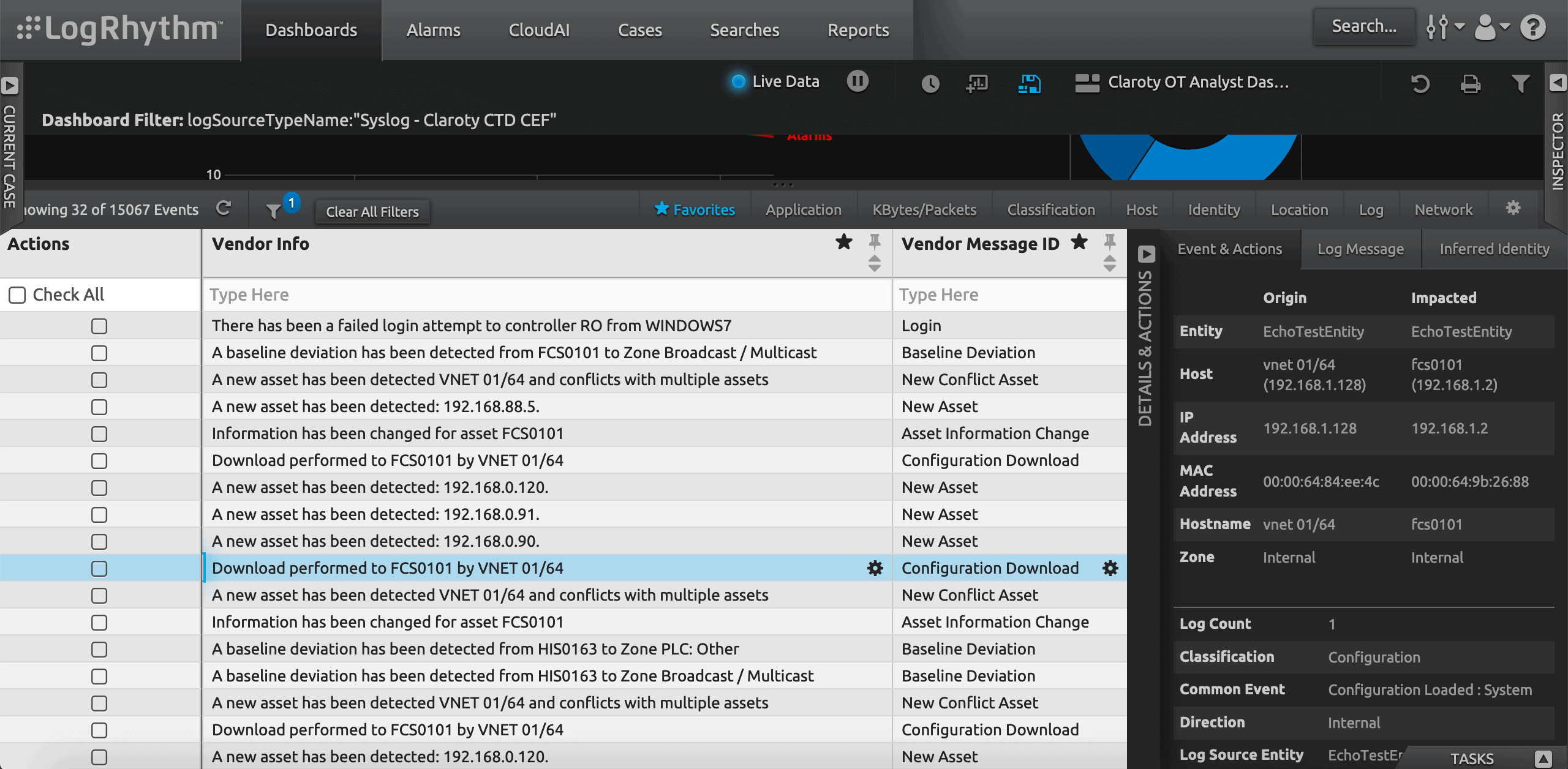
Monitor Any Change in Your OT Environment
LogRhythm provides a Claroty Change Monitoring Dashboard to monitor any changes in your OT environment in one view. This dashboard provides trend information about when most changes happen within your environment, so you can see when there is an anomaly. This dashboard is available in the dashboards section in Community under Shareables.
