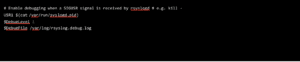
Troubleshooting Delayed Syslog Messages
Posted by: Jeffrey Braucher
Anytime our team has been involved in a system migration, there has always been someone who claimed the new system was slower than the old one. In a recent case, the team had just completed the migration of a computing…
Read More
November 16, 2018
Looking Back at LogRhythm Labs’ 2018 Predictions for Security – How Did We Do?
About this time every year, the LogRhythm Labs team watches bird flights, performs divination rituals, and contemplates what might happen in the world of information security in the coming year. Last year, we started a new tradition of examining our…
Read More
November 16, 2018
Your Questions About New U.S. State-Level Data Protection Laws Answered
This year, at least 11 U.S. states passed new or updated laws, with several specifically focused on data breach notification and data protection. From Alabama implementing its first data breach notification law to California passing its Consumer Privacy Act and…
Read More
November 13, 2018
Insight into User Behavior Using LogRhythm CloudAI: Part I
Posted by: Phil Villella
As Chief Scientist and de facto Technical Product Manager for LogRhythm’s Data Science team, I continuously evaluate the effectiveness of LogRhythm’s user and entity behavior analytics (UEBA) functionality to surface user activity that may be of interest to a security…
Read More
November 12, 2018
Protect Yourself Against User-Based Threats with UEBA
Posted by: Amy Tierney
Understanding Suspicious User Types in Your Organization Whether unintentional or malicious in nature, user-based threats can have devastating consequences on your organization. While your focus may be on protecting your organization from outside incidents, you also need to guard yourself…
Read More
November 5, 2018
Creating and Managing Playbooks with LogRhythm APIs
New to LogRhythm 7.4: Playbooks Feature Set Standard procedures have been a cornerstone of security best practice since their invention. You may call them runbooks, standing procedures, checklists, or playbooks. Either way, you likely have one or more collections of…
Read More
October 29, 2018