Take the First Steps Toward a Zero-Trust Model with Okta Automation
Managing multiple accounts across various cloud and on-premise infrastructures centrally is a challenge for most security operations centers. To address this ever-increasing need, the LogRhythm Office of the CISO recently implemented Okta. Okta enables a nearly seamless management process for…
Read More
May 21, 2018
Catch the Next WannaCry or NotPetya Ransomware Attack Before Damage Occurs
Posted by: LogRhythm Labs
Contributors to this blog include Nathaniel “Q” Quist and Sam Straka. On April 14, 2017, Shadow Brokers released a set of previously classified exploit tools developed by the National Security Agency. Within this cache of exploits, perhaps the most notorious…
Read More
May 14, 2018
Augmenting Your Cyber Resiliency Strategy with NextGen SIEM
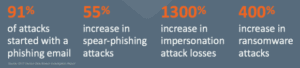
The cybersecurity challenge centers around a fundamentally simple concept: Email keeps businesses running and stores critically important corporate and personal data, but email is also the top vector for cyberattacks. The cyberattack trends and numbers speak volumes: Figure 1: Cyberattack…
Read More
May 2, 2018
Organizations Are Failing at Timely Detection of Threats
In today’s security space, we’re all too familiar with the challenges presented by industry-wide shortages in talent, budget, and dedicated security infrastructure. Many insights from the LogRhythm 2018 Cybersecurity: Perceptions & Practices benchmark survey confirm this common understanding, yet one…
Read More
April 24, 2018
Take a Deep Dive into PlugX Malware
In June 2017, Palo Alto’s Unit 42 Threat Research team published an excellent blog post on a newly detected version of the PlugX malware family, also known as “Korplug.” Interested to find out more about this new variant, I started…
Read More
April 18, 2018
Defending Your Organization with User and Entity Behavior Analytics (UEBA)
User and entity-centric threats are a growing concern for security teams. In fact, according to the 2017 Verizon Breach Study, 69 percent of organizations report a recent insider data exfiltration attempt. Compounding matters, 91 percent of firms report inadequate insider…
Read More
April 12, 2018