AlphaSights benefits from simplified approach to data gathering with user-friendly interface that gives organizations a unified overview of their security posture LogRhythm, the company helping security teams stop breaches by turning disconnected data and signals into trustworthy insights, has been selected by AlphaSights,…
SIEM

AlphaSights Chooses LogRhythm Axon to Protect Mission-Critical Data with Scalable Cloud-Native Threat Detection
Tags: Cybersecurity Visibility | LogRhythm Axon | partnership | SIEM | Threat Detection | Threat Hunting
Category: Customers | General
Type: Press Releases
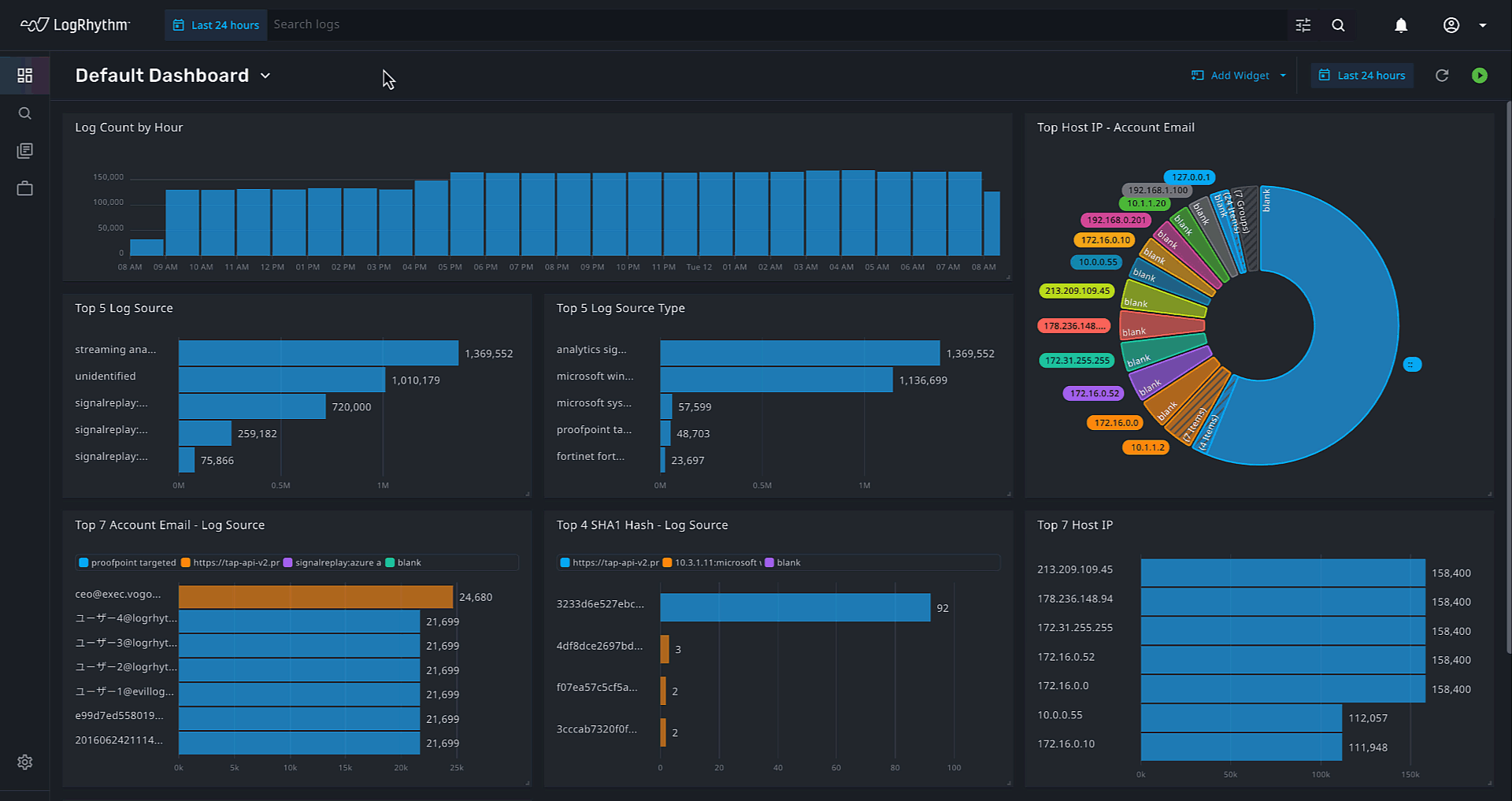
Why SaaS SIEM? A Comprehensive Guide for Businesses
Tags: SIEM
Category: Security Tips and Tricks | Thought Leadership
Type: Blog
Today’s businesses are increasingly reliant on technology, meaning the importance of airtight cybersecurity cannot be overstated. As organizations navigate the complexities of the modern digital ecosystem, maintaining the integrity of their systems has become more than just a “nice to…
