This blog is co-authored by LogRhythm Labs Incident Response Engineer Nathaniel “Q” Quist and Threat Intelligence Engineer Matt Willems.
Ransomware is currently one of the most widespread and highest-publicized threats on the Internet. Over the last few years, we’ve seen a marked increase in the use of ransomware tools like CryptoLocker, CryptoWall, TeslaCrypt and more recently Locky.
Security experts predict 2016 will follow this trend as more cybercriminals begin offering ransomware-as-a-service options to their list of nefarious wares.
As a SIEM provider, we assist our clients (and the industry in general) to detect indicators of compromise (IOCs) and prevent malicious file encryption events as quickly as possible.
In researching infection characteristics derived from several ransomware binaries, there are IOCs that LogRhythm is capable of identifying and triggering an early response countermeasure to assist in the isolation of infected hosts. While catching ransomware before it is able to infect and begin encryption on the target system is preferred, having these detection signatures available allows for the option of countermeasures, preventing the loss of all sensitive files due to encryption.
To aid in this task LogRhythm has several tools at its disposal. The use of process, file, and registry monitoring for endpoints—as well as industry threat feed integrations such as abuse.ch.
abuse.ch introduced Ransomware Tracker to maintain a list of IPs, domains, and URLs known to host or facilitate ransomware. The tracker provides indicators for several different malware variants including: Cryptowall, TeslaCrypt, TorrentLocker, PadCrypt, Locky, CTB-Locker and FAKBEN; with the possibility of many more being added.
Pulling Data into LogRhythm with PowerShell
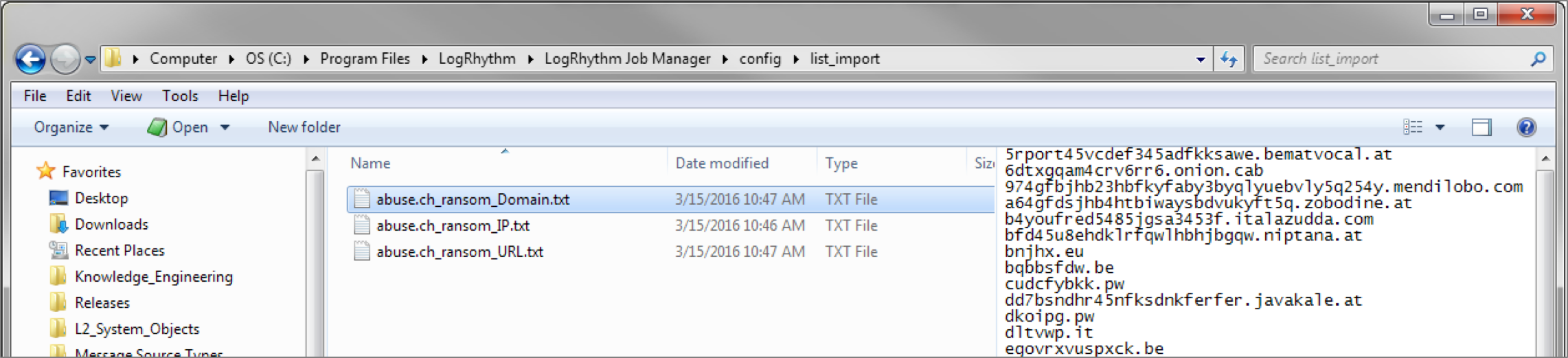
To get this data into LogRhythm, Matt wrote a PowerShell script that will pull down each of the three Ransomware Tracker feeds (IPs, domains and URLs) into separate text files that can be consumed into LogRhythm as Lists.
The PowerShell Execution Policy needs to be set to Unrestricted for this script to work. Run “Get-ExecutionPolicy” from a PowerShell prompt to check the current setting.