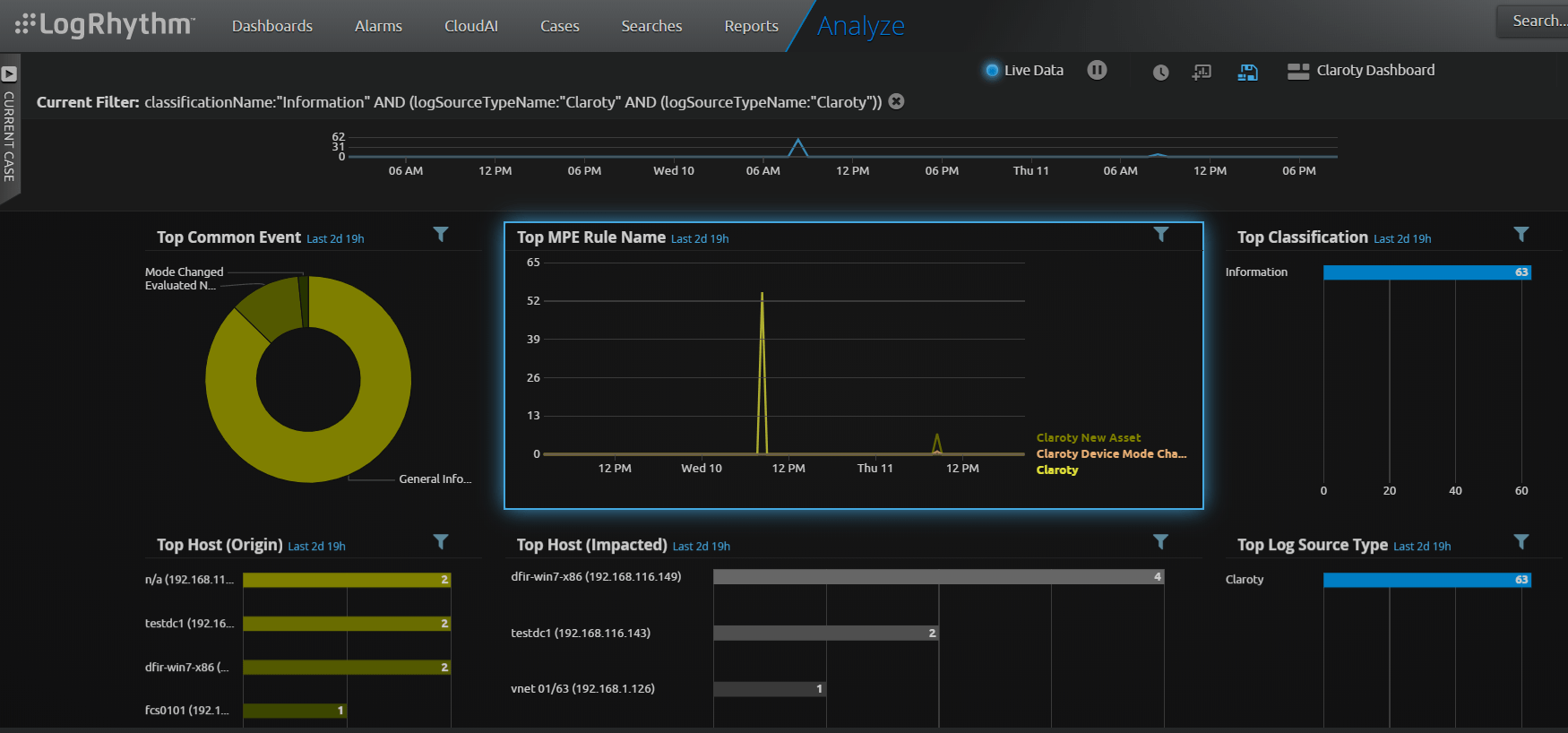
OT Security Threat Hunting with Claroty
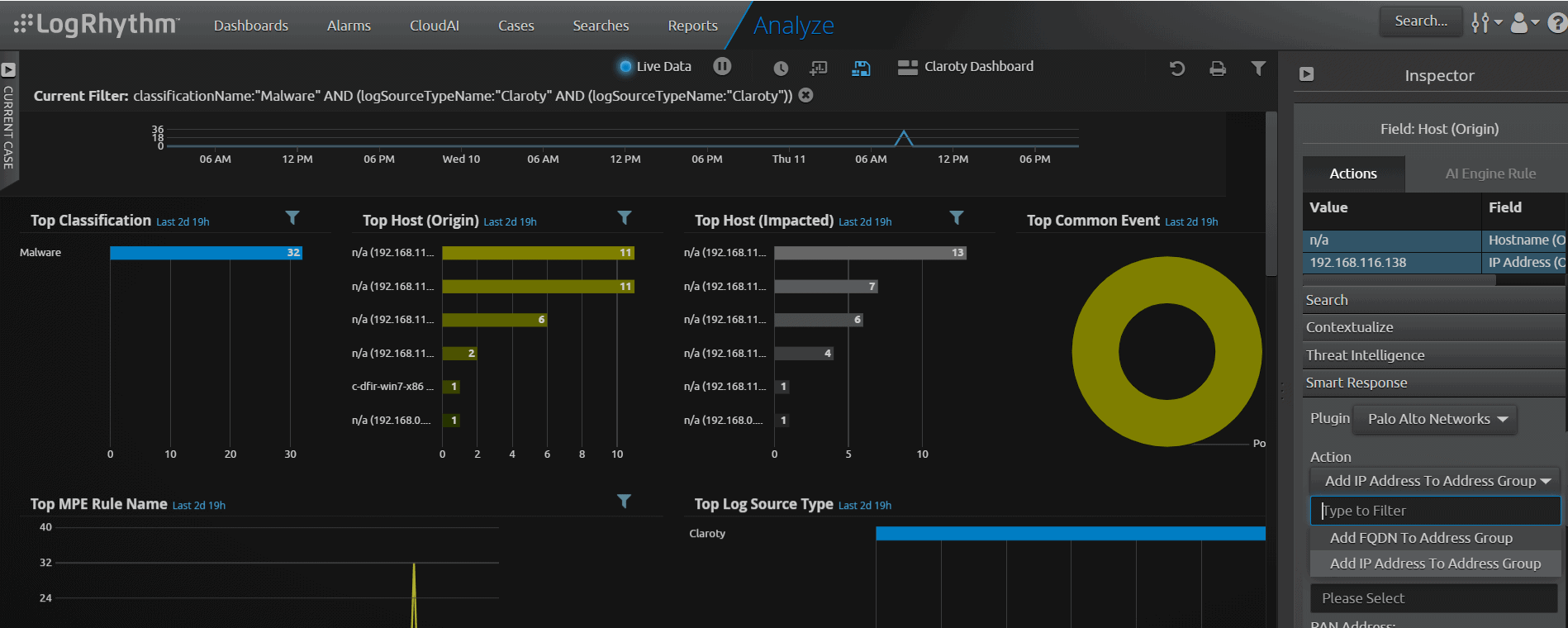
Dashboards are a vital component for investigation, because they provide a status on your OT security environment status in a glance. Most analysts’ first step during a threat-hunting exercise is to look at the alarms view in their LogRhythm dashboard. The alarms view provides notifications on what events or traffic require further investigation.
