Clear Next-Gen Leadership
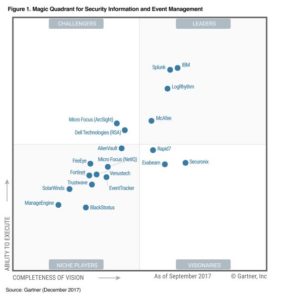
Gartner recently released its annual Magic Quadrant for Security Information and Event Management (SIEM) research report, an assessment of, arguably, the most strategic part of the enterprise security operations stack. Driven by an increasingly complex and challenging threat landscape, this…
Read More
December 19, 2017
One Compliance Module to Rule Them All: Consolidated Compliance Framework
Posted by: LogRhythm Labs
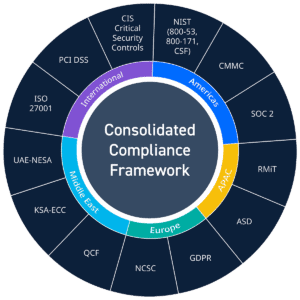
The continued growth, proliferation, and awareness of cybersecurity as a necessary focus for all companies has helped revolutionize the global compliance landscape. A growing number of old regulations have been re-factored to include more stringent cybersecurity controls. New regulations are…
Read More
December 13, 2017
Cybersecurity Readiness in Asia-Pacific – Five Areas That Leave Enterprises Vulnerable
The threat landscape is growing every day, and so is the risk of suffering a demanding data breach. While a dedicated security strategy can keep organizations out of headlines, many are still plagued by disjointed response workflows and manual processes…
Read More
December 11, 2017
Information Security Predictions for 2017 – How Did We Do?
Posted by: LogRhythm Labs
Around this time every year, we dust off our crystal ball, pull out the casting runes, and ruminate over what might happen in the world of Information Security in the year to come. While we are gathering information for our…
Read More
December 6, 2017
Enrich Your SIEM with Real-Time Threat Intelligence
Posted by: Chris Pace
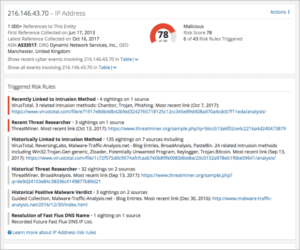
Just as hackers often reconnoiter their intended targets to gain insight into an organization’s defenses, companies can monitor the threat landscape to see who is prowling around just outside its gates. Organizations need more than just internal network data to…
Read More
December 5, 2017
A CISO’s Perspective: Sue Lapierre
As the Vice President, Information Security Officer of Prologis, Sue Lapierre is responsible for developing and maintaining information security operations for the global industrial real estate company. She also oversees third-party vendor risk management. Lapierre’s great responsibility is matched by…
Read More
November 27, 2017