Detecting Log4Shell with MistNet NDR and NetMon
Posted by: Andrew Hollister
To help security teams stay on top of Log4Shell, LogRhythm Labs recently released information for detecting the vulnerability with the LogRhythm NextGen SIEM and MistNet NDR platforms. In this blog, we’ll continue to dive deeper as we uncover more detection…
Read More
December 20, 2021
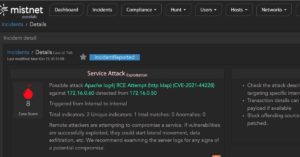
CVE-2021-44228 Log4Shell Detection
Posted by: Brian Coulson
News is spreading fast about the recent CVE-2021-44228 Log4Shell vulnerability. SANS noted that the first exploit seen by Cloudflare was 4:36 GMT on December 1st. This was eight days prior to the Proof of Concept (PoC) exploit published on GitHub on December 9th. SANS saw first attempts at 12:32 PM on December 9th. In…
Read More
December 14, 2021
AWS Defense Evasion and Centralized Multi-Account Logging
Posted by: Ashok Chokalingam
Amazon Web Services (AWS) is a widely known cloud service provider, but organizations that use AWS products face unique cybersecurity challenges. Leveraging techniques that reduce risk against new cloud security challenges will help you stay ahead of threats across your…
Read More
December 13, 2021
A Look Back at Which Predictions Came True in 2021
In 2021, cybercriminals took aim at critical infrastructure with ransomware attacks on Colonial Pipeline, JBS and others. They also continued to find new ways to exploit employees working remotely, those seeking information on COVID-19 vaccines, and improperly secured APIs. In…
Read More
December 8, 2021
Understanding Multi-Tenant Deployments Within the SIEM Platform
Posted by: Patrick Greenwood
The idea of multi-tenant infrastructure and deployments is not new in the cybersecurity landscape. For years, Cisco and Palo Alto firewalls and Citrix and F5 load balancers have supported the idea of a tenant-based deployment. The idea of supporting tenants…
Read More
December 1, 2021
Conducting an Information Security Risk Assessment Successfully
Posted by: Kyle Dimitt
Management of risk is not a simple undertaking but is essential for enterprise governance and decision making. Whether a company is adopting an enterprise risk management framework (e.g., ISO 31000, COSO, or NIST RMF) or building out an information security…
Read More
November 22, 2021