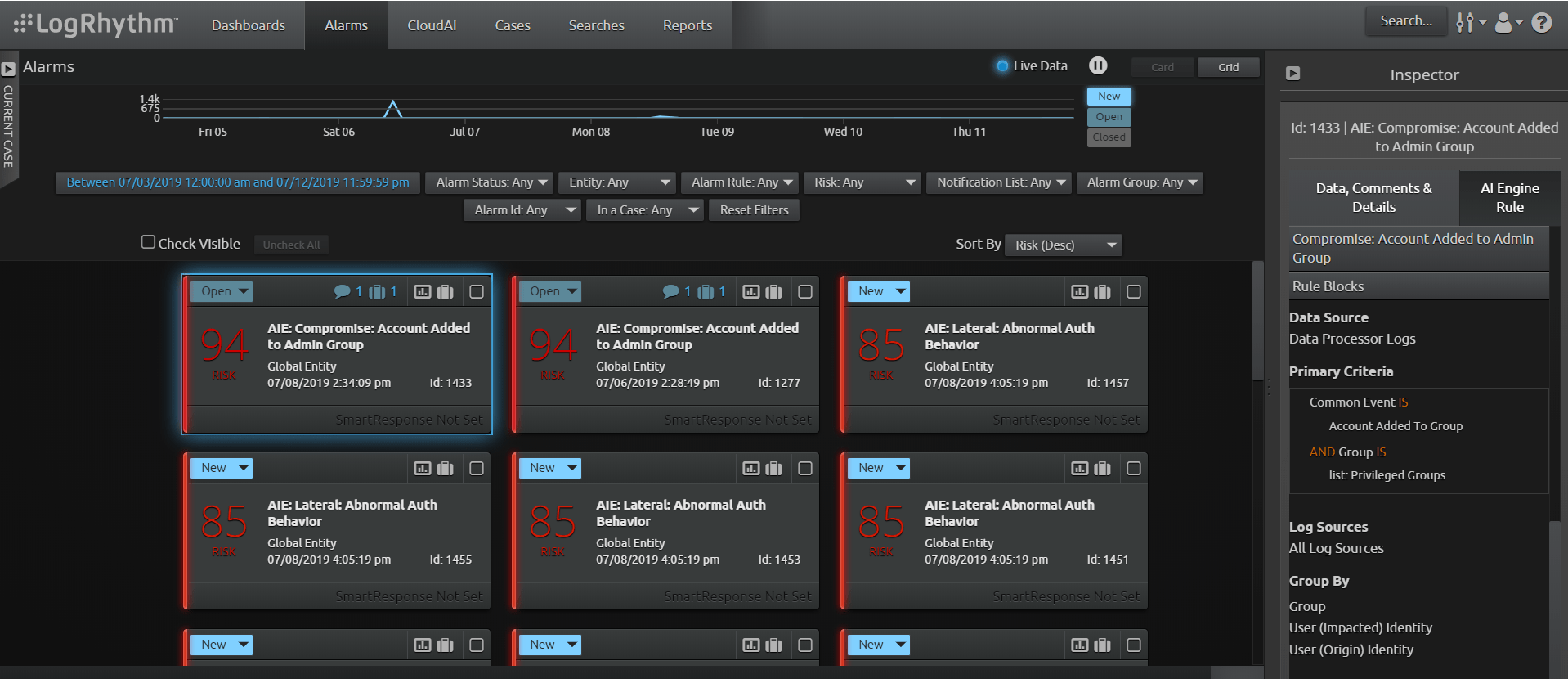
With the LogRhythm Alarms view, you can prioritize investigation and drill down to the correlated events that triggered the alarms for further analysis.
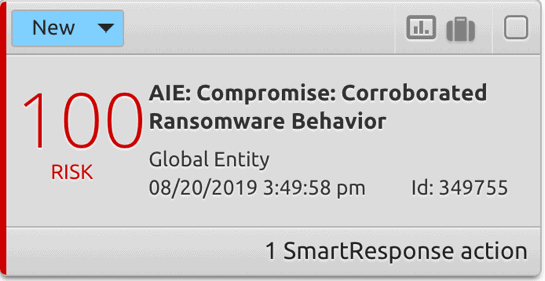
High-priority alarms, like ransomware alarms, can be linked to LogRhythm SmartResponse™ automation to trigger actions. With SmartResponse, you can enable actions like vulnerability scans, quarantine of an infected host, and disabling user accounts in seconds.
Control and Manage Events in One Platform
With the Claroty dashboard, you can use LogRhythm as centralized platform to control and manage all events in your OT environment.
In the dashboard, you can identify an attack on your OT environment, understand if the attack came from inside or outside your environment, and do further analysis.