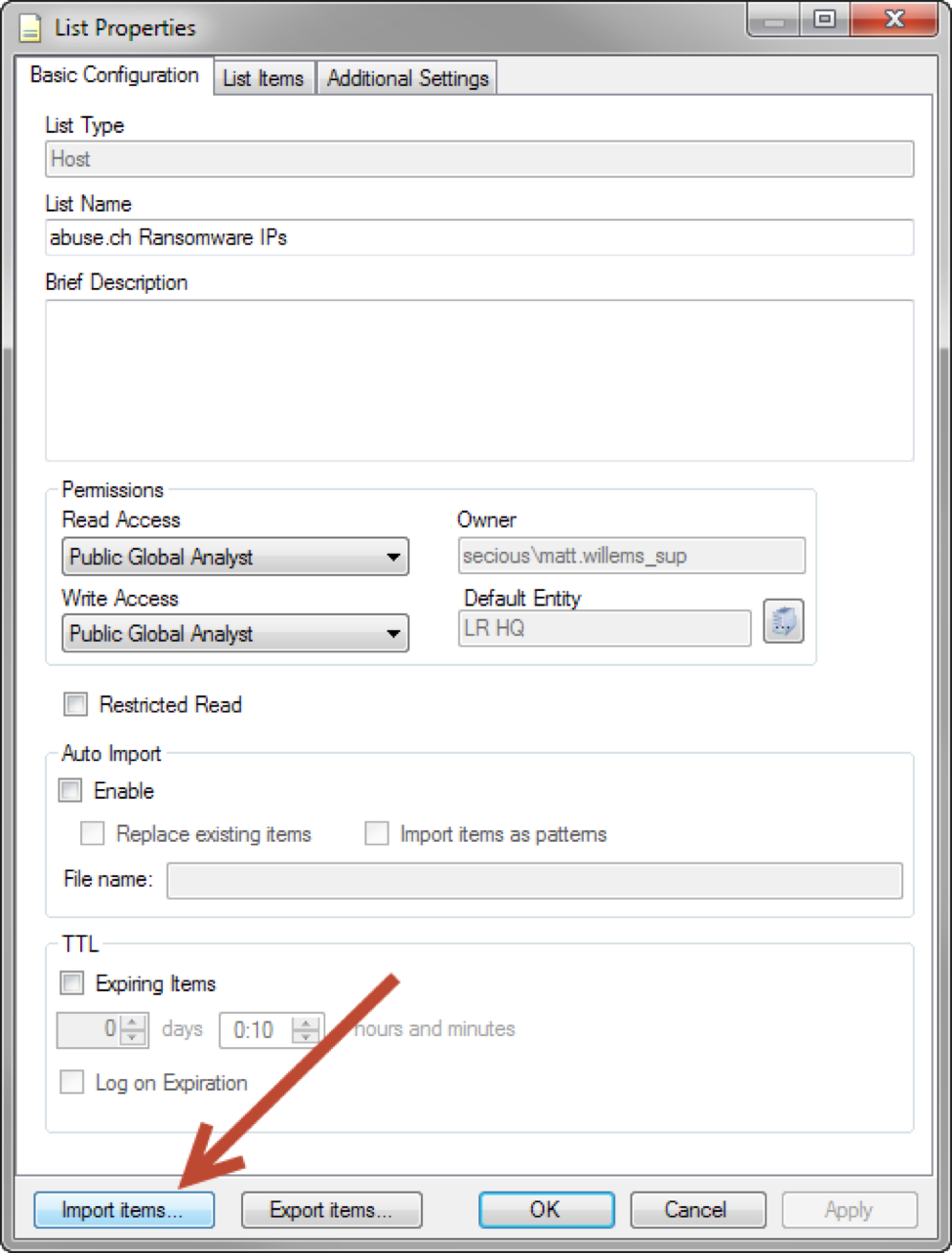
This script can be run manually and the output data can then be imported into the List Manager.
Click on images to expand
You can also run this script as a scheduled task on your LogRhythm Platform Manager or XM Appliance. The three text files will be output to the Job Manager’s list_import directory.
