Since we began our quarterly release cycle with LogRhythm NDR, we have been focusing on building a completely new user interface (UI) and introducing new features that help make the life of an analyst easier. Now that we’ve made significant…
LogRhythm NDR
Optimizing Threat Detection with LogRhythm NDR
Tags: LogRhythm NDR | network detection and response
Category: Product News
Type: Blog
Threat Hunting with LogRhythm NDR
Tags: LogRhythm NDR | Network Threat Detection | Threathunting
Category: Product News
Type: Blog
At LogRhythm, we’re constantly looking for ways to make the life of a security analyst easier and that is why we are always listening to our customers to prioritize the features that matter. With this LogRhythm NDR release, we enhanced…
Gain Greater Efficiency in Detecting Threats with LogRhythm NDR
Tags: LogRhythm NDR | Network Threat Detection
Category: Product News
Type: Blog
We’re always working to improve and expand our LogRhythm NDR functionality to better suit our customers’ requirements. Last quarter, we finished overhauling our User Interface (UI) to ensure that traffic anomalies that signal malicious activity surface quickly and that information…

LogRhythm présente ses dernières améliorations au Ready for IT 2023
Tags: Axon | français | france | LogRhythm Axon | LogRhythm NDR | LogRhythm SIEM
Category: General | Product News
Type: Blog
Q&R avec Vincent Peulvey, Directeur régional des ventes Europe pour LogRhythm Du 23 au 25 mai, Ready for IT, l’un des principaux événements informatiques en France, sera à nouveau organisé à Monaco. LogRhythm présentera ses dernières innovations en matière…
LogRhythm NDR Enables Analysts to Investigate Threats More Quickly with a New User Interface
Tags: LogRhythm NDR
Category: Product News
Type: Blog
It’s easy to get lost in the noise when trying to monitor, surface, and detect threats across network traffic. LogRhythm NDR identifies traffic anomalies that signal malicious activity such as command and control, lateral movement, data exfiltration, and malware activities.…
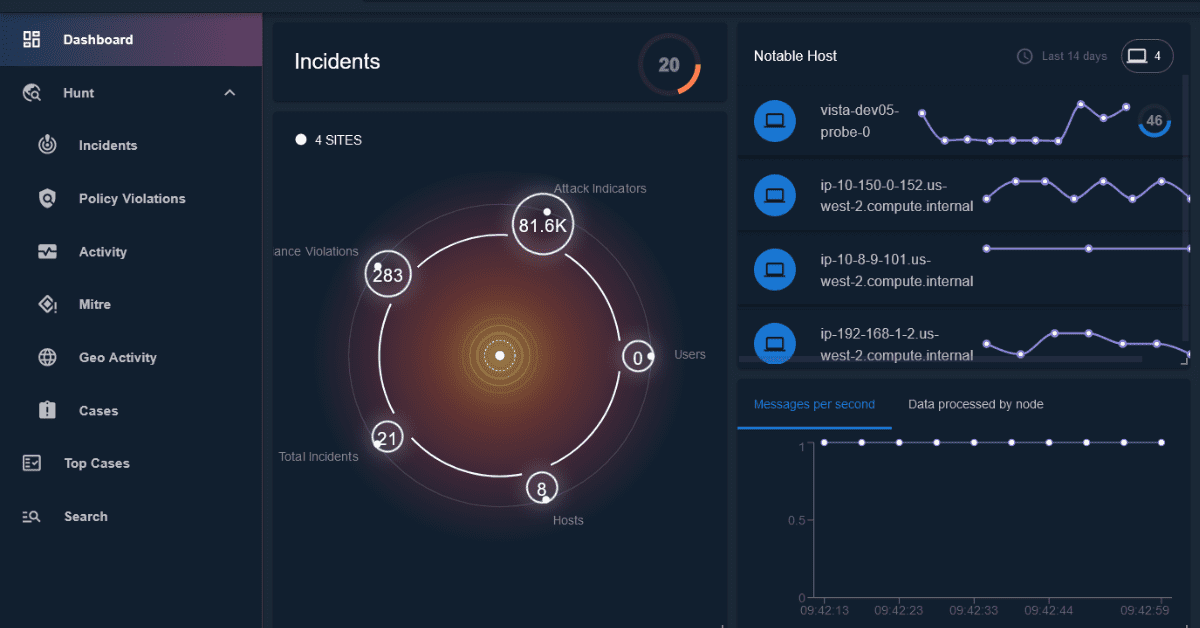
Increase Network Threat Detection Capabilities with LogRhythm NDR
Tags: LogRhythm NDR | Network Threat Detection
Category: Product News
Type: Blog
The amount of new network traffic that must be monitored across users and hosts in your environment make the job of an analyst difficult; new network threats appear every day and it is easy to get lost in all the…