LogRhythm SIEM 7.15: Leverage New Beats and Platform Improvements
Tags: SIEM
Category: General | Product News
Type: Blog
Getting data into your security information and event (SIEM) instance is crucial, and LogRhythm is highly focused on making it easy to do that. As part of our latest quarterly product release, LogRhythm SIEM version 7.15 builds on the innovation…
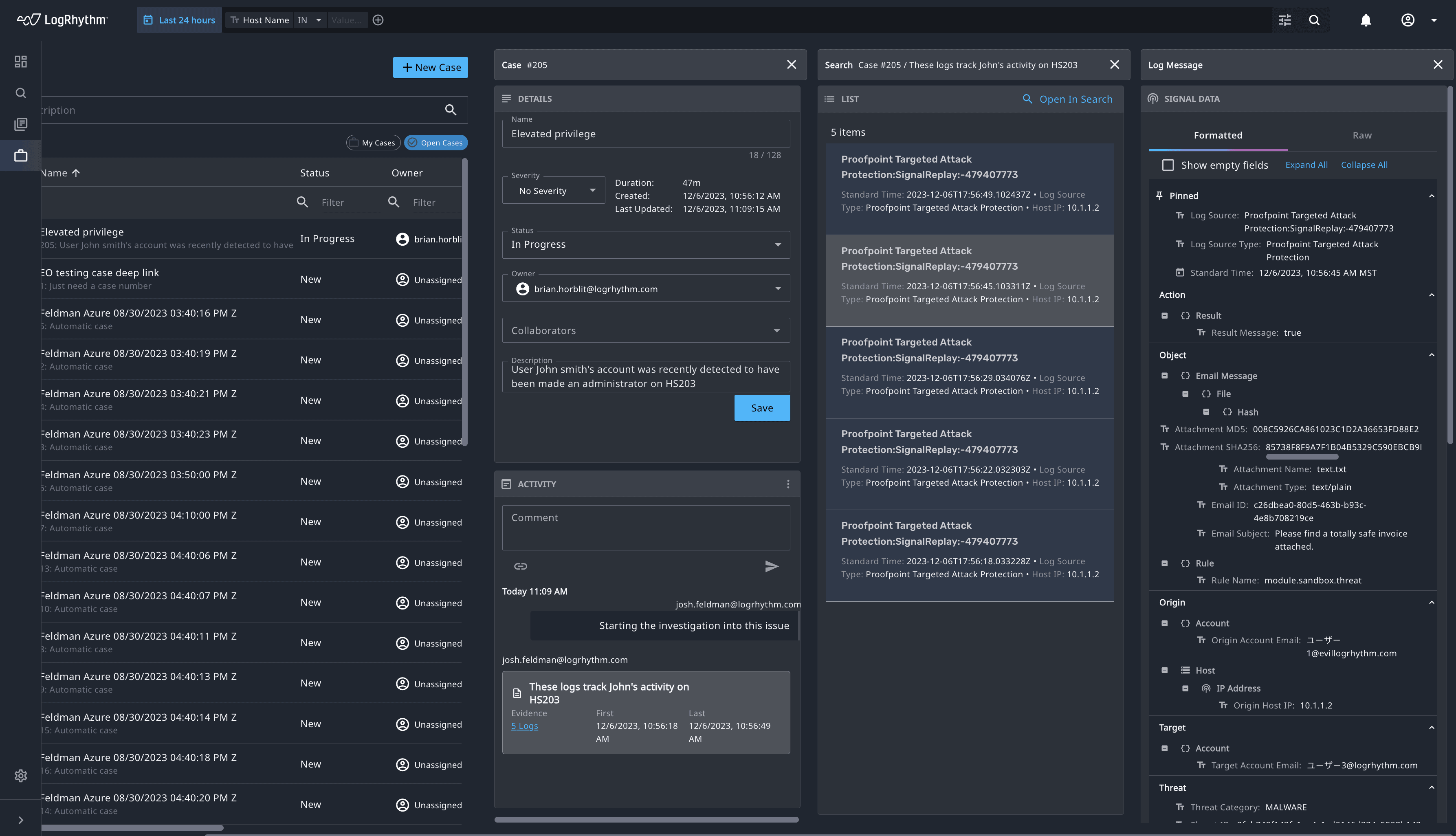
Attain Faster and More Accurate Threat Investigation with LogRhythm Axon’s Single Screen Investigation
Tags: LogRhythm Axon | SIEM | Threat Detection
Category: Product News
Type: Blog
When we built our cloud-native security information and event management (SIEM) platform, LogRhythm Axon, our goal was to make the product as efficient as possible to make the life of an analyst easier. With feature releases every two weeks, we’ve…
On-Prem SIEM vs. Cloud-Native SIEM: Which One Is Right for You?
