93% of Security Leaders Do Not Report to the CEO, According to New Research From LogRhythm
Global Research Finds IT Security Leaders Should Be Held Accountable for the Consequences of Cyberattacks, Yet Lack the Influence Required to Shore Up Security Strategies LogRhythm, the company powering today’s security operations centers (SOCs), announced the release of its report, “Security…
Read More
June 22, 2021
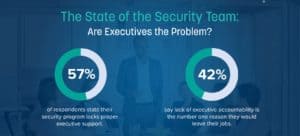
More than a third of organizations hold no one accountable for cyberattacks, according to research from LogRhythm
The global research reveals the disconnect between business decision makers and security teams, even as new risks from remote working and ransomware grow. London, UK. – June 22, 2021 – LogRhythm, the company powering today’s security operations centers (SOCs), has…
Read More
June 22, 2021
Total Economic Impact™ Study Reveals 258% ROI for LogRhythm SIEM
Organizations seeking a platform to mature their security operations center (SOC) and reduce risk to the business must make monumental decisions when choosing a security solution. IT security leaders need to understand the benefits, costs, and risks associated with implementing…
Read More
June 16, 2021
Highlights from RSAC 2021: Zero Trust, XDR, Cybersecurity Careers, and More
Posted by: Amy Tierney
In the months since the global pandemic impacted the U.S., people shifted to new ways of working and living, and new obstacles to overcome. As if the Covid-19 pandemic wasn’t challenging enough, this year we’ve already witnessed prominent cybersecurity attacks…
Read More
May 28, 2021
Sunspot Malware Scoured Servers for SolarWinds Builds That it Could Weaponize
The novelty of the malware “stems from how well it blends into the build process,” said Brian Coulson, principal threat research engineer at LogRhythm. “The adversary appears to have had great knowledge of the build process prior to the execution of…
Read More
January 13, 2021
Russian Hack Against the U.S. Government ‘Will Take Years to Overcome,’ Former National Intelligence Official Says
Susan Gordon, former principal deputy director of national intelligence, told CNBC that the massive cyberattack targeting federal agencies “will take years to overcome” as senior intelligence officials report there is little doubt the Russians were the perpetrators and that they’re still at…
Read More
December 18, 2020
7 Common CISO Pain Points and How to Overcome Them
Working in cybersecurity has its clear benefits: bringing value to a vital industry, competitive pay, and a thriving job market. With any career, however, there will always be pain points and some aspects that are less exciting than others. As someone…
Read More
November 1, 2020
Keeping Connected Devices Secure: National Cybersecurity Awareness Month Week 4
Do Your Part. #BeCyberSmart is the motto at the heart of this year’s National Cybersecurity Awareness Month (NCSAM). Promoted by the National Cybersecurity and Infrastructure Agency, the month-long event, now in its 17th year, offers key guidance in a world…
Read More
October 26, 2020
What is the Zero Trust Model of Cybersecurity, Really?
The Zero Trust Model framework is the next evolution of our security model. Explore what exactly the Zero Trust model is and how companies have successfully implemented their own models. The Zero Trust Model Explained The original Zero Trust model…
Read More
October 1, 2020
5 Ways to Alleviate Stress on Security Teams
Security teams are under more stress than ever. While that fact may not exactly make you fall out of your chair with surprise, our recent research report found that a whopping 75 percent of security professionals say they have more…
Read More
July 28, 2020
Australia Comes Under Comprehensive, ‘State-Sponsored’ Cyber Attack, LogRhythm Comments
Today, the Australian Prime Minister Scott Morrison announced that the country is under sustained and sophisticated ‘state-sponsored’ cyberattack that is targeting all levels of government, essential services and business. The attacks have been happening for over a month and are…
Read More
June 22, 2020
Deepen Your Remote Desktop Protocol Visibility with Log Sources
Posted by: Andrew Hollister
Remote desktop is a common feature in operating systems. It allows a user to connect to a computer in another location and interact with the desktop remotely. Microsoft implemented this capability via its Remote Desktop Protocol (RDP) for Windows desktop…
Read More
April 24, 2020
Monitor Zoom Security and Privacy Risks Using the LogRhythm NextGen SIEM
Posted by: Andrew Hollister
The mass migration to remote working in recent times has caused an increased focus on the security of remote collaboration tools. LogRhythm has found a variety of these tools in our customer base and has built collection methods and analytics…
Read More
April 21, 2020
Beware of Coronavirus Phishing Attempts — Tips to Keep Your Organization Safe
Coronavirus: it’s what every news outlet and person is talking about. With the outbreak of the infection, people want to stay up to date on the latest news and reports, so they’re looking up data and clicking on links to…
Read More
March 9, 2020
8 Cybersecurity Predictions for 2020
Posted by: LogRhythm Labs
As we do each year, the LogRhythm Labs team came together recently to reflect on the year in cybersecurity and think about what’s to come. 2019 was definitely interesting. Breaches continued to keep organizations on their toes, with over 5,000…
Read More
December 11, 2019
LogRhythm Brings Greater Choice to SIEM Pricing
For years, consumption-based pricing has dominated the security information and event management (SIEM) market. Whether organizations paid a fixed amount based on message per second, event per second, or gigabyte per day, that model was the go-to standard. However, as…
Read More
November 11, 2019
Experts Weigh in on National Cybersecurity Awareness Program
In honor of National Cybersecurity Awareness Month, we sat down with some of our security experts to talk about their experience raising awareness in the industry and implementing cyber training. Read the interview to get their thoughts and some inspiration…
Read More
October 28, 2019
The Top Five Benefits of Cloud SIEM, According to Security Experts
Gartner predicts that “By 2023, 80% of SIEM solutions will have capabilities that are only delivered via the cloud (for example, log storage, analytics, incident management), up from 20% currently.” As SIEM solutions start to offer their products via the…
Read More
August 20, 2019