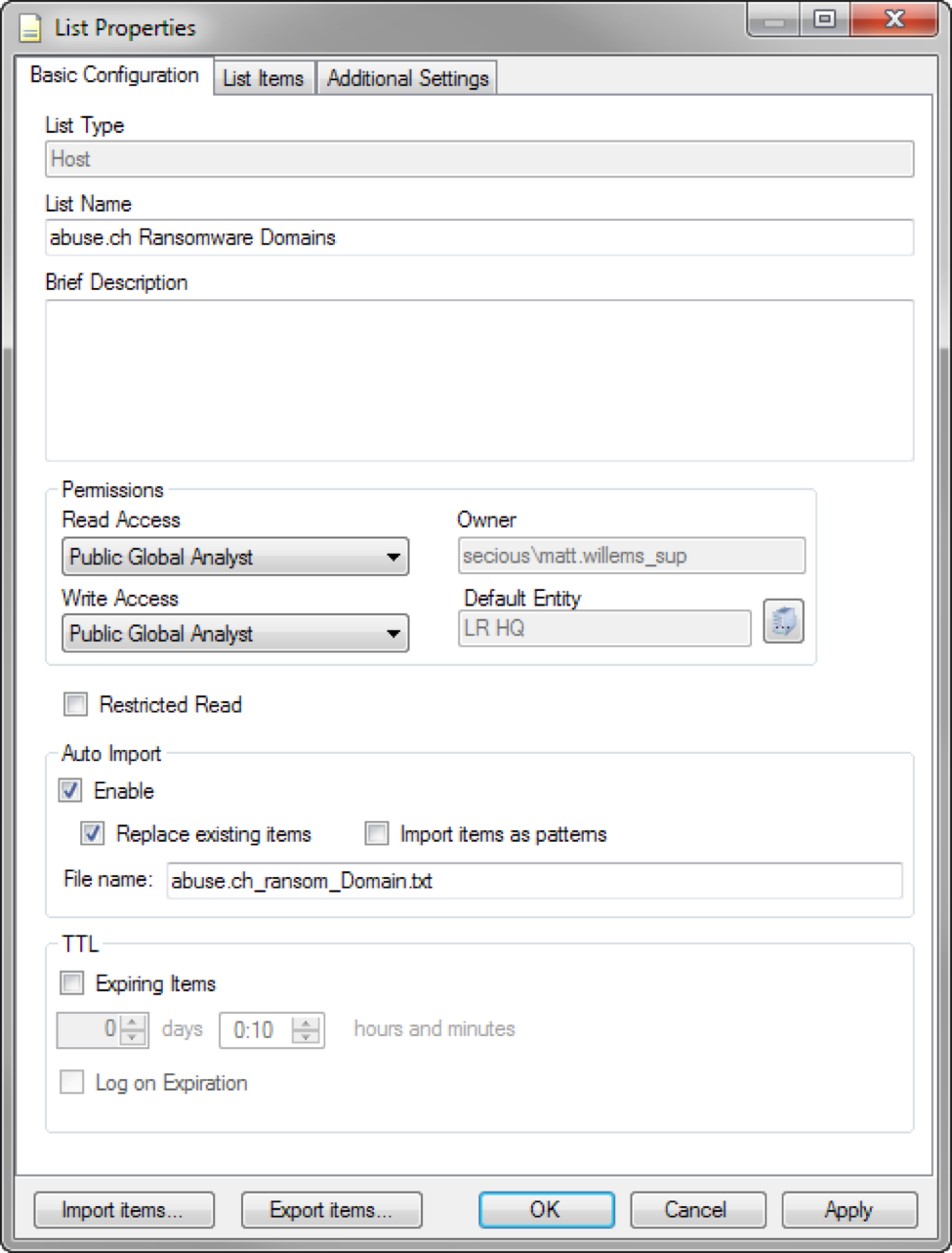
Then the LogRhythm List can be configured to automatically import the files when they appear. You should also enable the “Replace existing items” option to ensure any items removed from the tracker are also removed from the LogRhythm List.