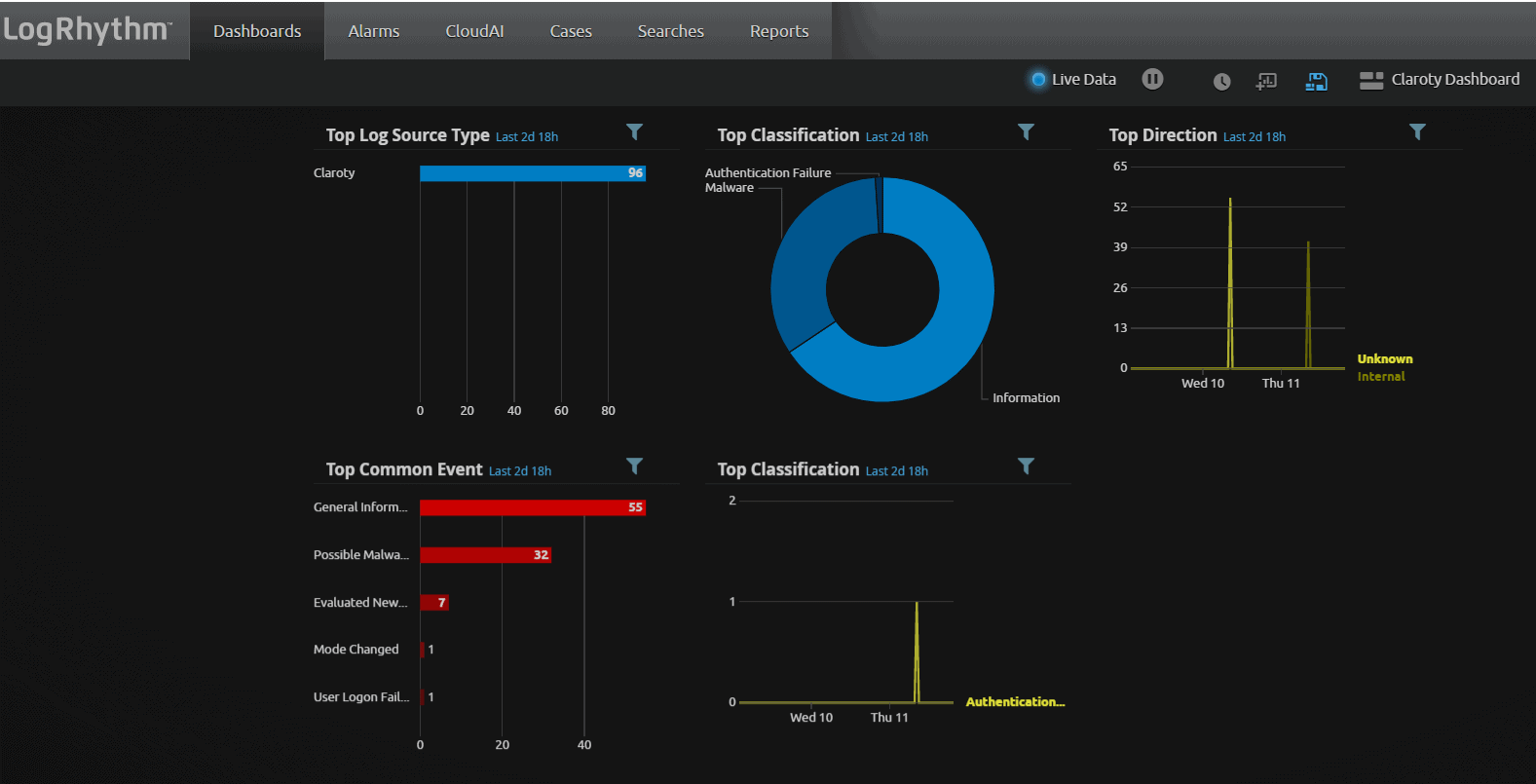
To gather more information, LogRhythm provides pivot-searching capabilities. By double-clicking data in the dashboard, which in this case is “possible malware” under common events, you can identify which hostname or IP address generated the event.
In the same dashboard, you can also run a SmartResponse automation task for your firewall’s policy to add the infected system into a block list and quarantine the infected hostname or IP address.
