After several meetings with health care security teams, it has become apparent that many information security departments are looking to move beyond basic, “check-the-box” compliance.
If you are in a health care organization, you may be seeking ways to improve your security posture and become more efficient and resilient. Sometimes the focus is on acquiring additional tools, and at other times, it’s about seeking support from managed service security providers (MSSPs) or some combination of the two.
Adding to the challenge of protecting patient data and ensuring patient safety is the business case that needs to be made because these investments are often seen as an expense or, at best, a cost avoidance. Given the current threat landscape and increased focus on health care by cybercriminals, what is the best way to build this business case? And what actions should you consider next?
Health Care Has Become a Focal Point
Recent articles highlight how hospitals have become a primary target for cybercrime. In an interview with InsideAlerts, Stuart Madnick, professor of information technology at the MIT Sloan School of Management, estimated that “hospitals are experiencing up to 70 percent of all ransomware attacks.”
The impact of these attacks cannot be understated when considering the potential impact on patients and business operations. The United Kingdom’s Department of Health and Social Care released its October 2018 report reviewing the impact of the 2017 WannaCry ransomware attack. Services were disrupted in one-third of the hospitals and eight percent of general practices. In total, 19,000 appointments or procedures were canceled. The immediate impact and costs to recover totaled over $118 million.
In the U.S., the consultancy firm CynergisTek released its annual report, Measuring Progress: Expanding the Horizon – 2019 Annual Report. The report reviews compliance with the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) with a sample of over 600 health care organizations and business associates.
CynergisTek found that, while compliance with HIPAA privacy regulations was 73 percent for health systems, that did not necessarily equate to security.1 It also found that health care organizations suffered two to three times more cyberattacks than other industries2. Additionally, while insider threats were the primary culprit for privacy breaches, vendors accounted for more than 20 percent of the breaches experienced.3
Building Your Business Case
How do you translate these risks and use them for your capital and operational funding requests? The best case to build for initial investments is one of cost avoidance and regulatory compliance.
Using studies and examples like those referenced earlier show hard dollar impacts when breaches have occurred in health care. There are also potential financial penalties to reference for violations of the Health Information Technology for Economic and Clinical Health Act (HITECH) when electronic protected health information (e-PHI) is lost. HIPAA violation fines range from $100 to $50,000, up to a maximum $1.5M per year for each violation.
Beyond meeting the compliance requirements of HITECH and avoiding fines, assuring and protecting privacy is a primary driver for any healthcare organization to mature their security operations. Consumers/patients expect that their privacy will be protected in a world where this is the norm across industries with the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) established in 2018. Failing to do so threatens the market position of an organization.
The largest HIPAA settlement following a data breach so far was $16 million which happened in 2018. Additionally, the Office for Civil Rights (OCR) pursues criminal charges in some cases and adds organizations to the publicly available OCR Breach Portal.
Track Your Own ROI
As you develop your SOC, tracking improvements related to your mean time to detect (MTTD) and mean time to respond (MTTR) to threats over time can build a powerful financial justification. An earlier blog post, “Evaluating the Maturity of Your SOC in Health Care,” referenced research by the Aberdeen Group that demonstrate significant savings when minimizing the dwell time of a threat.
The study, Quantifying the Value of Time in Cyber-Threat Detection and Response Aberdeen Group, determined that decreasing the dwell time of a threat actor4:
- to 30 days reduces the business impact by 23 percent
- to 7 days reduces the business impact by 77 percent
- to 1 day reduces the business impact by up to 96 percent
After time, showing more detailed reports that focus on how you have protected your organization from specific threats and what those impacts avoided in terms of financial costs can be a very powerful, personal story for securing additional support from your health care organization. You can use this data to build a case to supplement your SOC with off hours and weekend coverage with co-management from a managed services security provider (MSSP).
Maturing Your Information Security Position
After meeting basic regulatory compliance for security, it is time to plan the next phase of maturity to become even more efficient and resilient. There are a variety of cybersecurity frameworks and models for assessing the maturity of your information security position like the NIST Cybersecurity Framework and the Cybersecurity Capability Maturity Model (C2M2) for the energy sector. We will be using LogRhythm’s Security Operation Maturity Model as our reference.
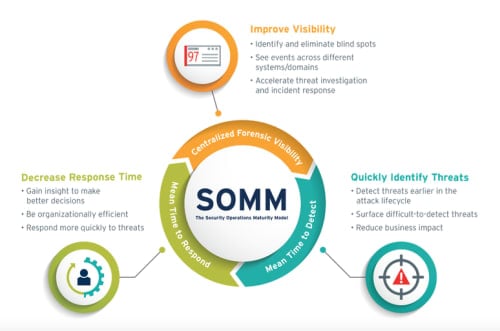 Figure 1: Outcomes of the Security Operations Maturity Model
Figure 1: Outcomes of the Security Operations Maturity Model
A key component in moving from a Level 1 (minimally compliant posture) to a Level 2 (securely compliant posture) is improved efficiency. This can entail investing in or improving the adoption of a Security Information and Event Management (SIEM) platform that centralizes your log data and security event management.
To move beyond the minimally compliant level, you need to consider how to increase visibility to data in transit in addition to the final resting place of that data to ensure safety along the entire privacy journey. The SIEM will likely have the most exposure to your overall data and be a critical tool in maturing your SOC and protecting the privacy of your patients.
A good SIEM platform will also provide a means of standardizing workflows with structured playbooks to guide your security analysts and provide repeatable processes to manage specific threats. Creating these standards for operations and adapting them as threats change over time improves the reliability of your SOC and enhances their ability to reduce MTTD and MTTR. Playbooks can also benefit managers as a tool to help train and increase the efficiency of new security analysts.
While centralizing log data, event management and standardizing workflows in responding to incidents may seem like basic steps, they are critical ones to take as you mature your SOC. You will still have vulnerabilities to more advanced persistent threats, but you will be more aware of where your blind spots are and more resilient to cybercriminals.
It would be nice to remove all vulnerabilities at once, but maturing your operations in a phased approach is necessary more often than not given the reality of financial and resource constraints particularly in health care. Please contact us with questions as you look at the next best step for your organization.
1 Measuring Progress: Expanding the Horizon 2019 Annual Report, Cynergistek
2 IBID
3 IBID
4 Quantifying the Value of Time in Cyber-Threat Detection and Response, Aberdeen Group, February 2016