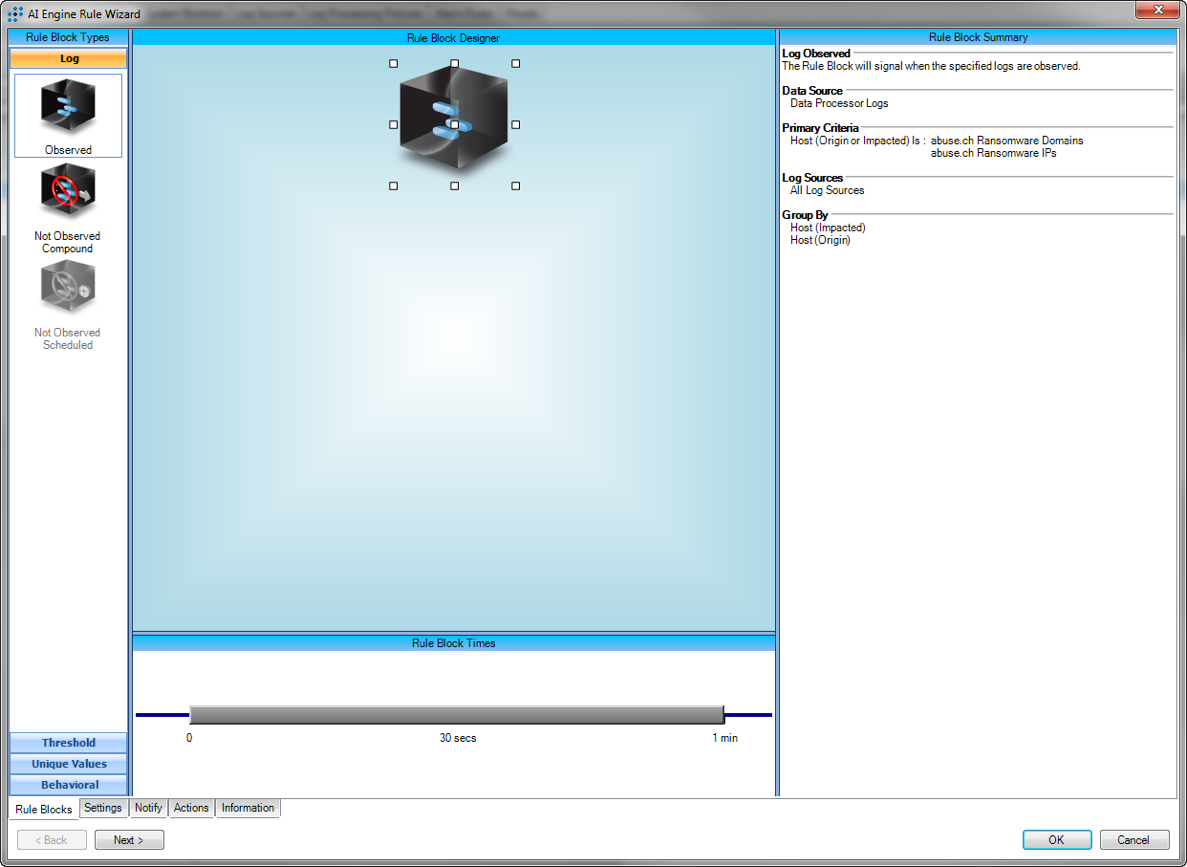
Once you have the lists created and data imported, they can be used for investigations and Web console searches, as well as AI Engine rules to detect communication with these hosts or hits on the URLs.
System Detection
Having the industry threat lists available for detection of potential drive-by attacks or listening for the callout from a successfully targeted phish is very important to the early detection. However, LogRhythm also has the capability to detect system specific infection signatures originating from ransomware.