Geolocation Capabilities
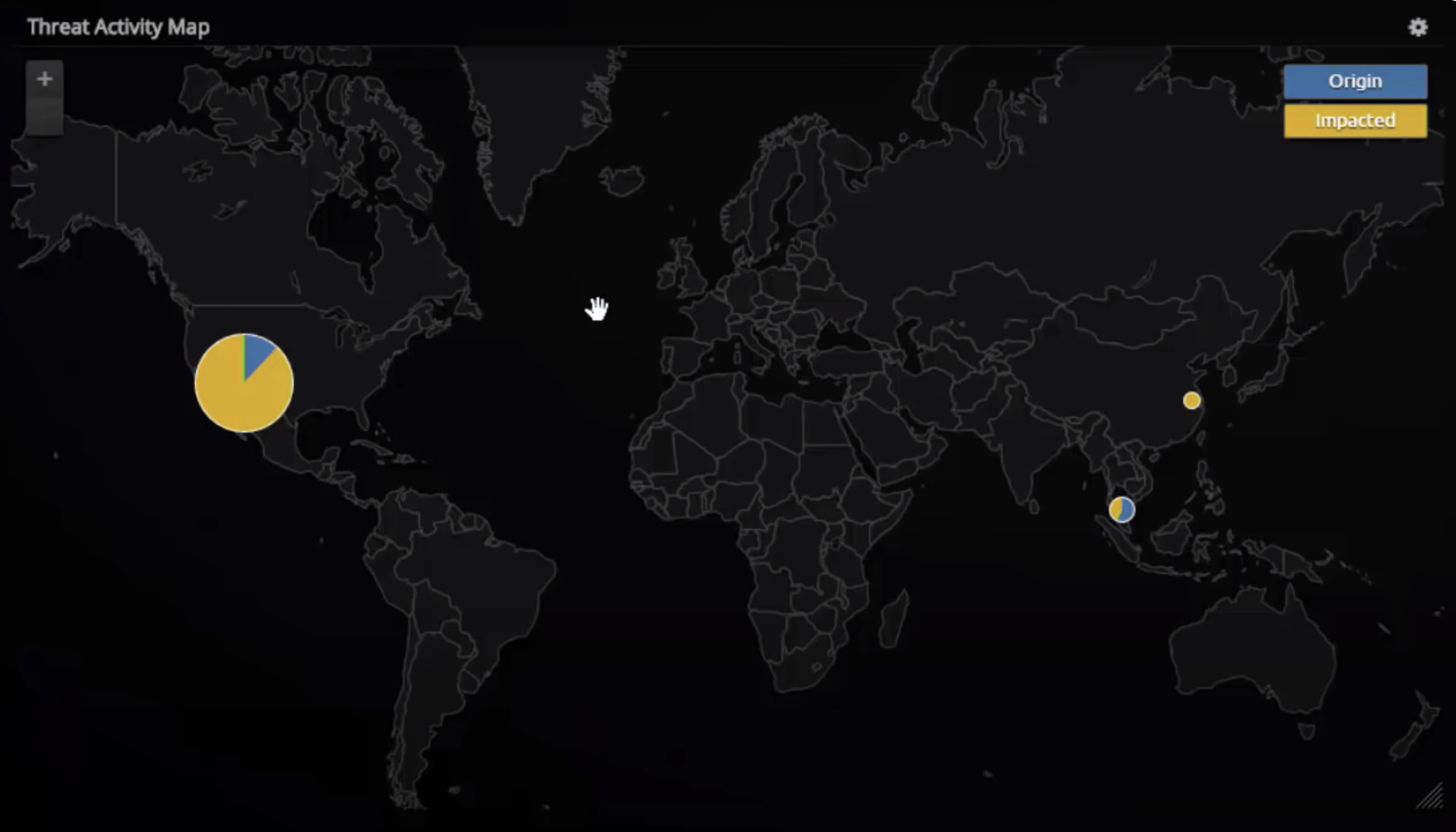
LogRhythm also provides a dashboard for interactive network visualization with integrated geolocation capabilities. This geolocation information helps you identify the country where an attack originated from and temporarily block any traffic in and out of that country until a ransomware outbreak is reduced.
Rapid Case Creation
LogRhythm Case Management allows you to organize the data you gather during investigation in a central repository to ensure you don’t overlook anything from the case.
By using Case Management, you can build a case to show a relationship between the ransomware information and malware classification information you gathered from your Claroty dashboards. With this information, you’re able to track the incident and add all related events, forensic files, and any additional notes all in the same user interface.
