Introducing Student LogWars — A LogRhythm EDU Partnership Program
Posted by: Jordan Kent
In the cybersecurity industry, one of the biggest problems facing recent graduates and employers is the lack of real-world experience from education. To address these challenges, LogRhythm is excited to announce a new facet of our EDU Partnership Program, Student…
Read More
June 15, 2021
LogRhythm Champions Profile: Steve Flannery
The LogRhythm Champions Network is an exclusive community of LogRhythm’s most passionate and strategic customers. This elite group of customer leaders in the InfoSec community are experts in all things LogRhythm. The LogRhythm Champions Network works to recognize these leaders for…
Read More
June 15, 2021
LogRhythm Champions Profile: Seth Shestack
The LogRhythm Champions Network is an exclusive community of LogRhythm’s most passionate and strategic customers. This elite group of customer leaders in the InfoSec community are experts in all things LogRhythm. The LogRhythm Champions Network works to recognize these leaders for…
Read More
May 25, 2021
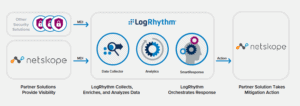
Automate URL and File Blacklisting with Netskope and LogRhythm
While many organizations focus on outside threats, network security shouldn’t be neglected. Having greater visibility into the websites people are searching and the files they are downloading in your network should be a priority. To strengthen your network visibility, LogRhythm…
Read More
April 20, 2021
LogRhythm Champions Profile: Kevin Merolla
The LogRhythm Champions Network is an exclusive community of LogRhythm’s most passionate and strategic customers. This elite group of customers leaders in the InfoSec community and are experts in all things LogRhythm. The LogRhythm Champions Network works to recognize these…
Read More
April 9, 2021
How to Audit and Test for Sudo’s CVE-2021-3156 with LogRhythm
Posted by: Brian Coulson
TL/DR Qualys has reported that Sudo, before 1.9.4p2, has a heap-based buffer overflow vulnerability that allows privileged escalation to root via “sudoedit -s” and a command-line argument that ends with a single backslash character. Detecting a successful exploit of the…
Read More
February 23, 2021
Code42 and LogRhythm Partner to Protect Against Insider Threats
As remote work has become the norm for many enterprises, organizations are struggling with the troubling reality of rising insider threats. Whether the results are from careless or negligent employees or malicious insiders, it’s crucial to arm your organization with…
Read More
January 15, 2021
LogRhythm and Getronics Partner for Comprehensive New SOC Solution
LogRhythm and Getronics announced a further commitment to the partnership that sees LogRhythm’s industry leading SIEM solution integrated into Getronics’ managed security offerings globally. The formal partnership allows the companies to tightly integrate LogRhythm’s SIEM solution – winner of SC Awards Europe 2020, Best SIEM Solution – with Getronics data processing and storage, located in the EU and meeting all GDPR regulatory requirements.
Read More
December 15, 2020
Avertium Enhances LogRhythm Expertise with Acquisition of 1440 Security
Avertium, an industry-leading managed security and strategic consulting partner to mid-to-large enterprises, today announced the acquisition of 1440 Security, a nationally recognized managed security service provider with a Colorado-based 24/7 security operations center…Named to the MSSP Alert Top 200 MSSPs list in 2019, 1440 Security has built a loyal customer base and a reputation for excellence in managed security, particularly in the deployment, configuration, and management of the LogRhythm NextGen SIEM Platform.
Read More
September 16, 2020
LogRhythm Power Users Share their Use Cases
LogRhythm’s 4,000 customers are finding success every day while using our platform. We asked some of LogRhythm’s best power users how they solved the specific security problems that were plaguing their teams using the LogRhythm NextGen SIEM Platform. Following are…
Read More
August 28, 2020
LogRhythm Receives Gartner Peer Insights’ SIEM Customers’ Choice Designation for the 4th Year in a Row
LogRhythm recently received Gartner Peer Insights’ SIEM Customers’ Choice designation for the fourth year in a row. We feel this is an honorable distinction, and one we acknowledge with gratitude. Ultimately, without our loyal customers, and our hard-working staff and…
Read More
August 3, 2020
How Case Management Tags Improve Efficiency, Reporting, and SOC Metrics
Posted by: Daniel Dallmann
Daniel Dallmann, Senior Information Security Engineer, is a guest blogger from Payworks and a valued LogRhythm contributor. Dan was on the SOAR Customer Panel at LogRhythm’s third annual user conference, RhythmWorld, and was generous enough to share some of the…
Read More
October 31, 2019
Your Best Work Hack: LogRhythm’s Tips & Tricks
Keeping your organization protected from threats is no easy task. It’s crucial to get the most out of your security platform. But how do you stay on top of all of your platform’s features and functionalities? Where can you find…
Read More
November 20, 2018
Gearing Up for RhythmWorld 2018
Here at LogRhythm, we’ve been planning, preparing, and practicing for RhythmWorld, our second annual global user conference. We’ve invited several hundred of our friends and customers to join us at Denver’s historic Brown Palace Hotel this week for two packed…
Read More
October 8, 2018
Why Do Our Customers Choose LogRhythm? IT Central Station Dives In
Posted by: Danielle Felder
Over the last year, the IT Central Station team reached out to LogRhythm customers with one goal: to find out what made them choose LogRhythm as their SIEM solution. As we looked into this customer feedback, we discovered that many…
Read More
September 5, 2018
First Financial Bank Unifies Threat Data and Streamlines Response
LogRhythm Enables Comprehensive Visibility and Enhanced Incident Workflows When Michael Cole took on his new role as Chief Information Security Officer at First Financial Bank (NASDAQ:FFIN), he inherited a fragmented security operations program that provided a limited visibility into the…
Read More
August 15, 2017
Northampton County Improves Visibility and Automation with LogRhythm
LogRhythm Enhances Efficiency by Streamlining Security Operations Bob Mace, senior information security analyst, leads a small IT team to manage and secure Northampton County’s IT infrastructure. As the team faced mounting challenges and time-consuming manual processes, Mace turned to LogRhythm.…
Read More
July 20, 2017
Alliant Credit Union Automates Fraud Detection
The Challenge Manual Analysis Resulting in Decreased Productivity and Visibility Bank fraud reached an all-time high in 2015. To combat this threat, Alliant Credit Union employs a team of fraud specialists that scrutinizes detailed reports in search of fraudulent financial…
Read More
January 10, 2017