LogRhythm Brings Greater Choice to SIEM Pricing
For years, consumption-based pricing has dominated the security information and event management (SIEM) market. Whether organizations paid a fixed amount based on message per second, event per second, or gigabyte per day, that model was the go-to standard. However, as…
Read MoreNovember 11, 2019
The Only Unlimited SIEM Data Plan in Town
Recently, you’ve heard a lot about unlimited data plans for security information and event management (SIEM) products in the information security (InfoSec) space. However, the word “unlimited” appears not to have an agreed upon definition across vendors. In fact, other…
Read MoreOctober 22, 2019
What Data Sources Would You Add to Your SIEM if Cost Wasn’t an Issue?
If your organization is dealing with digital transformation and modernizing your IT infrastructure, you’re likely also seeing data volumes in your environment grow rapidly. As your data grows, you need to find a security information and event management (SIEM) solution…
Read MoreOctober 1, 2019
The Top Five Benefits of Cloud SIEM, According to Security Experts
Gartner predicts that “By 2023, 80% of SIEM solutions will have capabilities that are only delivered via the cloud (for example, log storage, analytics, incident management), up from 20% currently.” As SIEM solutions start to offer their products via the…
Read MoreAugust 20, 2019
Introducing LogRhythm Echo
LogRhythm Echo is now available. LogRhythm Echo is a standalone app that simulates incident scenarios for demonstration purposes, allowing you to test security rules, verify embedded content, and perform red team preparedness exercises. Regardless of the size of your team,…
Read MoreJuly 24, 2019
The LogRhythm NextGen SIEM Platform Moves to the Cloud
Posted by: Chris Petersen
Principle Development Objectives for LogRhythm Cloud Building our award-winning NextGen SIEM Platform as a SaaS offering has been in the works for some time. When we initiated the project, our principle objective was quite simple: to deliver the most complete…
Read MoreMay 17, 2019
Selecting the Best Data Storage Solution for Your Organization
Security is powered by data, including many machine-generated log sources — from IT infrastructure to cloud applications, personal laptops to Point of Sale endpoints, and internet of things (IoT) devices. While you can’t investigate threats without it, it is often…
Read MoreMay 13, 2019
Leading from Every Angle: NextGen SIEM Leadership in 2019
I remember the first time LogRhythm was awarded Best SIEM by SC Media — formerly SC Magazine. It was 2009, Lady Gaga was winning Grammy awards, the global economy was at rock bottom, and LogRhythm had begun our climb to…
Read MoreApril 26, 2019
Aligning the LogRhythm NextGen SIEM Platform with the MITRE ATT&CK Framework
Posted by: LogRhythm Labs
Contributors to this blog include Dan Kaiser and Brian Coulson. The MITRE ATT&CK framework is quickly becoming a focal point in the security world — and for good reason. This framework provides a consistent, industry-wide standard on which you can…
Read MoreApril 15, 2019
Monitoring Cloud Infrastructure with LogRhythm: Data Collection
In the past few years, we’ve seen a massive uptick of interest in leveraging cloud infrastructure from Logrhythm customers. Just a few years ago, organizations viewed cloud as an interesting proposition for a few use cases. Today, we see many…
Read MoreMarch 27, 2019
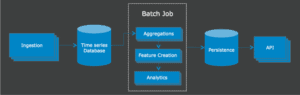
LogRhythm’s Road to Scalable Cloud Analytics
Posted by: Joel Holsteen
As a security company, our first priority is sharing relevant tools and content to make sure organizations can detect and respond to threats faster and more efficiently. To make this happen, there’s a lot that goes on behind the scenes;…
Read MoreJanuary 24, 2019
How LogRhythm 7.4 Drives Customer Success
Accelerating your return on investment (ROI) is critical to drive customer success at LogRhythm. But increasing ROI is only part of our secret sauce. Here at LogRhythm, we enable you to realize greater security operations workflow efficiency and increasingly advanced analytics with each release. To…
Read MoreDecember 13, 2018
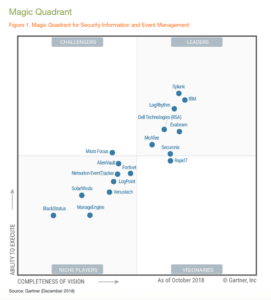
LogRhythm Named a Leader in the 2018 Gartner SIEM Magic Quadrant
We are pleased to see Gartner’s recognition of LogRhythm as a Leader in its recent release of Gartner’s Magic Quadrant for Security Information and Event Management (SIEM) research report. Figure 1: The 2018 Gartner SIEM Magic Quadrant This is on…
Read MoreDecember 5, 2018
Insight into User Behavior Using LogRhythm CloudAI: Part I
Posted by: Phil Villella
As Chief Scientist and de facto Technical Product Manager for LogRhythm’s Data Science team, I continuously evaluate the effectiveness of LogRhythm’s user and entity behavior analytics (UEBA) functionality to surface user activity that may be of interest to a security…
Read MoreNovember 12, 2018
Is It Time to Find a New SIEM?
Though we go head-to-head on a daily basis, I would be remiss if I didn’t appreciate the competition amongst us vendors within the Security Information and Event Management (SIEM) space. It’s this healthy competition that drives each of our respective…
Read MoreAugust 7, 2018
A Commitment to Customer Success: LogRhythm Receives Gartner Peer Insights Customers’ Choice Designation
Posted by: Kish Dill
Gartner recently announced that LogRhythm was named a 2018 Gartner Peer Insights Customers’ Choice for Security Information and Event Management (SIEM) Software. Based on more than 100 reviews, LogRhythm earned an average score of 4.4 out of five stars. More…
Read MoreAugust 2, 2018
With Thoma Bravo, LogRhythm Innovation Accelerates
Posted by: Chris Petersen
Last week, we announced a definitive agreement with Thoma Bravo, a leading private equity investment firm, to acquire a majority interest in LogRhythm. This investment validates LogRhythm’s significant history of market leadership and innovation, and is expected to support our…
Read MoreJune 5, 2018
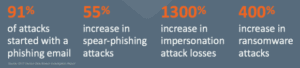
Augmenting Your Cyber Resiliency Strategy with NextGen SIEM
The cybersecurity challenge centers around a fundamentally simple concept: Email keeps businesses running and stores critically important corporate and personal data, but email is also the top vector for cyberattacks. The cyberattack trends and numbers speak volumes: Figure 1: Cyberattack…
Read MoreMay 2, 2018