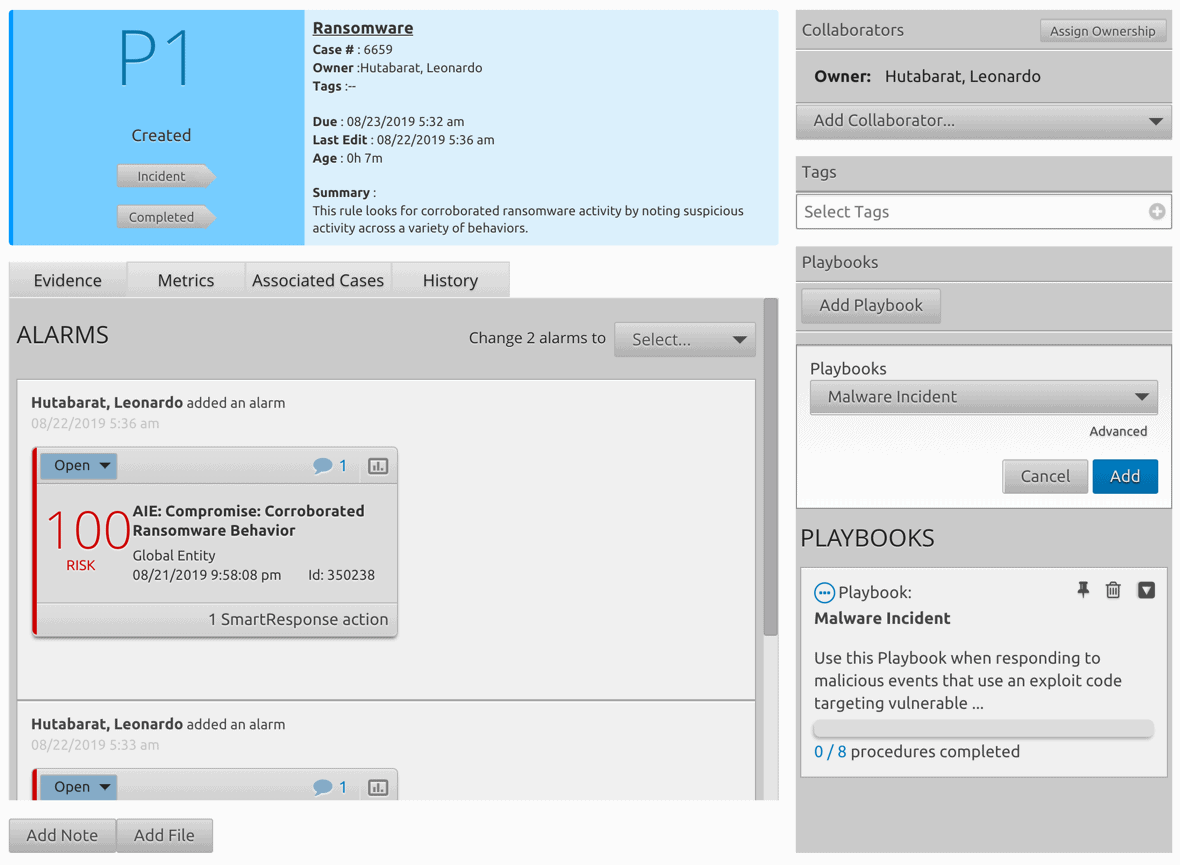
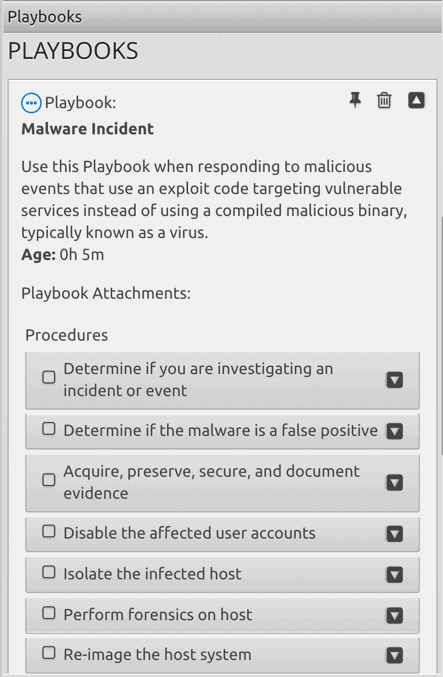
LogRhythm also incorporates Case Management into our Web Console using playbooks. You can attach playbooks to cases to give an analyst step-by-step guidance on how to resolve an incident effectively and efficiently.
