Defending Your Organization with User and Entity Behavior Analytics (UEBA)
User and entity-centric threats are a growing concern for security teams. In fact, according to the 2017 Verizon Breach Study, 69 percent of organizations report a recent insider data exfiltration attempt. Compounding matters, 91 percent of firms report inadequate insider…
Read MoreApril 12, 2018
Do You Have Real-Time Visibility into Your Epic EHR Instance?
In 2017, there were 477 reported health care breaches in the U.S. affecting 5.6 million patient records. Seventy-one percent of these breaches were due to hacking and IT incidents. In recent years, privacy breaches have proven to be a major…
Read MoreMarch 20, 2018
SANS Puts LogRhythm’s UEBA Capabilities to the Test
The threat landscape grows increasingly unpredictable and dangerous as threat actors expand in number and their attacks increase in sophistication. From motivated insiders to well-armed nation-states, threats to your organization are increasing in number and difficulty of detection. When threats…
Read MoreMarch 14, 2018
Journey to the AI-Enabled SOC: Advancing the Science of Threat Detection
Posted by: Chris Petersen
Artificial Intelligence (AI)-enabled analytics offer great promise for furthering the science of advanced threat detection. While it is difficult to imagine AI superseding the cognitive and instinctive power of talented security analysts and threat hunters in the immediate future, AI…
Read MoreJanuary 8, 2018
LogRhythm and DevOps: Bringing It All Together
There has been a recent uptick in corporate IT Development Operations (DevOps). Many tools, books, and experts sing the praises of the DevOps methodology. It can be difficult to fully recognize exactly what DevOps is and how it works, but…
Read MoreDecember 28, 2017
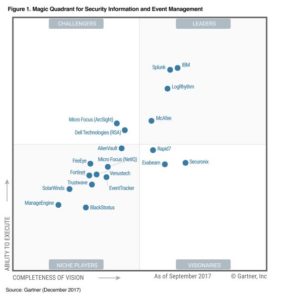
Clear Next-Gen Leadership
Gartner recently released its annual Magic Quadrant for Security Information and Event Management (SIEM) research report, an assessment of, arguably, the most strategic part of the enterprise security operations stack. Driven by an increasingly complex and challenging threat landscape, this…
Read MoreDecember 19, 2017
Journey to the AI-Enabled SOC: Unlocking Potential with Data
Posted by: Chris Petersen
The Importance of Data In my previous Journey to the AI-Enabled SOC blog, I mentioned the three key ingredients required to unlock the potential of artificial intelligence (AI) towards improved threat detection and transforming how enterprises realize threat lifecycle management:…
Read MoreNovember 16, 2017
Phishing Intelligence Engine (PIE): Open-Source Release
We are pleased to announce the release of the LogRhythm Phishing Intelligence Engine (PIE), an integrated app with LogRhythm’s NextGen SIEM Platform. What is Phishing Intelligence Engine (PIE)? LogRhythm’s PIE can help streamline and automate the entire process of tracking,…
Read MoreNovember 8, 2017
CloudAI for User and Entity Based Analytics (UEBA)
Earlier this month, LogRhythm proudly released LogRhythm CloudAI—the most recent chapter in our User and Entity Behavior Analytics (UEBA) story. LogRhythm CloudAI uses machine learning to apply behavioral analytics to user behavior. By modeling user behavior to uncover security relevant…
Read MoreOctober 31, 2017
Journey to the AI-Enabled SOC: Genesis
Posted by: Chris Petersen
The LogRhythm Journey Begins Nearly 15 years ago, Phil Villella and I set out to change the definition of security information and event monitoring (SIEM). Our motivation originated in two fundamental beliefs: First, U.S. companies and agencies were running blind…
Read MoreOctober 10, 2017
LogRhythm Enhances Cisco’s Security Hardware and Software Portfolio
Partnership Spotlight: Cisco Securing your organization is difficult work. Faced with an endless stream of data and disparate security tools, it’s easy to get lost in the noise. LogRhythm and Cisco can help you can sort through the noise and…
Read MoreSeptember 13, 2017
SANS Institute Validates LogRhythm’s Ability to Scale Above 300K MPS
The Importance of Security Analytics for Threat Prevention Many organizations are beginning to realize that they must use security analytics to recognize threats that bypass their preventative technologies. Unfortunately, despite the promise of a silver bullet, security analytics alone is…
Read MoreJune 7, 2017
Trifecta: LogRhythm Recognized by Forrester, SANS, and SC Labs
In just the last few months, LogRhythm has been named a Leader in the Forrester Wave: Security Analytics Platforms, Q1 2017 analyst report, was honored by the SANS Institute in the “Best of 2016 Awards” in the SIEM category for…
Read MoreMay 9, 2017
Stop Insider Threats with LogRhythm’s UEBA Capabilities
Detecting and responding to a threat in the earliest stages of the Cyber Attack Lifecycle is the key factor in preventing a breach from becoming a detrimental incident. LogRhythm User and Entity Behavior Analytics (UEBA) detects and neutralizes both known…
Read MoreMay 4, 2017
Achieving Intelligent Infrastructure Defense with LogRhythm’s Co-Pilot Service and Security Analytics
Retailers have learned hard lessons in recent years, as organizations such as Target have suffered major data breaches. In Target’s case, the compromised credit card information of 70 million customers have resulted in significant expense, lost revenues, and a damaged…
Read MoreJanuary 5, 2017
Avoid Major Data Breaches with Effective Threat Lifecycle Management
Posted by: Chris Petersen
A New Approach to Cybersecurity It’s a simple concept: The earlier you detect and mitigate a threat, the less the ultimate cost to your business. Implementing an effective end-to-end threat management process that focuses on reducing detection and response times…
Read MoreDecember 1, 2016
The Best Gets Better: Introducing LogRhythm 7.2
Posted by: Chris Petersen
I’m excited to share our latest release, LogRhythm 7.2. It arms your team with the ability to detect, respond to, and neutralize threats before they result in damaging cyber incidents like a data breach. LogRhythm 7.2 builds upon the groundbreaking…
Read MoreNovember 29, 2016
Detecting Home Network Issues with Network Monitor
I’ve been running a test Network Monitoring (NetMon) Mini device at home for the past few weeks and, up until recently, I didn’t notice anything “unexpected” on my home network. Figure 1: Miniature NetMon Home Appliance (Click on images to…
Read MoreNovember 8, 2016