Dynamic Data Exchange (DDE): Detection and Response, Part 1
Malicious actors have begun using Microsoft’s Dynamic Data Exchange (DDE) mechanism to deliver payloads via Microsoft Office documents instead of the traditional embedded macros or VBA code. Specially crafted Microsoft Office documents sent via email can be used to carry…
Read More
February 12, 2018
Integrating Threat Intelligence to Keep up with Today’s Cyberthreats
Today’s cyberthreats are advancing in both methodology and frequency. To keep pace with evolving cyberattacks, you need to make use of all of the information and intelligence available. Threat intelligence can help you stay one step ahead of cyberthreats by…
Read More
February 6, 2018
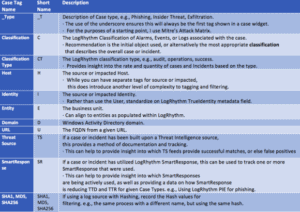
Optimize Platform Performance with Case Management
LogRhythm’s built-in Case Management provides end-to-end threat lifecycle management, but in order to maximize efficiency and provide key performance indicators (KPIs), a case tagging schema needs to be chosen and implemented. Without a standardized schema, WebUI users may make up…
Read More
January 29, 2018
IT Security in an OT World
Before we had the Internet of Things (IoT), ubiquitous wireless access, high speed data pipes, or even core internet protocols including HTTP and TCP, we had industrial automation. Operational Technology (OT) is the latest umbrella term to encompass functionalities such…
Read More
January 24, 2018
Security Perspective: The CISO of Colorado
As the Chief Information Security Officer (CISO) for the state of Colorado, Debbi Blyth is responsible for protecting Colorado residents’ information. This information is spread across 17 different agencies—ranging from corrections and public safety records to health information—and is highly…
Read More
January 22, 2018
Customizing SmartResponse to Streamline Threat Hunting
Mature organizations often have an abundance of sources producing contextual data. LogRhythm SmartResponse is a great tool to help automate this influx of data, as well as take enforcement action on findings. When launched from the search interface, however, SmartResponse…
Read More
January 18, 2018