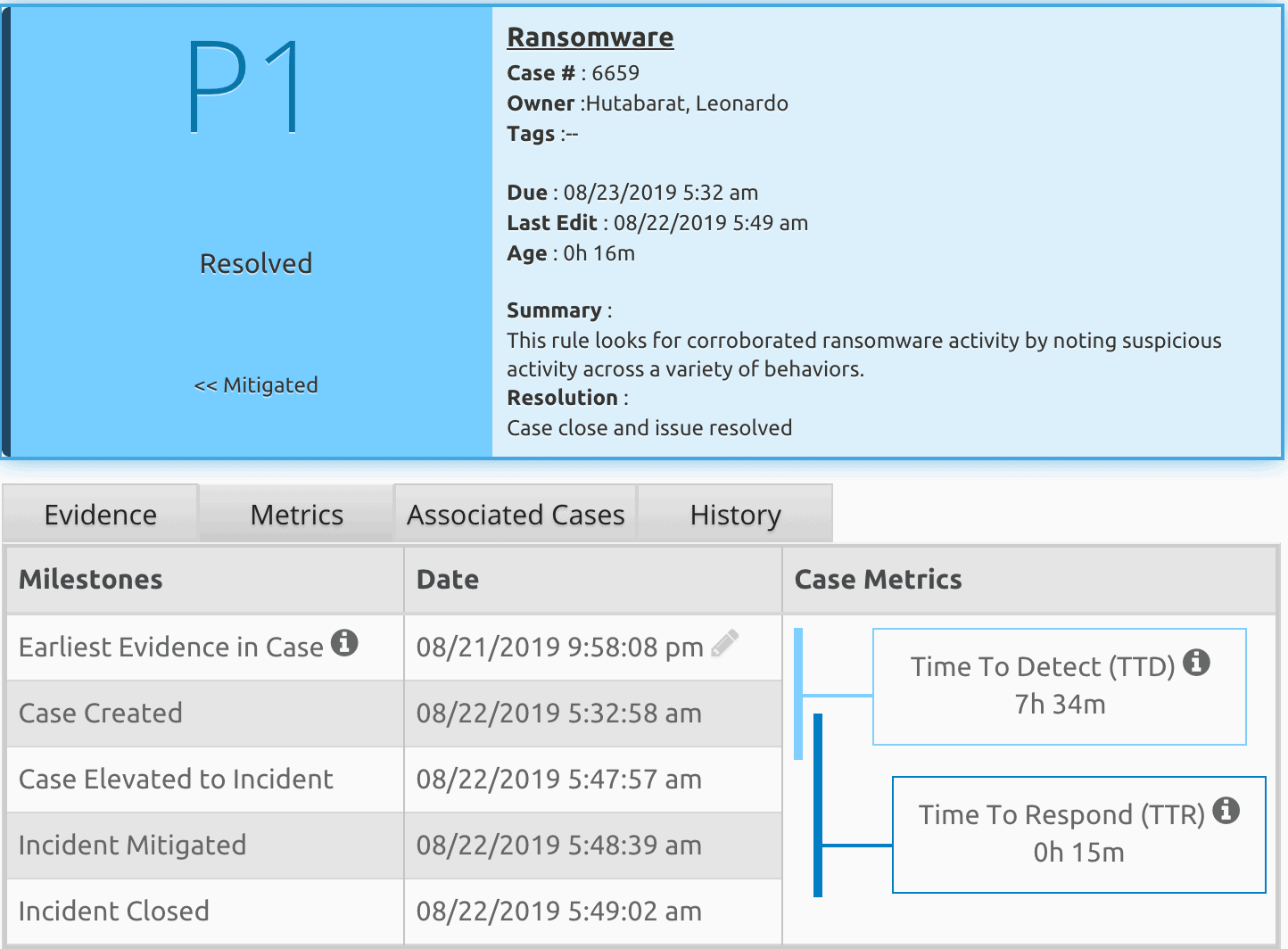
Incident Metrics
Once you resolved the issue and moved to closing the case, you should use incident metrics to strengthen your teams’ operations. LogRhythm’s incident metrics show MTTD and MTTR value can help improve your incident management processes.
Manage OT Environment Security Incidents
As cyberattacks on OT environments continue to increase, it will be critical to have a NextGen SIEM platform that can meet the unique security needs of an OT environment. LogRythm’s integration options allow teams in OT environments to manage events from a range of solutions, make correlations from events, and automate security workflow tasks from one platform.
To get started, visit the Community to download our Claroty CTD CEF configuration guide.
[1] Fortinet Operational Technology Security Trends Report, Fortinet, May 13, 2019