Tags: SIEM
Category: Security Tips and Tricks
Type: Blog
Security information and event management (SIEM) solutions are essential for organizations of all sizes to monitor their environment for security threats. SIEM solutions gather and scrutinize security logs originating from diverse sources like firewalls, intrusion detection systems, and web servers.…
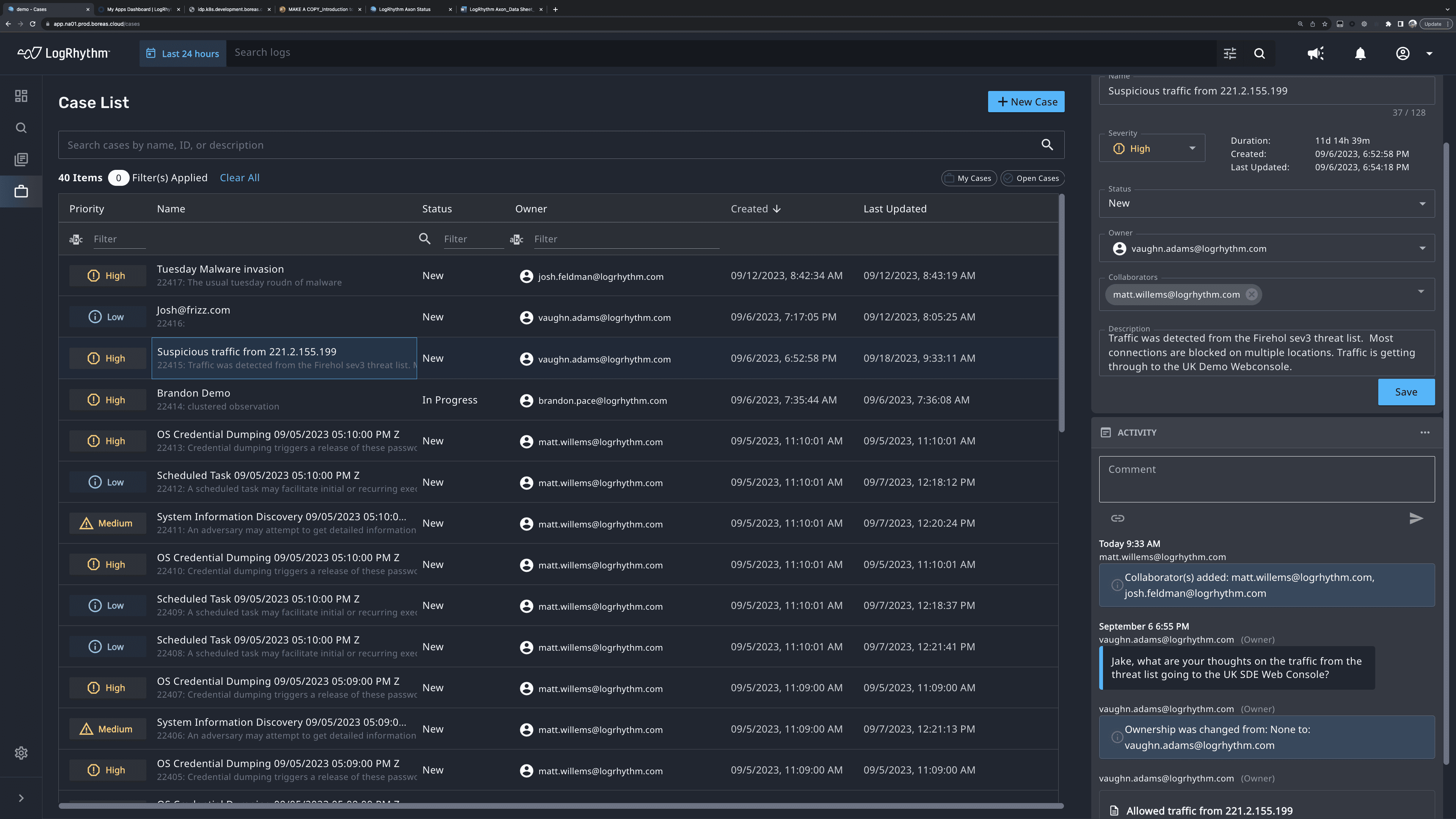
Cloud-Native SIEM Made Easy with LogRhythm Axon
Tags: cloud security | LogRhythm Axon | SIEM
Category: Product News
Type: Blog
With the ever widening talent gap in cybersecurity and the expanding complexity of the cloud, organizations need an intuitive Security Information and Event Management platform (SIEM) that ensures seamless threat detection, investigation, and response. That is why we built our…

What is SIEM? And How Does it Work?
Tags: SIEM
Category: Security Tips and Tricks
Type: Blog
What is SIEM? SIEM stands for security, information, and event management. SIEM tools aggregate log data, security alerts, and events into a centralized platform to provide real-time analysis for security monitoring. Security operation centers (SOCs) invest in SIEM software to…

Leverage Your SIEM as Part of Your Zero Trust Strategy
Tags: SIEM | Zero Trust
Category: Security Tips and Tricks
Type: Blog
Editor’s Note: This a partnered sponsored guest blog written by Avertium. Continuous monitoring is one of the most important facets of any Zero Trust architecture. The level of trust a system has in any user, application, or data flow may…