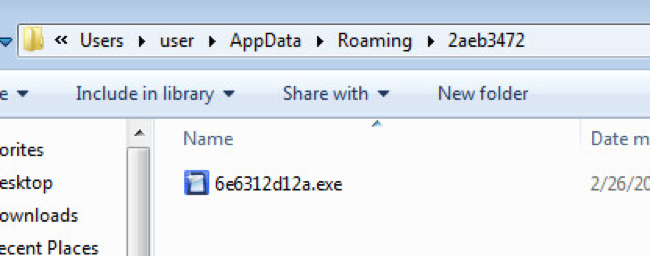
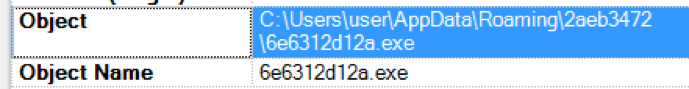
When ransomware is first exploited through drive-by attacks or from targeted spearphishing campaigns, the malware is dropped within a Temp directory on the Windows systems.
Within several of the most common ransomware variants, this is typically within the %AppData% or %Temp% directories.
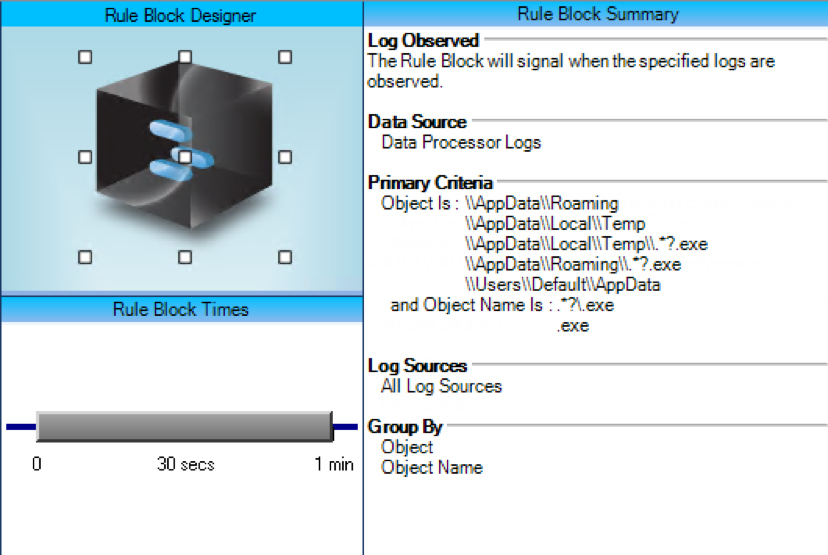
While this is not abnormal behavior for these directories to be the source of a launched executables (.exe), ransomware consistently uses this tactic. LogRhythm can use this tactic as a trigger.
Malware Dropper:
LogRhythm Detection of the Log:
AI Engine Rule Block:
Alarm Triggers:
Additionally, ransomware will start and stop a specific list of services depending upon the ransomware variant. CryptoWall and Locker both affect Volume Shadow Copy services as well as Windows Defender in varying degrees.
Changes to these services can also be detected by LogRhythm, adding additional validity to ransomware identification.
Finally, ransomware’s primary focus is upon the acquisition and encryption of specific file types. Typically the targeted file types are: pdfs, image files, text files, Word documents, and many more. When these file types change their extensions or their file names in bulk, this is again another trigger LogRhythm can use in the detection of ransomware.
CryptoLocker Example of an Encrypted File:
As each of these unique IOCs take place, LogRhythm is uniquely capable of seeing cradle to grave ransomware infections. It can detect initial callout or callback connections to any IP, URL, or domain listed through the abuse.ch Ransomware Feed.
LogRhythm can then also detect the unique signatures on compromised endpoints caused by the malware executable, the files it modifies, and the registry entries that may change. These configurations can be added to a current deployment to increase the platforms identification awareness.
More on Ransomware
To learn more, watch our on-demand webcast “Protecting Your Business from the Ransomware Threat.” In this webinar, James Carder and Ryan Sommers discuss the early indicators of ransomware, automated defenses you can put in place to stop the attack, and the steps you must follow to make a mole hill out of a possible mountain.