With the ever widening talent gap in cybersecurity and the expanding complexity of the cloud, organizations need an intuitive Security Information and Event Management platform (SIEM) that ensures seamless threat detection, investigation, and response. That is why we built our…
cloud security
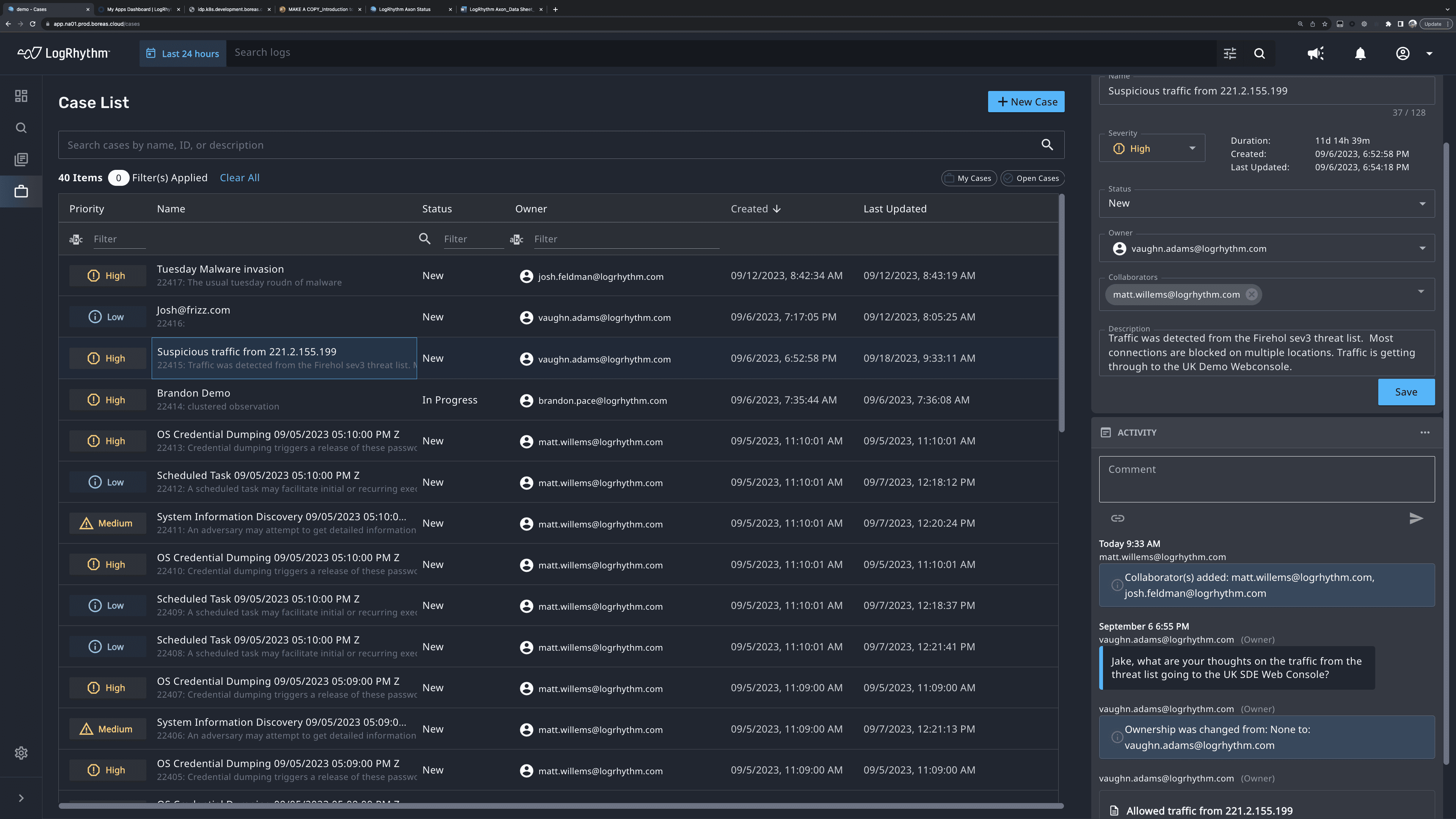
Cloud-Native SIEM Made Easy with LogRhythm Axon
Tags: cloud security | LogRhythm Axon | SIEM
Category: Product News
Type: Blog
LogRhythm Holds its First UK Cybersecurity Summit to Share Expertise and Insights About Elevating Cybersecurity Efficiency
Tags: cloud security | emea | SecureRhythm | security analytics | SOC | SOC Operations
Category: General
Type: Press Releases
Register now for the inaugural event to maximize the efficiency of your security operations and combat the ever-growing threat landscape London, UK, 6 June 2023 — LogRhythm, the company helping security teams stop breaches by turning disconnected data and signals into trustworthy…

Understanding Multi-Tenant Deployments Within the SIEM Platform
Tags: cloud security
Category: Customer Success | General
Type: Blog
The idea of multi-tenant infrastructure and deployments is not new in the cybersecurity landscape. For years, Cisco and Palo Alto firewalls and Citrix and F5 load balancers have supported the idea of a tenant-based deployment. The idea of supporting tenants…

An Overview of Cloud-Native Security Approaches
Tags: cloud security
Category: General
Type: Blog
Responsibility for cloud security is shared between the cloud service provider’s (CSP) security department and the corporate information security team. In order to ensure compliance, visibility, and control across the entire stack of applications, the cloud service providers and various…
