Top Ransomware Detection Techniques
Posted by: Sally Vincent
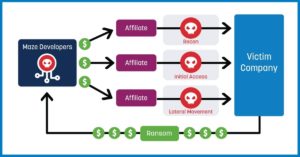
Ransomware is defined as a type of malware that blocks access to data until a sum of money is paid. This niche type of cybercrime is now big business due to the rise of cryptocurrency and the ransomware as a…
Read More
January 13, 2022
Enriching MITRE ATT&CK Techniques for Better Threat Detection
Read More
December 29, 2021
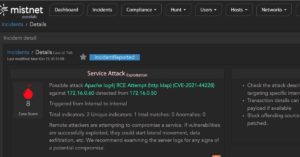
Detecting Log4Shell with MistNet NDR and NetMon
Posted by: Andrew Hollister
To help security teams stay on top of Log4Shell, LogRhythm Labs recently released information for detecting the vulnerability with the LogRhythm NextGen SIEM and MistNet NDR platforms. In this blog, we’ll continue to dive deeper as we uncover more detection…
Read More
December 20, 2021
CVE-2021-44228 Log4Shell Detection
Posted by: Brian Coulson
News is spreading fast about the recent CVE-2021-44228 Log4Shell vulnerability. SANS noted that the first exploit seen by Cloudflare was 4:36 GMT on December 1st. This was eight days prior to the Proof of Concept (PoC) exploit published on GitHub on December 9th. SANS saw first attempts at 12:32 PM on December 9th. In…
Read More
December 14, 2021
A Look Back at Which Predictions Came True in 2021
In 2021, cybercriminals took aim at critical infrastructure with ransomware attacks on Colonial Pipeline, JBS and others. They also continued to find new ways to exploit employees working remotely, those seeking information on COVID-19 vaccines, and improperly secured APIs. In…
Read More
December 8, 2021
Conducting an Information Security Risk Assessment Successfully
Posted by: Kyle Dimitt
Management of risk is not a simple undertaking but is essential for enterprise governance and decision making. Whether a company is adopting an enterprise risk management framework (e.g., ISO 31000, COSO, or NIST RMF) or building out an information security…
Read More
November 22, 2021
Ransomware-as-a-Service Breakdown: Auditing Conti and REvil TTPs Using the MITRE ATT&CK Framework
Read More
November 3, 2021
Integrating SIEM Within Compliance Programs
Posted by: Rem Jaques
At their core, information security and compliance seem like topics that should go hand in hand: InfoSec deals with the daily functions of identifying and responding to threats, while compliance includes responsibilities of implementing IT security controls and effective governance.…
Read More
July 19, 2021
Don’t Gamble with Golden SAML
Read More
June 30, 2021
Aligning Security Controls with Leading Cybersecurity Frameworks
Read More
June 16, 2021
Ransomware Detection and Mitigation Strategies in OT/ICS Environments
Posted by: Brian Coulson
On 9 May 21, the Federal Bureau of Investigation (FBI) issued a statement regarding a network disruption at Colonial Pipeline, one of the largest fuel pipelines servicing the eastern United States. Following immediate operational shutdowns and further initial investigation, the…
Read More
May 27, 2021
Moving Laterally to the Microsoft 365 Cloud Using a Simulated Domain Trust Modification Attack
Read More
May 19, 2021
Dissecting the Golden SAML Attack Used by Attackers Exploiting the SUNBURST Backdoor
Read More
March 5, 2021
Windows Certificate Export: Detections Inspired by the SolarWinds Compromise
Posted by: LogRhythm Labs
TL/DR Methods to detect when a certificate is exported from a Windows system are discussed in detail below using the audit log “Certificate Services Lifecycle Notifications” and collecting the log messages with “MS Windows Event Logging XML – Generic” log…
Read More
January 21, 2021
Telecommunication Security Use Cases
Posted by: Leonardo Hutabarat
Attacks made against telcos and internet service providers (ISPs) have steadily risen. Distributed denial of service (DDoS) attackers launched an 11-day attack against a Chinese telco in 2017 — breaking the DDoS record that year. That same year, Kaspersky Lab…
Read More
January 6, 2021
How to Detect and Respond to SS7 Attacks — OT Telco Use Cases
Posted by: Leonardo Hutabarat
In the telecom environment, using Signaling System No.7 (SS7) protocol is very crucial, especially in 2G networks. If you’re wondering how SS7 works, SS7 protocol is an international telecommunications standard used to set up public switched telephone network (PSTN) and…
Read More
December 28, 2020
How to Detect and Search for SolarWinds IOCs in LogRhythm
Posted by: LogRhythm Labs
LogRhythm Labs has gathered up the indicators of compromise (IOCs) from CISA, Volexity, and FireEye associated with the recent SolarWinds supply chain attack and made them available in a GitHub repository for your convenience. Feel free to download and import…
Read More
December 23, 2020
Threat Hunting Framework: Three Steps to Translate Threat Reports into Actionable Steps
Thanks to Sally Vincent and Dan Kaiser from the LogRhythm Labs team for developing the process and guiding content described in this post. Threat research can be an invaluable asset to security teams when attempting to formulate a proactive stance…
Read More
December 21, 2020