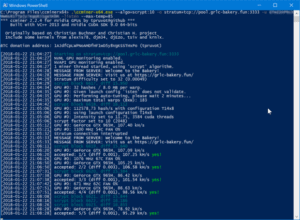
Insider Threat Use Case: Detecting and Stopping Cryptojacking
Cryptocurrency is a hot topic right now, and even though its price is drastically falling across the board, this incredible technology will have lasting impacts on the world for years to come. Though a majority of the focus on cryptocurrencies…
Read More
April 5, 2018
Do You Have Real-Time Visibility into Your Epic EHR Instance?
In 2017, there were 477 reported health care breaches in the U.S. affecting 5.6 million patient records. Seventy-one percent of these breaches were due to hacking and IT incidents. In recent years, privacy breaches have proven to be a major…
Read More
March 20, 2018
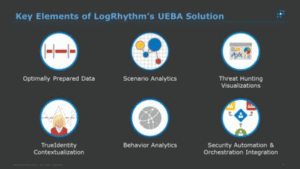
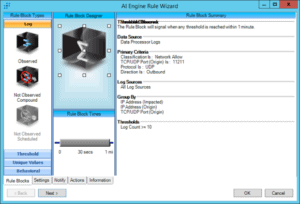
SANS Puts LogRhythm’s UEBA Capabilities to the Test
The threat landscape grows increasingly unpredictable and dangerous as threat actors expand in number and their attacks increase in sophistication. From motivated insiders to well-armed nation-states, threats to your organization are increasing in number and difficulty of detection. When threats…
Read More
March 14, 2018
Detecting Memcached DDoS Attacks Targeting GitHub
Posted by: LogRhythm Labs
Contributors to this blog include Nathaniel “Q” Quist and Dan Kaiser. On February 28 and March 5, 2018, Memcached DDoS attacks targeted GitHub. LogRhythm Labs performed an investigation into the cause, effect, and outcome of these attacks. The following will…
Read More
March 8, 2018
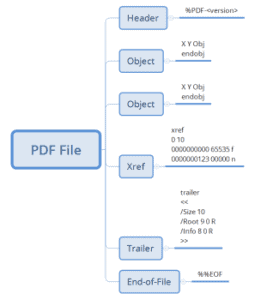
Detecting Potentially Malicious Javascript Embedded Within a PDF File Using LogRhythm Netmon
Various blog posts have been written by LogRhythm’s very own resident LogRhythm NetMon expert Rob McGovern regarding the numerous benefits of using Deep Packet Analytics within NetMon. If you’re not already familiar with deep packet analytics (DPA) rules, Rob’s post…
Read More
February 27, 2018
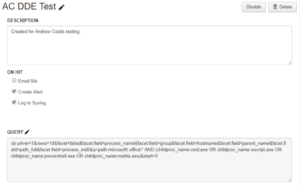
Dynamic Data Exchange (DDE): Detection and Response, Part 2
Part one of this blog series discussed what Dynamic Data Exchange (DDE) is, what an attack may look like, and steps for mitigation. In Part 2, I’ll cover how LogRhythm and Carbon Black can work together to help detect a…
Read More
February 20, 2018