Aligning the LogRhythm NextGen SIEM Platform with the MITRE ATT&CK Framework
Posted by: LogRhythm Labs
Contributors to this blog include Dan Kaiser and Brian Coulson. The MITRE ATT&CK framework is quickly becoming a focal point in the security world — and for good reason. This framework provides a consistent, industry-wide standard on which you can…
Read More
April 15, 2019
Exploring Legitimate Interest within the GDPR
We often get asked how to position, illustrate, and sell products worldwide when everyone still has the General Data Protection Regulation (GDPR) on their mind. We receive so many inquiries, that we decided to create this blog post. Depending on…
Read More
March 20, 2019
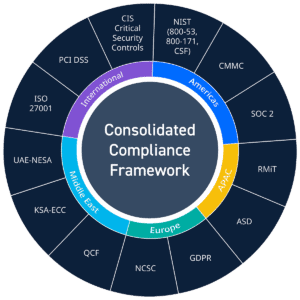
Simplify Compliance with LogRhythm’s Consolidated Compliance Framework and NIST
Compliance may seem complicated, but here at LogRhythm, were doing our best to simplify the hassle. As new compliance and security-related legislation, regulations, and standards are introduced every year, you might not know which regulations apply to your organization or…
Read More
December 4, 2018
8 Cybersecurity Predictions for 2019
Posted by: LogRhythm Labs
For the fourth year in a row, the LogRhythm Labs team came together to answer a question that’s on everyone’s mind this time of year: what is going to happen in cybersecurity next year? A few weeks ago, we revisited…
Read More
December 3, 2018
Looking Back at LogRhythm Labs’ 2018 Predictions for Security – How Did We Do?
About this time every year, the LogRhythm Labs team watches bird flights, performs divination rituals, and contemplates what might happen in the world of information security in the coming year. Last year, we started a new tradition of examining our…
Read More
November 16, 2018
Your Questions About New U.S. State-Level Data Protection Laws Answered
This year, at least 11 U.S. states passed new or updated laws, with several specifically focused on data breach notification and data protection. From Alabama implementing its first data breach notification law to California passing its Consumer Privacy Act and…
Read More
November 13, 2018
Creating and Managing Playbooks with LogRhythm APIs
New to LogRhythm 7.4: Playbooks Feature Set Standard procedures have been a cornerstone of security best practice since their invention. You may call them runbooks, standing procedures, checklists, or playbooks. Either way, you likely have one or more collections of…
Read More
October 29, 2018
NotPetya Anniversary — Is a Version 2 Coming?
Just over a year ago, the world saw two major ransomware outbreaks in short succession. The first being WannaCry, followed by NotPetya a few weeks later. Unlike WannaCry, NotPetya infected machines on a network by exploiting the devices that were…
Read More
July 5, 2018
Detecting Drupalgeddon 2.0
Despite a patch being released for the Drupal vulnerability known as Drupalgeddon 2.0, educational institutions and government entities globally are still feeling its impacts. Since its release on March 28, 2018, the bug has impacted about 1 million sites that…
Read More
June 27, 2018
Time to Reset Your Router? Understanding and Removing VPNFilter Malware
On May 23, 2018, Talos Group released its analysis of an ongoing malware attack it named “VPNFilter.” The Talos analysis indicates that this attack was first identified in 2016 and, as of June 2018, has compromised more than 500,000 endpoints.…
Read More
June 13, 2018
Take the First Steps Toward a Zero-Trust Model with Okta Automation
Managing multiple accounts across various cloud and on-premise infrastructures centrally is a challenge for most security operations centers. To address this ever-increasing need, the LogRhythm Office of the CISO recently implemented Okta. Okta enables a nearly seamless management process for…
Read More
May 21, 2018
Catch the Next WannaCry or NotPetya Ransomware Attack Before Damage Occurs
Posted by: LogRhythm Labs
Contributors to this blog include Nathaniel “Q” Quist and Sam Straka. On April 14, 2017, Shadow Brokers released a set of previously classified exploit tools developed by the National Security Agency. Within this cache of exploits, perhaps the most notorious…
Read More
May 14, 2018
Organizations Are Failing at Timely Detection of Threats
In today’s security space, we’re all too familiar with the challenges presented by industry-wide shortages in talent, budget, and dedicated security infrastructure. Many insights from the LogRhythm 2018 Cybersecurity: Perceptions & Practices benchmark survey confirm this common understanding, yet one…
Read More
April 24, 2018
Take a Deep Dive into PlugX Malware
In June 2017, Palo Alto’s Unit 42 Threat Research team published an excellent blog post on a newly detected version of the PlugX malware family, also known as “Korplug.” Interested to find out more about this new variant, I started…
Read More
April 18, 2018
Insider Threat Use Case: Detecting and Stopping Cryptojacking
Cryptocurrency is a hot topic right now, and even though its price is drastically falling across the board, this incredible technology will have lasting impacts on the world for years to come. Though a majority of the focus on cryptocurrencies…
Read More
April 5, 2018
Detecting Memcached DDoS Attacks Targeting GitHub
Posted by: LogRhythm Labs
Contributors to this blog include Nathaniel “Q” Quist and Dan Kaiser. On February 28 and March 5, 2018, Memcached DDoS attacks targeted GitHub. LogRhythm Labs performed an investigation into the cause, effect, and outcome of these attacks. The following will…
Read More
March 8, 2018
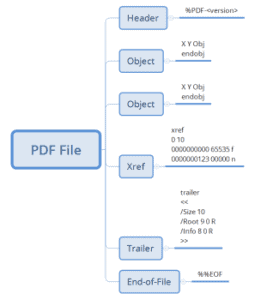
Detecting Potentially Malicious Javascript Embedded Within a PDF File Using LogRhythm Netmon
Various blog posts have been written by LogRhythm’s very own resident LogRhythm NetMon expert Rob McGovern regarding the numerous benefits of using Deep Packet Analytics within NetMon. If you’re not already familiar with deep packet analytics (DPA) rules, Rob’s post…
Read More
February 27, 2018
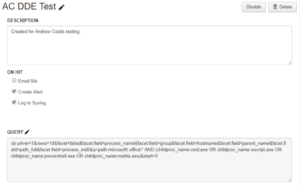
Dynamic Data Exchange (DDE): Detection and Response, Part 2
Part one of this blog series discussed what Dynamic Data Exchange (DDE) is, what an attack may look like, and steps for mitigation. In Part 2, I’ll cover how LogRhythm and Carbon Black can work together to help detect a…
Read More
February 20, 2018