Streamline Your Cyber Defense with the MITRE ATT&CK Framework
In this webcast, SANS reviews findings from a recent report, providing expert guidance to help cyber defense professionals learn how to best leverage the MITRE ATT&CK Framework to improve their organization’s security posture.
Read More
July 22, 2020
Detecting Operational Technology Threats with Claroty and LogRhythm
Posted by: Leonardo Hutabarat
Attacks on operational technology (OT) have been rising in the for the last decade.[1] The rise began with the Stuxnet worm that attacked Programmable Logic Controllers (PLCs) in SCADA systems and has increased sharply in the last few years. Much…
Read More
July 17, 2020
Securing Telemedicine: The Current Landscape and Future Risks
In this on-demand webinar, LogRhythm CSO James Carder and Healthcare Cybersecurity Advisor Kevin McDonald provide an overview of the growing telemedicine landscape, the specific threats attempting to exploit telemedicine, and a step-by-step plan that cybersecurity practitioners can implement to best protect their healthcare organization, practitioners, and patients.
Read More
July 10, 2020
A Roundup of LogRhythm’s Most Visited Technical Blog Posts
The LogRhythm blog is an abundance of content and insight from our LogRhythm Labs team, security tips and tricks, threat research, infosec news, use cases from our customers, and more to help you stay at the top of your game…
Read More
June 19, 2020
Anatomy of a Hacker Group: APT29 (AKA Cozy Bear)
Watch the on-demand webinar now to learn from members of LogRhythm Labs’ threat research team and Randy Franklin Smith of Ultimate Windows Security, who will do a deep-dive into the APT29 threat group, their activities, and how you can automate the detection and mitigation of threats either associated with the group or that use similar techniques.
Read More
June 9, 2020
4 Key Processes to Maximize Security Operations Center Procedure Effectiveness
Posted by: Amy Tierney
Building a security operations center (SOC) is a major undertaking, but it’s worth the effort to keep your organization secure. To create an efficient SOC, you need to develop security operations center procedures that connect people, processes, and technologies within…
Read More
June 4, 2020
A Security Analyst’s Guide to Monitoring Remote VPN Activity in the LogRhythm SIEM
Posted by: Brian Coulson
Remote work is no longer a trend, and is becoming the norm for many companies. Whether your organization has been practicing remote work for a while, or it is just beginning to adopt work-from-home policies, VPN monitoring — the ability…
Read More
May 21, 2020
Use Case: Detect and Respond to Malware Traffic with NDR
Posted by: Amy Tierney
As malicious actors continue to use a variety of techniques to evade detection, it’s paramount to protect your organization’s network activity. You need a solution that can detect and prevent malicious network activity. One solution is network detection and response…
Read More
May 21, 2020
Prevent Data Exfiltration with Network Traffic Analytics
When it comes to company data, you need to protect it at all costs. But it is hard to defend what you can’t see. This blog post will explore techniques threat actors commonly use to illegally copy an organization’s data,…
Read More
May 7, 2020
Deepen Your Remote Desktop Protocol Visibility with Log Sources
Posted by: Andrew Hollister
Remote desktop is a common feature in operating systems. It allows a user to connect to a computer in another location and interact with the desktop remotely. Microsoft implemented this capability via its Remote Desktop Protocol (RDP) for Windows desktop…
Read More
April 24, 2020
Lateral Movement and How to Detect It
Posted by: Justin Knapp
You may have heard of the concept of lateral movement within the context of security operations and possess a general idea of how threat actors leverage this tactic to gain access to your data. But what exactly is lateral movement?…
Read More
April 23, 2020
Monitor Zoom Security and Privacy Risks Using the LogRhythm NextGen SIEM
Posted by: Andrew Hollister
The mass migration to remote working in recent times has caused an increased focus on the security of remote collaboration tools. LogRhythm has found a variety of these tools in our customer base and has built collection methods and analytics…
Read More
April 21, 2020
Measure the Maturity of Your SOC in the LogRhythm NextGen SIEM Platform
If you are a security operations center (SOC) manager, reducing risk is your No. 1 priority. Even if you are not tracking any metrics today, you know how important metrics are for proving out the value, efficiency, and needs of…
Read More
April 20, 2020
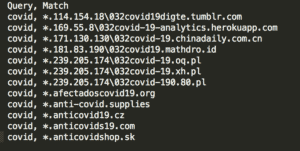
Detecting Young Domains with Palo Alto Networks and LogRhythm
Posted by: Brian Coulson
As the world continues dealing with a pandemic involving the coronavirus disease (COVID-19), malicious campaigns are well underway. For example, an opportunistic attacker will leverage a user’s sense of urgency and curiosity to prompt them to open a malicious email,…
Read More
April 9, 2020
Automate Amazon S3 Provisioning for Healthcare Compliance with SOAR
Cloud storage instances like Amazon Simple Storage Service, Amazon S3, have made it easier than ever before for healthcare professionals to access and share valuable patient data. While these advancements have improved customer care across providers, configuring access policies, provisioning…
Read More
April 8, 2020
Using Open-Source Intelligence to Detect Attacks Using Newly Created Domain Names
Posted by: LogRhythm Labs
When high-profile threats surface, they are often accompanied by a flurry of information sharing from security researchers and practitioners. The information they share can be delivered in a variety of formats. For example, following the recent malware activity surrounding the…
Read More
April 1, 2020
Detect Phishing Campaigns and Stolen Credentials with Custom AI Engine Rules
Posted by: LogRhythm Labs
Attackers have been known to take advantage of world events to increase their use of phishing, social engineering, malware delivery, and numerous other nefarious attacks. The recent COVID-19 pandemic is no exception as attackers are currently creating custom campaigns to…
Read More
March 31, 2020
Insights and Included Content to Protect Your Organization During Times of Crisis
Posted by: LogRhythm Labs
In times of crisis and uncertainty, nefarious threat actors have always preyed on the public and worked to exploit the situation for their benefit. The COVID-19 pandemic is no exception, as attackers have begun to masquerade and disguise common cyberattacks…
Read More
March 27, 2020